Hello, aspiring ethical hackers. In our previous blogpost, you have learnt how to crack a WPA/WPA2 passphrase with aircrack. In this article, you will learn about another such tool cowpatty.
Cowpatty is a WPA-PSK, WPA2-PSK auditing tool that can be used to identify weak passphrases of an SSID with WPA, WPA2 enabled. Cowpatty does offline cracking of passwords and as it works offline, it needs packet capture file (pcap) with WPA handshake captured.
Let’s see how this tool works. For this, we will be using Kali Linux as cowpatty is installed by default on it. We will also need a wireless adapter that can monitor wireless packets. I am using ALFA AWVS036NHA adapter for this article.
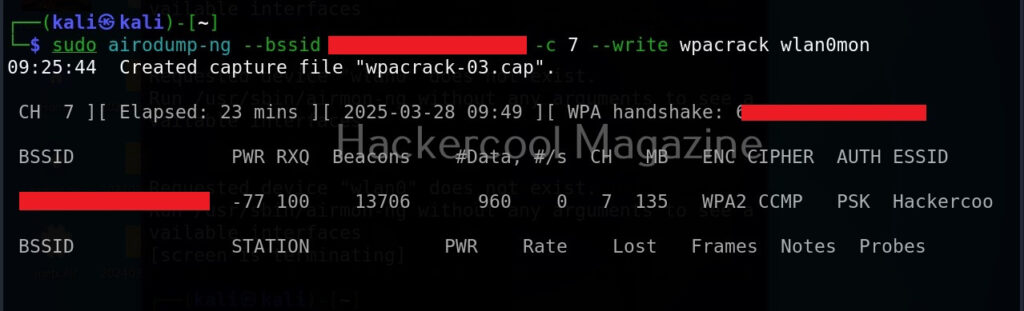
The role of Cowpatty in Wi-Fi auditing starts after the wireless networks data is captured in a PCAP file. Notably, this data should include a WPA handshake, a process where a client connects to the wireless access point with WPA/WPA2 enabled. This can be done with airodump-ng (a tool included with aircrack) or kismet or Fern wifi cracker.
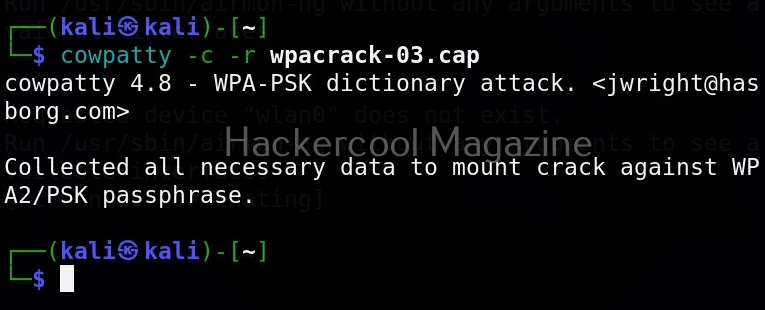
Before beginning to crack the passphrase, cowpatty can be used to check if the packet capture file has all the necessary data to start cracking against WPA2?PSK passphrases. For example, here we are trying to capture wireless traffic of a network named “Hackercool_Labs” and saving the capture data to a file named “wpa-crack-03.cap.
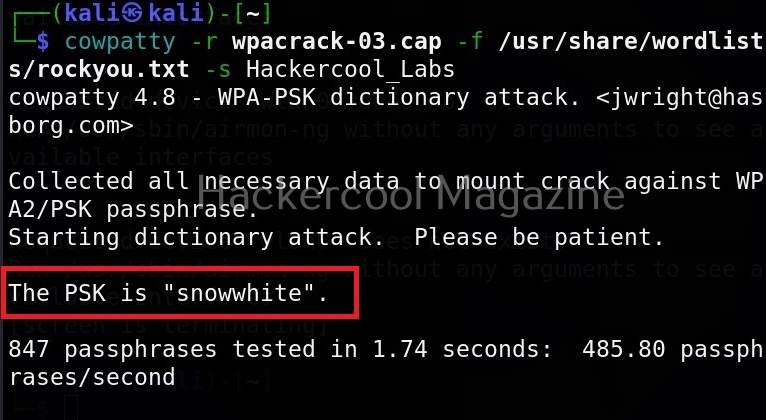
Once all necessary data is collected, we can crack the WPA2 passphrase as shown below. As you can see, the passphrase is “Snowwhite”.
Here is the explanation for the options specified in the above image.
-r: This option is used to specify the the packet capture file.
-f: path to the wordlist to be used for dictionary cracking (here we are using rockyou.txt).
-s: SSID of the wifi access point you are trying to crack.
If cowpatty succeeds is cracking WPA2 passphrase, it means the wifi security is weak and the password needs to be changed immediately.
Next, learn how to crack any WIFI password automatically with Besside.
Follow Us