Hello, aspiring ethical hackers. In one of our previous blogposts, you studied in detail about website footprinting and different methods used to gather information about a website. In it you have learnt that directory scanning and subdomain enumeration is one of the techniques used to gather information about a website. In this blogpost you will learn about a tool named gobuster which can do both.
Gobuster is a tool built in Go programming language that can brute-force URIs (directories and files) in websites, DNS subdomains, virtual host names on target web servers, open Amazon S3 buckets, open Google cloud buckets and TFTP servers. It is present by default in the repositories of Kali Linux and can be installed by just typing the command as shown below.
Once installed, gobuster can be used using the same command.
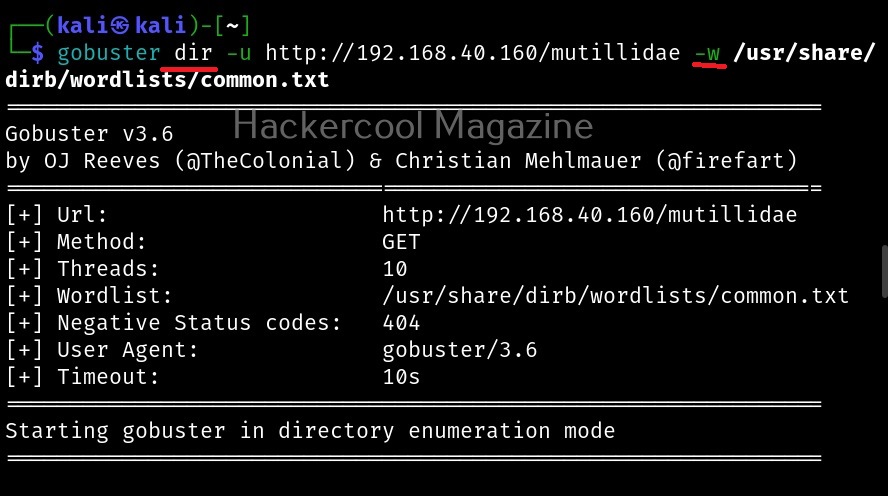
There are different modes in gobuster tool for different operations. No matter what mode you use, since Gobuster is a brute-forcing tool it needs a wordlist. Let’s see how to scan web directories first. For this tutorial, we will be using Mutillidae as our target. It is installed by default in Metasploitable 2. See how to install Metasploitable 2 in VirtualBox and see how to create a web application penetration testing lab.
Let’s see how to scan directories with Gobuster.
Let’s explain the options here.
dir – to scan for directories.
-u: URL to be scanned.
-w: wordlist from which earlier are scanned.
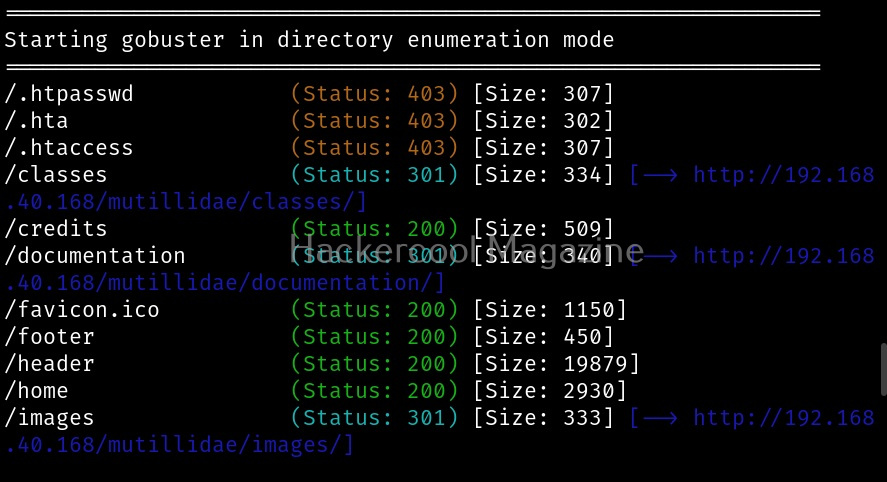
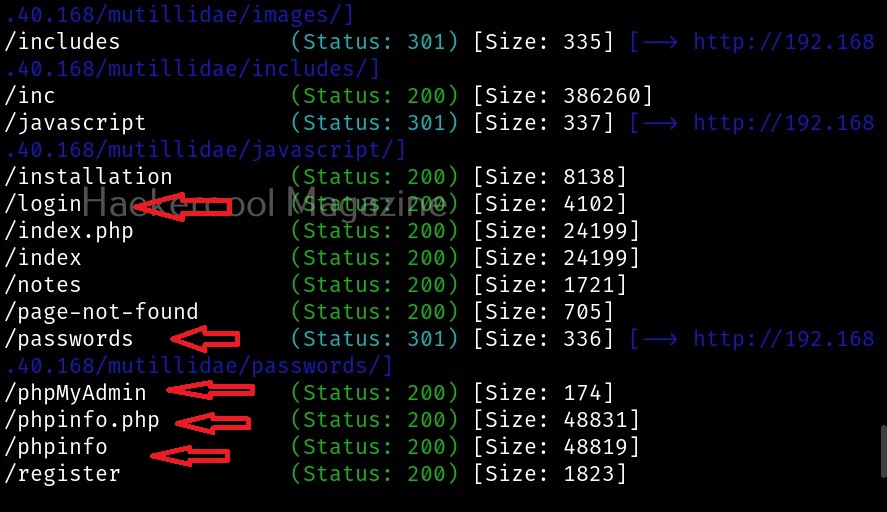
Here is the result of this scan.
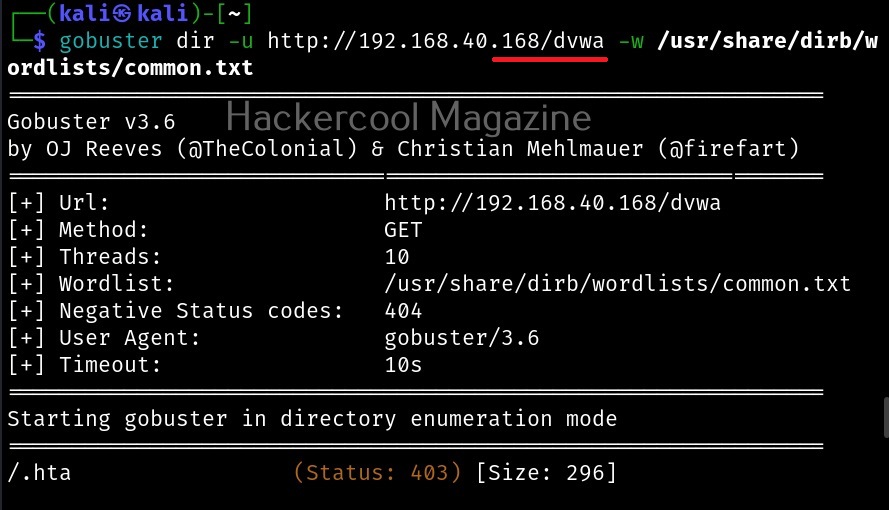
You can see that gobuster found some interesting files along with a file named “passwords”. As an exercise, scan DVWA also as it is also installed by default on Metasploitable 2.
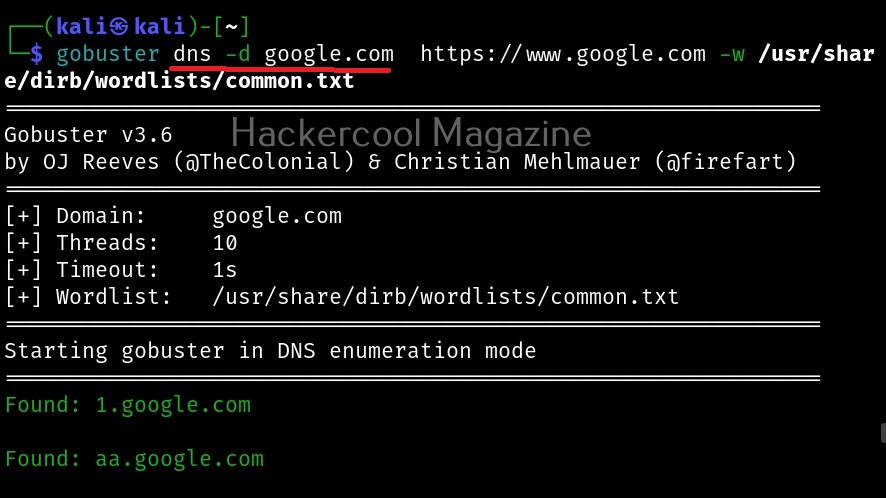
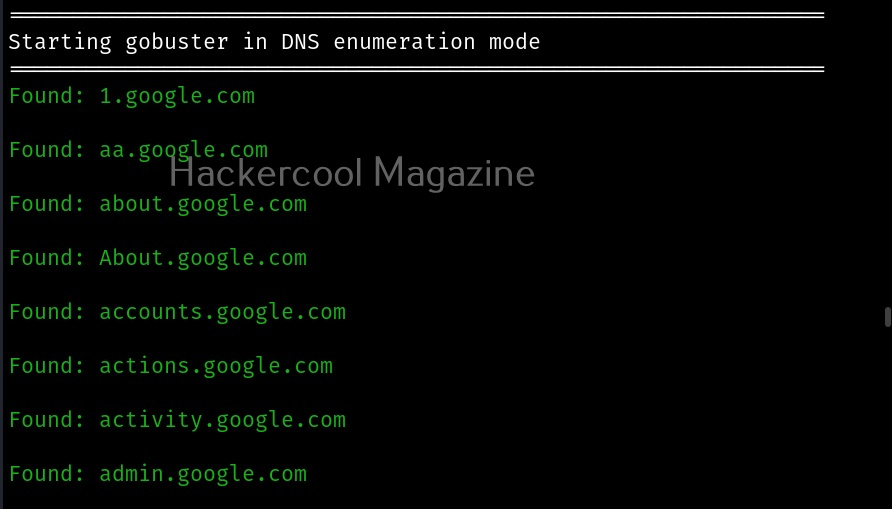
Now, lets see how to scan for subdomains using gobuster. We have to just change the “dir” option to “dns”.
Learn how to perform directory scanning with dirb.
Follow Us