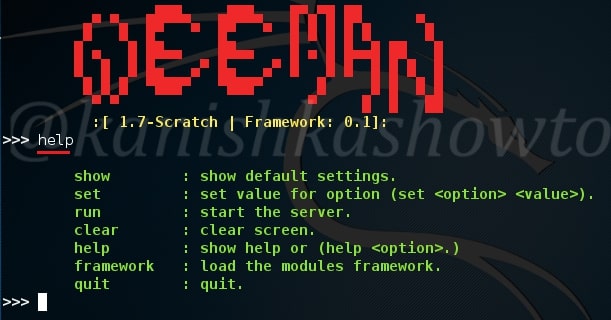
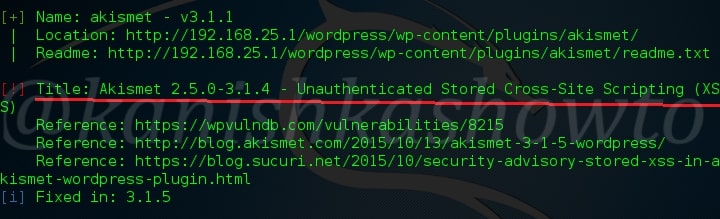
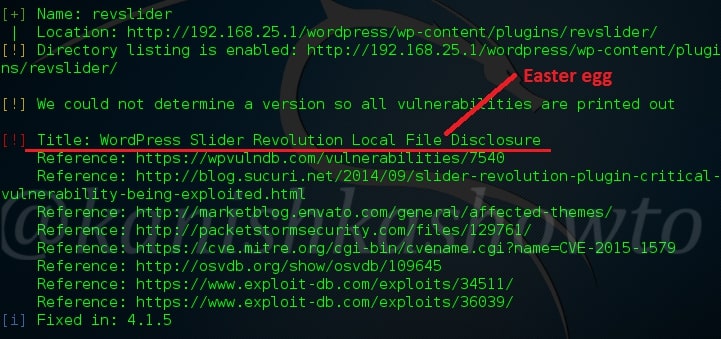
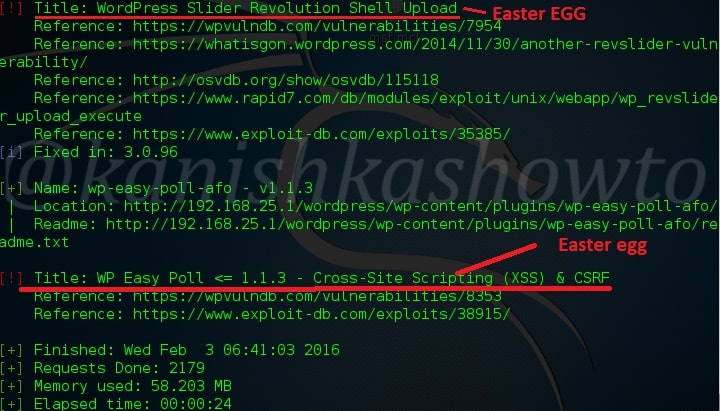
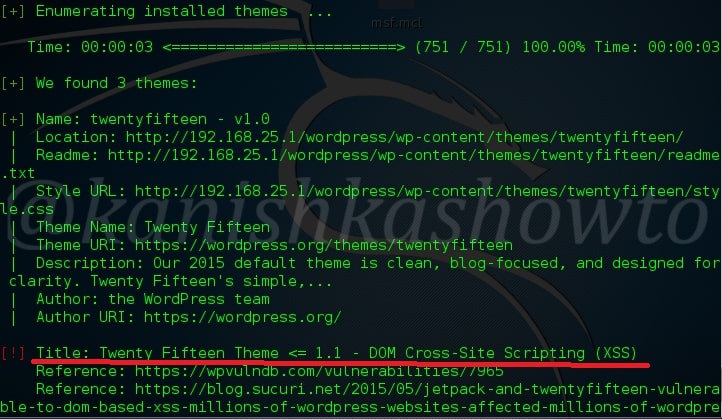
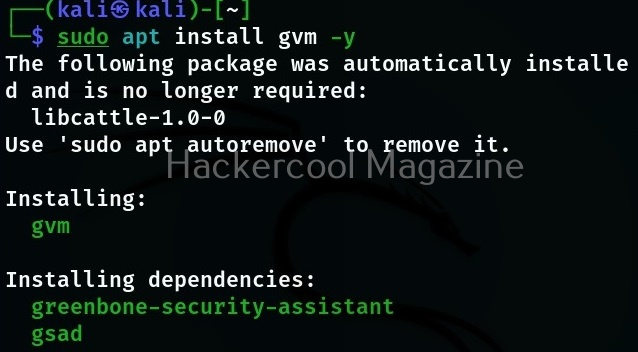
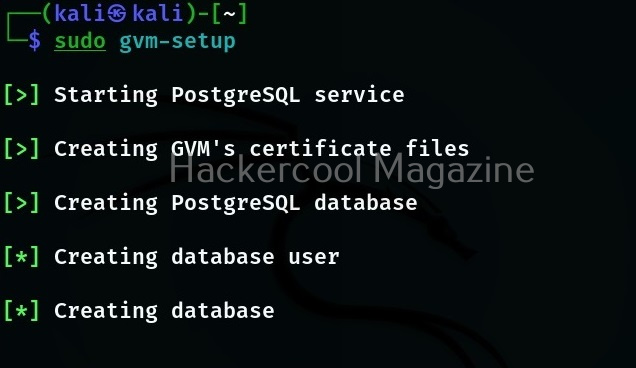
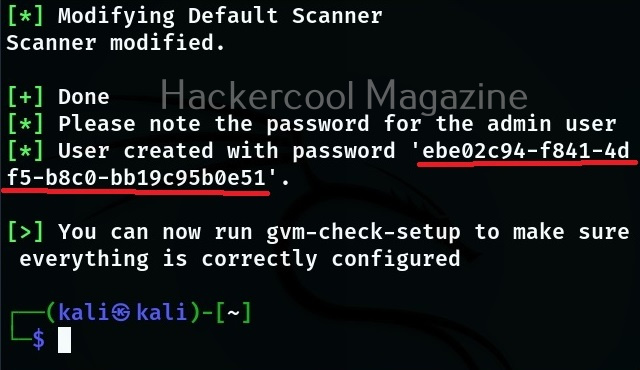
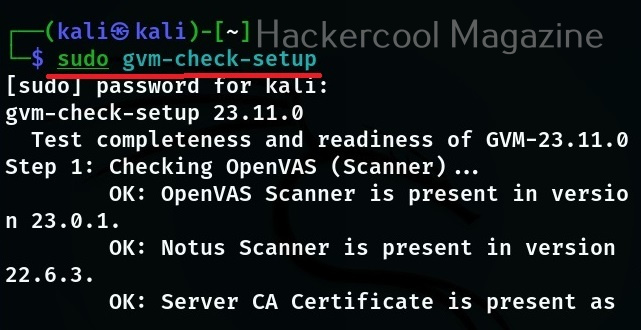
Hello, aspiring ethical hackers. In our previous blogpost on web application hacking, you learnt about various vulnerabilities a web app or website may contain. It would be good if these vulnerabilities are detected and patched before they are exploited by hackers in real-world. The vulnerabilities can be detected either manually or by using automated scanners. HP WebInspect is one such automated tool.
Hp WebInspect is an automated web application security scanning tool from HP. It helps the security professionals to assess the potential vulnerabilities in the web application. It is basically an automated dynamic application security testing (DAST) tool that mimics real-world hacking techniques and attacks, and provides comprehensive dynamic analysis of complex web applications and services. It can be downloaded from here.
Let’s see how to perform website vulnerability assessment with HP WebInspect. Open the program and click on basic scan. We will see other scan options in the following parts of this tutorial. As its name implies, this option performs a basic security scan on a website.
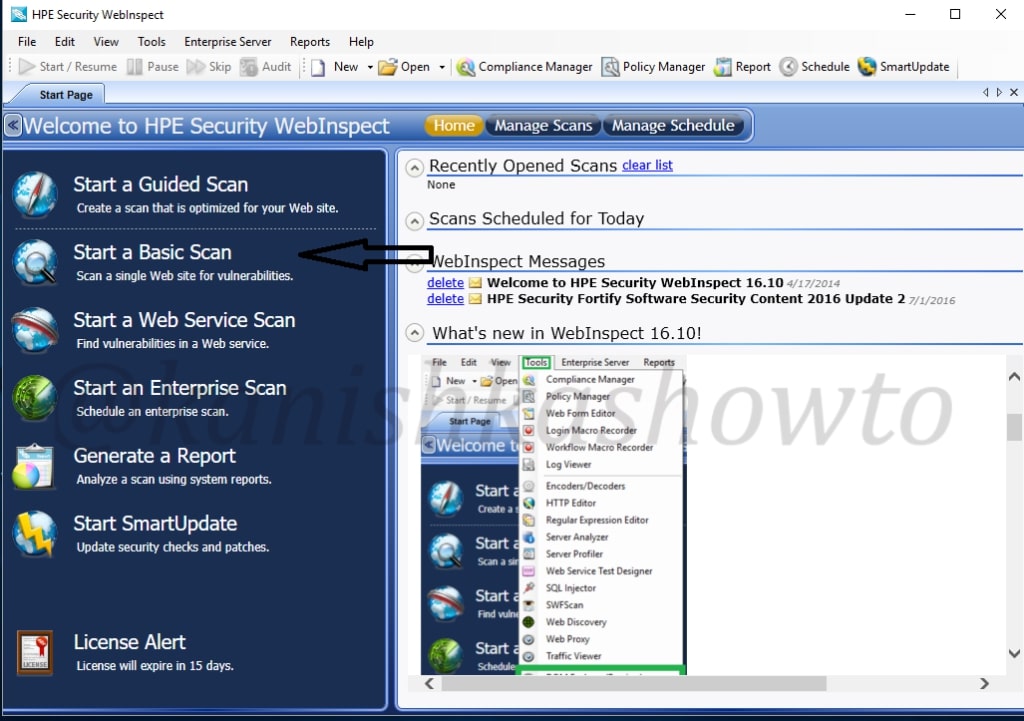
As we select the basic scan option, the “scan wizard” opens as shown below. As I am using a trial version of HPWebinspect I am only allowed to scan the website deliberately provided by HP for this purpose. This website simulates a bank ( named zero bank ) and this will be our target from now on.
I allot the given name. Below the scan name option, we have features with radio buttons. Let’s see these options.
crawl:- This process makes a list of all the pages on the entire website and builds its structure.
auditing:- Auditing is the process in which HPwebinspect will attack the website to find out the vulnerabilities.
I have selected the “crawling and auditing” option. HP Webinspect provides four types of scans.
Standard scan:- Normal scan.
List Driven scan:- You can specify the list of urls for the tool to scan. It will only scan those urls.
Workflow Driven scan:- Similar to list driven scan. You can scan a port of your website by specifying a macro.
Manual scan:- You can specify each link you want to scan. step by step.
Next specify the website you want to scan and click on “Next”.
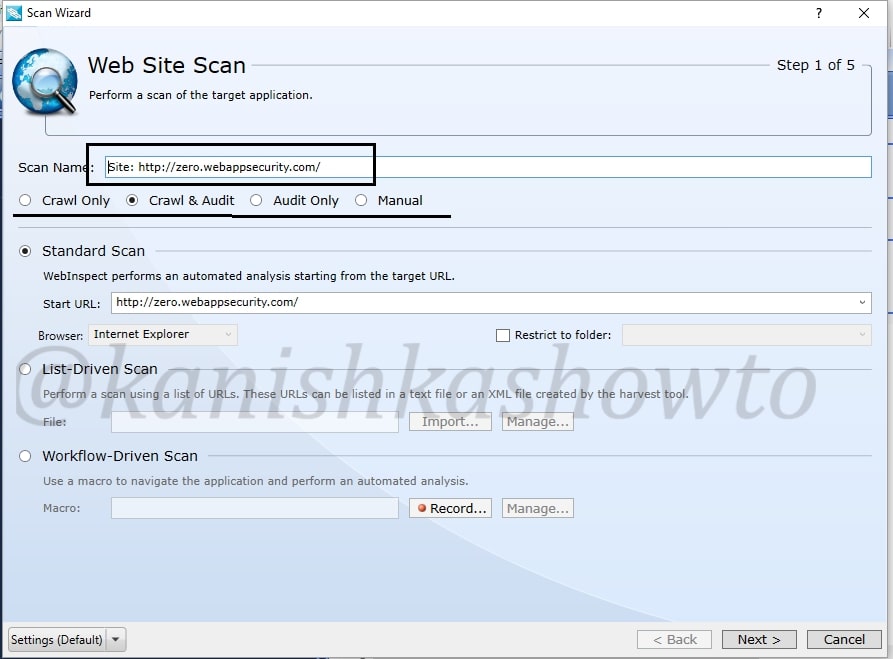
In the next window, you will be prompted for authentication. If your website or network requires authentication, provide them . Choose if you want network proxy or not and click on “Next“.
The profiler automatically samples the website and recommends best configuration for the scan. You can select the option. We will see more about profiler later. There are some other settings. Leave them to their default settings and click on “Next”.
You will get a congrats message telling about the successful configuration of scan settings. It’s time to start the scan. Click on “scan”.
The scan will start as shown below. It will take some time dependent on the size of the website you are scanning.
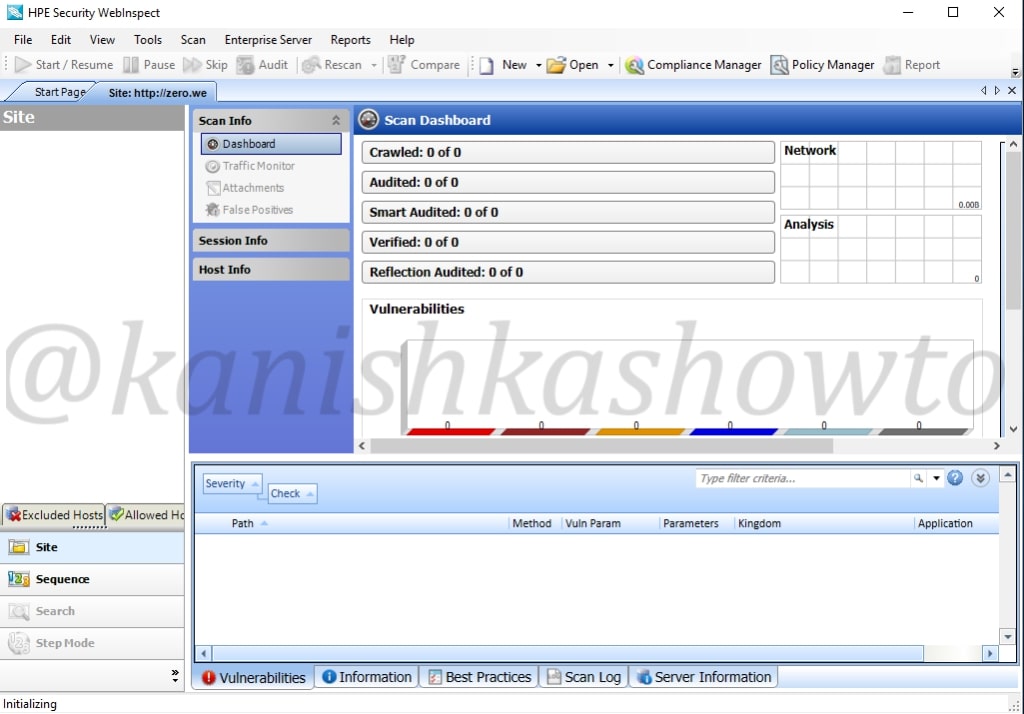
After the scan is finished, it will show the results as shown below. This tool classifies vulnerabilities into critical, high, medium, low and info. That was about basic scanning of website with HPWebinspect.
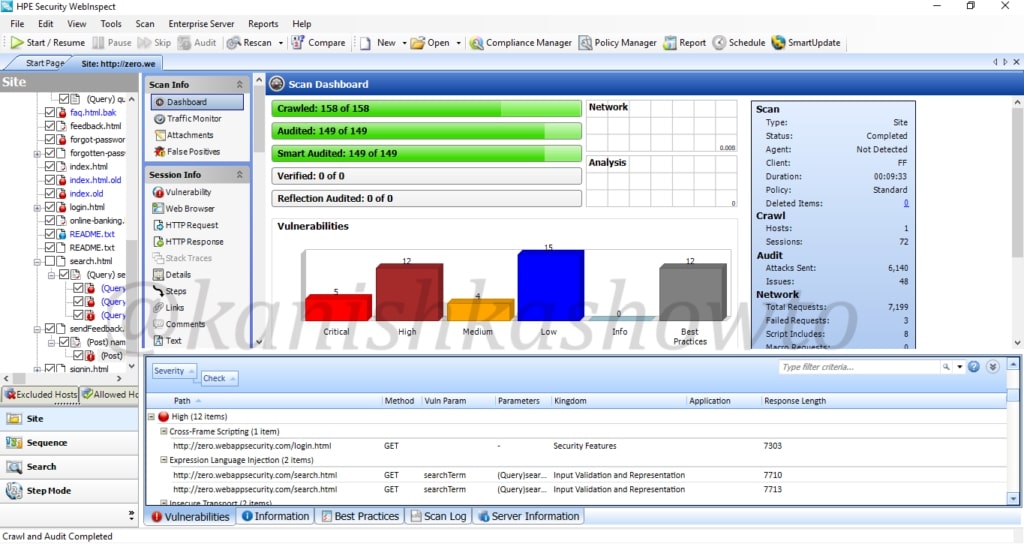
That’s all in WAPT with HP WebInspect. Now, we will see analyzing these vulnerabilities. Wait, but why do we need this analysis? Just because we have used an automated tool doesn’t mean it is cent percent effective. There may be lot of false positives and in the worst case false negatives. The threat it shows as critical may not be really that dangerous or a threat it shows as medium may be critical depending on the situation. The analysis part is very important part of the WAPT. Let us see how to perform this analysis . We will take our previous scan report.
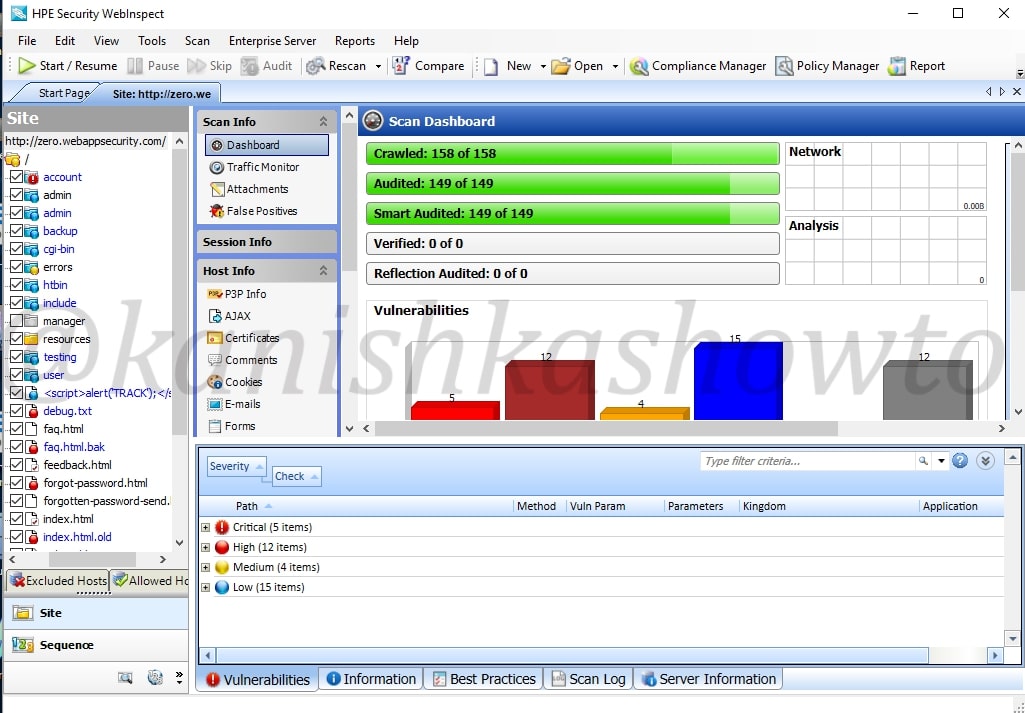
Before we do the analysis, let us have a look at the interface of HPWebinspect. To the down left, we have view options of the scan ( site and sequence ). The “site view” shows us the hierarchical structure of website we just scanned with vulnerabilities found highlighted as shown below to the left. We can see that in account part of the website there is a critical vulnerability.
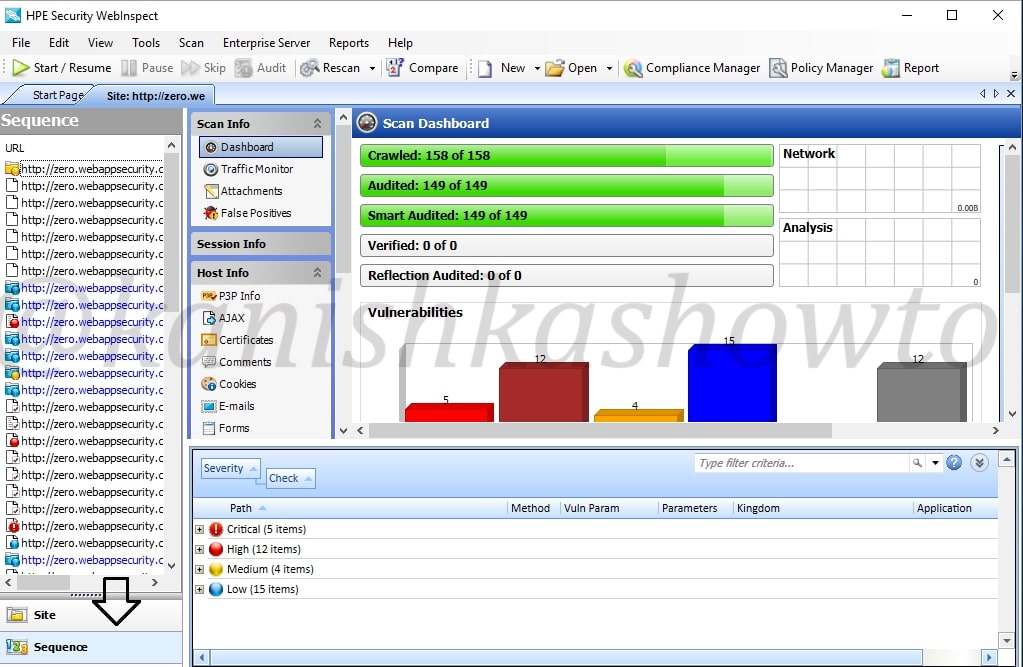
The sequence view shows us the order in which WebInspect scanned the URLs. It is shown below.
Occupying large area of the interface is the Scan dashboard with a pictorial representation of vulnerabilities. It also has vulnerabilities classified into its attack types ( how exactly these vulnerabilities will be used ).To its left, we have sections called scan info, session info and host info. The scan info has four options : dashboard, traffic monitor, attachments and false positives. We have already seen dashboard and others are self explanatory.
Below scan info we have have session info. It is empty because we didn’t include any sessions in our scan.
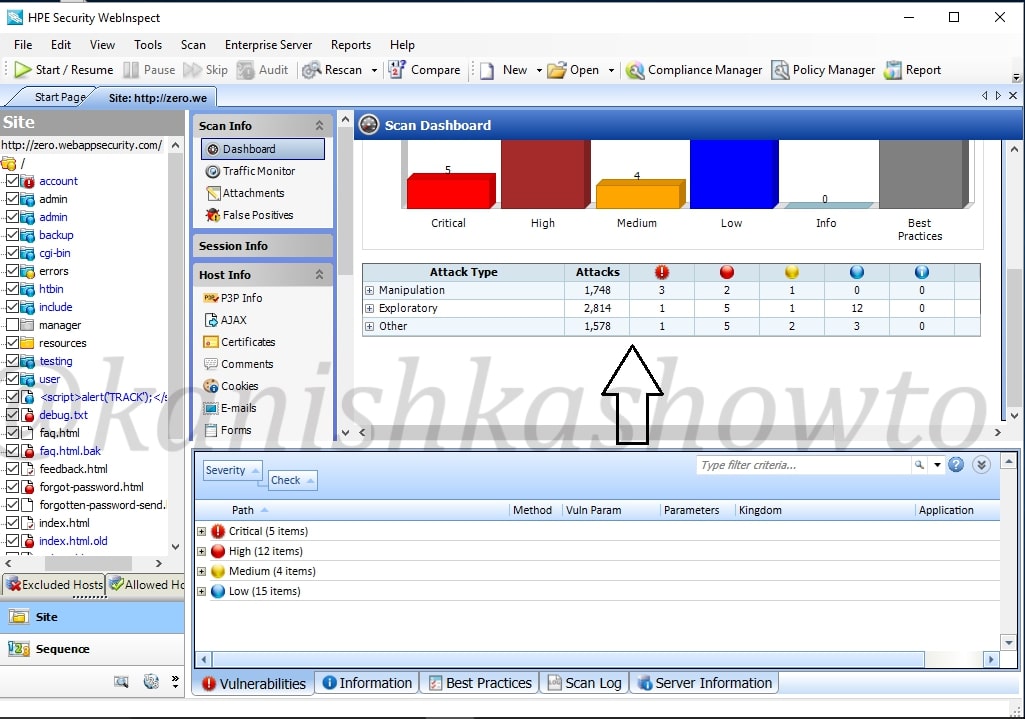
Below session info, we have the host info which is obviously information about the host we scanned. It will provide us info like P3P info ( protocol allowing websites to declare their intended use of information they collect about users) , AJAX, certificates etc, etc, etc. Let us look at the cookies collected by the scan.
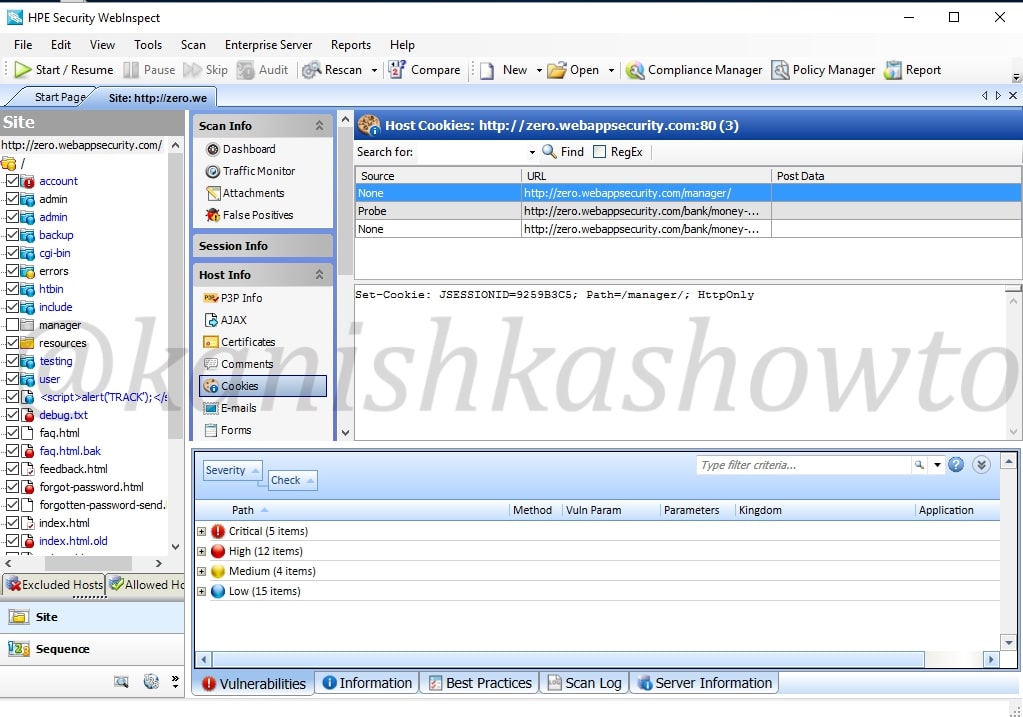
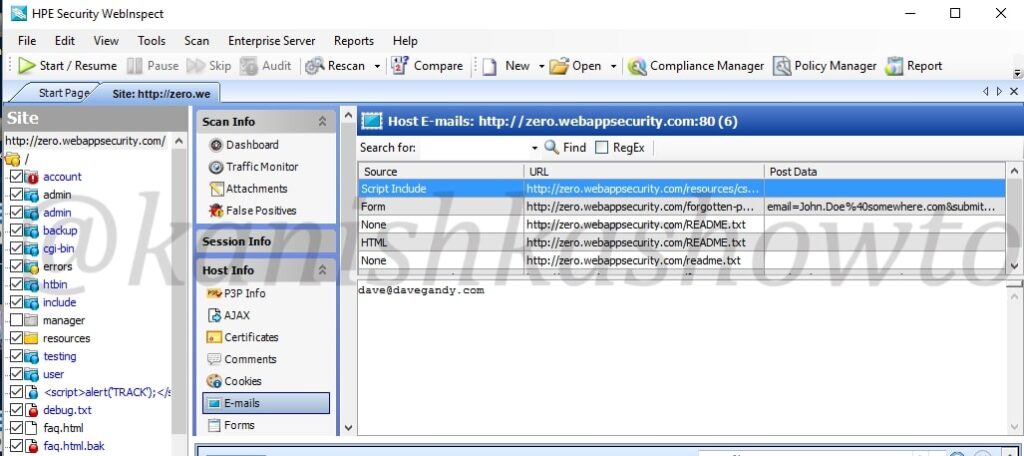
It also shows us the emails we found during scan.
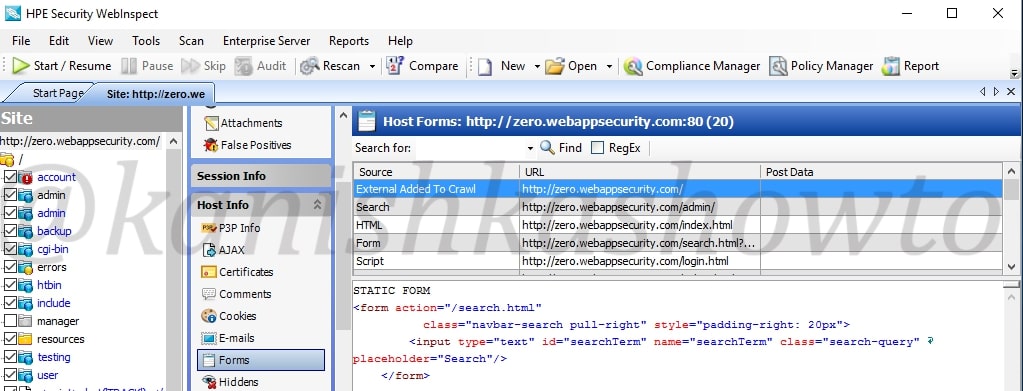
Also the forms.
Now we come to the most important part of the interface which is right down below. These are the vulnerabilities found during the scan. As already said, these are classified according to the dangers posed by them but there may be false positives. We need to analyze each vulnerability for this exact reason.
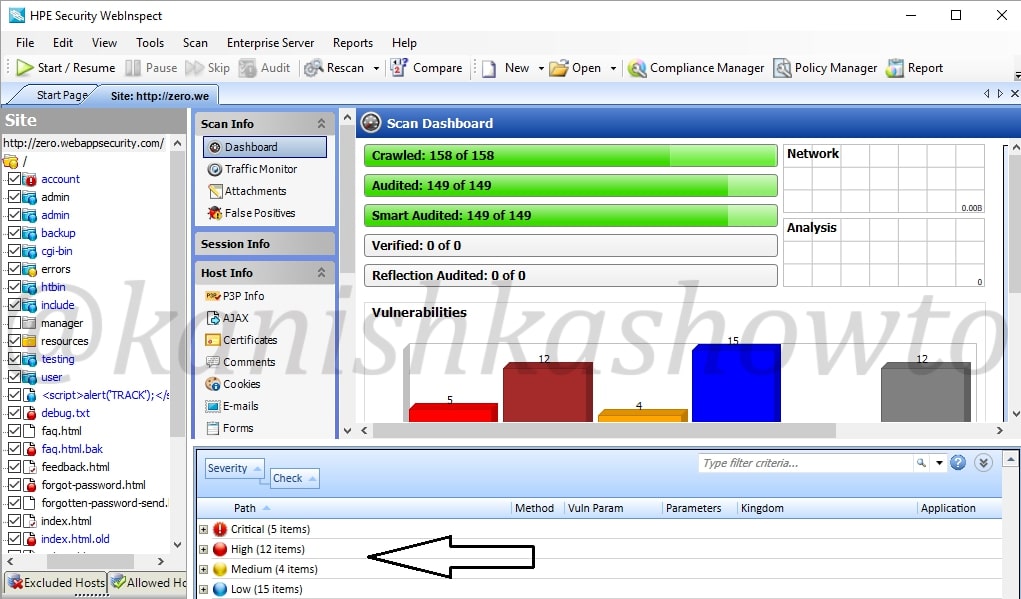
In this howto, we will cover analysis of one or two vulnerabilities. Expand the “critical” section of vulnerabilities. We can see that there is a XSS vulnerability in the search page. We will analyze this vulnerability.
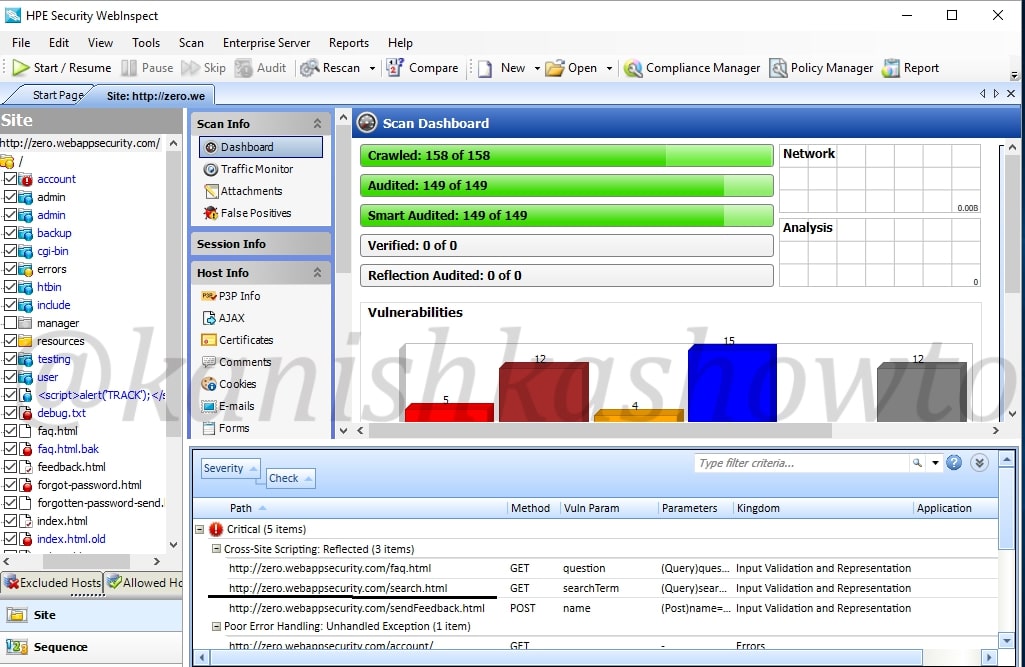
Click on the vulnerability. The dashboard of HPWebinspect will show information about the particular vulnerability ( in our case XSS ) and how hackers might exploit this.
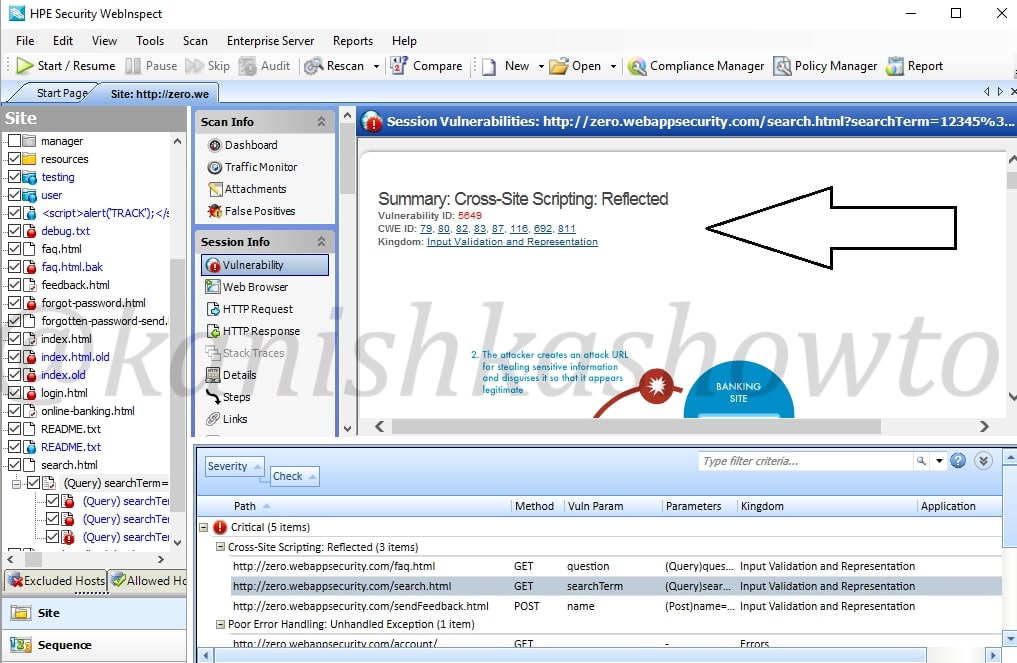
Scroll down the dashboard to get more info about the vulnerability. We can see the exact query used by the tool to get the result. In this case, our target is using tag removal to prevent XSS but we can bypass using the query given below. ( We will learn more about XSS and its evasion filters in a separate howto)
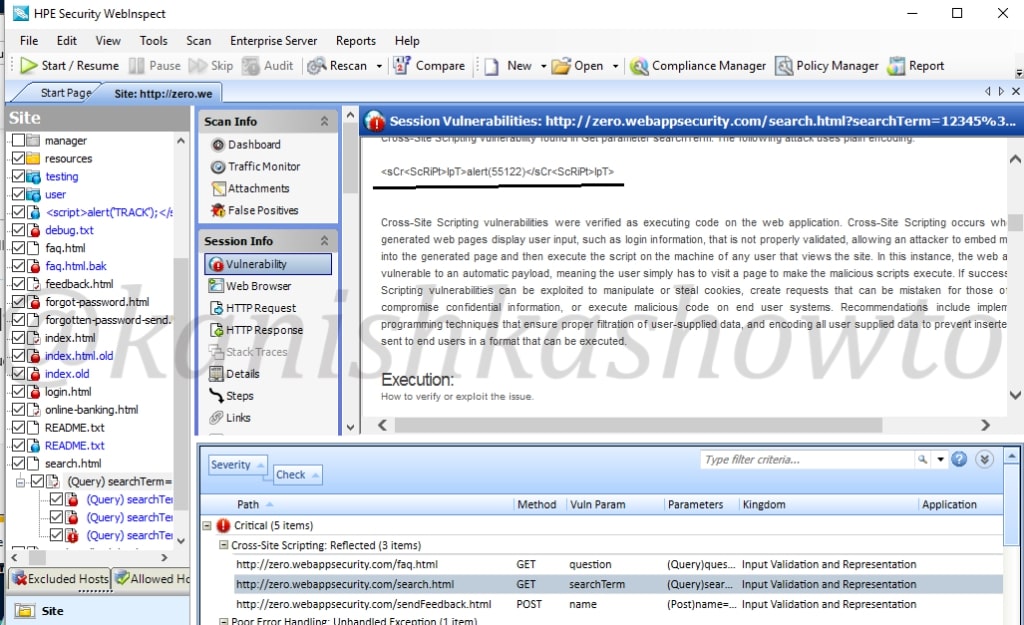
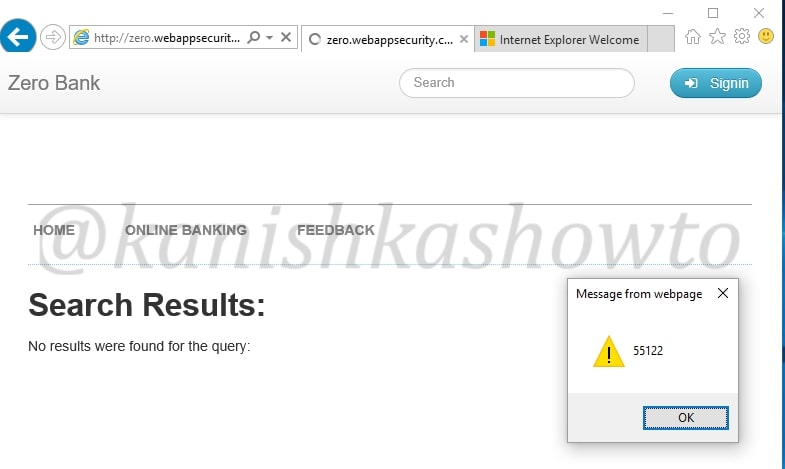
Now right click on the vulnerability we are analyzing. In the menu that opens, click on “View in Browser” to see this exploit practically in the browser.
We can see the browser result below. In this case, it is displaying a messagebox with a number but hackers can use it to display cookies and session ids. Hence this is definitely a critical vulnerability.
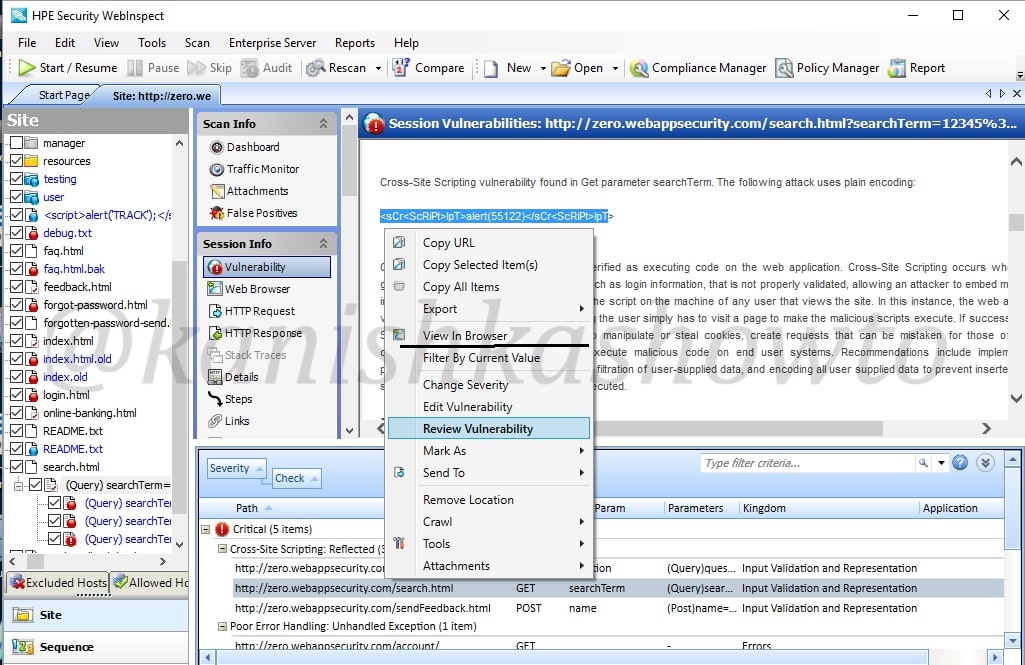
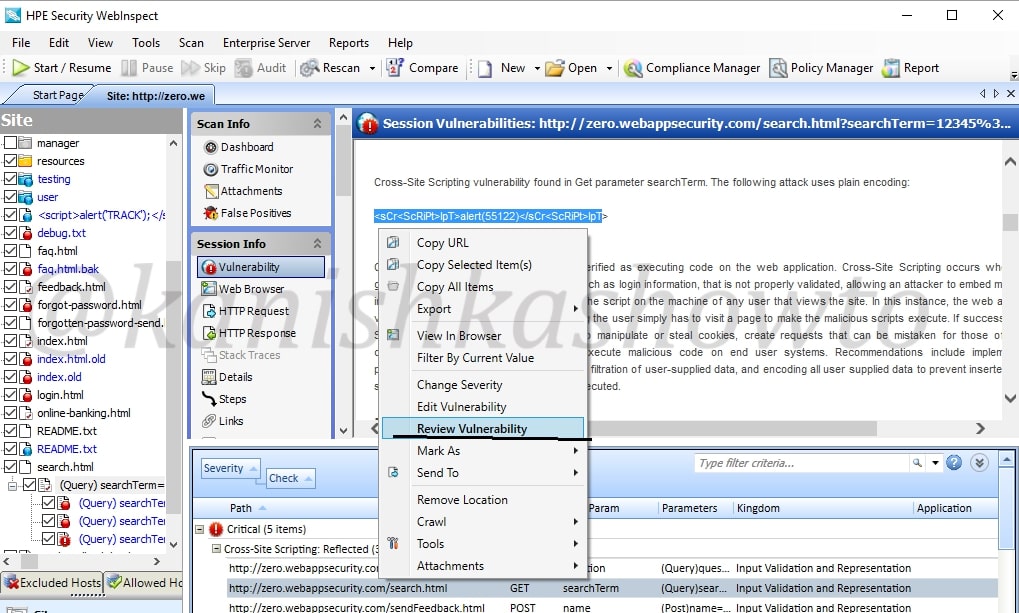
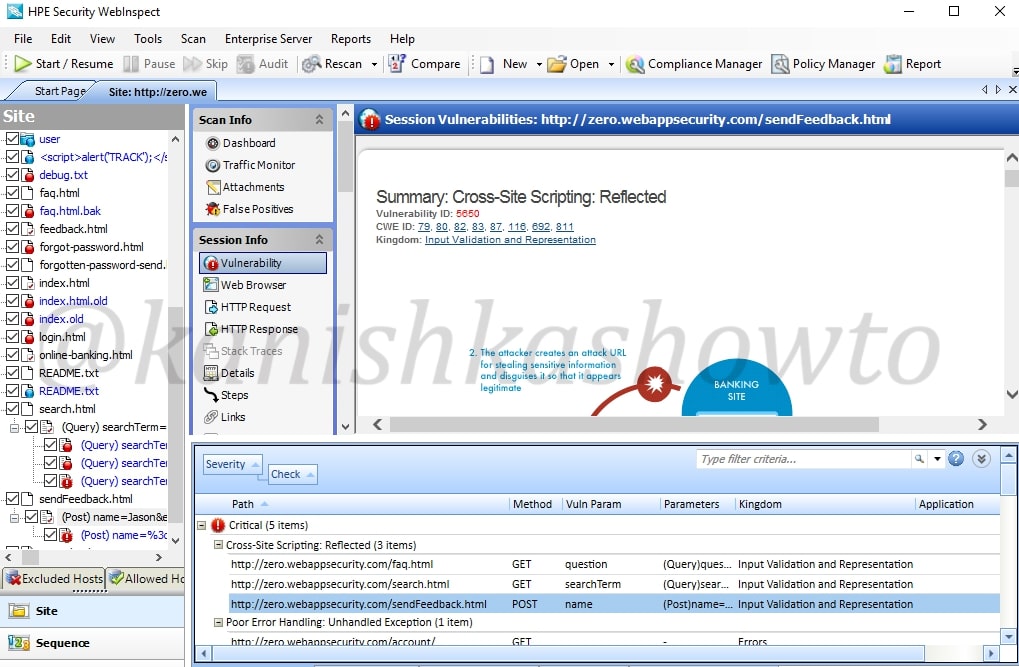
Right click on the vulnerability and select the option “Review vulnerability”. This is helpful in knowing more precisely about the vulnerability.
Another window will open as shown below. It will automatically show you the browser view.
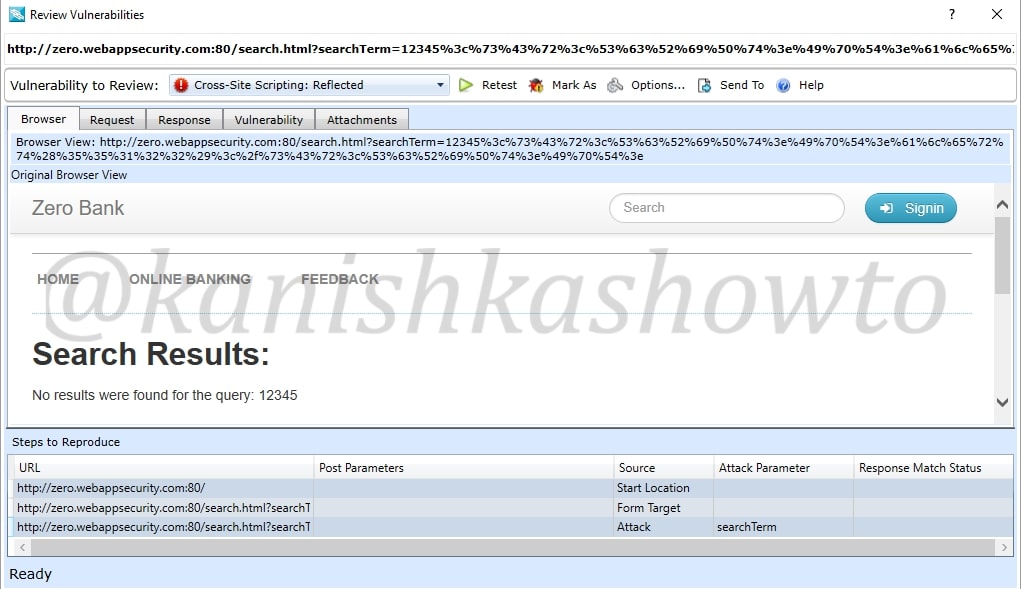
We can click on “Request tab”to see the request sent by our tool.
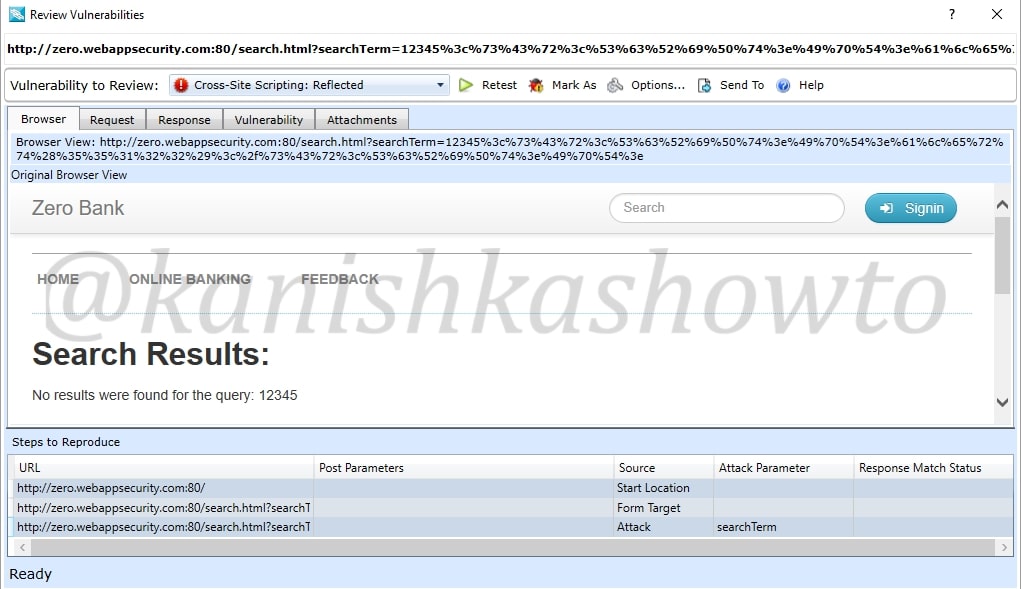
Similarly the response tab shows us the response given by the target.
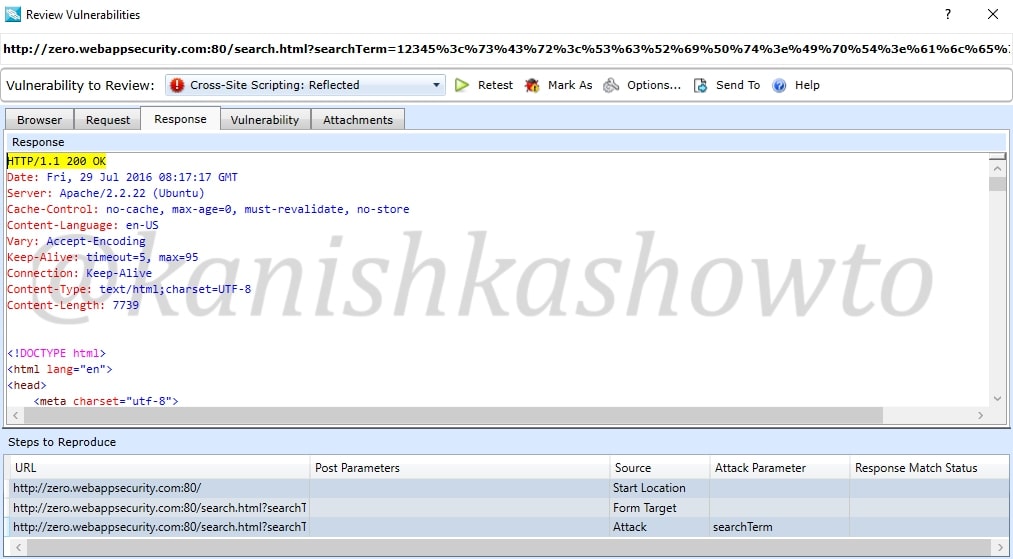
We already saw this before in the dashboard. The “vulnerability tab” give us information about the vulnerability and how hackers might exploit it. There are also options like “Retest” and “Mark as”. The Retest option allows us to test the vulnerability again. We shall see the “mark as” option below.
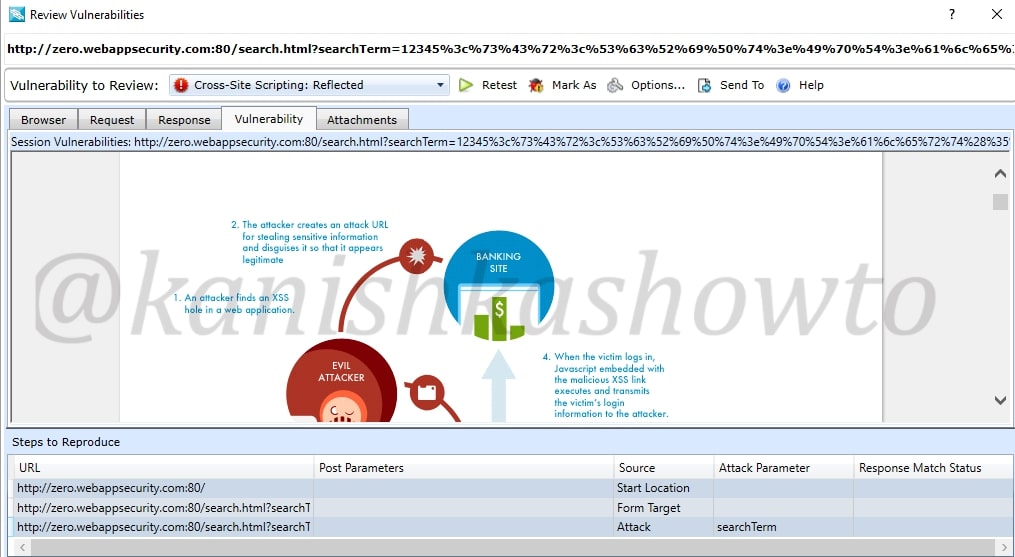
Close the window. Once again right click on the vulnerability. You can see the option “change severity”.
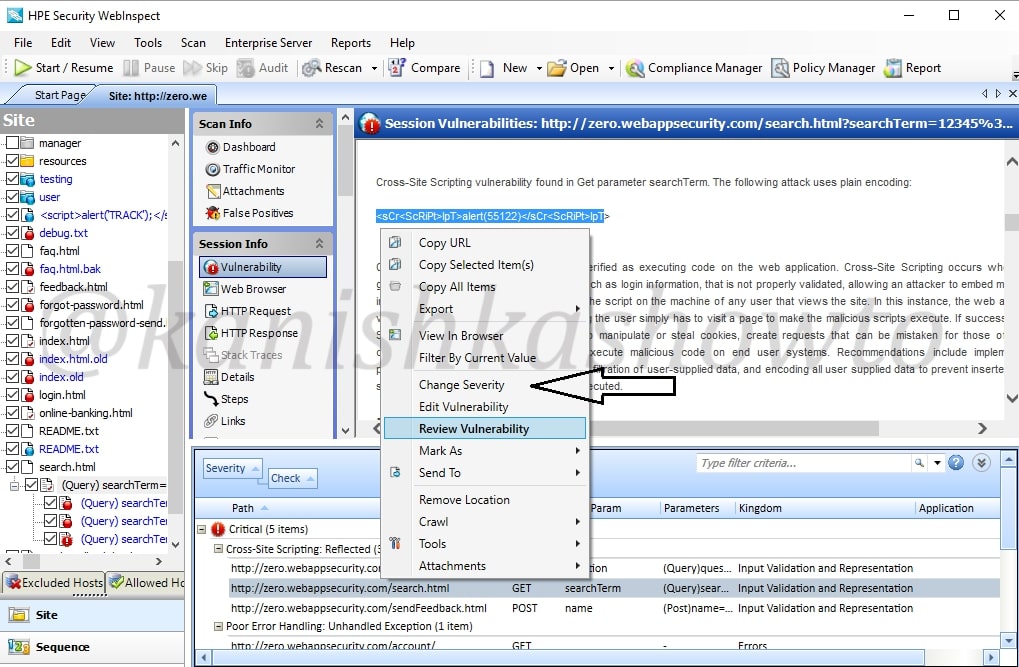
For instance, the vulnerability detected is not that critical, we can change its severity suitably to high or medium or low.
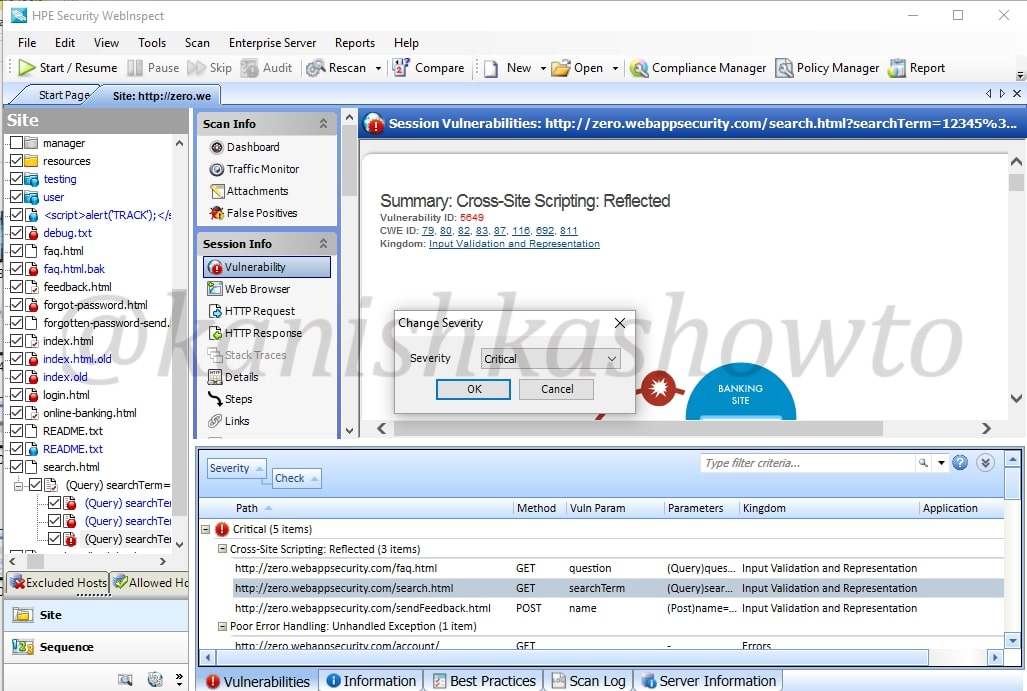
Now what if the vulnerability detected is not an actual vulnerability. This is known as false positive. For example, we have this send feedback page of the target website. Let us assume it is just a false positive. In that scenario, just below the “review vulnerability” option we have “Mark as” option.
We can also access this option from the “review vulnerability” window as already shown above.
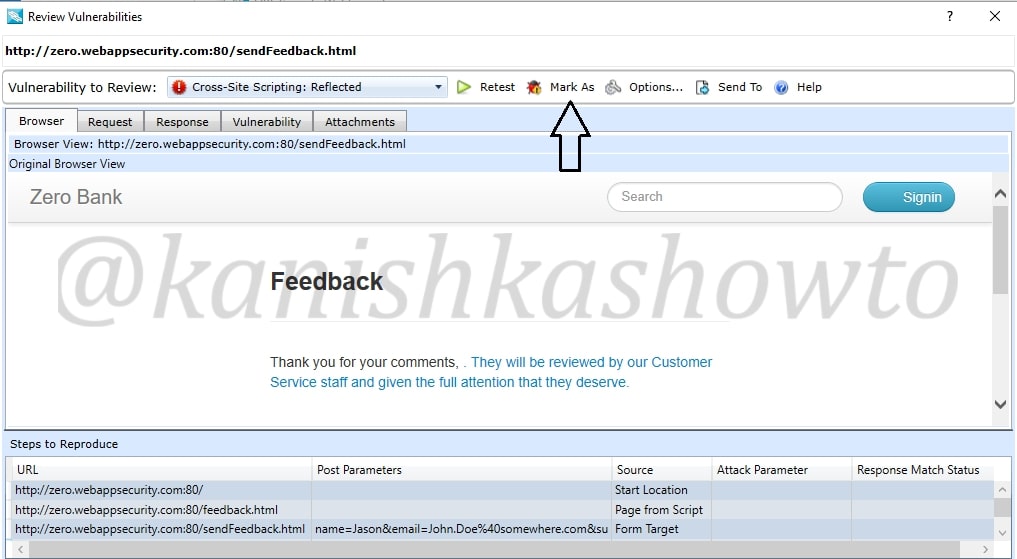
When we click on that option, we get two sub-options to mark it either as false positive as shown below
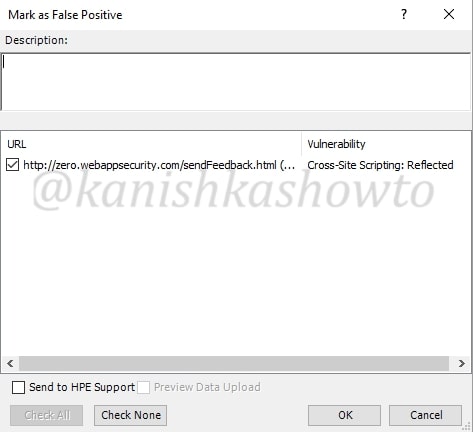
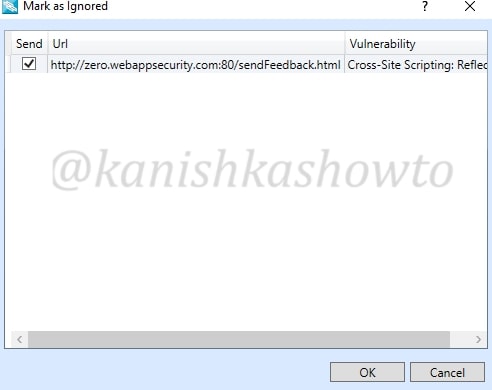
or to completely ignore the vulnerability. We can only ignore the vulnerability if it doesn’t pose any valid threat. We can also provide some description about why we are marking it as false positive or ignoring.
When we have successfully finished reviewing each vulnerability, it’s time to write the penetration testing report. To automatically generate a report, click on “Reports” tab. Select the scan for which you want to generate the report and click on “Next”.
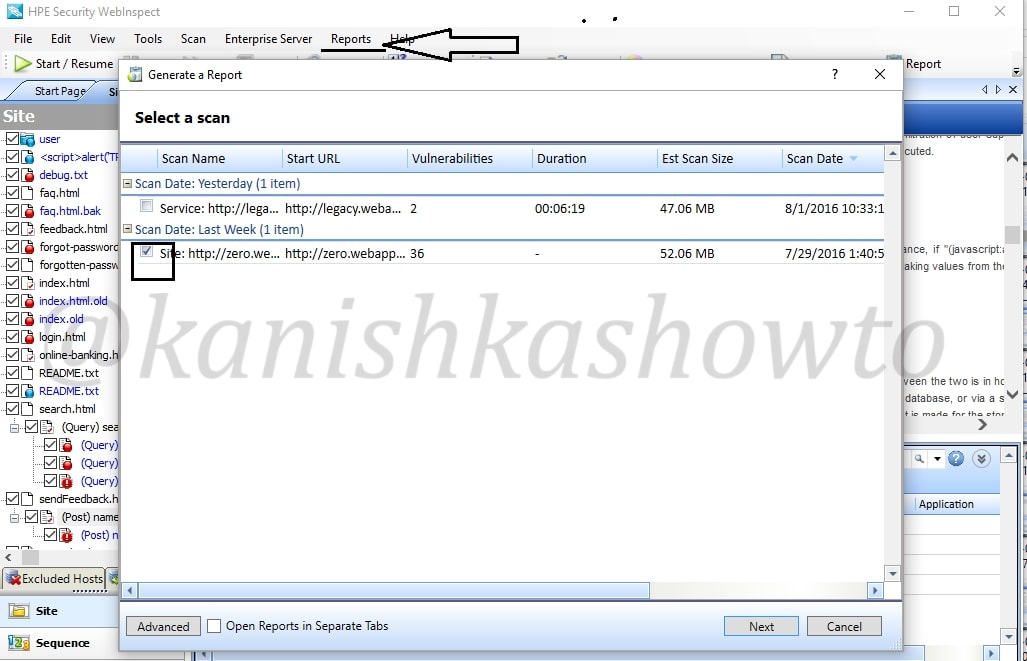
Select whatever you want to include in your report as shown below and click on Finish.
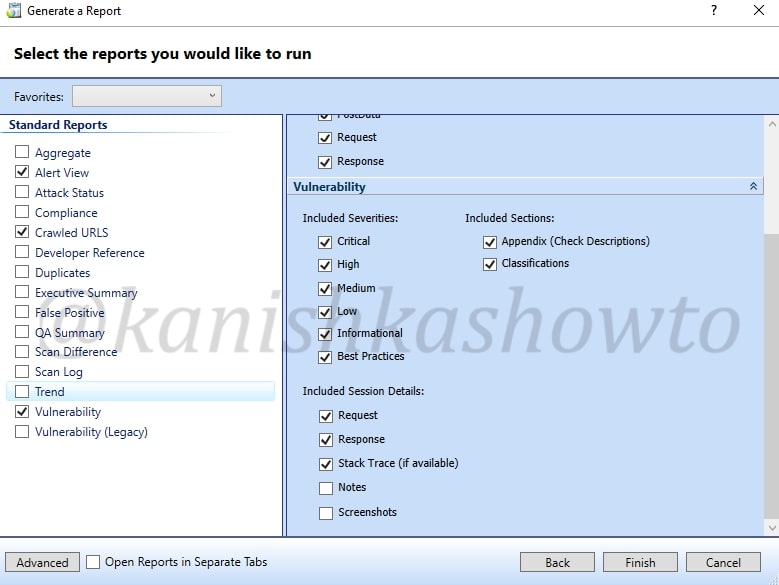
The report generation takes some time depending on the options you selected. The report generated would be in the format as shown below. That’s all for now and in our next howto, we will see more about the tool.
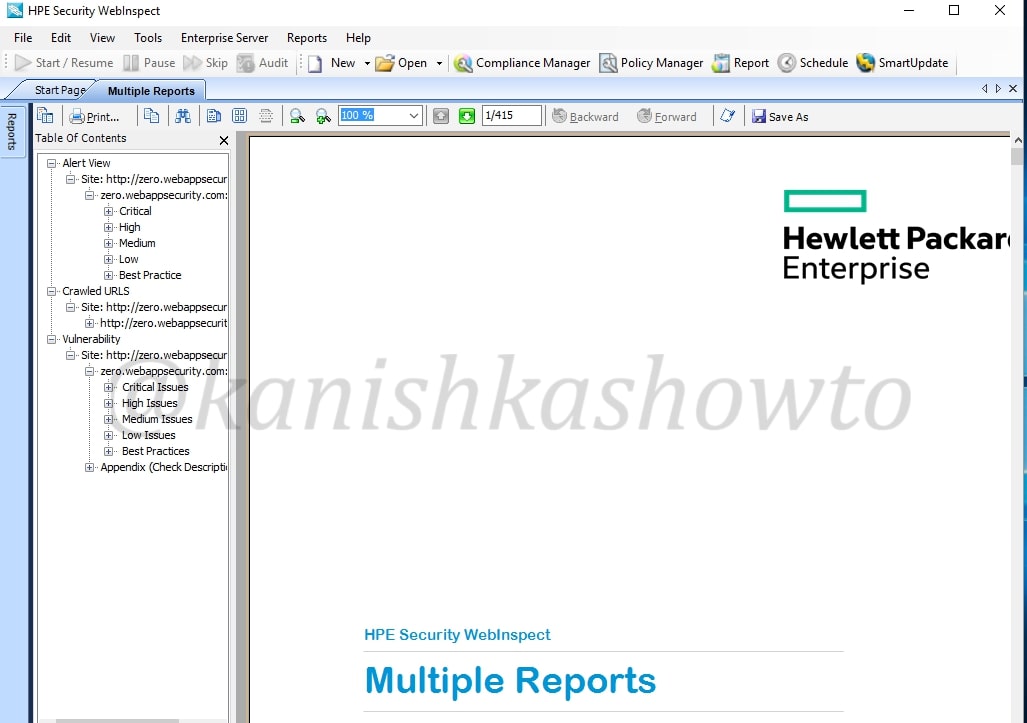
That’s how we can find vulnerabilities in website with HP WebInspect.