Hello, aspiring ethical hackers. In our previous blogpost, you learnt about LinSSID, the graphical wifi scanner for Linux. In this article, you will learn about sparrow-wifi, a graphical wifi analyzer. Sparrow-wifi is a Python tool that provides a comprehensive GUI based alternative to tools like InSSIder. . This tool can be used to analyze WiFi, software defined radio, bluetooth and GPS etc.
Its features include,
1. Basic wifi SSID identification.
2. Wifi source hunt: Switch from normal to hunt mode to get multiple samples per second and use the telemetry windows to track a wifi source.
3. 2.4 GHz and 5 GHz spectrum view: Overlay spectrums from Ubertooth (2.4 GHz) or HackRF (2.4 GHz and 5 GHz) in real time on top of the wifi spectrum (invaluable in poor connectivity troubleshooting when overlapping wifi doesn’t seem to be the cause).
4. Bluetooth identification: LE advertisement listening with standard bluetooth, full promiscuous mode in LE and classic bluetooth with Ubertooth.
5. Bluetooth source hunt: Track LE advertisement sources or iBeacons with the telemetry window.
6. iBeacon advertisement: Advertise your own iBeacons.
7. Remote operations: An agent is included that provides all of the GUI functionality via a remote agent the GUI can talk to.
8. Drone/Rover operations: The agent can be run on systems such as a Raspberry Pi and flown on a drone (its made several flights on a Solo 3DR), or attached to a rover in either GUI-controlled or autonomous scan/record modes.
9. The remote agent is JSON-based so it can be integrated with other applications.
10. Import/Export : Ability to import and export to/from CSV and JSON for easy integration and revisualization. You can also just run ‘iw dev scan’ and save it to a file and import that as well.
11. Produce Google maps when GPS coordinates are available for both discovered SSID’s / bluetooth devices or to plot the wifi telemetry over time.
12. Integration with Elasticsearch to feed wireless and optionally bluetooth scan data into Elastic Common Schema compliant indices.
Let’s see how this tool works. For this, we will be using Kali Linux as sparrow-wifi is available by default in its repositories. We will also be needing a wireless adapter that can monitor wireless packets. I am using ALFA AWUS036NHA adapter for this article.
Note that Sparrow-frim needs SUDO root privileges to work.
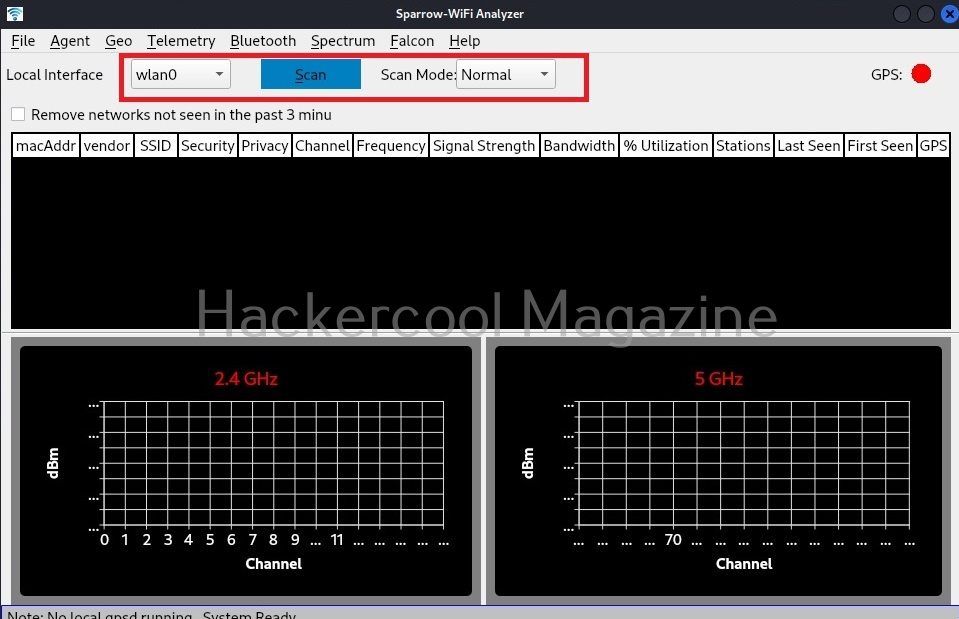
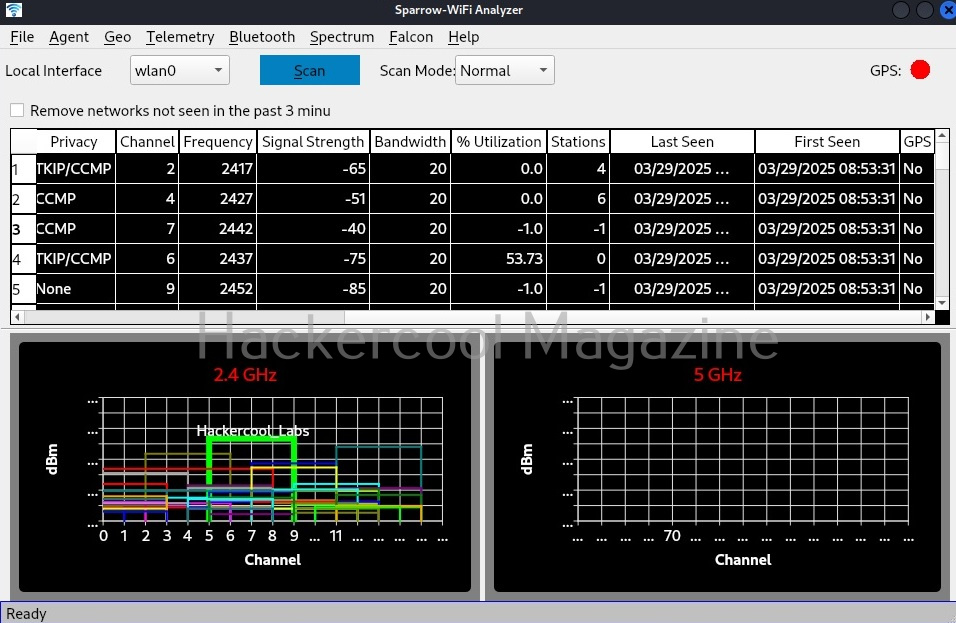
This is how the interface of sparrow-wifi looks.
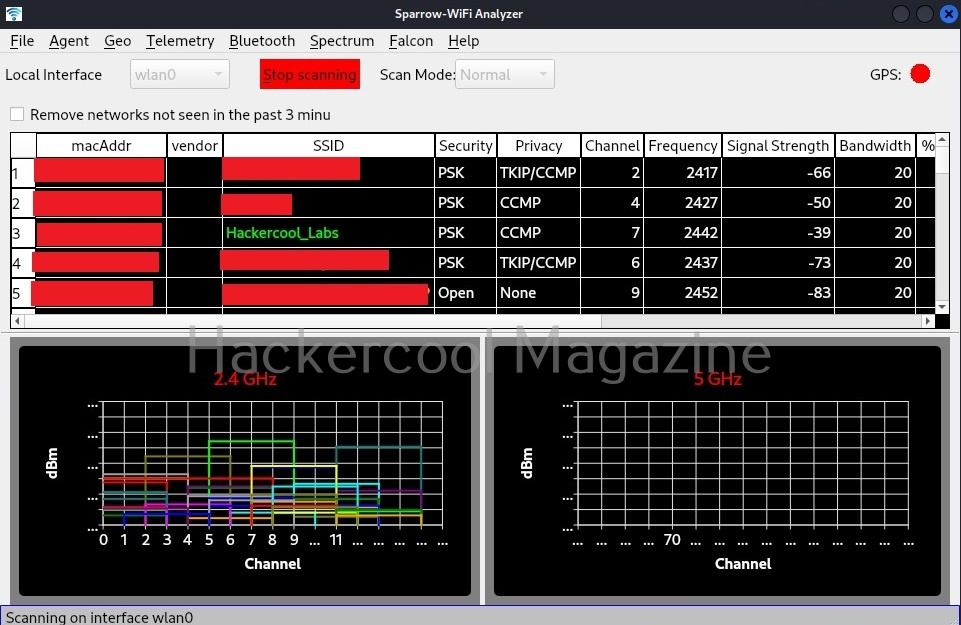
To start scanning for wireless networks click on “scan” button.
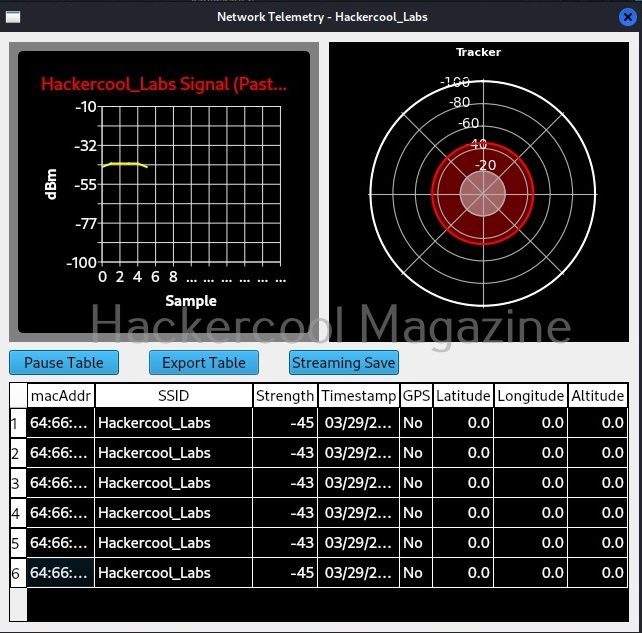
It will display the available wifi networks in 2.5ghz and 5ghz frequencies separately. From the telemetry menu, you can see the telemetry information about any wireless access point. For example, let’s see telemetry of target network “Hackercool_Labs”.
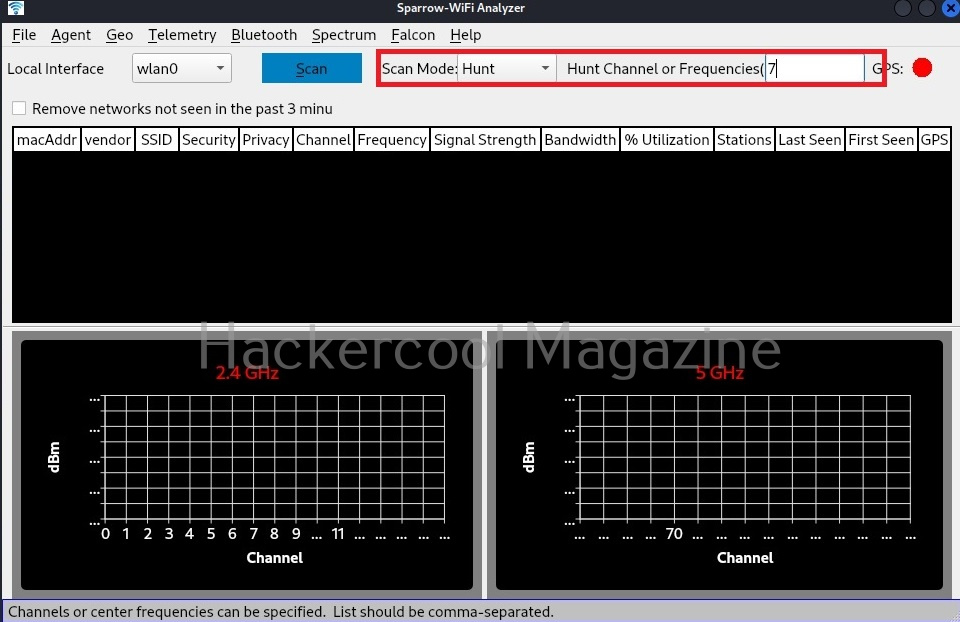
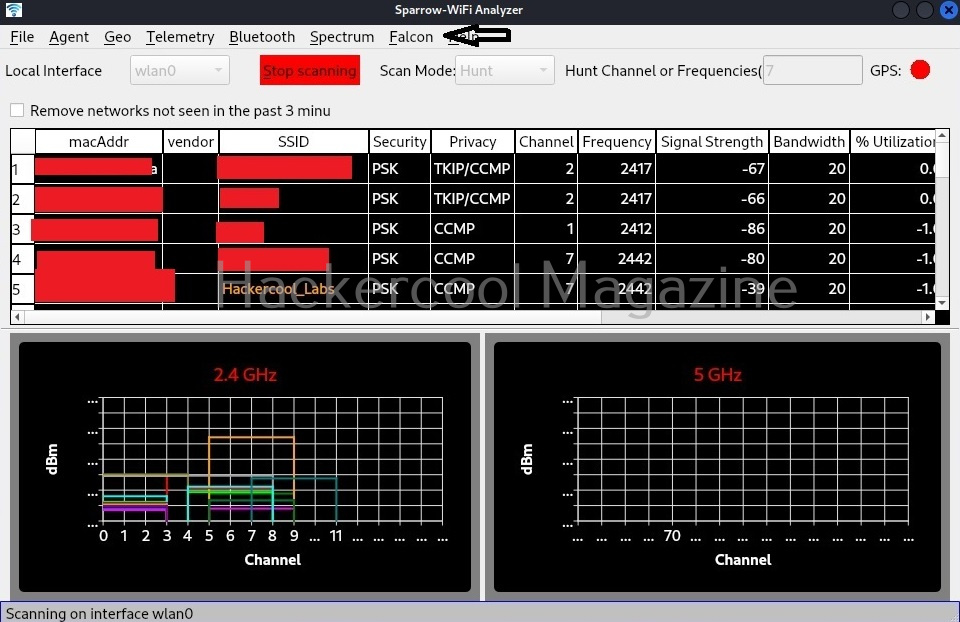
As you have already read at the beginning of this article, Sparrow-wifi has a hunt mode in which multiple samples per second are grabbed and used to track a wifi source.
Recently they added a new Falcon Plugin to this tool. Falcon provides the following features.
- aircrack-ng integration which allows for the enumeration of hidden SSIDs
- client station enumeration
- client station probed SSID enumeration
- client station connected access point and channel
- deauthentication right-click capabilities (single and continuous, targeted and broadcast)
- WEP IV captures
- WPA password hash capture and hash capture detection
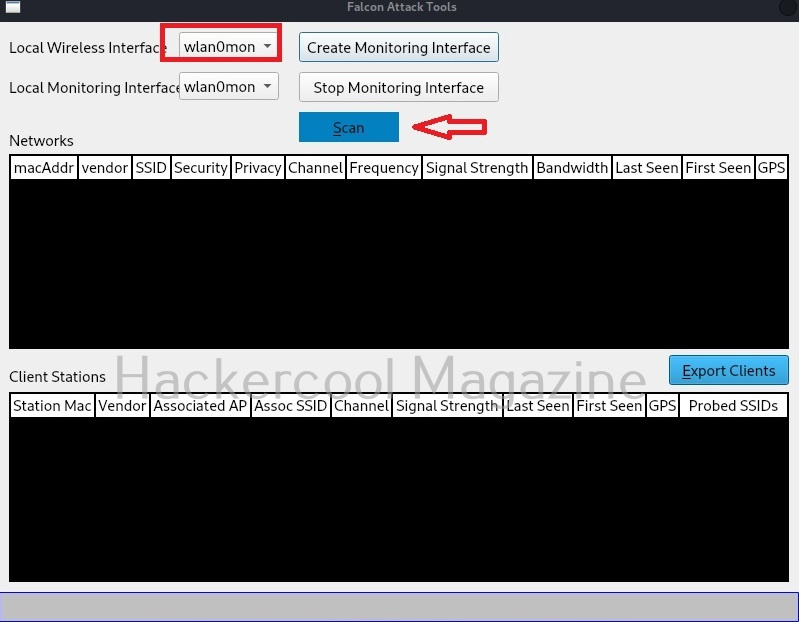
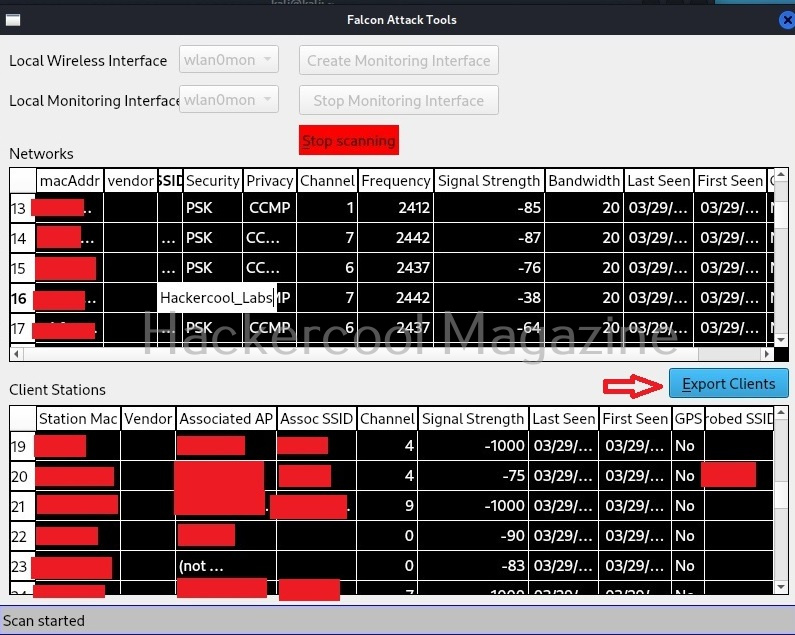
Falcon Plugin can be accessed from Falcon menu as shown in the above image. First, let’s enable monitoring mode on this tool by clicking “Create monitoring interface” button.
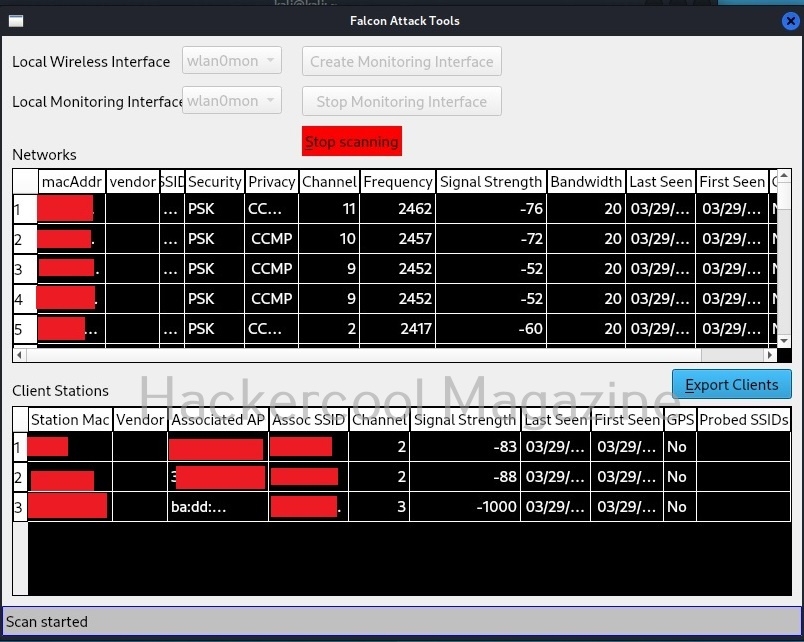
Immediately, all available wireless access points and clients are displayed. You can export clients to a CSV file using the “Export clients” button.
Select a wifi access point to target. For example, I select “Hackercool_Labs” as shown.
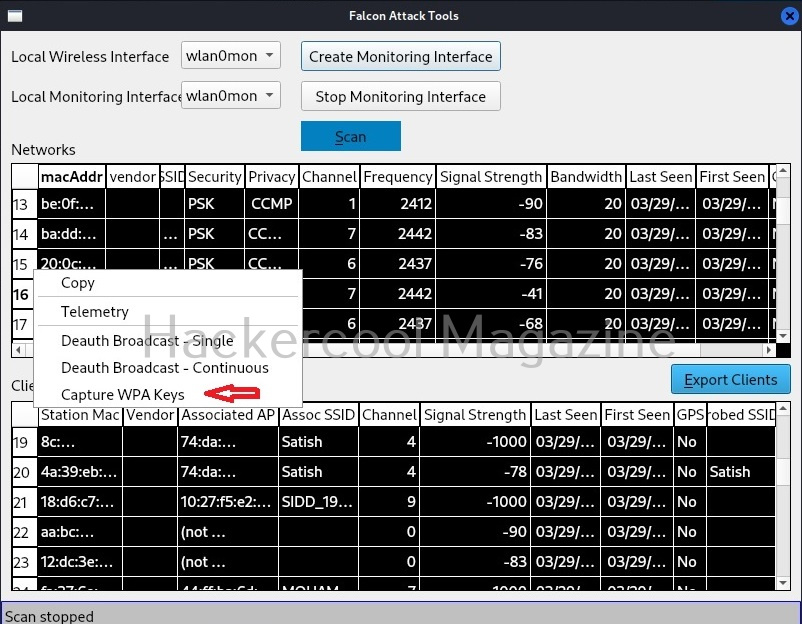
Stop the scan. Right clicking on the selected wifi network opens a menu which contains the following options.
- Copy
- Telemetry
- Deauth Broadcast-single
- Deauth Broadcast-continuous
- Capture WPA key.
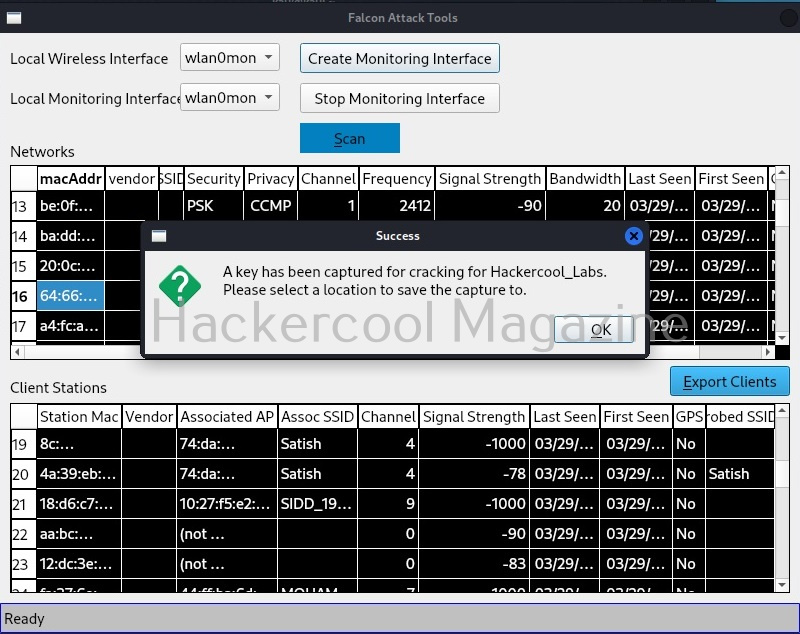
Let’s select “Capture WPA keys”. After selecting this, you can once again right click on the target access point and select any deauth broadcast. What this does is it with deauthenticates all the clients connected to our access point. Why are we doing this? This will force all the clients to connect to our access point again and hence we get a WPA handshake. Once a key is captured, sparrow wifi will display a message as shown below.
You can save it to the location you want.
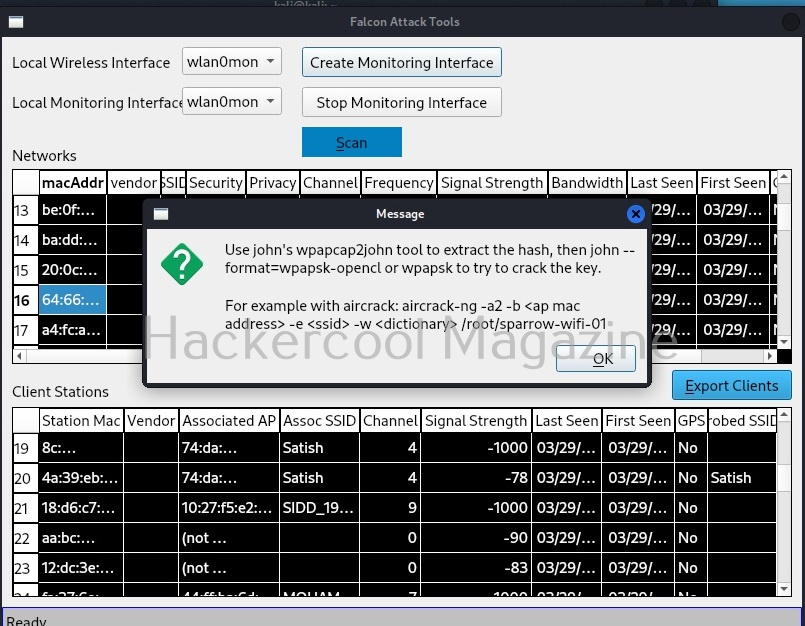
Then, it will display information on how to crack the key. You can use aircrack or Cowpatty to crack the passphrase.
That’s all about sparrow-wifi. Next, learn about airgeddon, a multi purpose wireless auditing tool.
Follow Us