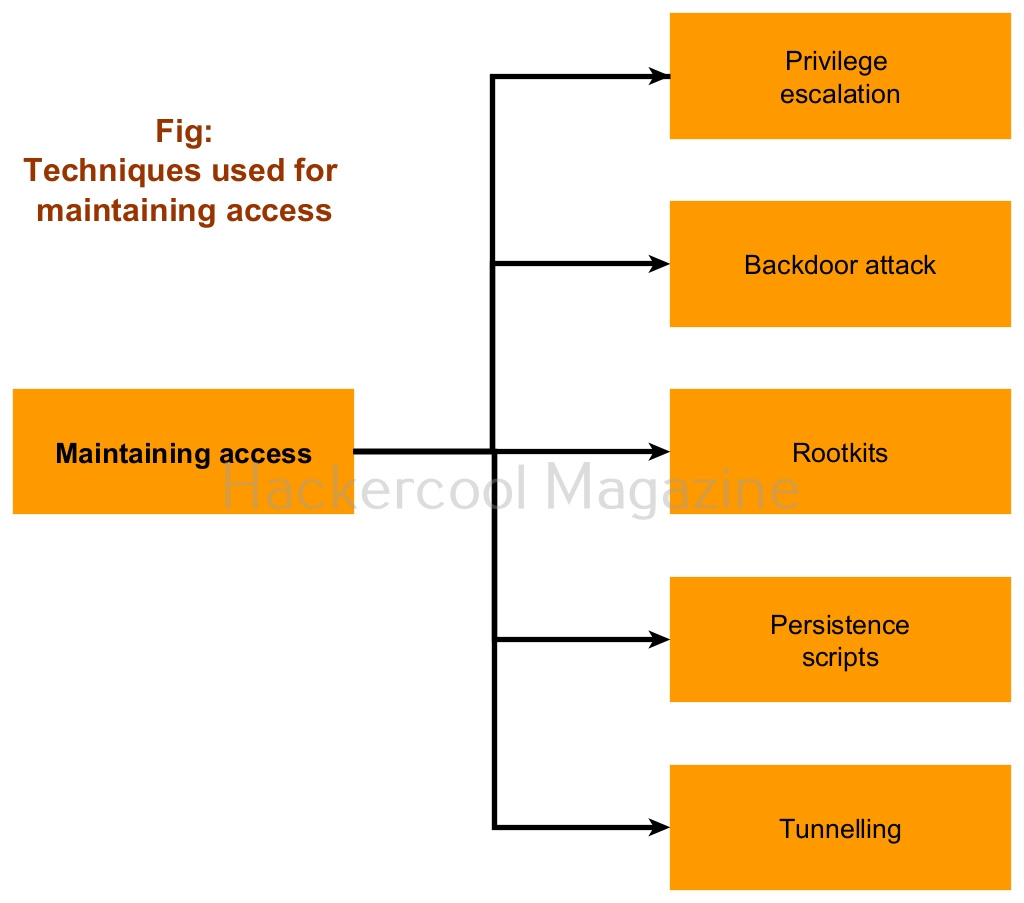
Hello, aspiring ethical hackers. In this blogpost, you will learn about maintaining access in ethical hacking. Maintaining access is the fourth phase in the total 5 phases of ethical hacking. In this phase, hackers try to hold on to the initial access or foothold they have gained on the network.
This is done using various methods. They are,
1. Elevating privileges:
Most of the time when hackers gain initial access on the target system or network, it is a lower privileged one. So, as soon as hackers gain access, they try to elevate their privileges on the target system to be able to perform important actions on the target network or system. Learn more about privilege escalation.
2. Backdooring:
In this method of maintaining access, hackers try to install a backdoor on the target system or network. They do this by either modifying the legitimate components or by installing specific backdoors like C&C servers, genuine remote administration software etc.
3. Rootkits:
Sometimes, hackers install rootkits on the target system or network. A rootkit is a type of malware that masks its existence from the system software including Antivirus. Normally a rootkit provides higher level of access or sometimes even kernel level access to hackers.
4. Persistence scripts:
Hackers also use widely available persistence scripts to maintain access on the target system of the network.
5. Tunneling:
Maintaining access is not always about installing a backdoor or rootkit etc on the target system. Sometimes, it involves tunneling. Tunneling is a process in which data is usually shared between two different networks privately without being detected.
Follow Us