Hello, aspiring ethical hackers. Payloads play a very important role in ethical hacking. In this blogpost, you will learn everything about Metasploit payloads beginning from what is a payload, how many types of payloads are there and various functions of payloads etc.
What is a payload?
A payload in cyber security is a piece of code that is executed after successfully running an exploit to take advantage of a vulnerability. When a Proof Of Concept (POC) for a vulnerability is disclosed, this allows most hackers around the world to execute their chosen payloads. This payload can be anything from malware, reverse shell, RAT, ransomware etc or their own custom payload.
For example, ms08_067 vulnerability was exploited in real-world to deploy Conficker worm, but while pen testing, a meterpreter payload is used most probably.
Types of Metasploit payloads
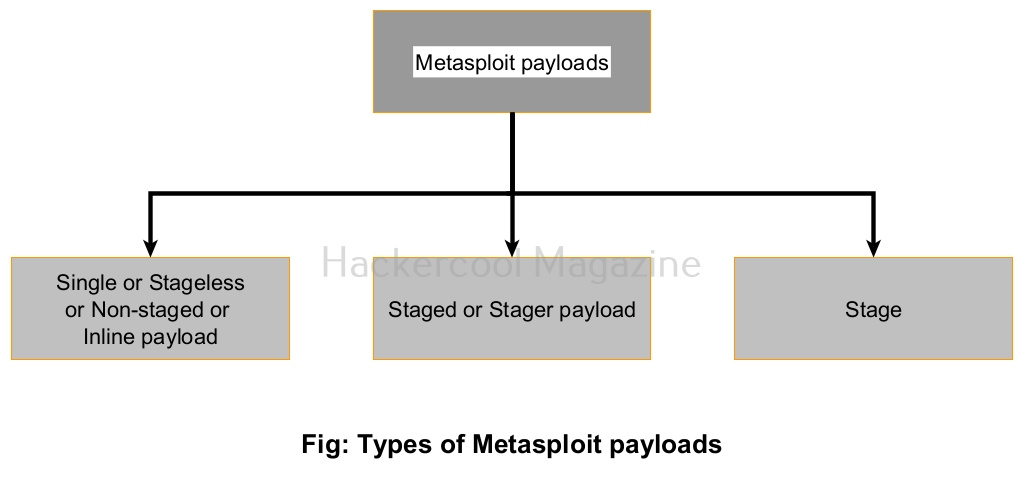
Payloads in Metasploit can be classified into three types based on their function. They are.
- Staged payloads or stagers.
- Stageless or Non-staged (Inline) payloads or Single payloads.
- Stages
1. Single or Stageless / Non-staged or Inline payload:
A single payload s self-contained as it contains in itself all the code required to do what it does. This is one of the easiest payloads to create but its size is a bit large. This may increase suspicions.
2. Stager payload:
Stager payloads also known as stagers set the stage for another payload. Their purpose is to establish a network connection between the target system and attacker system.
3. Stages:
This is the payload that is downloaded by stager payload.
Follow Us