Hello aspiring Ethical Hackers. In this blogpost, you will learn about steganography. Before you learn what is it, you need to learn why are we learning about it. In Feb 2023, Red Eyes Hacking Group (APT37) used a jpg image as attachment in one of their spear phishing email. When victims clicked on this image, it triggered an exploit that ran shellcode on the victim’s computer to download and execute a malicious payload that is stored within the jpg file mentioned above. But how was the malicious payload was hidden inside the jpg image?
What is Steganography?
It is an art or technique of hiding secret or any precious information inside something that looks common & ordinary. This information is hidden in such a manner that its presence is not evident to the human inspection. The word stegano graphy came from Greek word steganographic, that is combination of words steganos (meaning hidden or concealed) and graphia (writing).
In ancient and medieval times, kings used steganography to forward messages secretly. Greeks were the fist to use it. Coming to modern times, hackers are using it to hide malicious code in images, text, files, audio, video film and any other medium that looks benign.
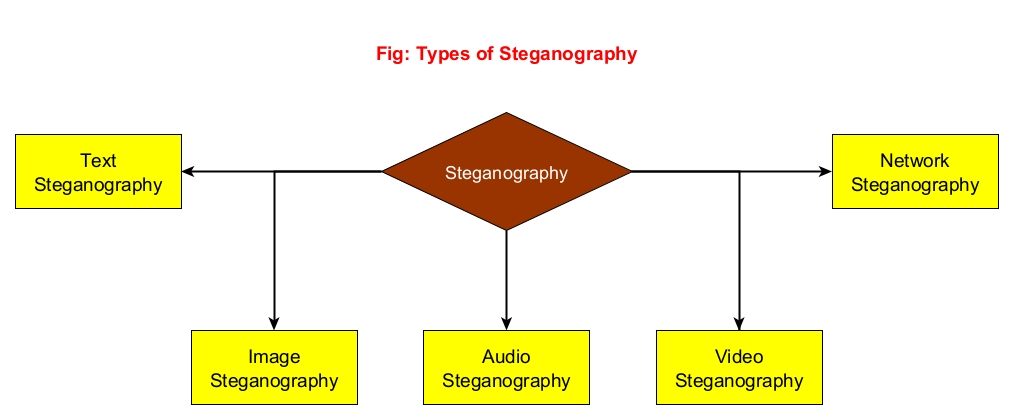
Types of Steganography
There are five types of stegano graphy. They are,
- Text stegano graphy
- Image stegano graphy
- Video stegano graphy
- Audio stegano graphy
- Network Stegano graphy
1. Text Steganography::
In text steganography, the secret information is hidden in a piece of text. For example, let’s say a text contains “Indians love Unity”. This may look like an ordinary or normal text. But just take the first letter of these three words. That becomes “ILU” a shortcut for I Love You message used by youngsters.
2. Image Stegano graphy:
As you might have already expected, when the secret information is hidden in an image (digital image) it is known as Image steganography.
3. Audio Steganography:
If the information we want to hide is hidden in an audio, it is known as audio steganography. Humans can hear sound that only contains certain frequencies. So, by altering the properties of audio like frequency, amplitude etc. secret messages can be hidden. However, to be able to receive and understand this secret information, the receiver needs to have smart listening devices to decipher the hidden information.
4. Video Steganography:
If the secret information is hidden in a video, it is called video steganography. A video is simply a representation of a sequence of consecutive images. So, we can say that this is an advanced version of Image steganography.
5. Network Steganography:
Considered to be more advanced and practically useful to Black Hat Hackers, in Network steganography information is hidden in network traffic. For example, it can be hidden in the TCP/IP headers etc.
Examples of Steganography attacks in hacking
- In September 2022, researchers at ESET discovered a previously unknown Threat actor they named Worok hiding malicious payload in PNG files.
- In 2019, researchers at Symantec observed a Russian cybersecurity group waterbug (also known as just the malicious) delivering a publicly known backdoor by hiding it in a WAV file.
- In the same year, security researchers at Cylance observed a hacking campaign that was delivering XMRIG Monero CPU miner by hiding them in WAV files.
- PLATINUM hacker group, that usually targets Governments of South Asia and South East Asia, embedded their malware commands in the HTML code of a website. They achieved this by encoding malware commands in a specific sequence of “TAB” and “SPACE” bar.
In future steganography is going to increase in cyber security.
Follow Us