Hello, aspiring ethical hackers. In our previous blogpost, you learnt what is a vulnerability and about vulnerability scanning. In this article, you will learn in detail about vulnerability management.
What is vulnerability management (VM)?
Vulnerability management is a continuous process of identifying, prioritizing, assessing, remediation, reporting and verification of vulnerabilities in an organization.
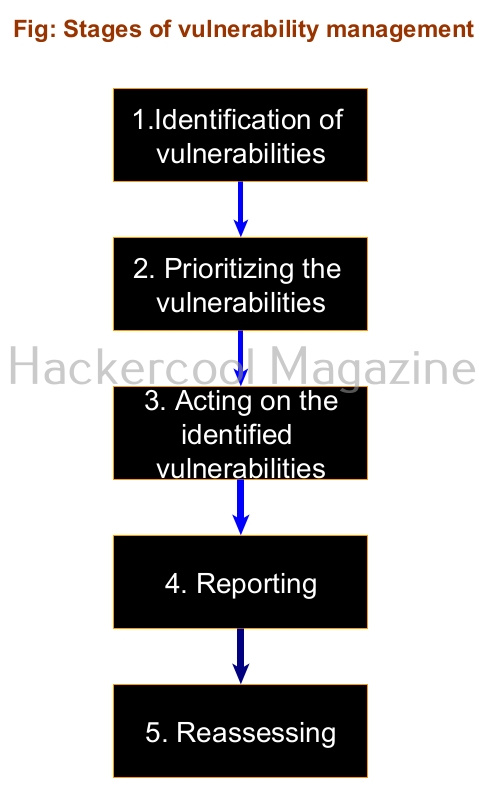
Stages of vulnerability management
There are fives stages in vulnerability management. They are ,
1. Identification:
To be able to effectively manage vulnerabilities in an organization and to prevent them from becoming a threat, first and foremost, the vulnerability needs to be identified. For this, vulnerability scanning needs to be performed on all the software, hardware, operating systems and services running in an organization.
2. Prioritizing:
After all the vulnerabilities are identified, they need to be prioritized based on the risk they pose to the security of organization and the impact its exploitation has on it. This stage includes vulnerability assessment and use of vulnerability scoring.
3. Acting on the vulnerabilities:
After all the detected vulnerabilities are classified and assessed based on the risk they pose, the next stage is to remediate or fix the vulnerabilities or at least mitigate the vulnerability. This can be done by patching the vulnerabilities, reducing its exposure etc.
4. Reporting:
The next stage is reporting the vulnerabilities. The reporting is not just limited to the heads of the organizations but also to all stakeholders like public CVE databases, partners or customers. The goal of vulnerability reporting is to bring awareness about the vulnerabilities to others before they become victim of a cyber attack.
5. Reassessing:
The last stage of VM is to once again start the entire process from the beginning. Note that vulnerability management is a cyclical or continuous process that is used to improve the security of the organization.
Vulnerability management vs vulnerability scanning vs Vulnerability assessment.
Although these terms are used interchangeably they are entirely different. Vulnerability scanning is the process of identifying the security vulnerabilities in a software or a network of the organization. Vulnerability assessment is a systematical review of vulnerabilities or weaknesses in an organization. Vulnerability scanning and vulnerability assessment are part of vulnerability management.
Vulnerability management vs penetration testing
Many people often confuse VM with pen testing, if not in reading of the terms may be in their use. While VM is useful in finding out and managing the vulnerabilities in an organization, Pen testing is performed to find out and exploit the vulnerabilities and weakness in the applications, system, device and network. Both play equally important and different roles in protecting the organization from cyber attacks.
Next, learn what is threat intelligence.
Follow Us