Hello aspiring Ethical Hackers. In this blogpost, you will learn about vulnerability scanning. Before you learn what a vulnerability scan is, you need to know what a vulnerability is? A vulnerability is a weakness, flaw, error or a misconfiguration in a software or network that allows hackers to gain unauthorized access to the organization by exploiting it.
What is vulnerability scanning?
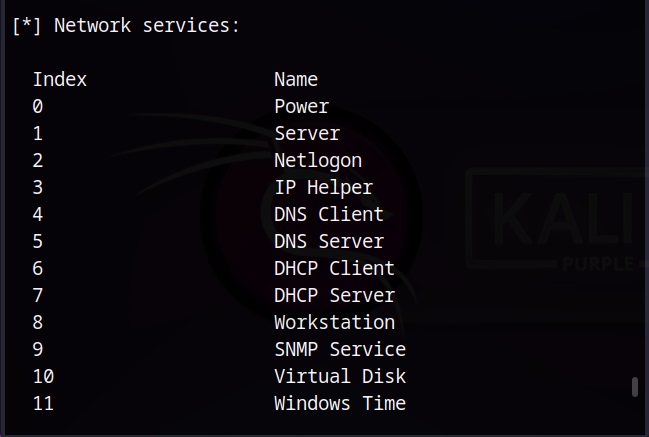
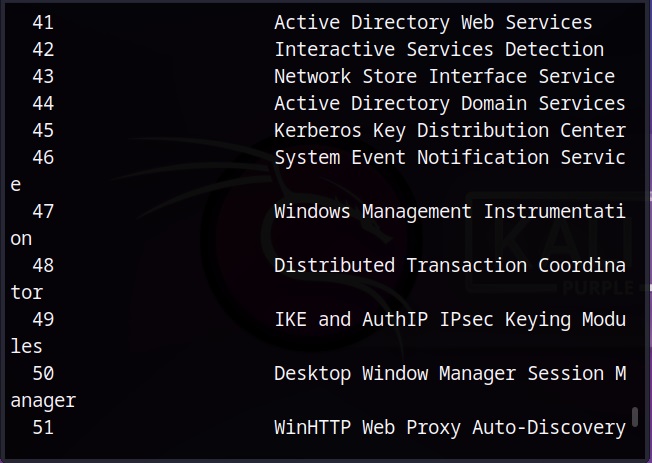
Now that you have understood what is a vulnerability, let’s see what is scanning. Vulnerability scanning is the process of identifying the security vulnerabilities in a software or a network of the organization. Vulnerability scanning is usually performed to protect the organization from hackers although it is also performed by hackers to gain access to the organization.
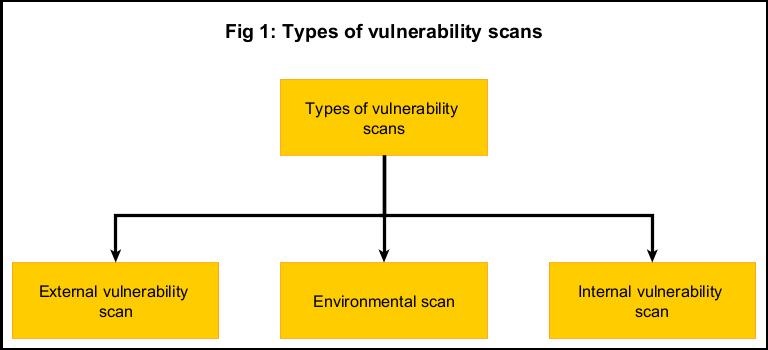
Types of vulnerability scans
Vulnerability scanning can be categorized into different types. They are,
- External Vulnerability Scan
- Internal vulnerability scan
- Environmental scans
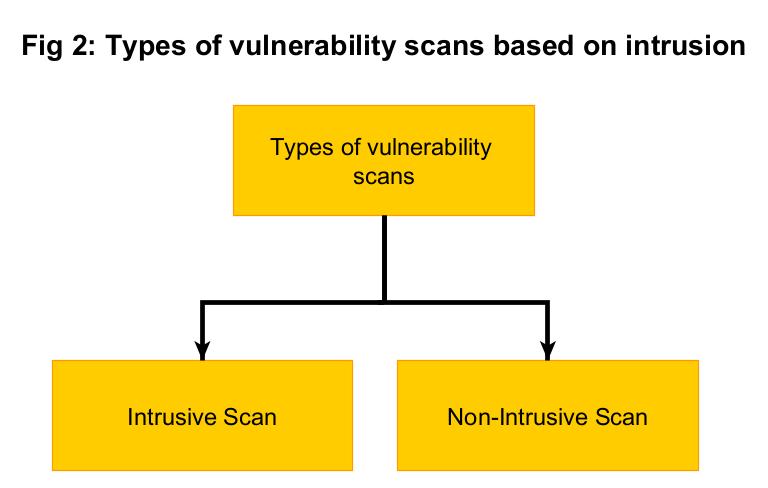
- Intrusive Scans
- Non-Intrusive scan.
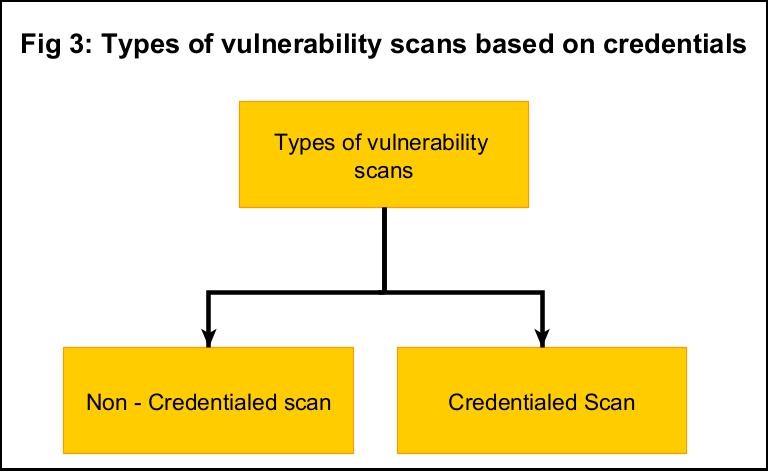
- Credentialed scan
- Non-credentialed scan
1. External vulnerability scan:
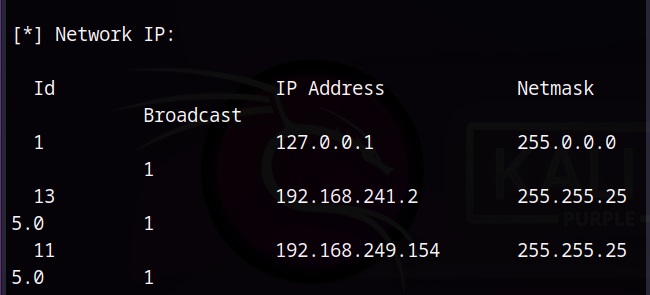
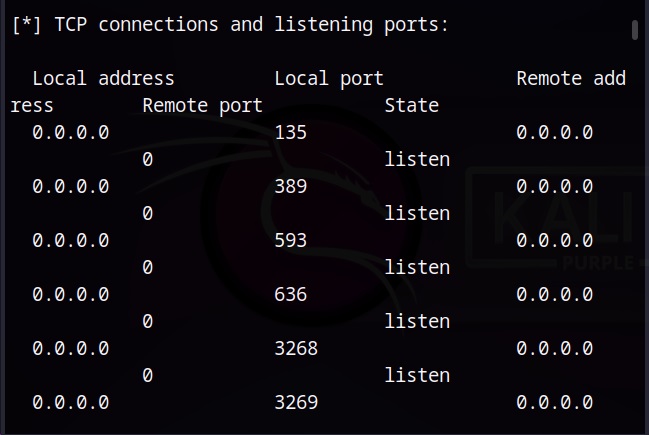
In an external vulnerability scan, the external facing resources of an organization are scanned. These include, websites, systems, ports and services.
2. Internal vulnerability scan:
In this type of scan, the vulnerability scan is performed on the internal network of the organization or on resources to which the users or employees of the organization have access to. This scan is performed to get information about the vulnerabilities which employees or malware which gained access to the network can exploit.
3. Environmental scan:
Environmental vulnerability scans are performed based on the target environment. For example, target environment can be cloud based, IOT, mobile devise, websites etc.
Vulnerability scans can also be classified as either Intrusive or Non-Intrusive.
4. Non- Intrusive scan:
In a non-intrusive vulnerability scan, vulnerabilities are just identified and reported.
5. Intrusive scan:
In an intrusive vulnerability scan, vulnerability is not just identified but also exploited.
Apart from these categorizations, vulnerability scan is also classified as credentialed scans and non-credentialed scans.
6. Credentialed scan:
Also known as authenticated scan, this vulnerability scan in performed using a set of credentials. This type of scan gives the trusted users view of the organization.
7. Non-credentialed scan:
Also known as non-authenticated scan, this vulnerability scan gives the external user’s view of the network or revenue of organization.
Uses of vulnerability scans
Vulnerability scanning can help cyber security personnel of the organization to get an idea about the vulnerabilities in the organization beforehand and to prevent them from being exploited by attackers. As hackers also perform vulnerability scans, vulnerability scanning gives an idea to the organization as to what hackers can see.
How are vulnerability scans performed?
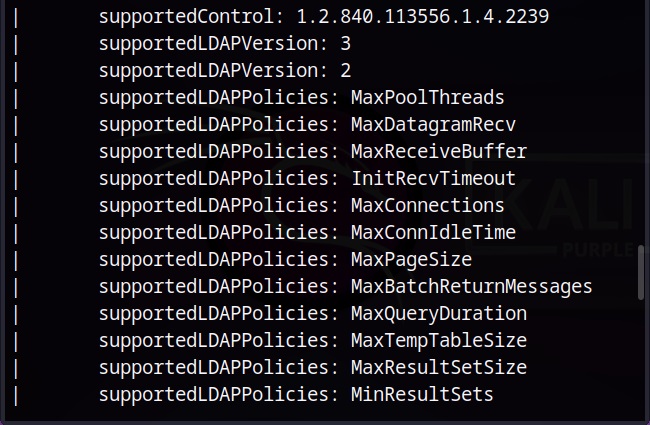
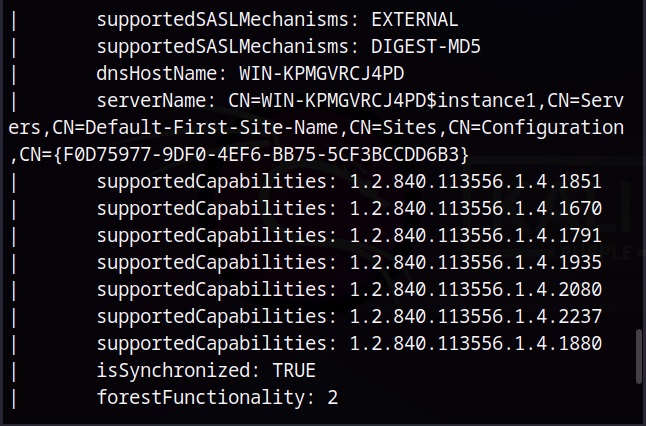
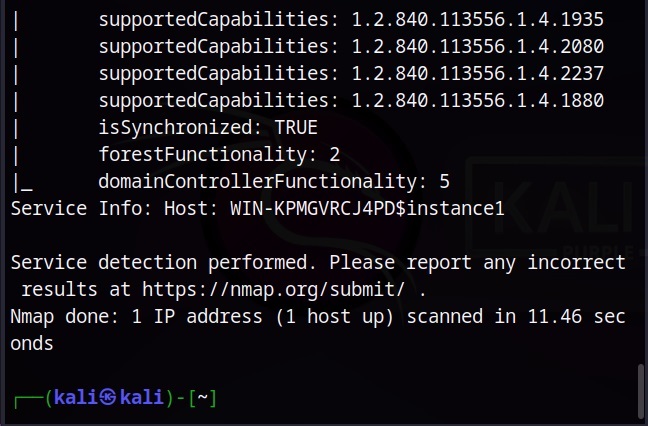
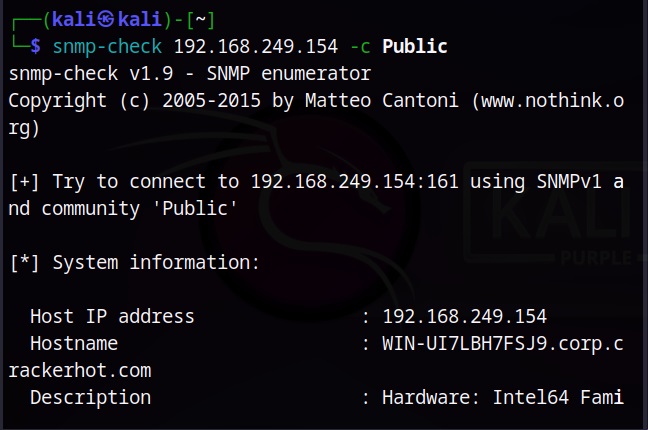
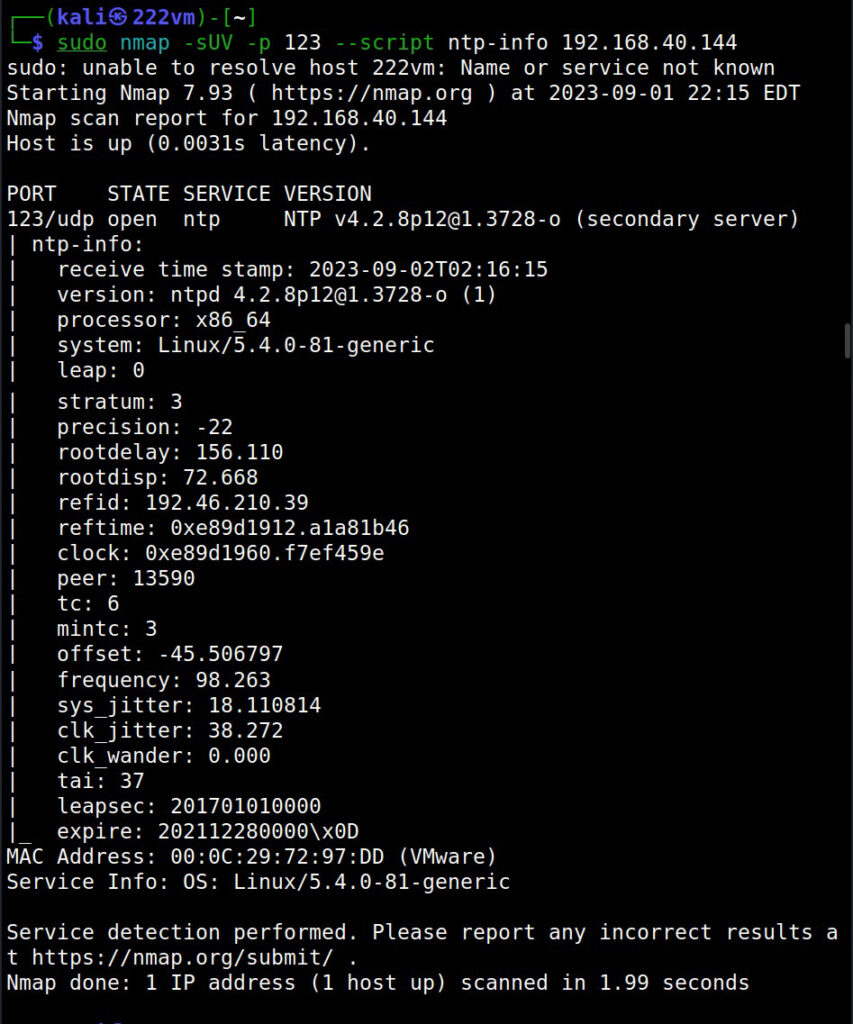
Vulnerability scans can be performed manually or using tools (vulnerability scanner). See how to perform vulnerability scanning with Nikto and Nessus.
Vulnerability scan vs Vulnerability assessment
In vulnerability scanning, vulnerabilities are scanned and reported whereas in vulnerability assessment, apart from identifying vulnerabilities the impact of the vulnerabilities when exploited is also assessed. Learn more about vulnerability assessment.