Hello, aspiring ethical hackers. In this blogpost, you will learn about dirbuster, a tool used to scan web directories and file names on web application servers. Dirbuster is written in Java and can be installed on Linux systems. Almost all pentesting distros include this in their tools list. For this tutorial, we are going to use Kali Linux. Dirbuster can be started on Kali by using the command as shown below.
dirbuster
Typing this command will open a GUI window as shown below.
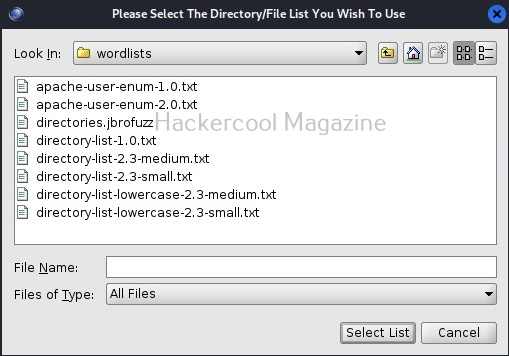
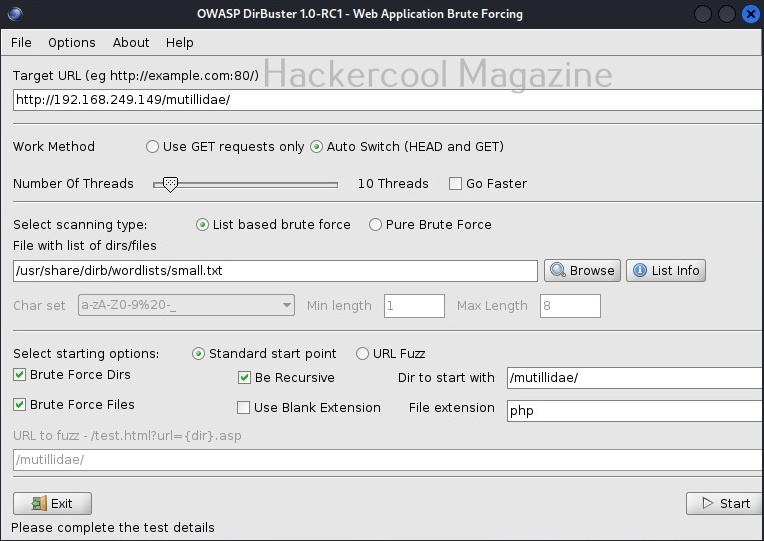
Here, you can configure all the options required to scan the target web server. For this tutorial, we will be using Metasploitable 2 as our target. Any directory scanning and fuzzing tool is as good as the wordlist it uses while scanning for hidden directories and files. Dirbuster provides its own set of wordlists which are located in “usr/share/dirbuster/wordlists” directory in Kali.
Unlike other wordlists, these wordlists are created using a different approach. These lists are created from scratch by crawling the internet and making a collection of the all the files used by all developers. It comes with a total of 9 different lists. If all these lists fail, dirbuster also has brute force option.
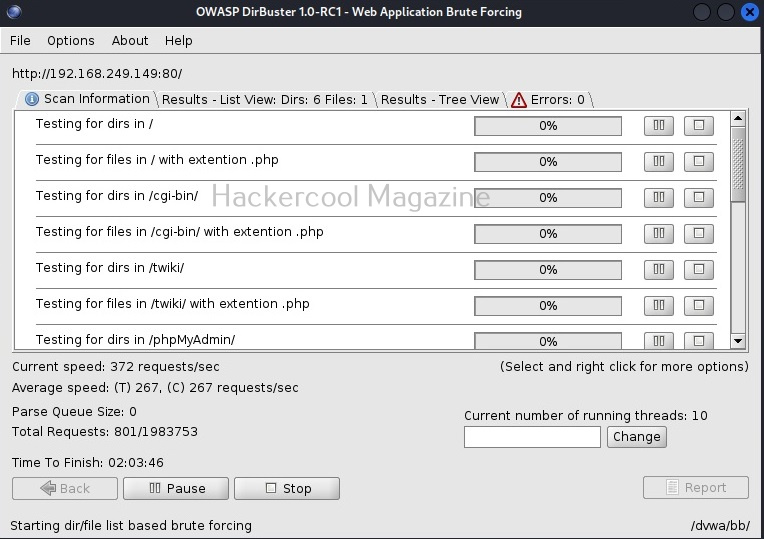
The scan starts. Depending on the size of the target web server, finishing time may vary. The progress of the scan will be displayed in the “scan information” tab.
As the scan continues, you can see the results in different views. The “List view” shows all the detected directories and files by dirbuster in the form of a list.
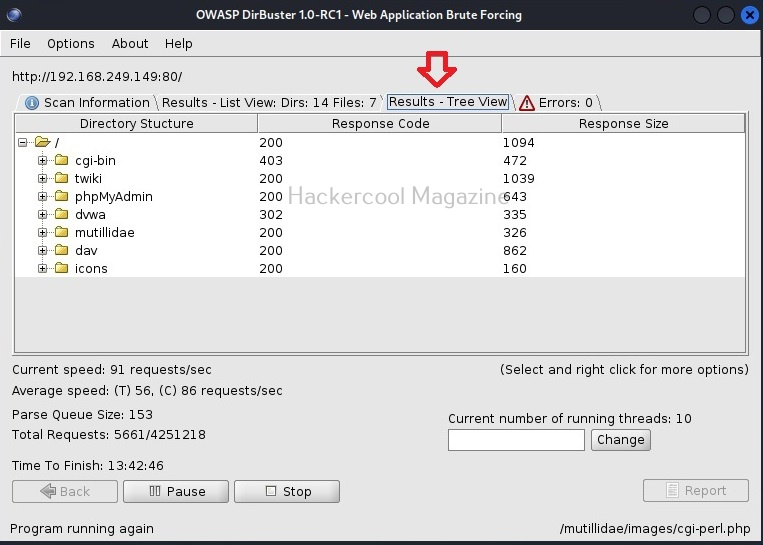
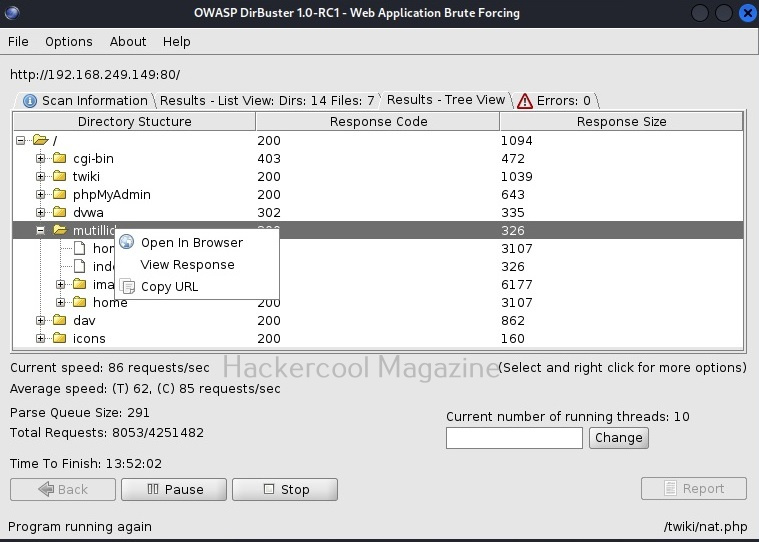
You can also see the results of the scan in the form of “Tree view” that enables us to gain understanding about the target web server directories structure.
You can right click on the detected directories for more options as shown below.
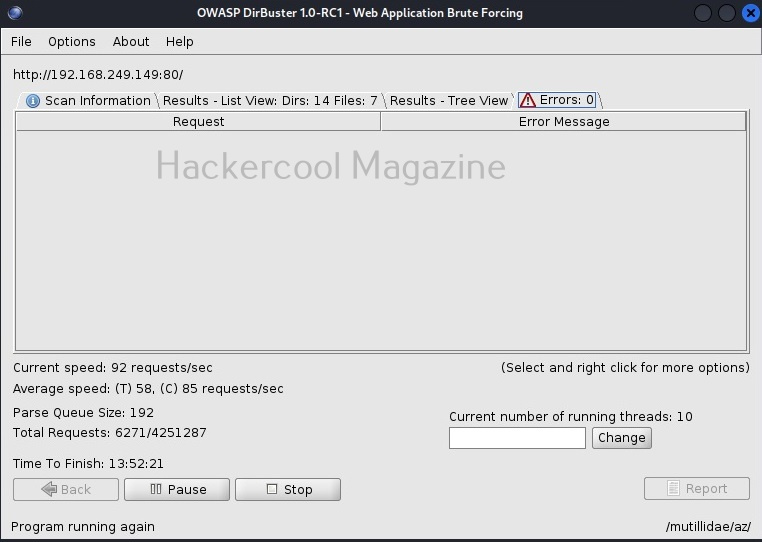
If dirbuster faces any errors while scanning directories, they are displayed in the “errors” tab.
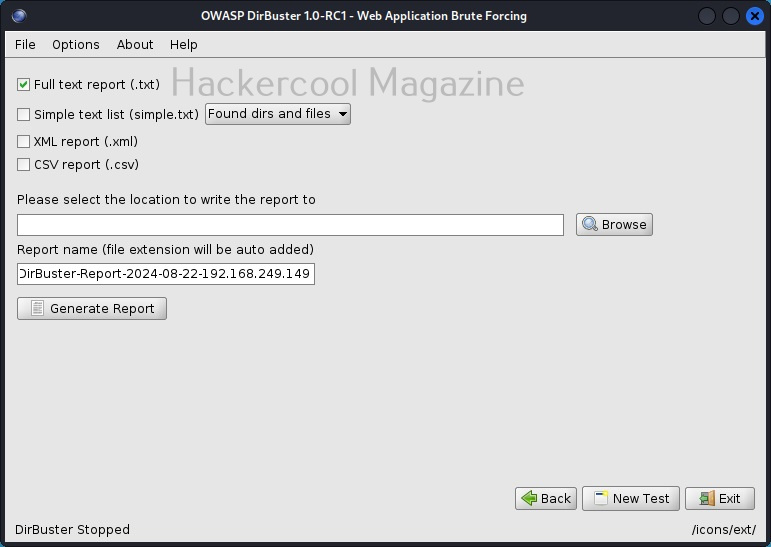
You can wait until the scan finishes or you can even end the scan by hitting “stop” button. Once you do that, dirbuster will prompt you to save the result of the scan as shown below.
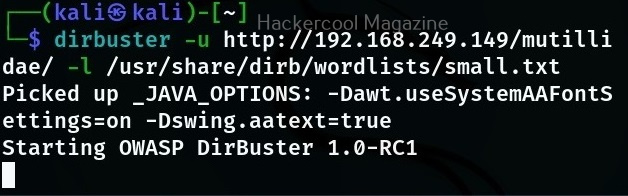
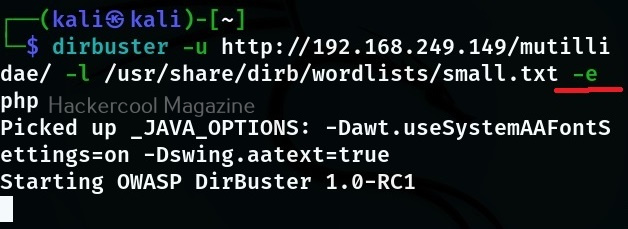
You can also use dirbuster by specifying its options through command line. The basic options to set are the URL and the wordlist. These can be set with ‘-U’ and ‘-r’ options respectively.
Then, all you have to do is click on “Start”. If you want to find files with a particular extension with dirbuster the option is ‘-e’. For example, let’s say you want it scan for files with “php” extension here is the command,
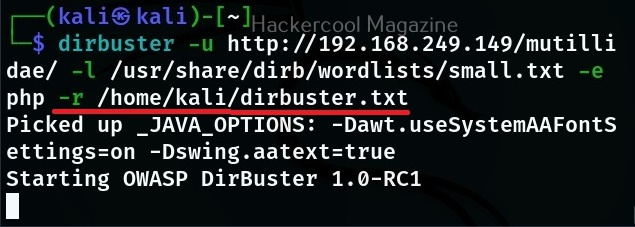
To save the output of dirbuster scan, use command line option ‘-r’.
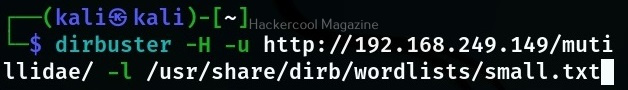
Headless mode (-H)
You can run dirbuster in headless mode without GUI option as shown below.
Follow Us