Hello, aspiring ethical hackers. In this blogpost, you will learn about a tool called Lynis, the security auditing and hardening tool for UNIX based systems like Linux, macOS, BSD and others. It performs an in-depth security scan to test security defenses and provide suggestions for further system hardening.
This tool audits the following features on the system.
- General system information.
- System tools.
- Operating system.
- Boot and other services.
- Kernel vulnerabilities.
- Memory and processes.
- Users, groups and authentication
- Kerberos
- Shells
- File systems
- USB devices
- Storage
- NFS
- Name Services
- Ports and packages
- Networking
- Printers and Spool
- Email and messaging software
- Firewalls
- Web servers
- SSH and SNMP
- Databases
- PHP (in web server)
- Logging and log files
- Insecure services
- Banners
- Scheduled Tasks
- Accounting
- Time and synchronization
- Cryptography
- Virtualization
- Containers
- Security frameworks
- System tools and malware
- File permissions etc.
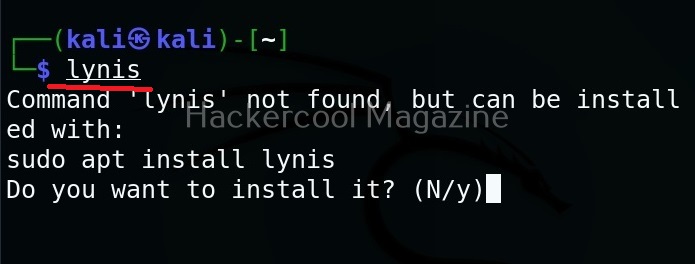
Let’s see how to run Lynis for the first time. For this, we will be using Kali Linux. It can be installed on Kali as shown below.
After the installation is successful, run the command shown below to run it to audit the entire system.
lynis audit system
It runs as shown below.
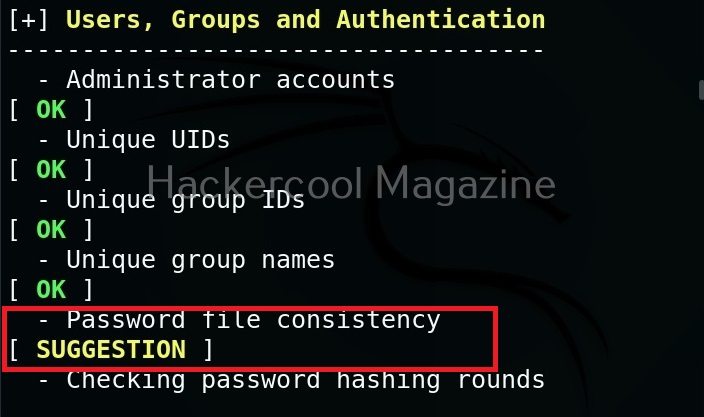
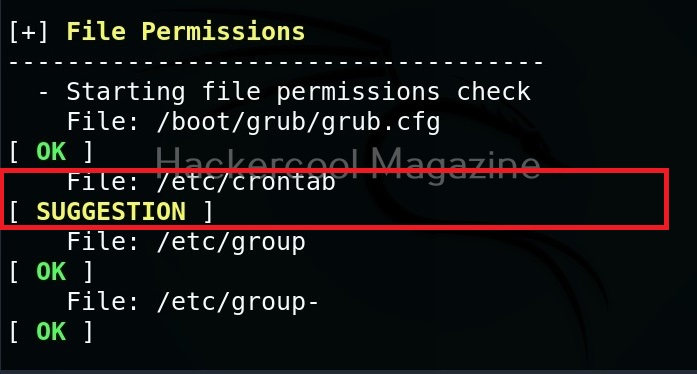
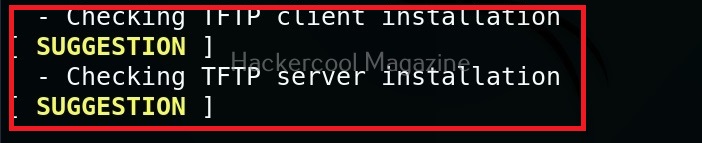
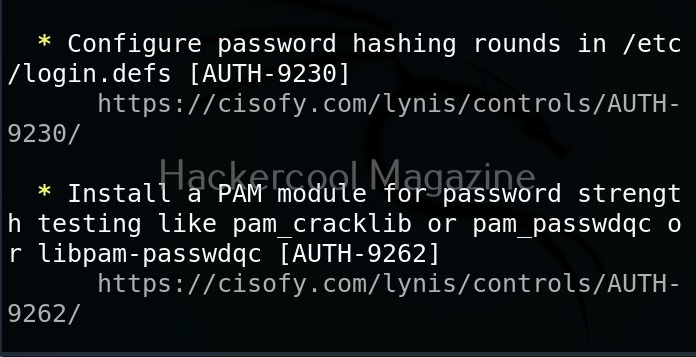
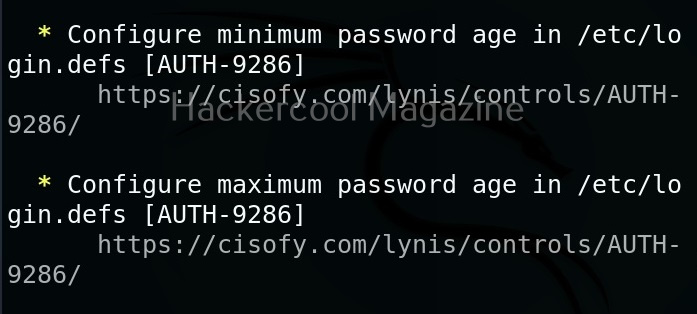
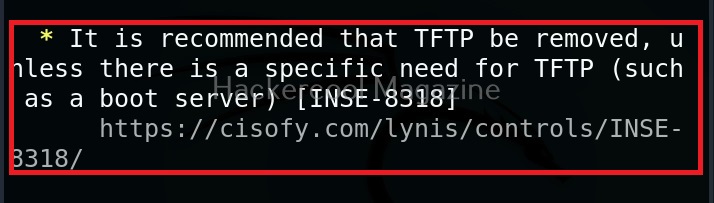
While auditing, wherever there is scope for hardening, lynis adds a suggestion as shown below.
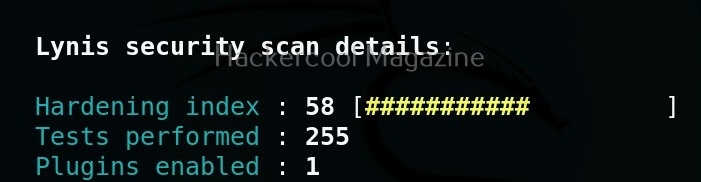
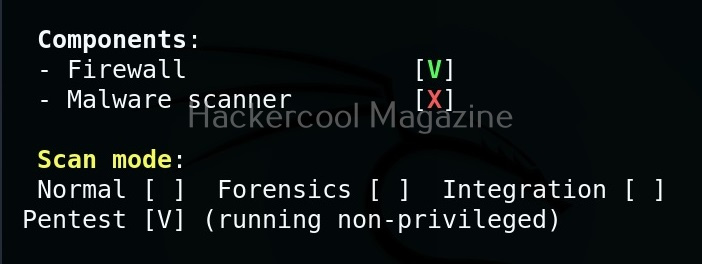
After the entire system is audited, Lynis provides summary of the entire audit as shown below.
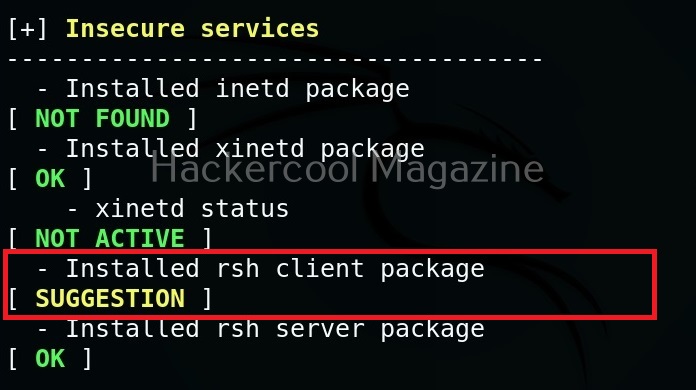
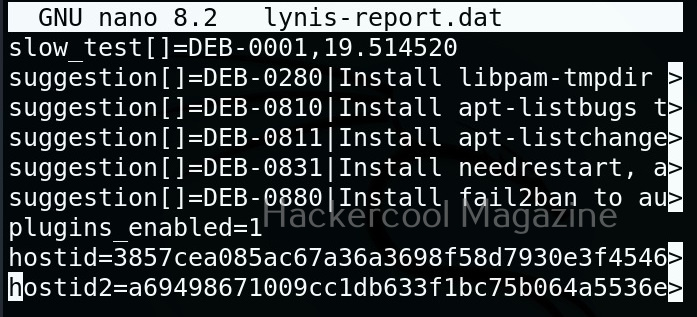
Below the summary, you can find each suggestion as shown below.
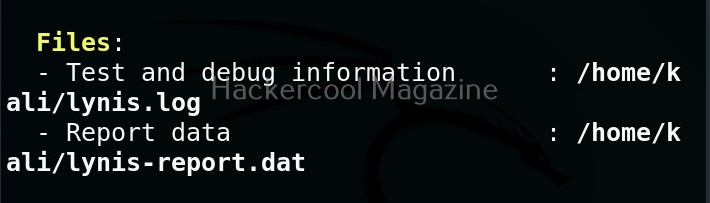
You can harden your system based on these suggestions. You can also find this information in the log reports of Lynis.
Follow Us