Hello, aspiring ethical hackers. In this blogpost, you will learn what is ethical hacking and the 5 phases of ethical hacking.
What is Ethical Hacking?
Ethical hacking is hacking that is performed while following the ethics and rules. It is a procedure of detecting vulnerabilities and weaknesses in the target organization’s network and exploiting them with the written permission of an individual or organization. It is performed to find out and fix the vulnerabilities in the network that can be exploited by bad hackers aka Black Hat hackers.
What are the 5 phases of ethical hacking?
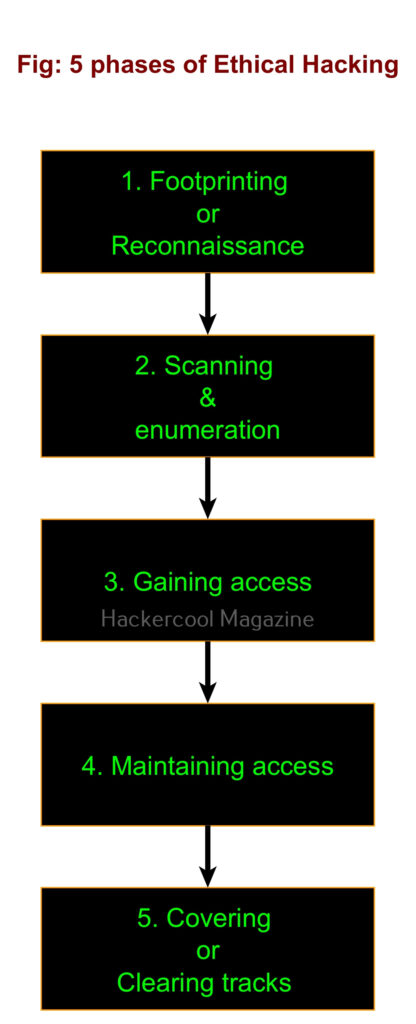
Ethical hacking consists of 5 phases. They are,
1. Foot printing:
Also known as information gathering or reconnaissance, in this phase ethical hackers try to collect as much information as possible about the target organization or individual that may be helpful to them in the next phases of ethical hacking. Learn more about Footprinting.
2. Scanning & enumeration:
In this phase, the target organization’s network is probed to find any path of entry that can provide a way for ethical hackers into the network. It includes scanning for live systems in the network range, scanning for open ports on the LIVE systems and services running on them and scanning for any vulnerabilities in those services.
Then these services are enumerated to find any user accounts or other Information about the target networks. Learn more about scanning & enumeration.
3. Gaining access:
In this phase ethical hacking, ethical hackers exploit one of the vulnerability or weakness found in the second phase and gain a shell on the target system or network. Learn more about gaining access.
In this phase, ethical hackers after gaining initial access on the target system or network, try to maintain this access for future and continuous use. Learn more about various techniques used for maintaining access.
5. Covering tracks:
In this phase, ethical hackers try to hide or erase all their operations performed on the target system or network until now. This is to remove any evidence of their malicious activity. In Black Hat Hacking, they do this to prevent tracing of the hack back to them. This phase is also known as clearing tracks. Learn more about covering tracks.
Follow Us