Hello aspiring Ethical Hackers. In this article, readers will learn about Follina, the latest Zero-Day vulnerability in Microsoft.
Vulnerability & Impact
Follina is the name given to a remote code execution (RCE) vulnerability in the Microsoft Support Diagnostic Tool (MSDT). This vulnerability allows a remote attacker to use a Microsoft Office document template to execute code via MSDT and download a malicious payload from a remote URL. It affects Office 2013, 2016, 2019, 2021, Office ProPlus and Office 365.
What actually is Follina?
Follina is a municipality that is located 60 kms northwest of Venice in Italy. Completely unrelated, the vulnerability has been named Follina as the malicious file was referencing to an executable that was named 0438. This is the area code of Follina, hence the zero-day has been named so.
What is MSDT?
Follina exploits MSDT but what is MSDT? Microsoft Support Diagnostic Tool (MSDT) is a service used for gathering diagnostic data about the system.
Proof Of Concept
Let’s see how to exploit Follina practically. For this let’s download a exploit from Github. Navigate into the cloned directory and you will files as shown below.
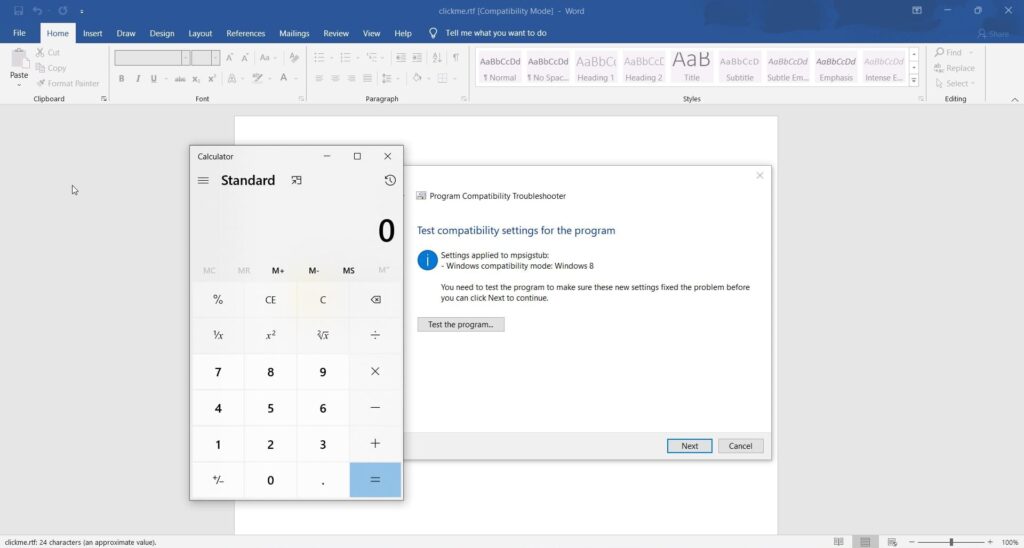
Two files are important in this directory. The “clickme.docx” is the file that uses MSDT to connect to a remote website and execute the exploit. The exploit is present in the “exploit.html” file. If this POC is successful, the exploit will popup calc.exe.
I tested this exploit on MS Office 2019 running on Windows 10. I hosted the exploit using Wamp server running on localhost.
I opened the clickme.doc and waited. Nothing happened. Then I saved it as clickme.rtf file as shown below.
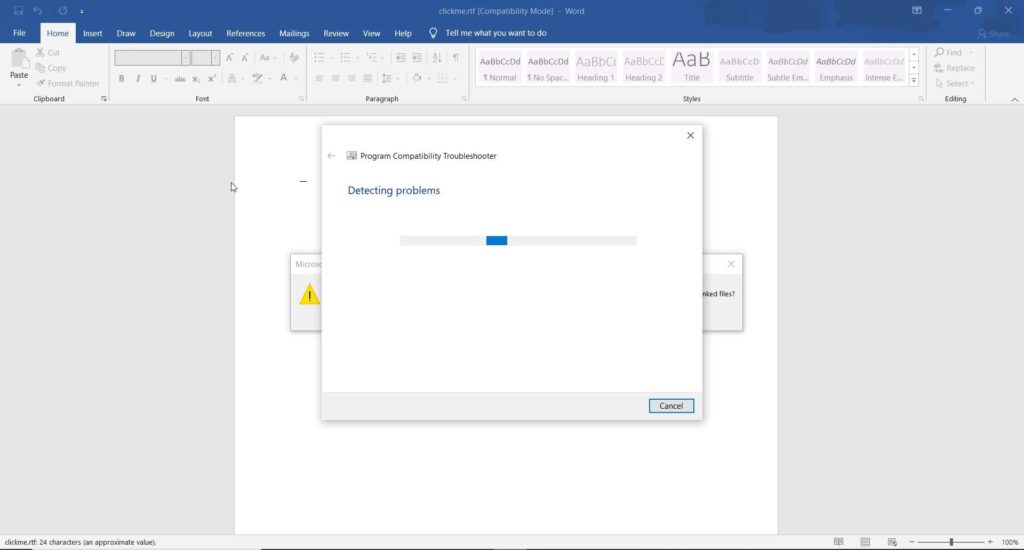
This time when I clicked on clickme.rtf file, this happened,
And the calculator popped up. The Proof Of Concept Is Successful.
Follow Us