Hello, aspiring ethical hackers. In our previous blogpost, you learnt in detail about packet sniffing and packet analyzing. A sniffer or a packet analyzer plays a very important role in packet sniffing. In this blogpost, you will learn about a sniffer or packet analyzing tool called tcpdump.
tcpdump is an open-source data-network packet analyzer that runs under a command line interface. It works on almost all Unix-type operating systems like Linux, Solaris, FreeBSD, macOS etc. Tcpdump was written by Van Jacobson, Sally Floyd, Van Paxson and Steven McCanne in 1998 while working in Lawrence Berkely Laboratory Network Research group. Let’s see how to perform packet sniffing with tcpdump. For this tutorial, we will be using Kali Linux as tcpdump is installed by default on it.
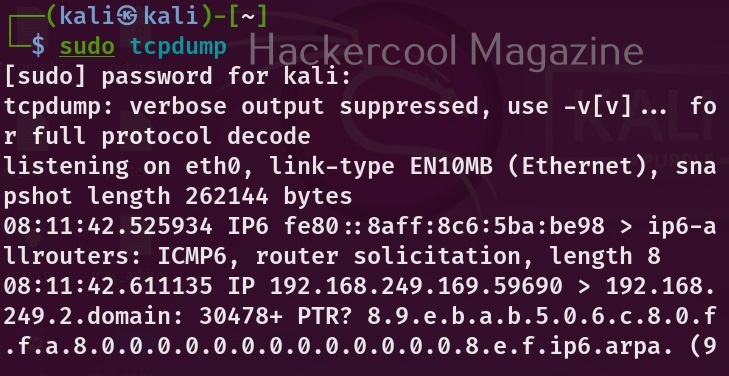
The command to start sniffing with tcpdump is given below.
tcpdump
if you are unable to start tcpdump with the above command, run tcpdump as sudo. On many UNIX operating systems, running this command requires SUDO privileges.
sudo tcpdump
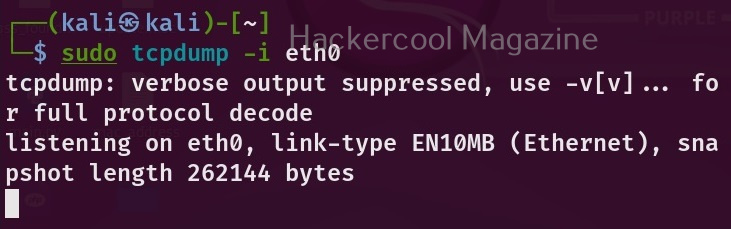
As soon as you execute the above command, tcpdump starts sniffing on all the network interfaces connected to the machine. If you want tcpdump to perform sniffing on only a specific interface, you can specify the interface with the ‘-i’ option.
sudo tcpdump -i <network interface>
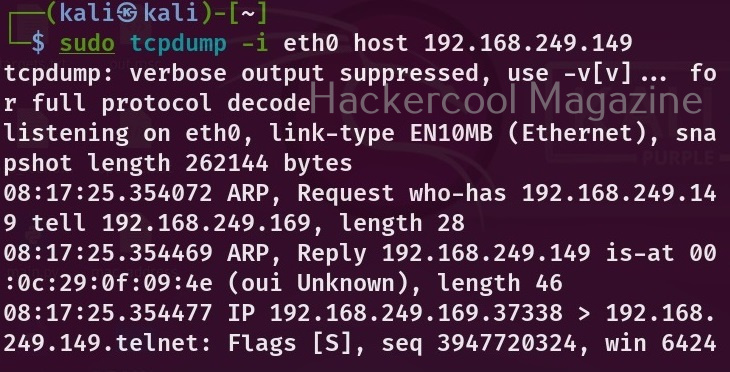
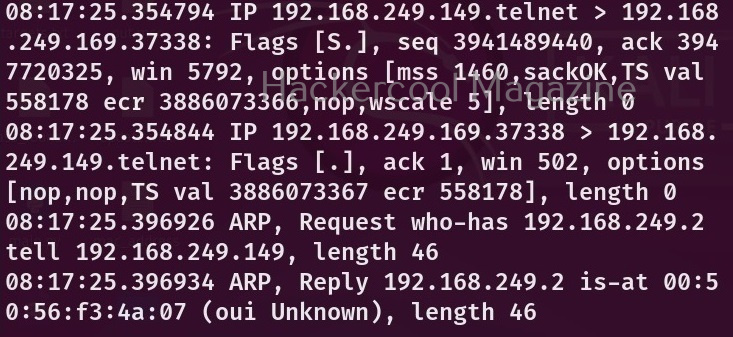
Depending on the number of devices connected to the interface, the packet analysis output may contain heavy or less traffic. To view traffic belonging to only one machine on the network, you can use the “host” option and specify the IP address. For example, let’s say we want to only see traffic belonging to device with IP 192.160.254.144 on the network. Here’s how to do it.
sudo tcpdump -i <network interface> host <host ip>
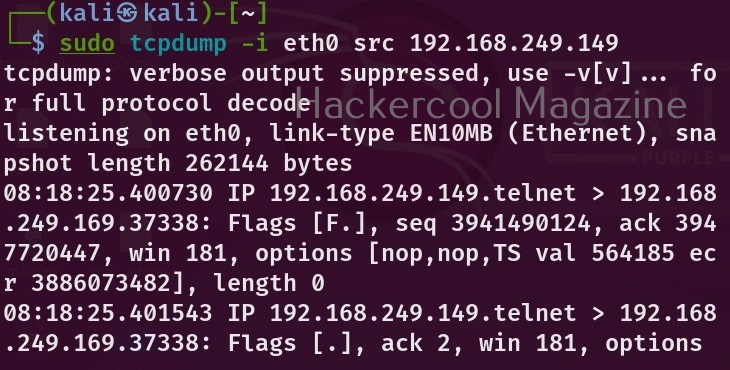
Let’s say you want to view traffic only that is originating from a particular device, you can use the option “src” for that.
sudo tcpdump -i <network interface> src <device IP>
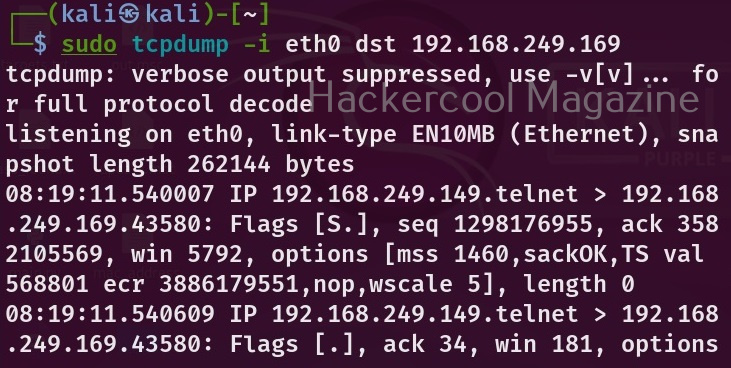
Similarly you can also view only the traffic that is coming to the particular system using the “dst” option.
sudo tcpdump -i <network interface> dst <device IP>
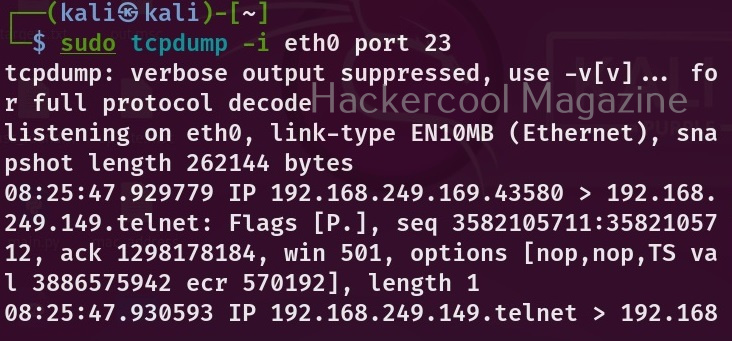
We can also view traffic belonging to a specific part using the “port” option.
sudo tcpdump -i <network interface> port <port number>
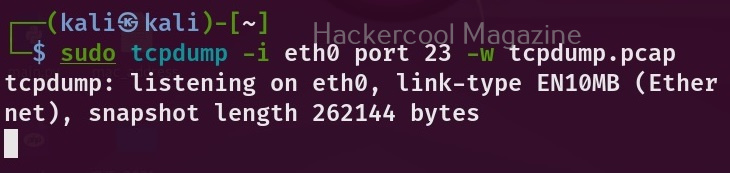
To write the output to a file, we have to use the “-w” option as shown below.
sudo tcpdump -i <network interface> port <port number> -w <file to write to>
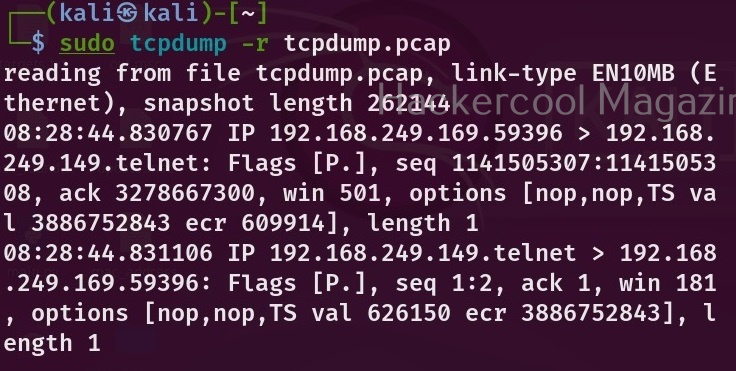
To open the saved pcap file, you have to use the ‘-r’ option as shown below.
sudo tcpdump -r <pcap file>
This pcap file can also be opened with Wireshark.
Follow Us