Hello, aspiring ethical hackers. In this blogpost, you will learn about Firewalls. A firewall is a software or a hardware device that acts as a wall between the internet and the internal networks or between any two networks. The main purpose of the firewall is to prevent malicious traffic from entering the internal network.
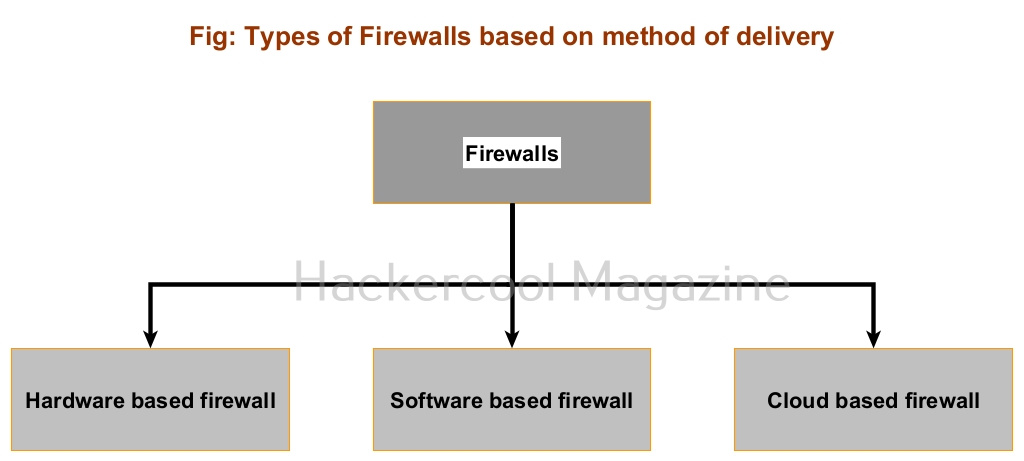
Based on the delivery method, a firewall can be classified into three types. They are,
- Hardware
- Software
- Cloud based
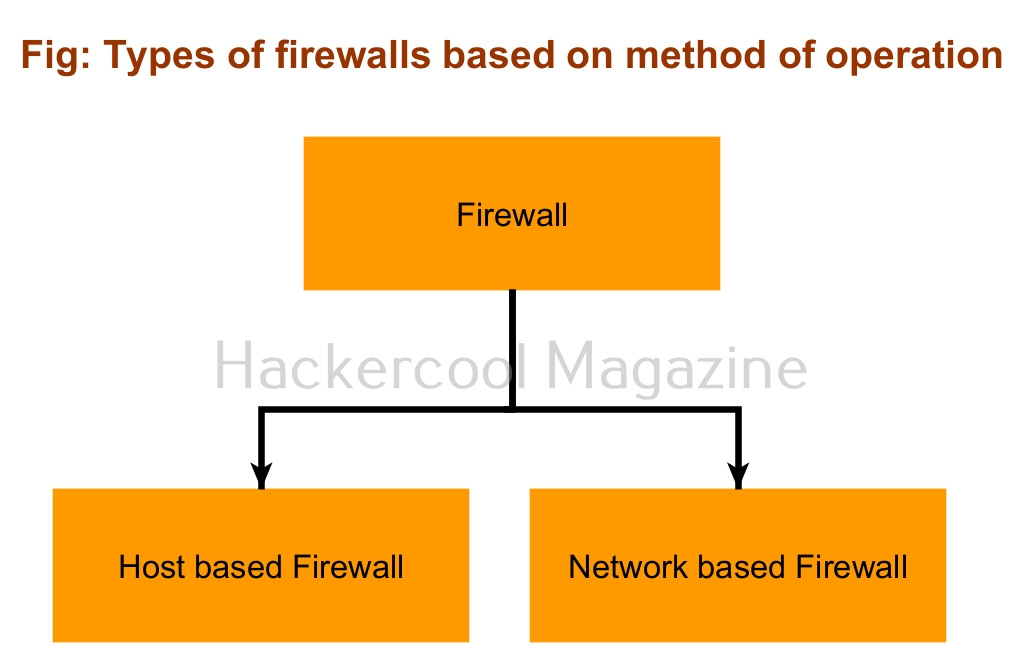
There are two types of firewalls based on the method of operation. They are, Host-based and Network based firewalls.
- A host-based firewall is a software that is installed on a computer or network. Ex: Windows Firewall.
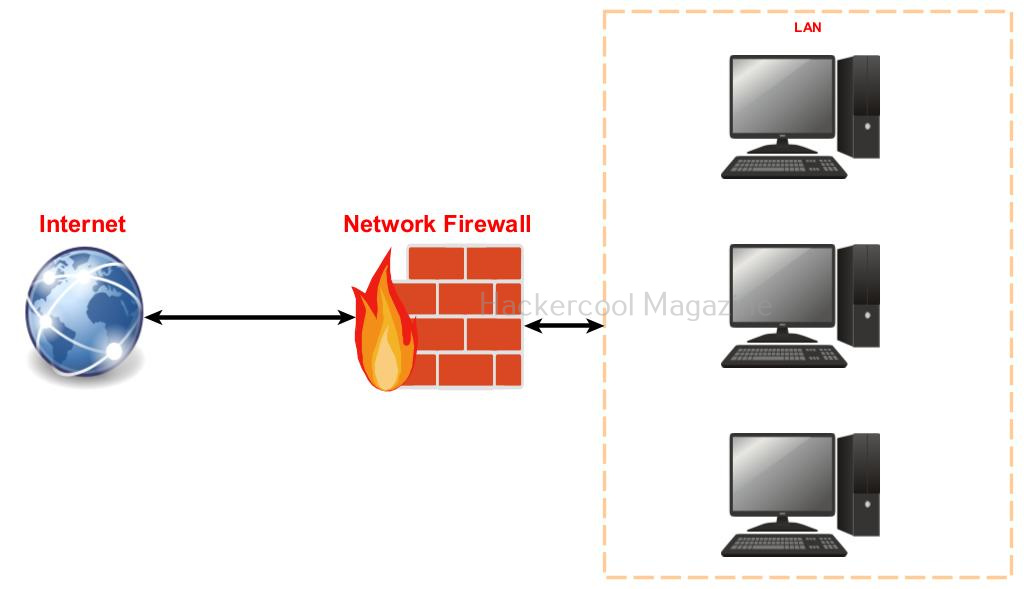
- Network based firewall is a software or hardware firewall that acts as a barrier for the entire network.
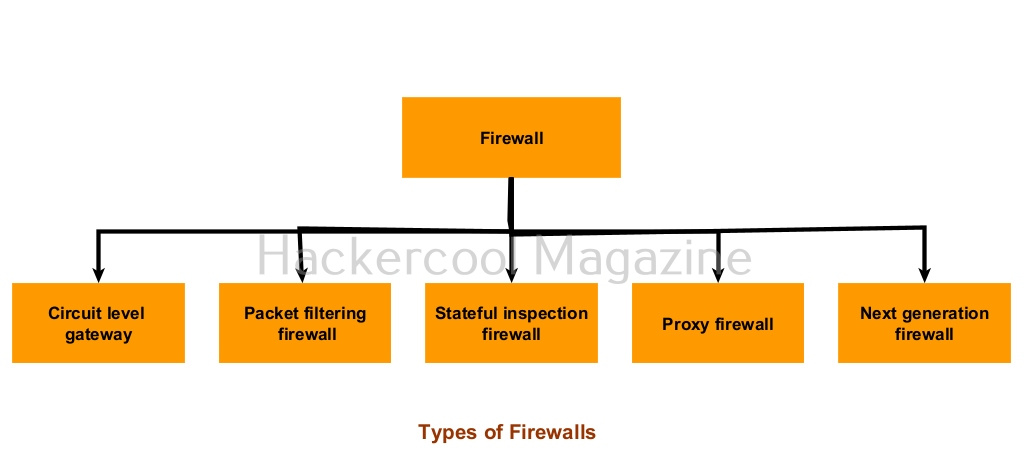
Types of Firewalls
Different types of firewalls use different methods of operation to block malicious traffic. Before you learn about how firewalls operate, let’s first see how network traffic travels from one computer to another computer.
When one computer (let’s say computer A) sends data to another computer (let’s say computer B), the data is first split into differ parts which are known as packets. These packets are sent to computer B. Before being transmitted, a header is added at the beginning of each packet. This header contains information like source IP address, destination IP address, source and destination ports, network ports etc. Once these packets reach the computer B, they are reassembled. Now, let’s learn about the different types of firewalls.
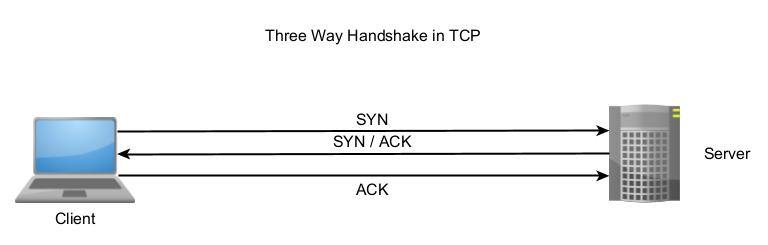
1. Circuit level gateway:
The simplest types of firewall, it operates at the session layer of the OSI model. This type of firewall monitors TCP handshakes between two machines.
Based on the configured settings of the firewall, it accepts or blocks traffic. Circuit level gateways don’t inspect the packets. So as long as there is a handshake, even malware laden requests are allowed.
2. Packet filtering firewalls:
As the name of the firewall says, this firewall inspects the packet’s header for information about source and destination IP address, port etc. It operates on the network layer of OSI model. Note that it doesn’t inspect the actual payload.
3. Stateful Inspection firewall:
Stateful Inspection firewalls work on network and transport layer of the OSI models. It uses both TCP handshakes and packet filtering to detect malicious traffic. It specifies traffic as malicious after observing the traffic for a particular period of time which is known as state. Then it compares the network traffic to the observed state to classify traffic as malicious or not.
4. Proxy firewall:
A proxy firewall is mostly used to hide or make the IP address of the client’s system or network IP. It operates at the application layer and checks both header of the payload and the payload to classify traffic as malicious.
5. Next Generation firewall:
A next-generation firewall uses the features of all the above-mentioned firewalls to classify traffic as malicious or not.
Follow Us