Hello aspiring ethical hackers. In this blogpost, you will learn in detail about ethical hacking. As the cybersecurity threat landscape is continuously evolving, the role of ethical hacking role in protecting the organizations is also increasing. But what exactly is ethical hacking?
What is Ethical Hacking?
Ethical hacking is the process of hacking into a system, network or application but with the permission or authorization of the owner of the resource. In simple terms ethical hacking is gaining access to someone’s system, network or application with their prior permission. Ethical hacking is performed to detect and find any threats or vulnerabilities malicious hackers in real-world may exploit and then patch them to improve the security of the organization.
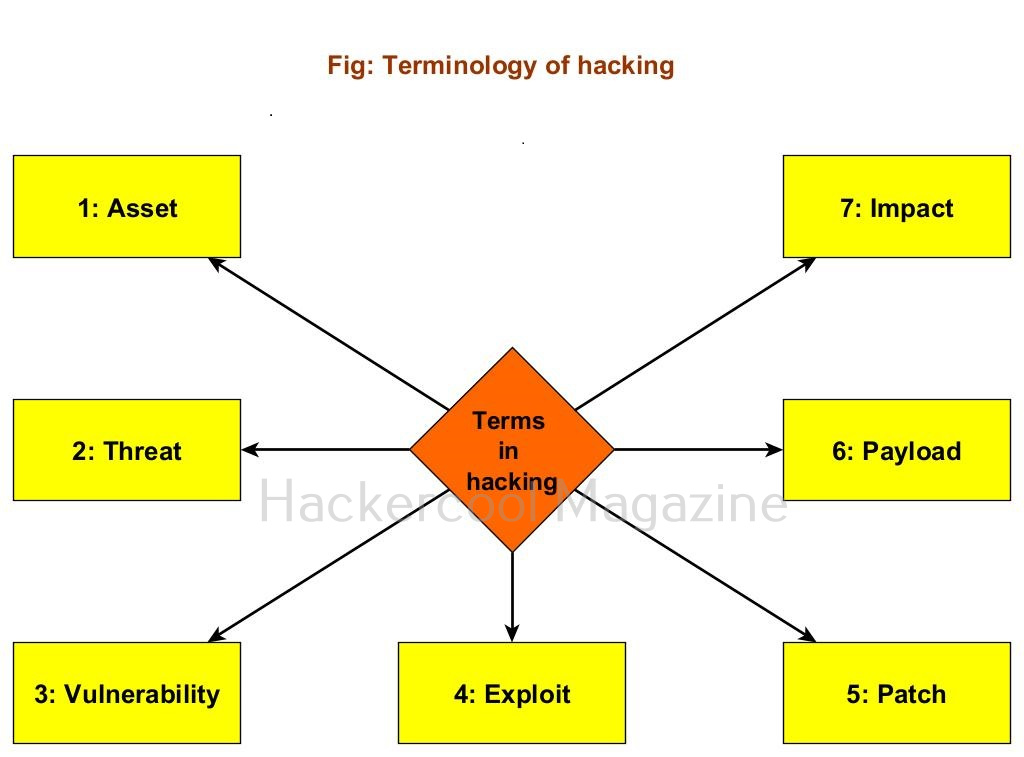
Terminology of ethical hacking
To understand hacking, you need to have a basic understanding of some of the terms related to hacking. They are,
1. Asset:
In an organization, anything of value is considered as an asset. For example, employee records of the organization, employee credentials, records of its customers, the servers, computers etc are considered of value to the organization.
2. Threat:
Any action or event that can disrupt the organization’s activities can be termed as threat. For example, these actions can be deleting the user accounts of employees of the organization, making their services unavailable to their customers etc.
3. Vulnerability:
A vulnerability is a weakness in the system application or network of the organization.
4. Exploit:
The programing code written to take advantage of this vulnerability is known as exploit. (A zero-day vulnerability is a vulnerability which doesn’t have any patch yet).
5. Patch:
Code written to mitigate the vulnerability in the system, application or network is known as a patch. (You should have heard of Exploit Database. As the name of the website implies, it hosts all the exploits or POC’s. A proof of Concept is the exploit code written to demonstrate the vulnerability.
6. Payload:
In hacking, exploit takes advantage of the vulnerabilities. After exploiting the vulnerability, hackers usually run specific code. This code is known as payload. For example, ms_08_067 is a vulnerability which is exploited by the exploit module of same name, while meterpreter is the payload. Learn more about the payloads here.
7. Impact:
The damage done to the asset due to exploitation of vulnerability is known as impact.
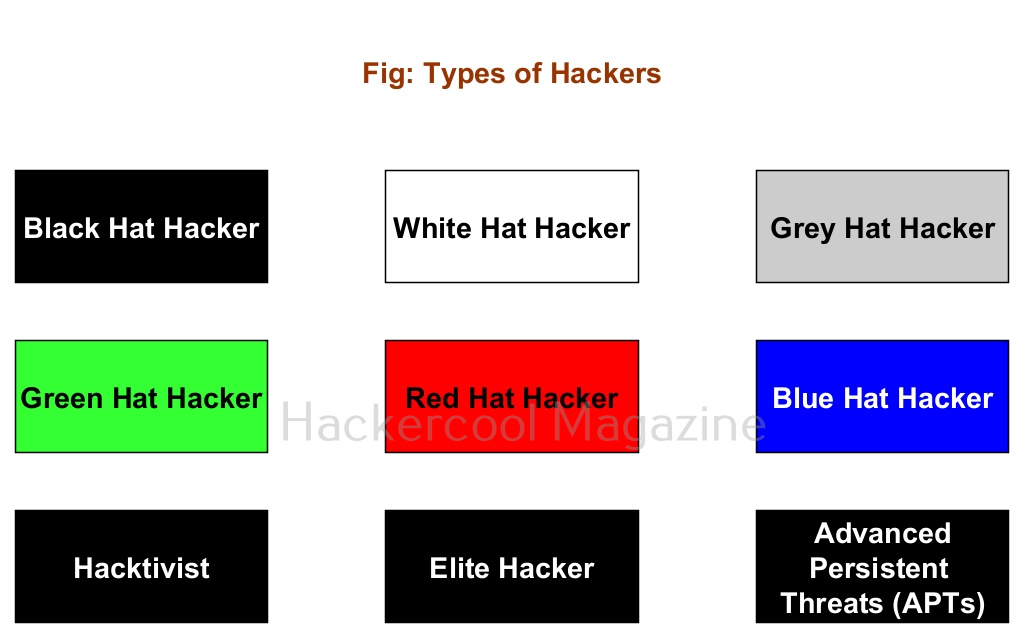
Types of hackers
A person performing ethical hacking is known as an ethical hacker. You have learnt that a person performing hacking is known as a hacker. Based on the type of hacking they perform; hackers can be classified into different types. They are,
1. Black Hat Hacker:
A Black Hat Hacker is a hacker who performs all illegal hacking attacks. These are the villains in the domain of hacking.
2. White Hat Hacker:
If there are bad guys of hacking, there are bound to be good guys of hacking. White Hat hackers are the good guys of hacking. They protect the organizations from the Black Hat Hackers.
3. Grey Hat Hacker:
Like the Grey zone, these hackers are in the group of ambiguous zone, who cannot be necessarily called Black Hat or White Hat hackers. For example, a person working as a White Hat Hacker in day and taking Black Hat assignments at night.
4. Green Hat Hacker:
Green Hat Hackers are those hackers who have no knowledge but are “experts” at using readymade tools and exploits made by Elite Hackers.
5. Red Hat Hacker:
Red Hat Hackers are White Hat Hackers that try to take down or prevents Black Hat Hackers. They sometimes use aggressive tactics to achieve their goal.
6. Blue Hat Hacker:
Blue Hat Hackers (also known as Blue Teams) are hired to test the organization for any vulnerabilities or weaknesses. They are similar to White Hat Hackers but are extreme.
7. Hacktivist:
A hacktivist is a type of hacker who hacks to promote a political or social or environmental cause.
8. Elite Hackers:
At the opposite ends of Green Hat Hacker or script kiddie, we have the Elite Hackers who have deep knowledge of hacking. He/she likes to write his/her own exploits, find zero-days etc.
9. Advanced Persistent Threats (APTs):
APT’s are state-sponsored hackers (more rightly hacker groups) that are specifically used to target enemy nations, perform cyber espionage, collect information etc.
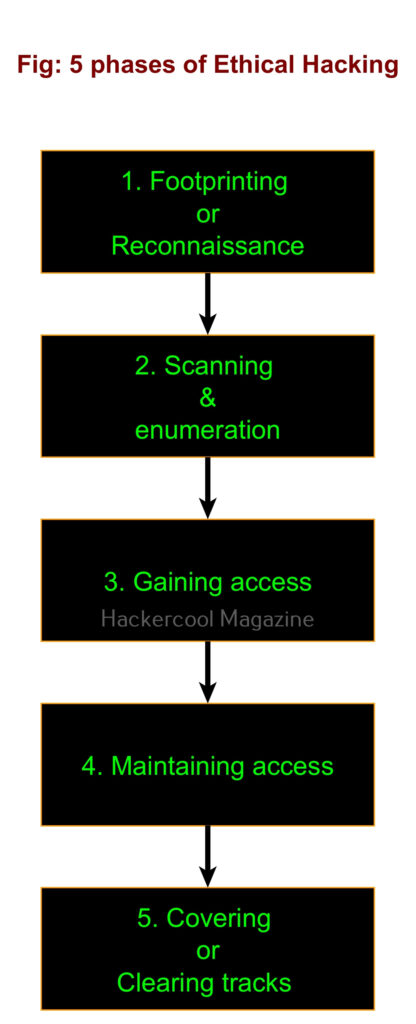
What are the 5 phases of ethical hacking?
Ethical hacking consists of 5 phases. They are,
1. Foot printing:
Also known as information gathering or reconnaissance, in this phase ethical hackers try to collect as much information as possible about the target organization or individual that may be helpful to them in the next phases of ethical hacking. Learn more about Footprinting.
2. Scanning & enumeration:
In this phase, the target organization’s network is probed to find any path of entry that can provide a way for ethical hackers into the network. It includes scanning for live systems in the network range, scanning for open ports on the LIVE systems and services running on them and scanning for any vulnerabilities in those services.
Then these services are enumerated to find any user accounts or other Information about the target networks. Learn more about scanning & enumeration.
3. Gaining access:
In this phase ethical hacking, ethical hackers exploit one of the vulnerability or weakness found in the second phase and gain a shell on the target system or network. Learn more about gaining access.
In this phase, ethical hackers after gaining initial access on the target system or network, try to maintain this access for future and continuous use. Learn more about various techniques used for maintaining access.
5. Covering tracks:
In this phase, ethical hackers try to hide or erase all their operations performed on the target system or network until now. This is to remove any evidence of their malicious activity. In Black Hat Hacking, they do this to prevent tracing of the hack back to them. This phase is also known as clearing tracks. Learn more about covering tracks.
Follow Us