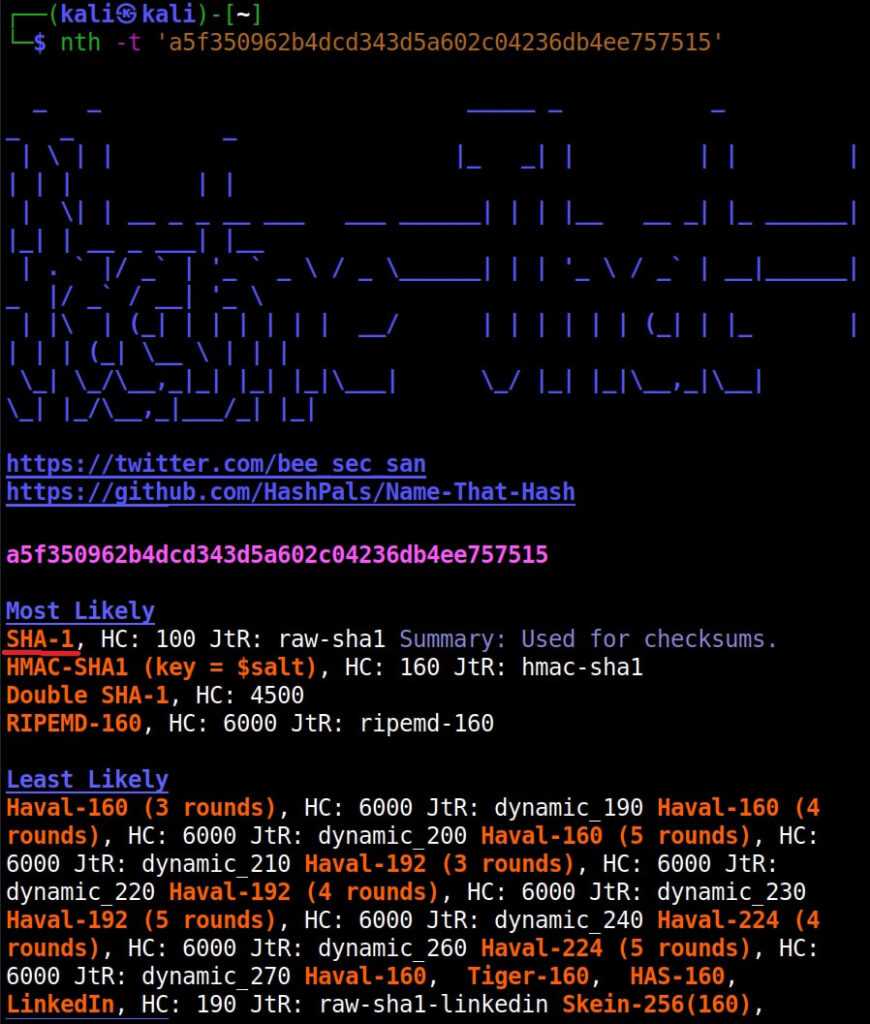
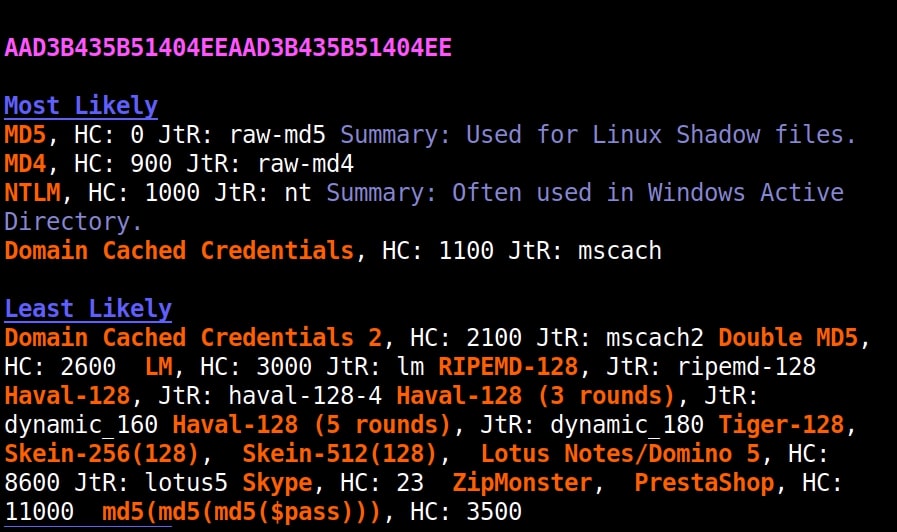
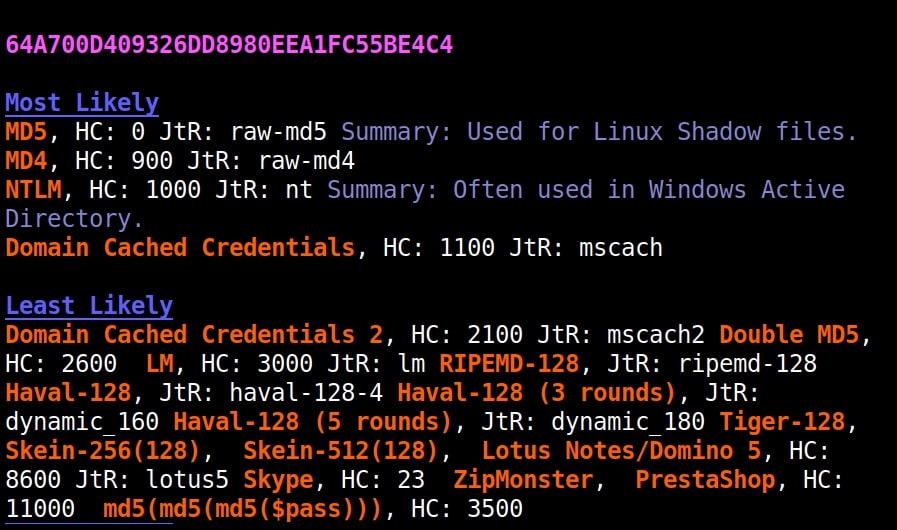
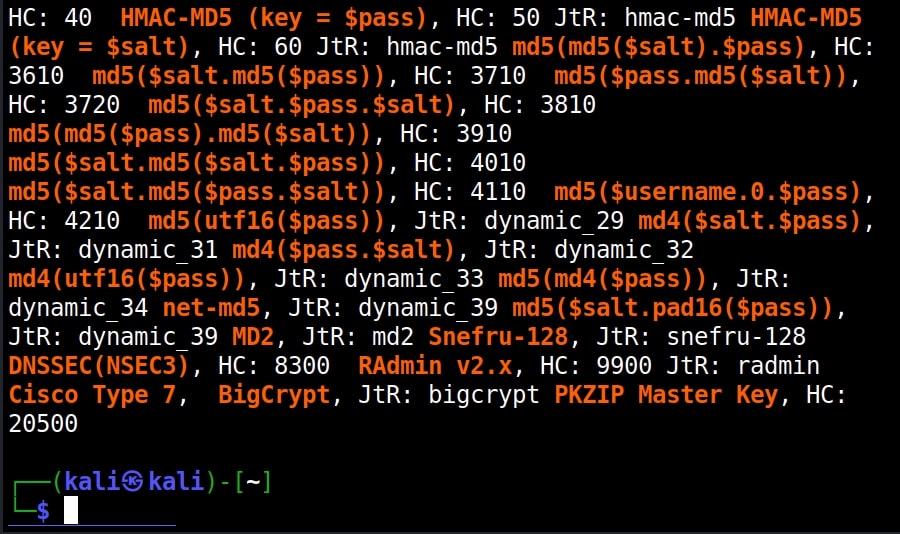
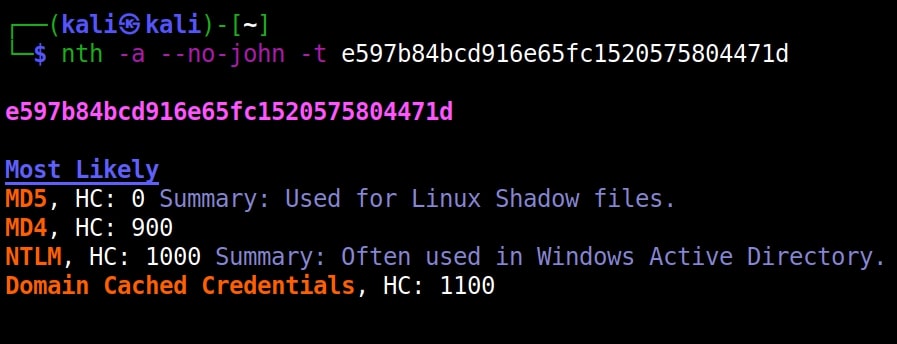
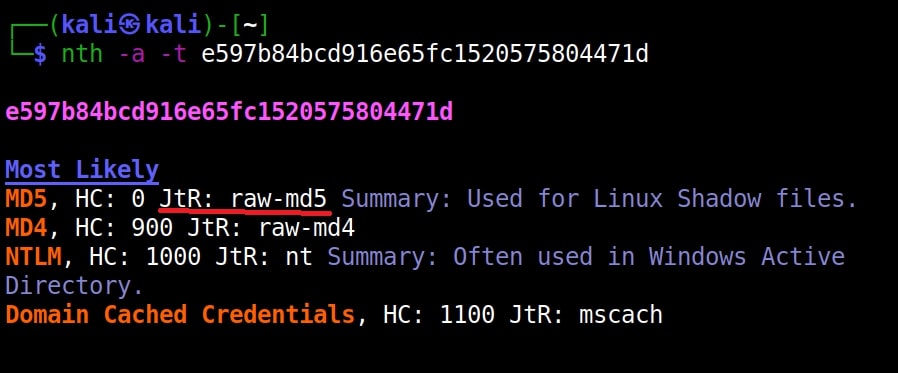
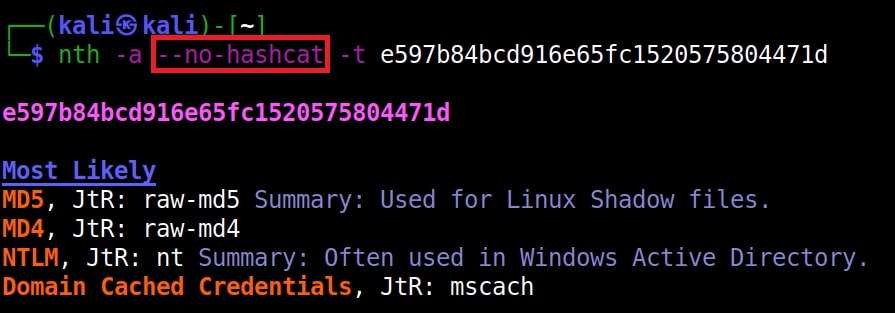
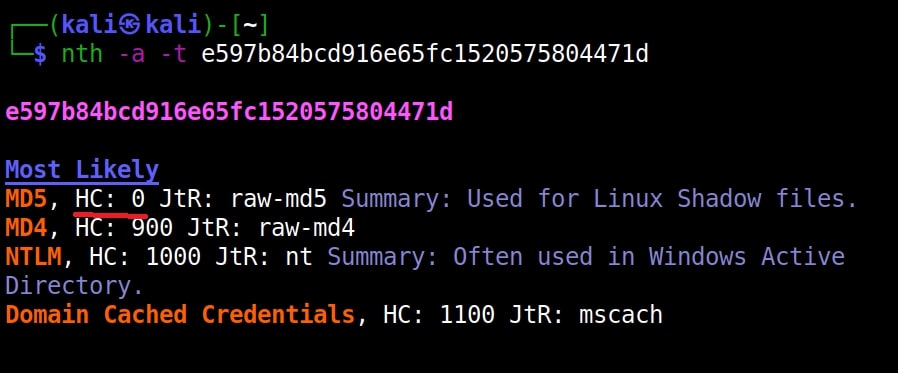
Hello aspiring Ethical Hackers. In our previous blogpost, you learnt what is password cracking and various techniques of cracking passwords. In this blogpost, you will learn about Brutus password cracker, one of the popular tools that is used for cracking passwords.
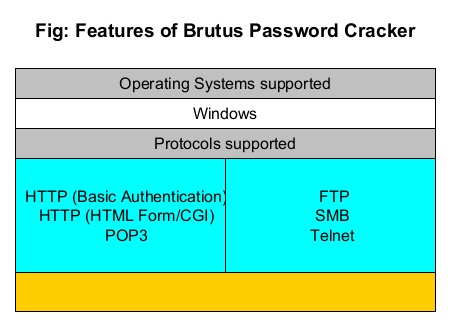
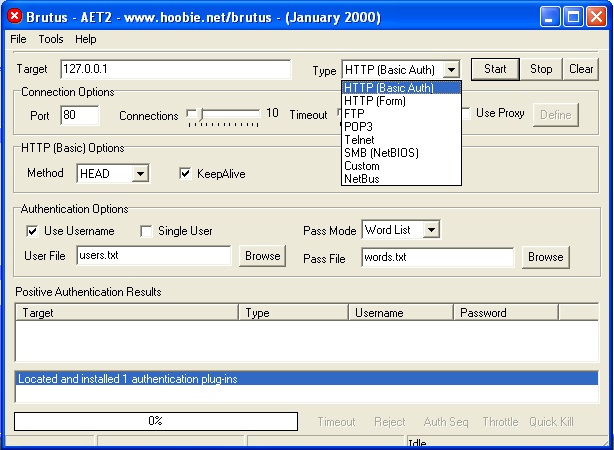
Brutus is a password cracking tool that was actually designed to test for default credentials for routers . It was made public way back in October 1998 but it is still popular in present time. It is a portable password cracking tool and there is no need of installing it. It can be downloaded from here. It works only on Windows and supports cracking passwords of various protocols. They are,
- HTTP (Basic authentication)
- HTTP (HTML form/CGI)
- POP3
- FTP
- SMB
- Telnet
After downloading, we just need to extract the contents of the archive.
To run Brutus, click on the BrutusA2 application file.
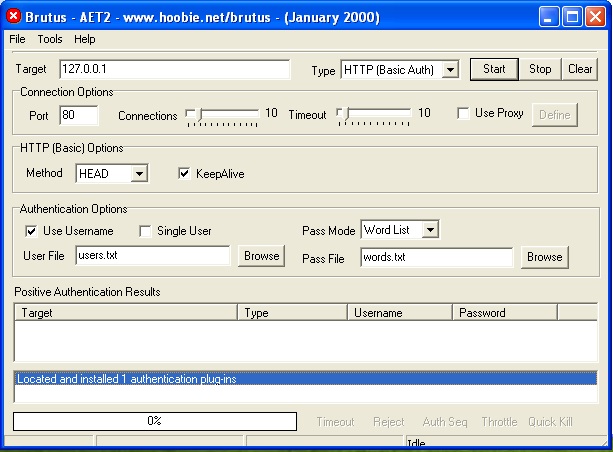
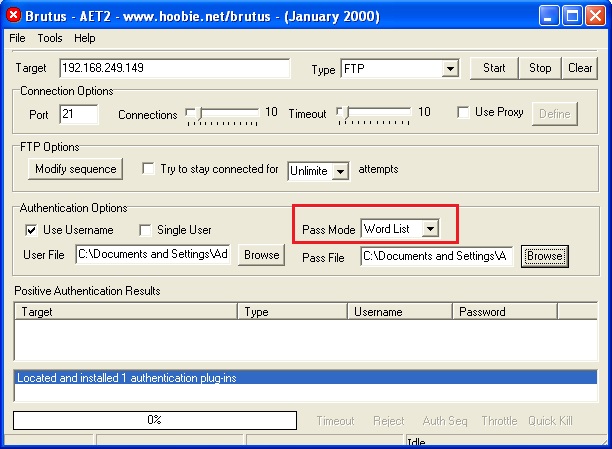
It has three modes of operation. They are, wordlist, brute force and combo list where credentials are given as username/password pairs.
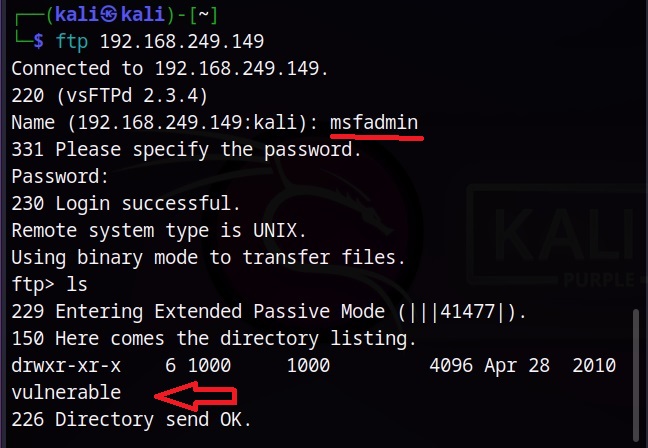
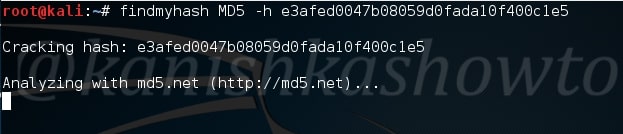
For the purpose of demonstration, let’s try to crack FTP password of Metasploitable 2. I will be using the wordlist mode of attack for this. This wordlist was created while performing SMB enumeration of the target. Wordlists can also be generated using tools like Crunch, Cewl etc. After specifying the wordlist, I just need to click on “Start” to begin cracking passwords.
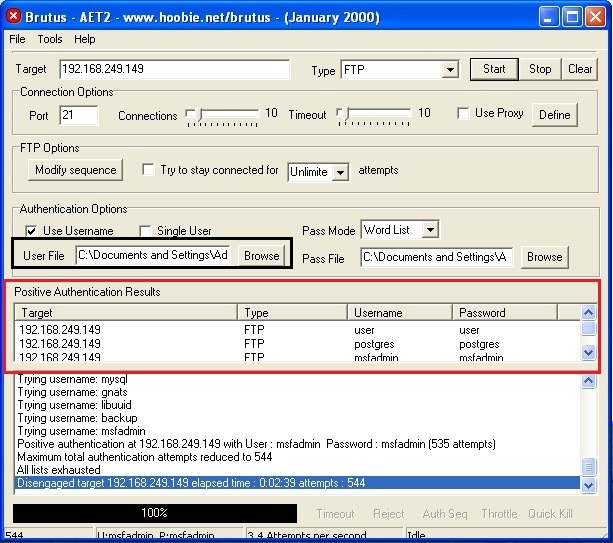
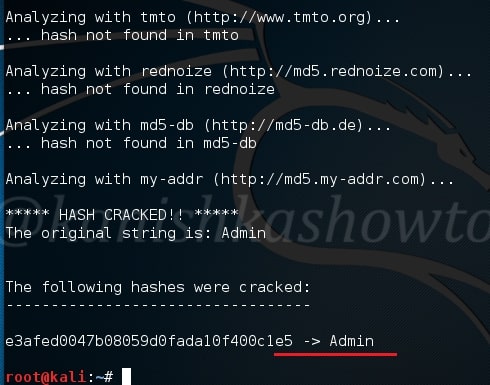
As the tool continues to crack credentials, any positive authentication results will be displayed as soon as they are found. In our current example, Brutus successfully extracted three credentials. They are,
- user:user
- postgres:postgres
- msfadmin:masfadmin
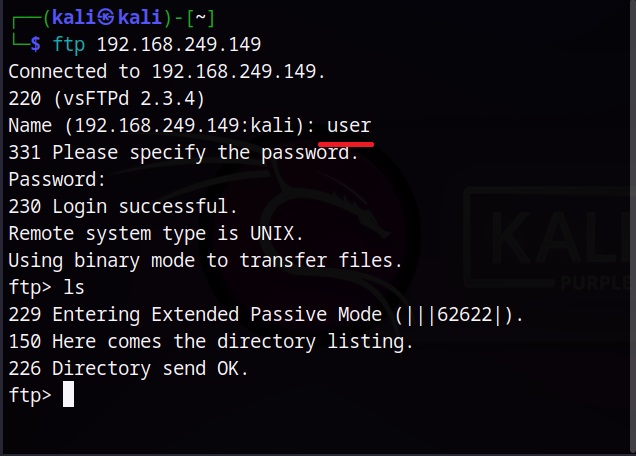
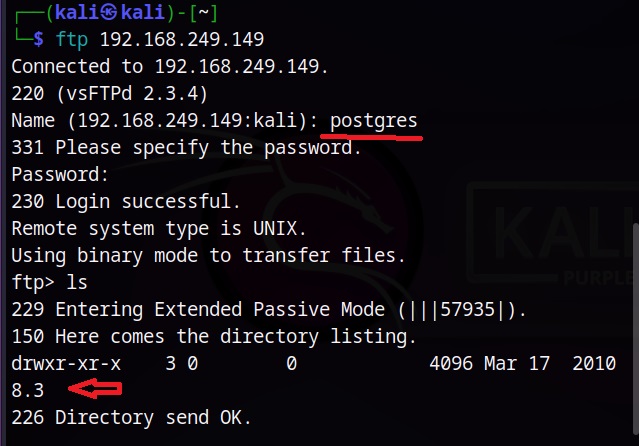
Let’s use them to login into our target.
Successful. Similarly Brutus password cracker can be used to brute force credentials too.