Hello aspiring Ethical Hackers. In our previous blogpost you learnt what is a port? what is port scanning etc. In this blogpost, you will learn about different port scanning techniques that are be used to determine if a port is open or not. Ethical Hackers and Penetration Testers use different port scanning techniques to determine if a port is open or not. Unless a port is open, you cannot enumerate the service running on it for further exploitation. So, using a wrong port scanning technique can give you a wrong result.
In order to understand the various port scanning techniques, readers need to first understand how TCP communication takes place between programs and applications. You have read in our article on OSI model that the Transport Layer is responsible for reliable data transfer between end systems. You have also read two protocols are used for data transfer between devices and applications. They are Transmission Control Protocol (TCP) and user Datagram Protocol (UDP).
Transmission Control Protocol is a reliable connection-oriented protocol that ensures that data is transmitted accurately and completely between programs and applications.
How TCP communication takes place?
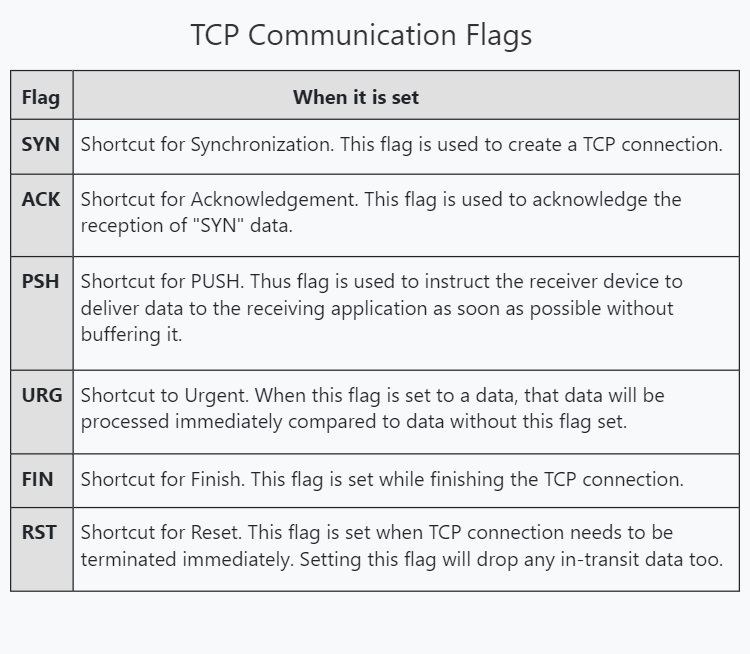
To make sure that data is transmitting correctly and completely, Transmission Control Protocol (TCP) uses various flags in the headers. These flags are given below.
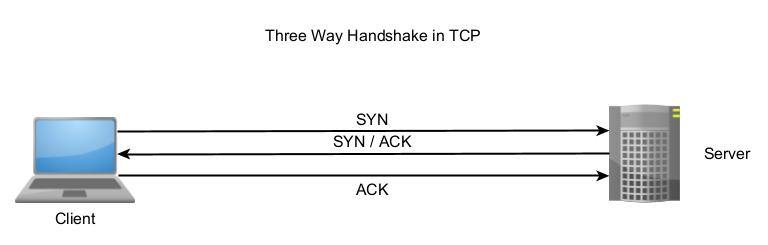
TCP Three-Way Handshake
Before sending data using TCP, two devices establish a connection using a Three-Way handshake which is shown below.
- A client sends a TCP packet to the Server with SYN flag set.
- The Server responds with a TCP packet with both SYN and ACK flags set.
- The client replies to the packet with a TCP packet with ACK flag set.
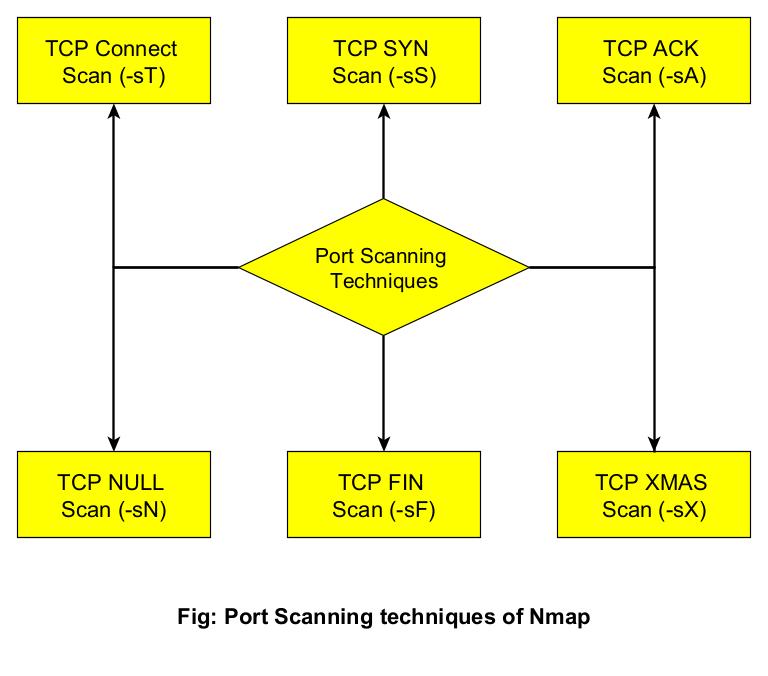
After this 3-way handshake, both client and Server start sending and receiving data. Now, that you understood how a TCP communication works it’s time to see different port scanning techniques.
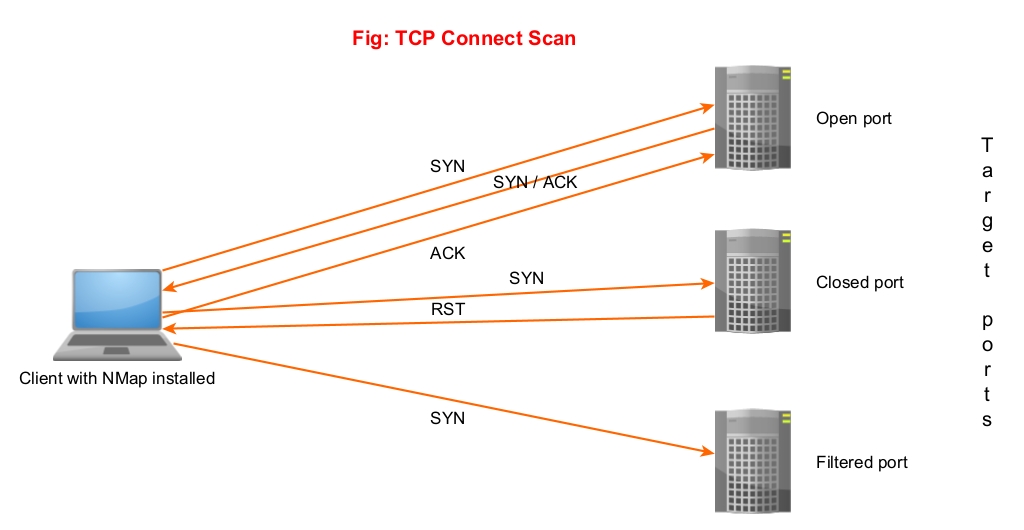
1. TCP Connect Scan (-sT)
In this type of scan, NMAP sends a TCP packet to a port with the SYN flags set. If the port is open, the target responds with a SYN/ACK flag set to packet. Then Nmap sends ACK packet. If the port is closed, the target sends a RST packet. If the target doesn’t respond, the port can be considered filtered.
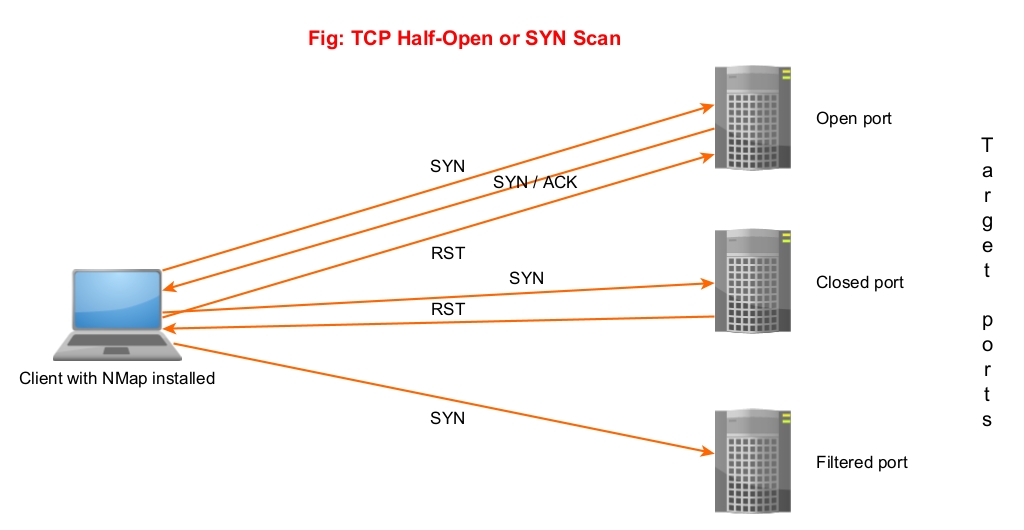
2. SYN or Half-Open Scan (-sS)
In a SYN scan, Nmap sends a SYN packet to the target port. If the port is open, the target sends a “SYN/ACK” set packet. Then Nmap instead of sending a packet with ACK flag set, sends a packet with RST flag set to terminate the connection. Since the Three-way handshake is not complete, it is known as “half-open” scan. Similarly, since the TCP connection is not complete it is not logged and hence considered a stealthy scan. Also, unlike TCP connect scan this scan is fast.
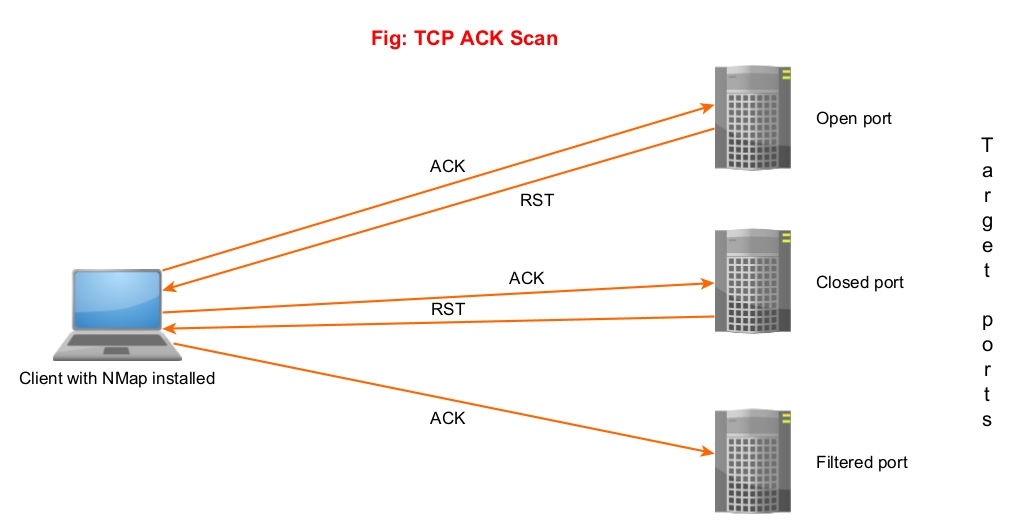
3. ACK Scan (-sA)
Unlike the above two scans, this scan is not used to determine if a port is open or not. In fact, it is used to determine firewall rulesets. In this scan, Nmap sends a packet with ACK flag set to the target port. Here, both open and closed ports send a packet with RST flag set. These ports are labelled as unfiltered. If the ACK packet is dropped, the port is labelled as filtered.
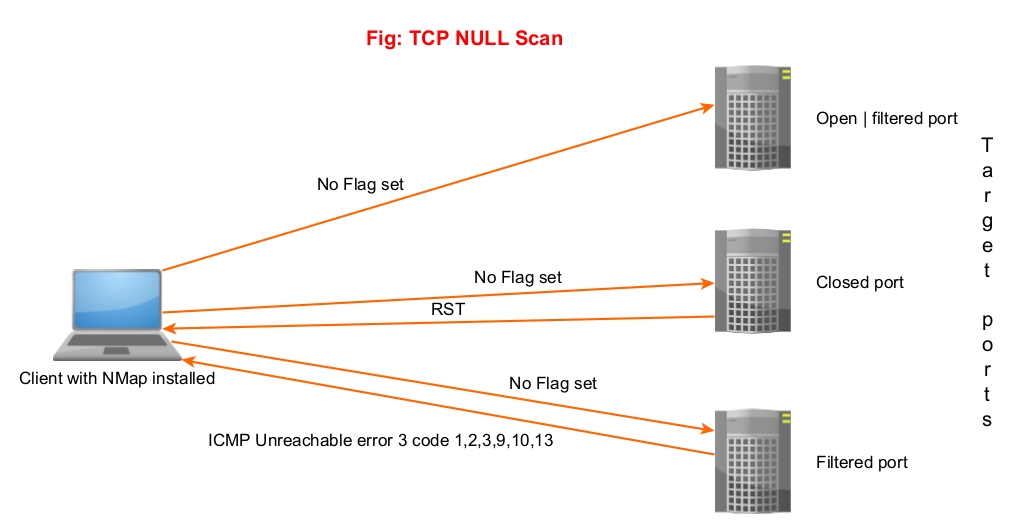
4. NULL Scan (-sN)
In this scan, Nmap doesn’t set any flags while sending a packet to the target. If no response is received, the port is assigned as open/filtered. If an RST flag is received from the target port, the port is considered closed and if any ICMP unreachable error 3, code,1,2, 9,10 or 13 is received, it is considered as filtered.
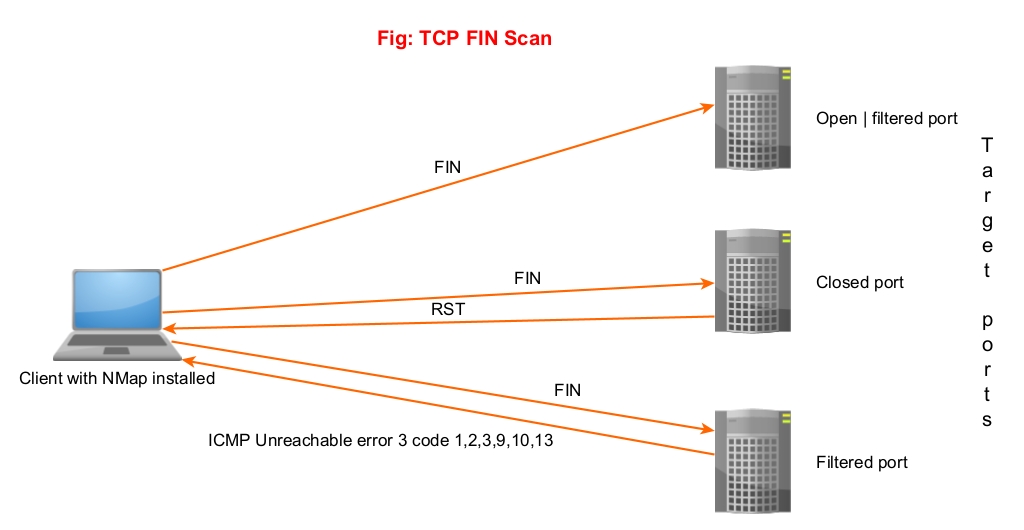
5. FIN Scan (-sF)
In this scan, Nmap sends a packet with FIN flag set to the target. The result is same as that of NULL scan.
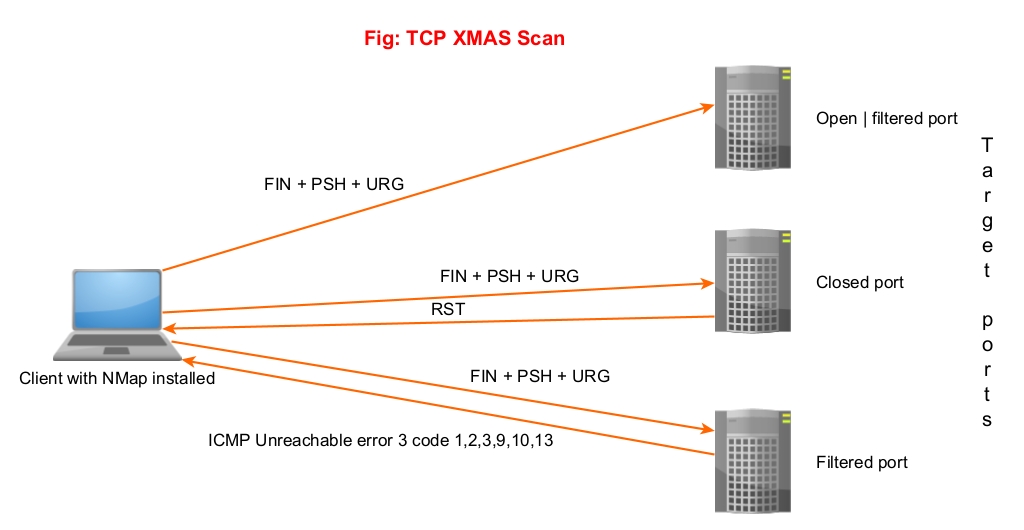
6. XMAS Scan (-sX)
In this type of scan, NMAP sets FIN, PSH and URG flags to the packet and sends it to target port. The result is same as that of Null scan & FIN scan.
Since the packet is lighted up like a Christmas tree when these 3 flags are set, it is known as XMAS scan. Learn about different port scan results.
Follow Us