Hello, aspiring ethical hackers. In this blogpost you will learn about DoS attack. In April 2007, the government services, financial institutions and various media outlets of Estonia, a nation in eastern Europe were hit with a massive Denial of service attacks. The attack that almost crippled Estonia (almost all services of Estonia are based only online) coincided with the relocation of “Bronze soldier of Tallinn” a world war II monument which Russia objected to.
What is DoS attack?
DoS or Denial-of-Service attack is an attack that makes a website, service, network or software inaccessible to legitimate users. For example, imagine you are a user of Gmail. When you are trying to access Gmail to check an important mail sent from your office, you are unable to reach the servers of Gmail as there is a DoS attack on Gmail servers.
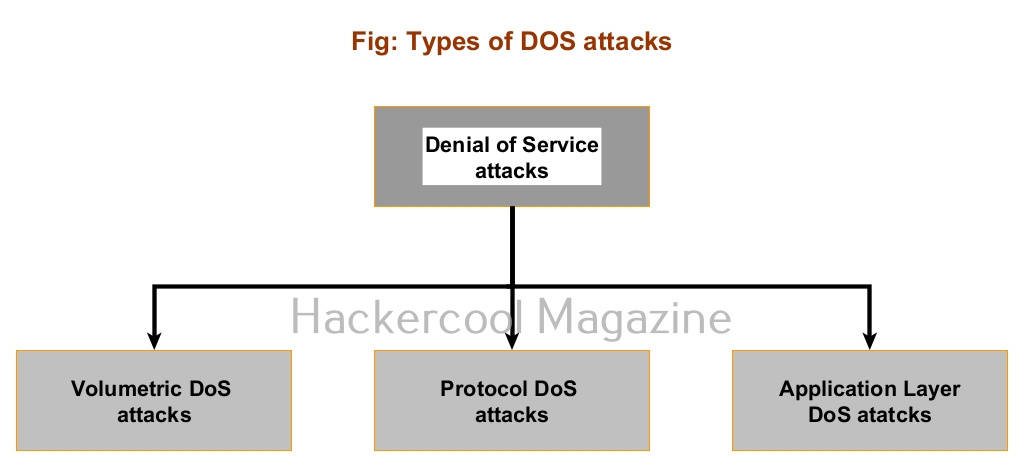
Types of DoS attacks
DoS attacks can be classified into three types. They are Volumetric attacks, Protocol attacks and Application layer attacks.
Volumetric attacks
In volumetric attacks, the bandwidth of the target network or service is exhausted, thus denying any legitimate users access to bandwidth. The magnitude of the attack is measured in bits-per-second (bps). Examples of these types of attacks are Ping of Death attack, UDP Flood attack, ICMP flood attack and Smurf attack.
1. Ping Of Death attack:
According to RFC791 IP, the maximum size of the packet should not exceed 65,535 bytes. In the Ping of Death attack, an attacker sends an oversized packet of size more than the prescribed limit with a ping request. (For example, a packet of size 65,550 bytes). The target system may crash while trying to reassemble this packet.
2. UDP Flood attack:
In this type of attack, an attacker sends a number of spoofed UDP packets to random ports of the target system. Target server tries to check for these applications (some of which are nonexistent) repeatedly. This causes exhaustion of the bandwidth in use thus replying to legitimate connections with a ICMP destination unreachable message.
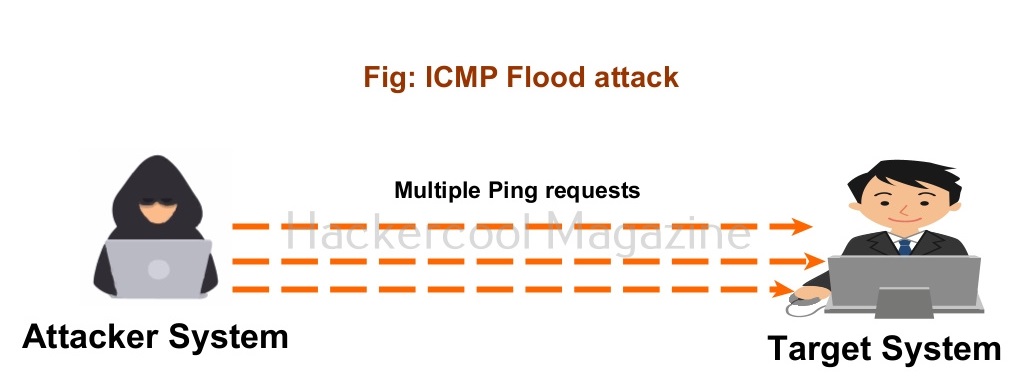
3. ICMP Flood attack:
In the ICMP flood attack, the attacker sends a large volume of ICMP request (ping) messages to the target server either from a single IP or multiple IP addresses. The target server is bound to reply to these packets with a ICMP echo reply message thus exhausting the bandwidth.
4. Smurf attack:
In a smurf attack, the attacker sends ICMP echo request message to the broadcast network address spoofing the IP address of the target server. This makes all the devices in the network to reply to this echo request message with a echo reply message. Since the address of the target server is used in the echo request message, all the devices reply with this IP thus, making the target server inaccessible to the legitimate users.
Protocol attacks
In this type of DoS attacks, instead of exhausting the bandwidth, attackers try to exhaust resources available on the target network or website thus making it inaccessible to the legitimate users. Examples of these DoS attacks are SYN Flood attack, ACK Flood attack, TCP connection flood attack, Fragmentation attack and RST attack. This DoS attack is measured in Packets-per-second (pps).
1. SYN Flood attack:
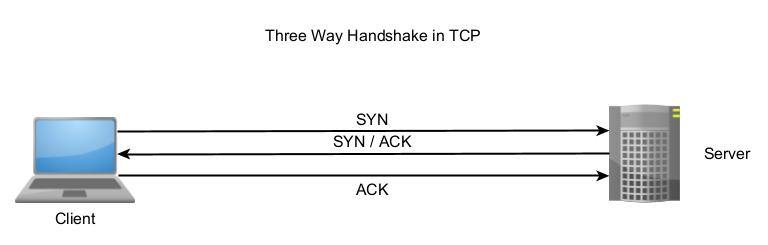
In our blogpost on port scanning techniques, you learnt about the 3-way handshake.
In this attack, attackers exploit this 3-way handshake. How? The attacker sends multiple TCP SYN requests to the target server. When the target server responds to these SYN requests with a SYN/ACK packet, the attacker never sends a ACK message in response. This creates a partially open connection. By default, the target server or machines should track a partially opened connection for 75 seconds.
This is known as SYN flood. In these 75 seconds, the attacker can send large volume of SYN requests thus overloading the target system which eventually makes it inaccessible to the legitimate users.
2. Fragmentation attack:
Network or IP layer of OSI model allows packet fragmentation in order to overcome the problem of any higher-level protocol creating a packet larger than the size any particular local network supports. Attackers exploit this feature to send a large number (1500+bytes) of fragmented packets to the target server. The size of each fragment is usually reduced and small packet rate is used. This forces the target server to utilize a large number of resources to reassemble these fragmented packets thus causing DoS attack.
Application Layer attacks
In this type of DoS attacks, attackers exploit any vulnerabilities in the target server to prevent its access to the legitimate users. These vulnerabilities include cross site scripting, CSRF, File upload but most probably a Buffer overflow vulnerability. The magnitude of this attack is measured in requests-per-second (rps). Examples of this attacks include HTTP flood attacks and Slowloris attack.
1. HTTP GET/POST attack:
Browsers connect to the web server using HTTP requests. These requests can be either HTTP GET or HTTP POST. In this type of attack, attackers exploit these requests to perform DoS attacks.
In a HTTP GET DoS attack, attackers use time delayed HTTP headers to exhaust resources of webserver whereas in HTTP POST DoS attack the attacker sends HTTP requests with complete headers and without a message body or an incomplete message body.
Follow Us