Hello, aspiring ethical hackers. This blogpost is a beginner guide to IDS (Intrusion Detection System) and IPS (Intrusion Preventions System). IDS and IPS are two of the security technologies used for securing the network of any organization from hackers.
What is an IDS and what is an IPS?
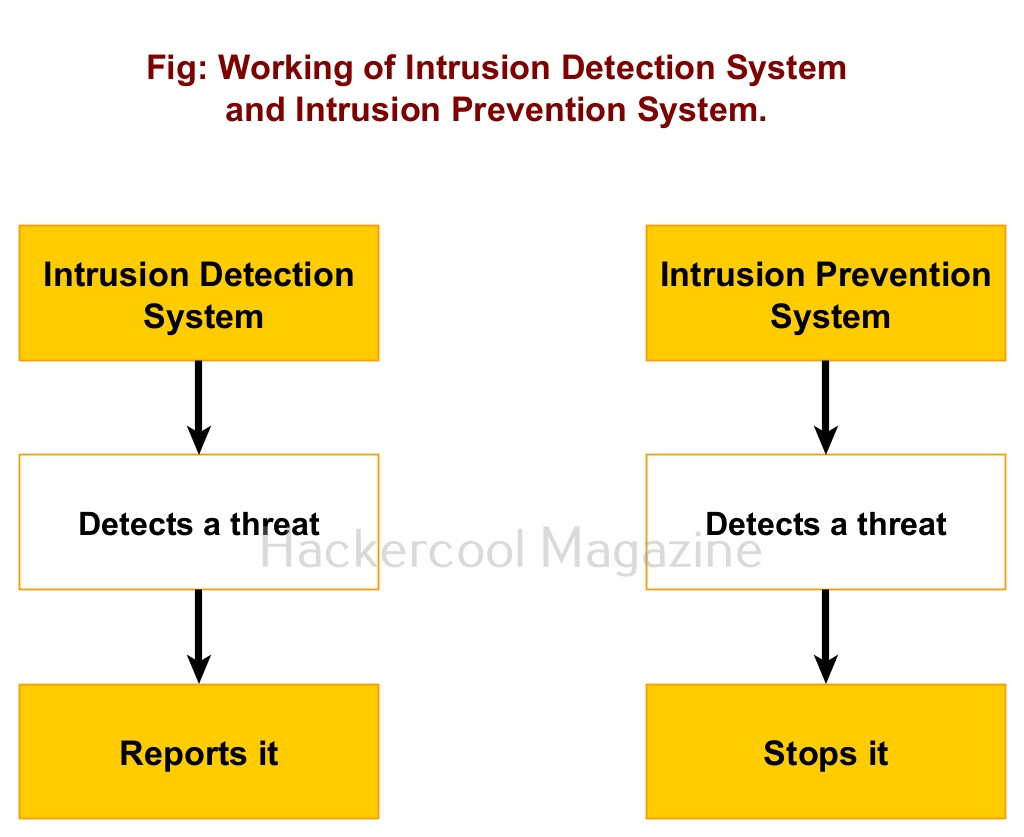
Intrusion Detection system (IDS) is an appliance or software that detects any malicious activity on the network and reports it. Intrusion Prevention System (IPS) on the other hand acts just like Intrusion Detection System but, unlike it doesn’t just make a report but tries to prevent its occurrence. This malicious activity can be anything like modification of system or important files, suspicious network traffic and execution of some files etc. Both Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are useful in enhancing the security of the network.
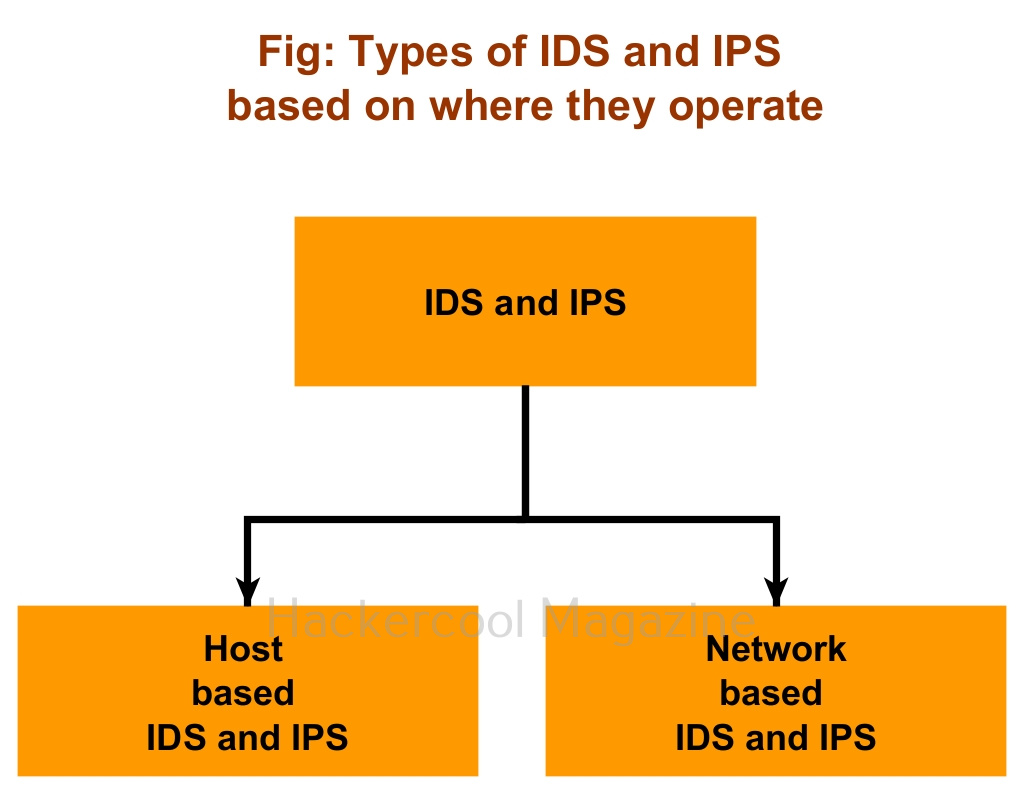
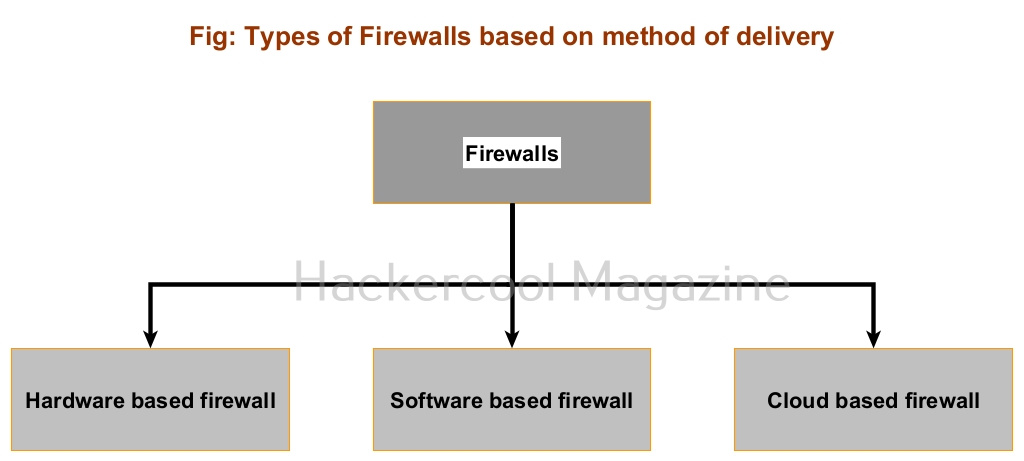
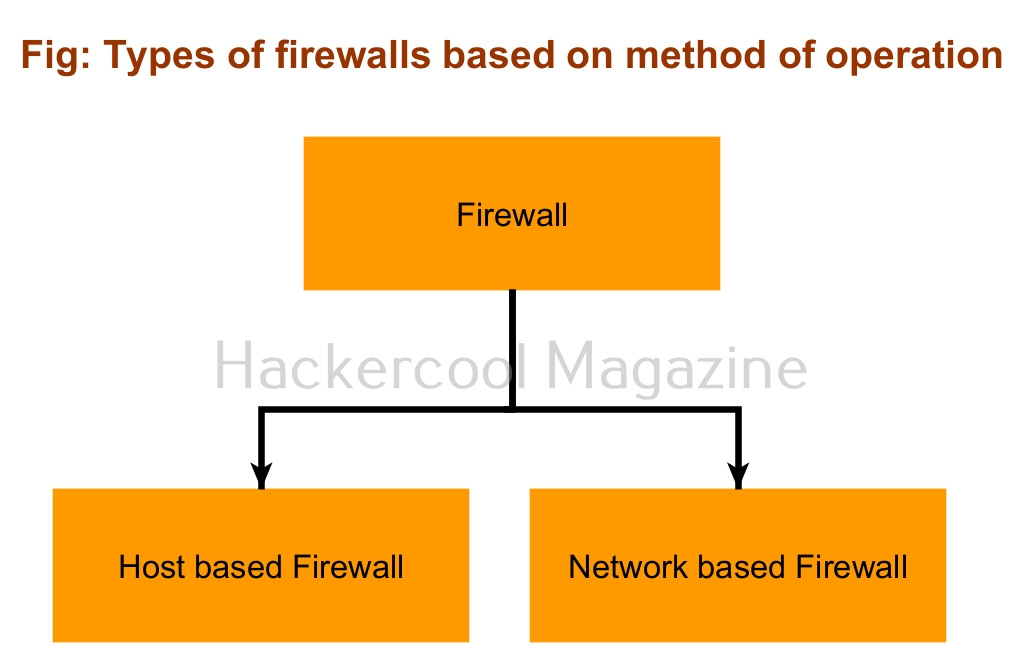
Based on the mode of operation, Intrusion Detection System and Intrusion Prevention System can be classified into two types. They are, 1) Host based (Software) 2) Network based (Hardware).
- Host based Intrusion Detection and Prevention Systems: They work by detecting or preventing threats on a single system.
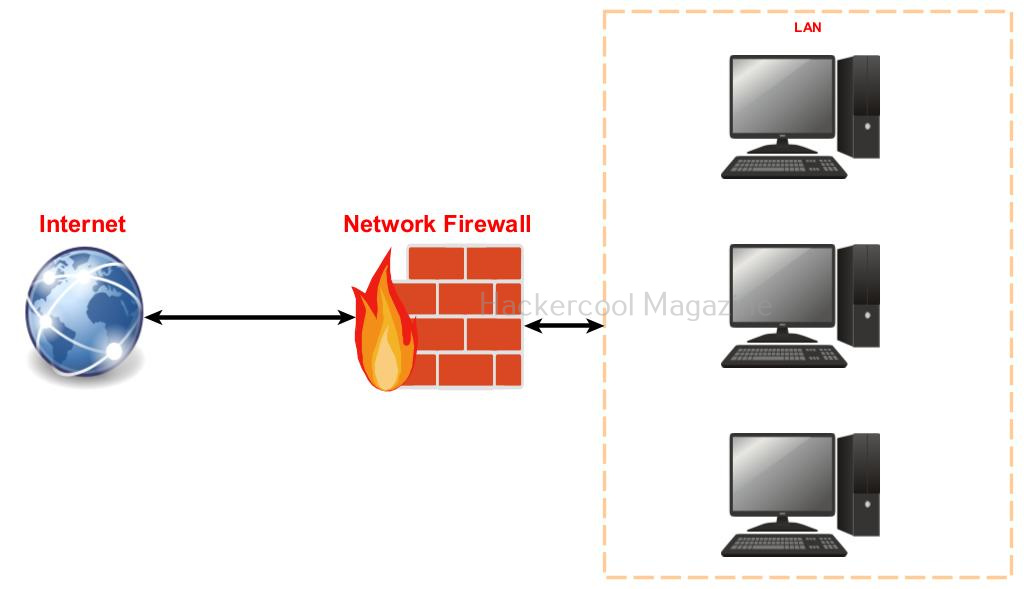
- Network based Intrusion Detection and Prevention Systems: These are most probably a hardware appliance that detects or prevents threats on the entire network.
Types of IPS and IDS
Based on the techniques they use to identify and prevent threats, Intrusion Detection Systems and Intrusion Prevention Systems can be classified into two types. They are,
1. Signature-based :
This type of Intrusion Prevention Systems and Intrusion Detection Systems detect threats by comparing actions with predefined signatures. For example, If action of an executable matches with a pre-defined signature of an IDS or IPS, it is classified as a threat.
2. Anomaly based:
Anomaly based Intrusion Detection Systems and Intrusion Prevention Systems detect threats by observing the behavior of the assumed threat. If the IDS and IPS see any different behavior than that is considered to be normal, it classifies it as a threat. For example, if a program being installed is trying to alter system files, this can be considered as an anomaly.