Hello, aspiring ethical hackers. In this blogpost, you will learn about web application hacking. Based on research of Verizon, web applications were the most exploited vector in hacking incidents and data breachers that happened last year (2023).
According to the CyCognito State Of Web application Security Testing 2024 report, each organization exposes 100s of web applications to the web out of which 70% are untested for any security vulnerabilities. These web applications provide a large attack surface which can easily be exploited by hackers. To understand threats to web applications you need to thoroughly understand what a web application is, what is web application hacking, types of attacks that affect web applications etc.
What is a web application?
A web application is any program or application that is rendered through web browsers. Any app that you use through the browser without downloading it to your Desktop or Laptop is a web app. Example of web applications are Gmail, Netflix, Yahoo, Canva etc.
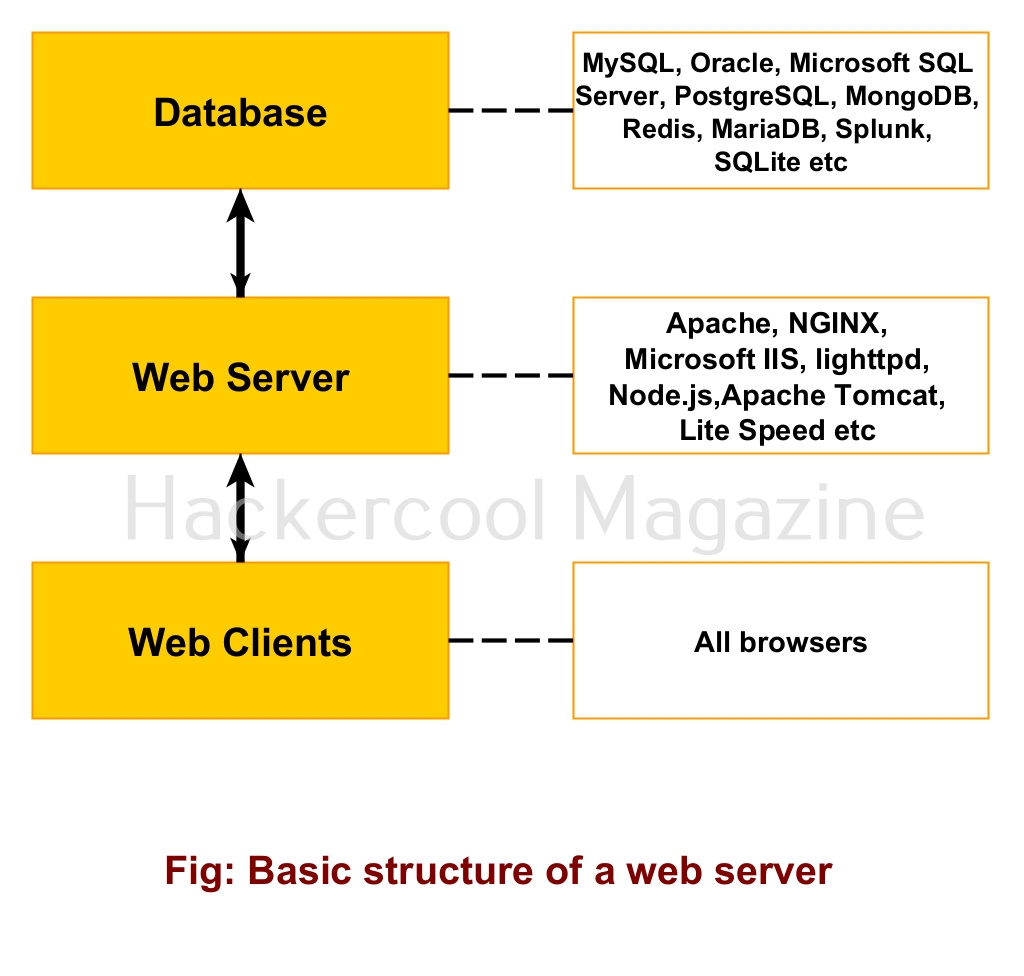
A web application is hosted on a web server and application server. A web server consists of both hardware and software components. Examples of popular web server software are Apache, NGINX, Microsoft IIS, Lighthttpd, node.js, Apache Tomcat and LiteSpeed etc. To store data, web servers use a database. Most popular databases in use are MySQL, Oracle, Microsoft SQL Server, PostgreSQL, MongoDB, Redis, MariaDB, Splunk, SQLite etc.
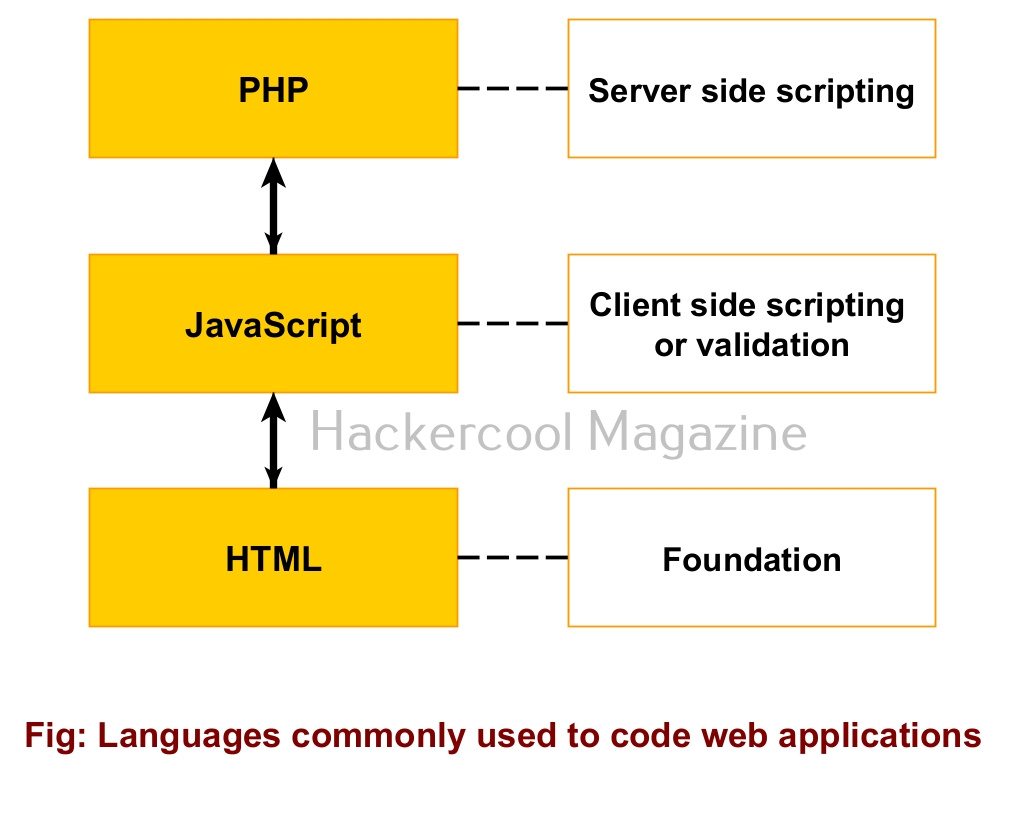
Similar to a website, a web application is written in HTML/CSS, JavaScript and it uses PHP/ASP for server side programming and Database for storing data etc. Apart from a web server there is also presence of an application server to serve web apps.
What is web application hacking?
Hacking of these web applications to compromise the entire web server or the entire network is known as web application hacking.
Types of web application attacks
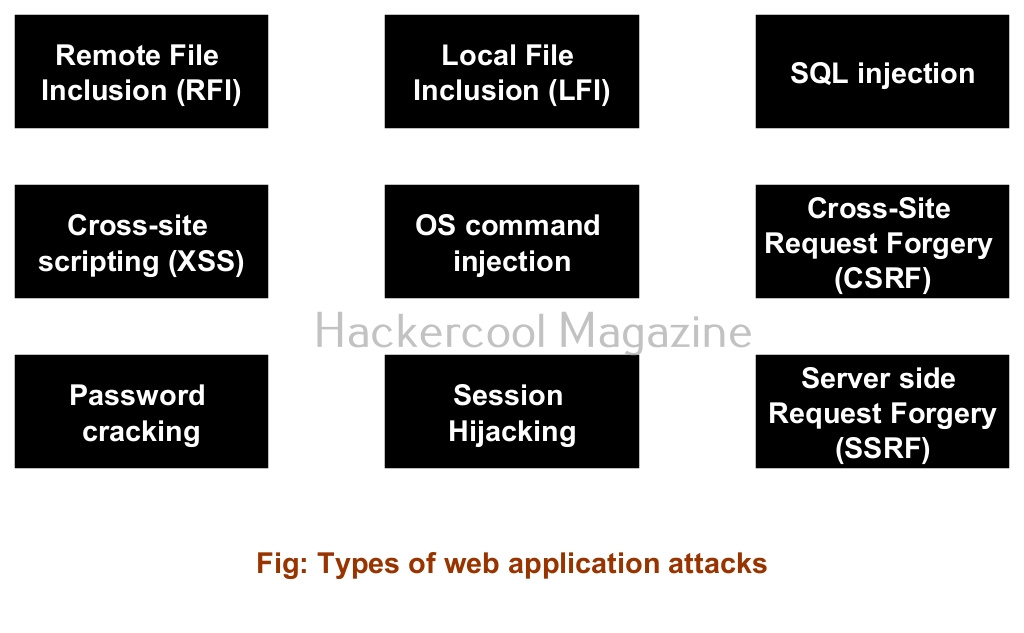
There are many attacks that can be used to compromise web applications..
1. Remote File Inclusion (RFI) attack
2. Local File Inclusion attack
3. SQL injection attack
4. Cross-site scripting (XSS) attack
5. OS Command Injection attack
6. Cross site Request Forgery (CSRF) attack
7. Password cracking attack
8. Session Hijacking attack
9. Server side request forgery (SSRF) attack
Impact of a web application hacking
Compromise of a web application can have many affects. Most important of them are,
1. Data breach and Data theft:
Compromise of a web application can result in a data breach and data theft.
2. Leak of sensitive information:
Sometimes, a web application compromise can leak sensitive information about a company or organization.
3. Web app defacement:
Every web application has an index page that is the page that loads when you visit a website. When hackers change the index page and replace it with another page, it is known as website defacement.
4. Secondary attacks:
Once a web application is compromised, it can be used by hackers for other malicious purposes like hosting malware, to perform a DDoS attack or using it as a proxy to perform attacks on other websites.
Follow Us