Hello, aspiring ethical hackers. This article is a beginner guide to gaining access. Gaining access is the third phase in ethical hacking after footprinting and scanning & enumeration. It should be noted that the earlier two phases will play a major role in gaining access. This blogpost will explain you about different ways in which hackers or pen testers gain access to a target system or network.
What is gaining access?
In our previous blogpost, you learnt what a shell is and types of shell in cybersecurity. When a hacker or pen tester gains a shell on the target system or network, it is called as gaining access. Gaining access is the first phase where a hacker or pen tester gains some control on the target system.
Methods of gaining access
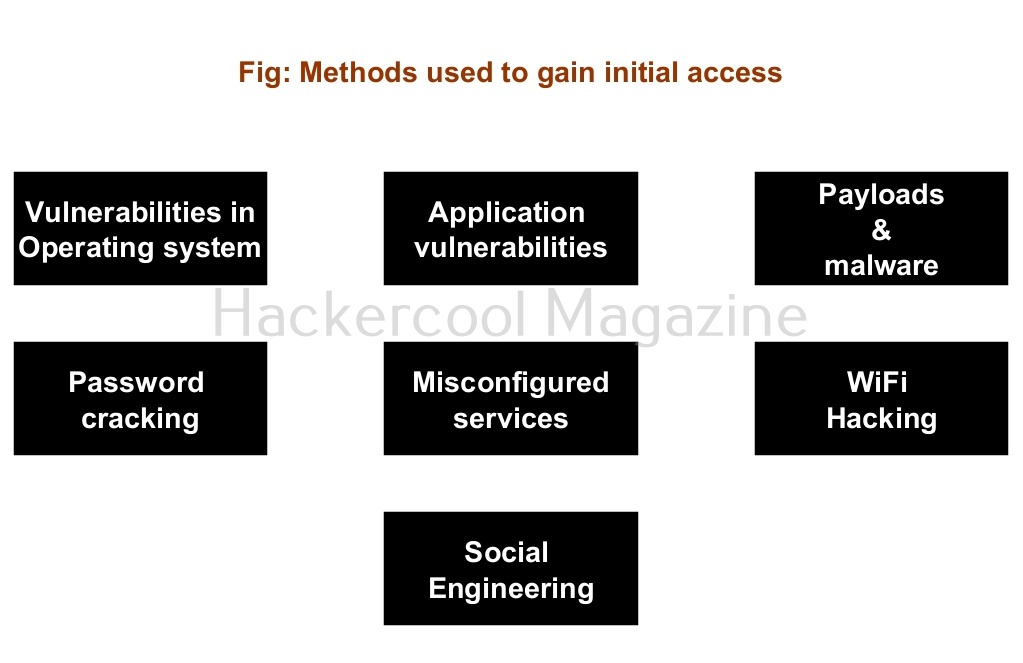
There are multiple ways by which hackers can gain initial access. They are,
- Vulnerabilities in the operating system or firmware.
- Application vulnerabilities.
- Payloads & malicious software.
- Password’ cracking.
- Misconfigured services.
- Social- engineering.
- Wi Fi hacking
1. Vulnerabilities in the operating system or firmware:
An operating system is the core of any computing device. Enterprises around the world use different operating systems for different purposes. Some of the popular operating systems used by enterprises around the world are Windows, Linux, MacOS, Android, IOS, chrome OS, Red Hat Enterprise Linux, Solaris, Centos, Ubuntu, IRIX and FreeBSD etc. No matter what operating system it is, it is a software consisting of programs. So, any vulnerability exposed in the operating system can be exploited by hackers to gain initial access. For example, ms08-067 and EternalBlue.
2. Application vulnerabilities:
An operating system is by itself not useful. So, a lot of application or programs are installed over the operating system to perform certain functions. Any vulnerabilities in these installed programs can be exploited successfully gain initial access. For example, Macros or Excel Macros.
3. Malicious payloads:
Hackers just don’t use vulnerabilities to gain access. They also use malicious payloads like malware and virus to gain access. Learn more about payload generators.
4. Cracked passwords:
Sometimes enterprise systems are enabled with remote access so that employees can connect to them remotely for the purpose of their work. The protocols enabling remote access like SSH, FTP, Telnet and RDP etc. Cracking the credentials of these services give hackers a way to gain access to the servers and subsequently to the entire system or network. Learn more about password cracking.
5. Misconfigured services:
Sometimes, services being used by the target network can be misconfigured either by mistake or on purpose. Hackers can exploit these misconfigurations to gain initial access.
6. Hacking Wi-Fi network:
Wi Fi hacking is often sometimes ignored as a factor that can provide initial access to the hackers. Hacking WiFi (especially if the password is not complex) is very easy compared gaining access through the above explained methods. It also provides easy access to hack. Learn more about WiFi hacking.
7. The human factor:
No matter how strong the firewall on the network is or how secure the devices are in a network, if the employees of the organization are not well trained, they can eventually give hackers access into the network or devices. Social-engineering is often very underrated as a factor that allows hackers to gain access. Learn more about social engineering.
Follow Us