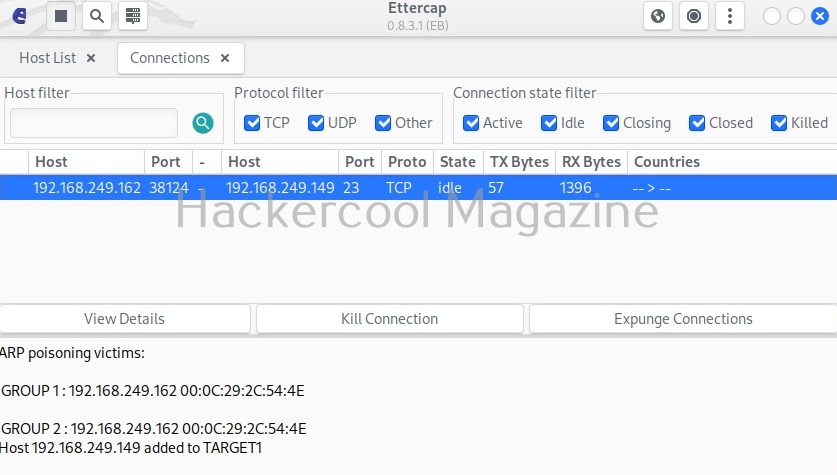
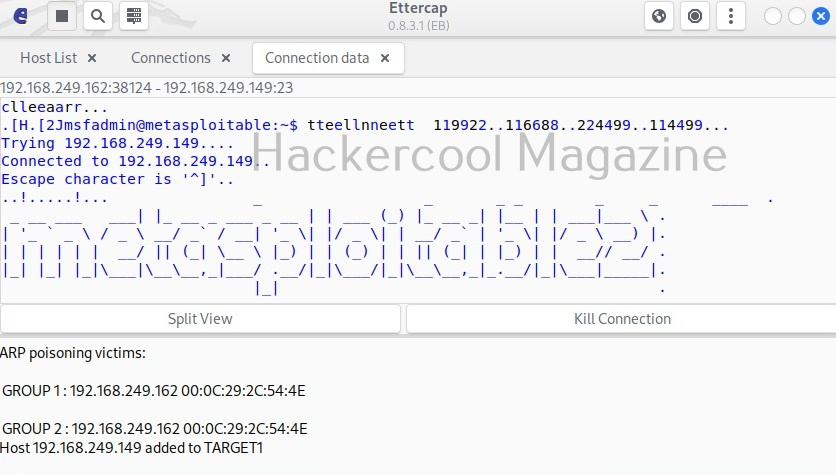
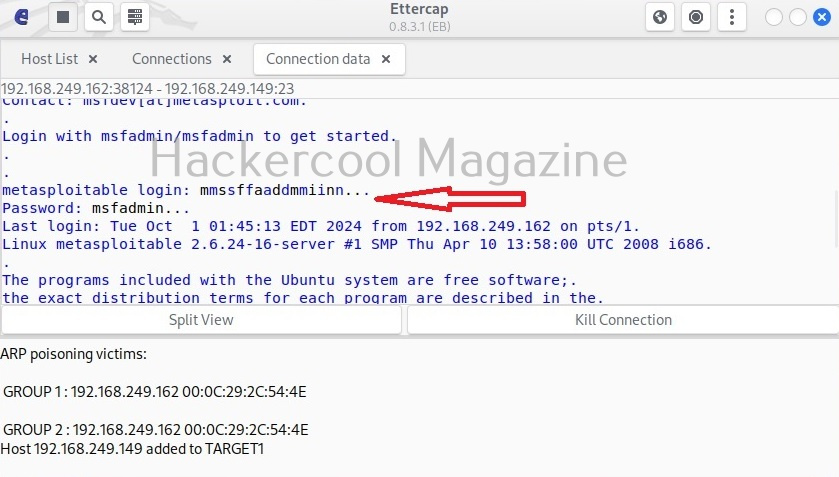
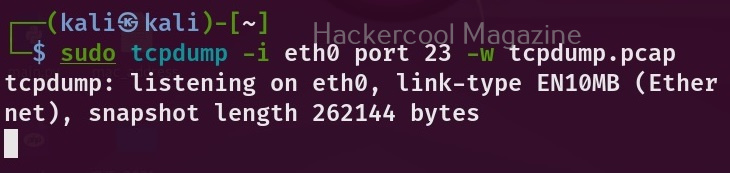
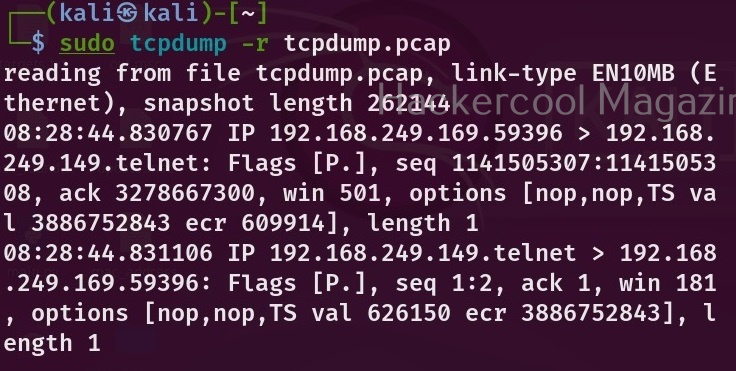
Hello, aspiring ethical hackers. In this blogpost, you will learn what is a payload and how to create a payload manually. Note that it is only for educational and knowledge purposes and not for performing any malicious actions. The aim of this article is to give you a basic understanding on how to create a payload. Let’s start with defining what exactly is a payload.
What is a payload?
A payload in cyber security is a piece of code that is executed after successfully running an exploit to take advantage of a vulnerability. When a Proof Of Concept (POC) for a vulnerability is disclosed, this allows most hackers around the world to execute their chosen payloads. This payload can be anything from malware, reverse shell, RAT, ransomware etc or their own custom payload.
For example, ms08_067 vulnerability was exploited in real-world to deploy Conficker worm payload, but while pen testing with Metasploit, meterpreter is used as payload. Although payloads can be created using payload generators simply, it would be very thrilling and educative to create manually.
Creation of a computer payload consists of six steps. They are,
- Decide the function you want your payload to perform.
- Select a programming language in which you want to code your payload.
- Code the payload.
- Compiling the payload.
- Testing.
- Sharing the payload.
Let’s learn about each step in detail.
1. Function of a payload:
Before you even start coding a payload, you need to decide what exactly you want your payload to do. In real-world, payloads perform many functions that include downloading and installing additional payloads, wiping data from the infected system and even taking complete control of the system. For example, I decide that my payload should open a Firefox browser when executed.
2. Choose your language:
After deciding the function you want your payload to perform, next thing you have to do is choose a programming language to code this payload. Payloads can be written in many programming languages like C, Delphi, Visual Basic, C#, C++, Cobol, Ruby, Python etc. They can also be created using scripting languages like JavaScript, Batch script, Bash, PowerShell etc. Choose the programming or scripting language of your choice. For example, I want to write my payload in Batch scripting.
3. Write code:
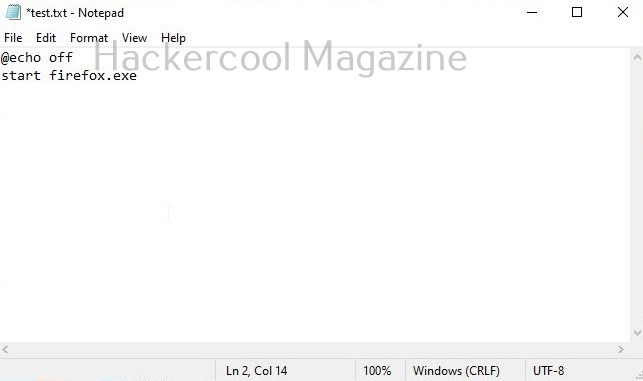
Once you select the programming language or scripting language, you need to code the payload. To code a batch script, all I have to do is open a notepad, add the code shown below and save the file as Batch file (with extension .bat)
@echo off
start firefox.exe
4. Compile (if necessary):
Compile the payload. Compiling is a process of converting source code into machine-readable code so that a computer can execute it. Since we have written our code in Batch, it doesn’t need any compilation. But programs written in C,C++, Python need compiling. Compiled programs are usually fast.
5. Test the payload:
Once you have finished coding the virus and compiling it, test its working by executing the virus. I execute the Batch virus I created and it open Firefox browser as shown below.
6. Share the virus:
The last step is to share the payload to make your target user execute it. Normally hackers use social engineering or phishing schemes to spread the paylaod.