Hello aspiring ethical hackers. In this blogpost, you will learn about WPScan, a tool used to perform WordPress vulnerability assessment. WordPress is one of most popular Content Management system (CMS) WPScan is a black box WordPress vulnerability scanner that can be used to scan remote WordPress installations to find security issues and also for enumeration. Let’s se how it works. It is installed by default in Kali Linux and we are going to use the same for this tutorial. Now open a terminal and update our tool by typing command as shown below.
wpscan
To scan a WordPress website, all you have to give is the URL as shown below. For this blogpost, I am using a local installation of WordPress as target. Assign the target as shown below. The scan will start as shown below.
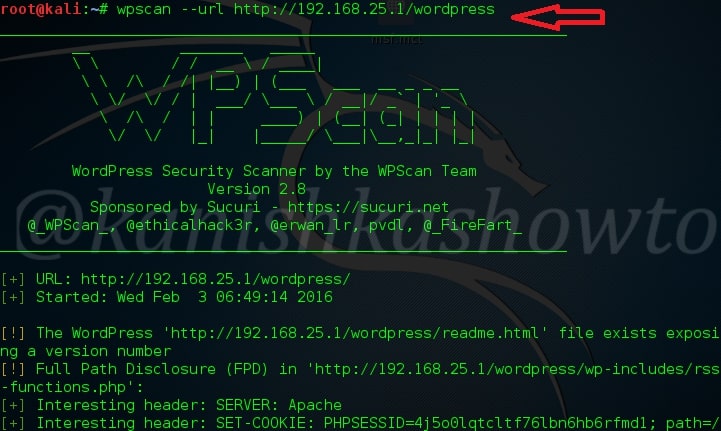
Here are the screenshots of result of this scan. As you can see we have 13 vulnerabilities in the present installation and the vulnerabilities are given below.
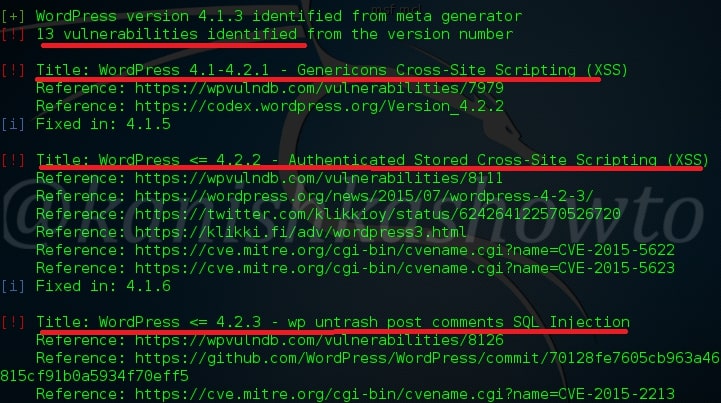
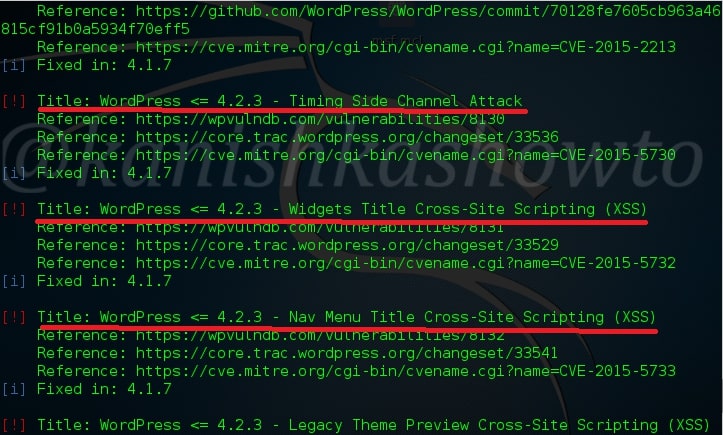
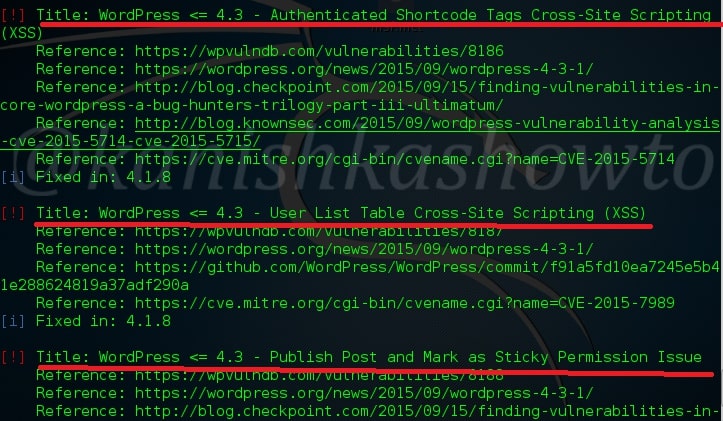
One of the easiest ways to hack a WordPress site is to exploit the plugins installed in the target as most of the WordPress vulnerabilities nowadays exist in the plugins installed on it. So it is very important to enumerate the plugins installed on our WordPress target. We can enumerate the plugins using the “enumerate” option as shown below.
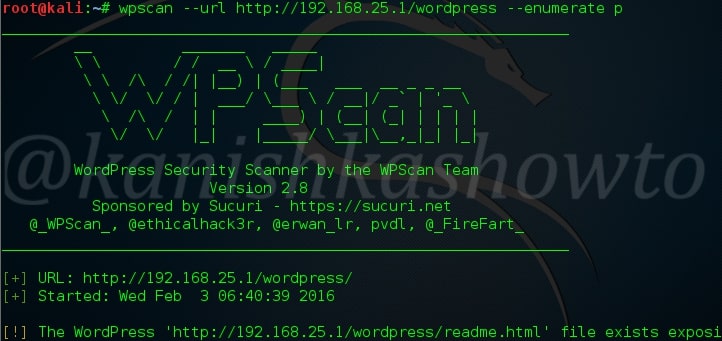
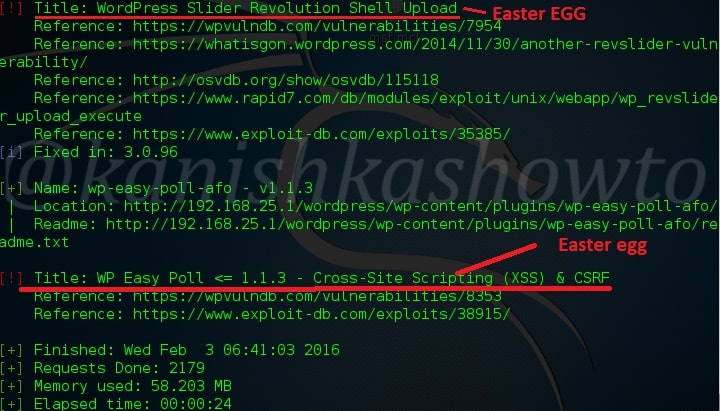
The scan result will be as shown below.( And there you have the first Easter egg). So totally we found four plugins. The first one is Ajax Load More Plugin. As the red exclamation mark shows, it is vulnerable.
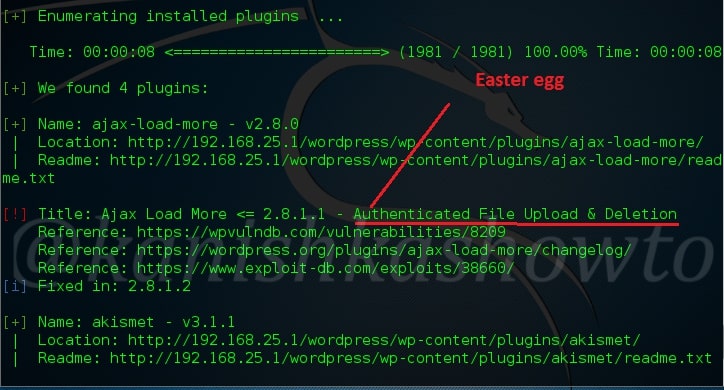
The second plugin is the vulnerable version of Akismet.
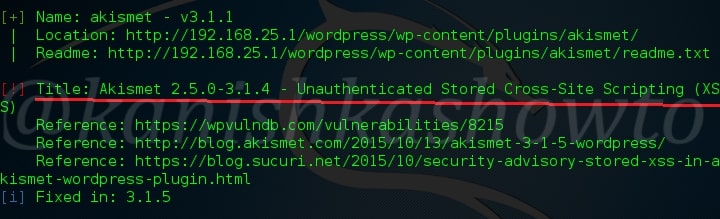
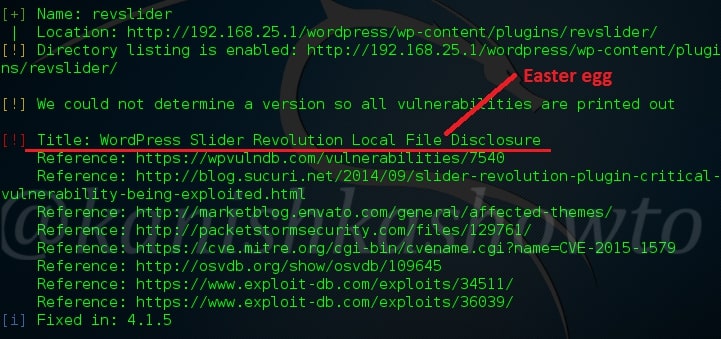
The third vulnerable plugin is the WordPress Slider revolution plugin. We will see more about this in our next blogpost.
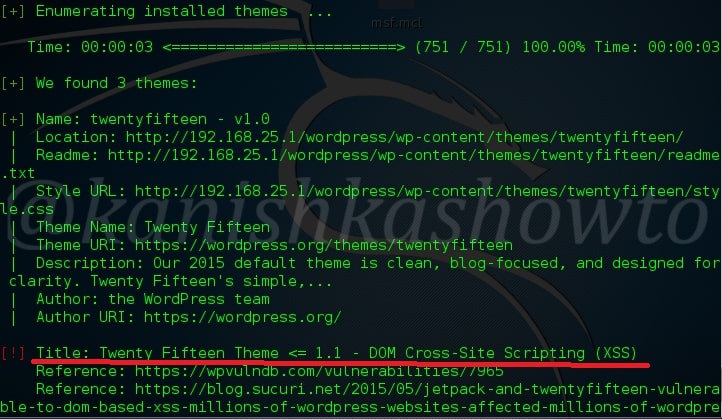
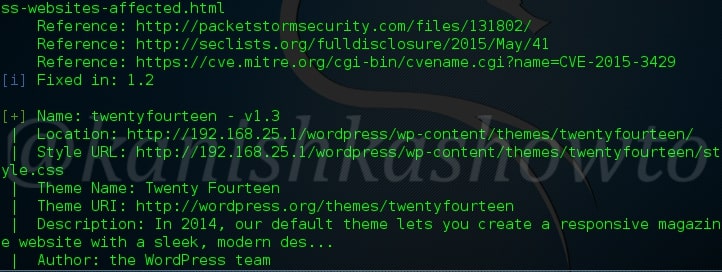
Another important aspect to find vulnerabilities in the WordPress is its theme. Now let’s enumerate the theme as shown below. The vulnerabilities present in the theme are given below.
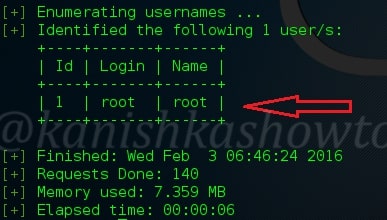
After that let’s enumerate the users in our remote target as shown below.
We can see that the only username in our target. That’s WPscan for you. Hope it was helpful to you and wait for the sequels.


[…] Evening friends. This howto is a direct sequel to our previous howto WordPress vulnerability assessment with WPscan, so I suggest you go through that how to first and look out for the Easter eggs. This howto is […]
[…] The first question is how will we know the username. Just go through one of our previous howto : WordPress vulnerability assessment with WPSCAN. The tool gave use a hint that username is “root”. Now we will set the username as […]