Hello, aspiring ethical hackers. In one of our previous blogposts, you learnt in detail about OSINT. In this blogpost, you will learn about a tool called theharvester that is used to gather open source intelligence (OSINT) on a company or domain.
Using theHavester tool, we can gather information like subdomain names, email addresses, virtual hosts, open ports, banners and employee names of an organization from different public sources like search engines, pgp key servers, IP addresses and URLs.
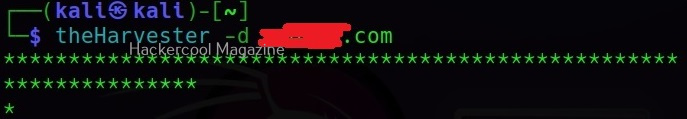
theHarvester is installed by default on almost all pen testing distros. For this tutorial, we will be using Kali Linux. theHarvester is very simple to use but very powerful during footprinting stage of a red team assessment or a penetration test. It can take a domain or an organization as target as shown below.
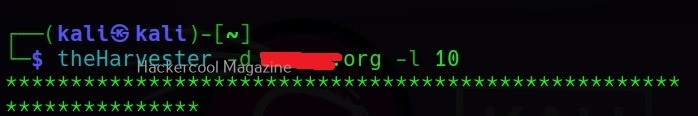
theHarvester can list a lot of entries as part of performing OSINT. You can specify the limit to the number of entries you want to be displayed.
You can even start querying from particular entry form list of entries displayed. For example, you want to start querying from the 10th entry.
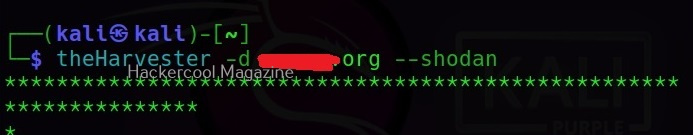
–shodan
theHarvester also has a option called “–shodan” that queries the Shodan search engine for any open ports or banners from discovered hosts. However, this requires api keys.
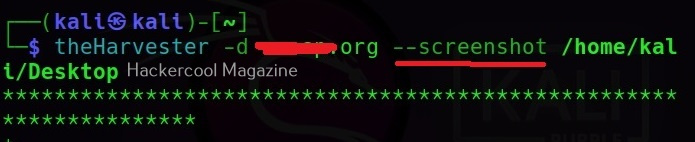
–screenshot
This command allows theHarvester to take screenshots of subdomains that are found.
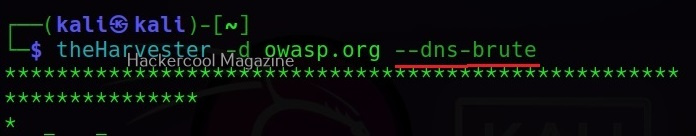
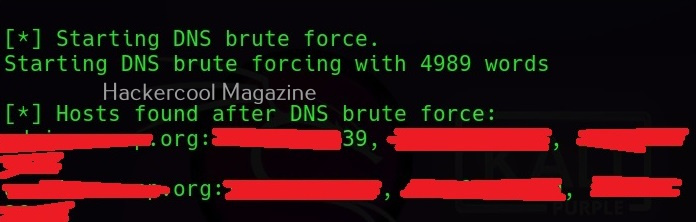
–dns-brute
As the command explains, you can brute force DNS servers using this option.
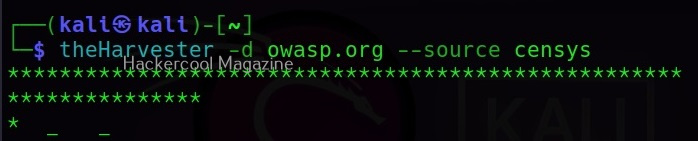
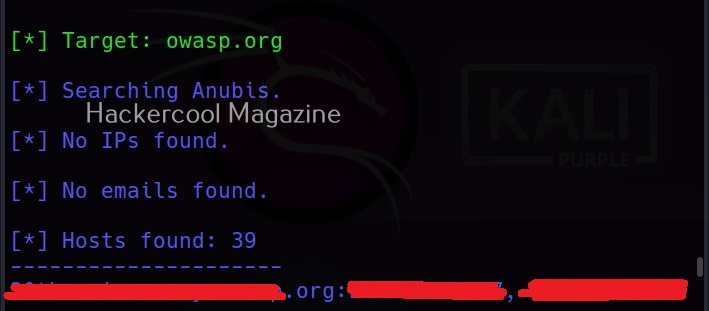
–source
theHarvester uses many public sources to collect information. Some of them are anubis, baidu, bing, brave, censys, etc. We can even ask it to use a specific source using the “–source” command.
Learn how to perform OSINT using amass or Maltego or Spiderfoot.
Follow Us