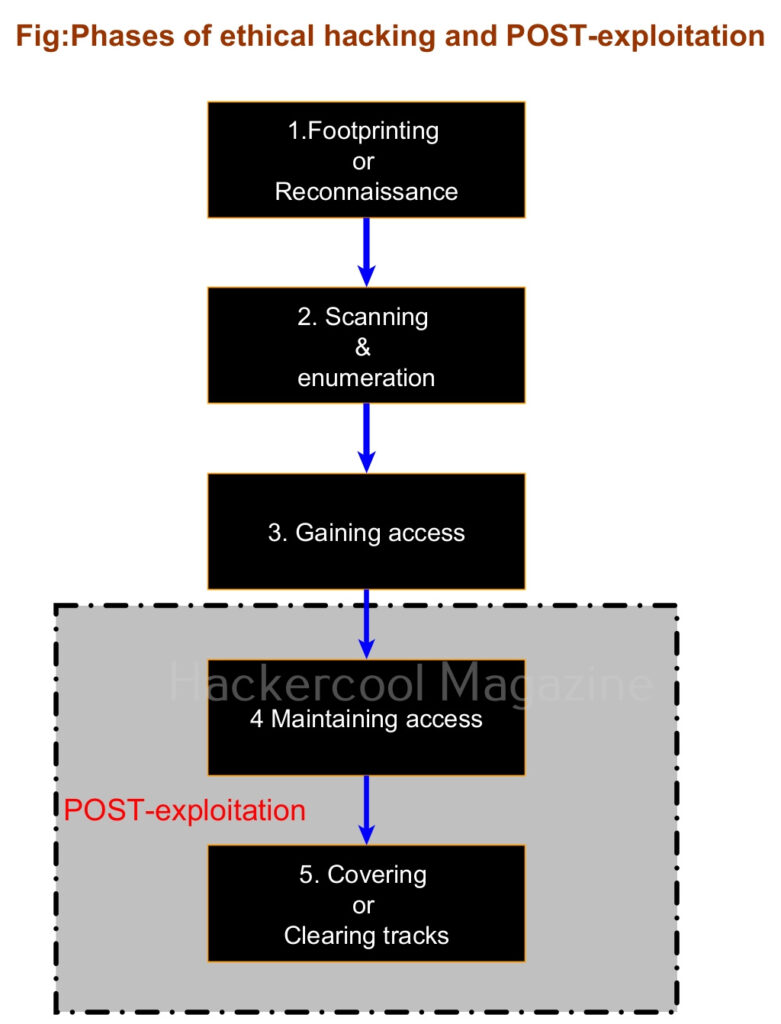
Hello, aspiring ethical hackers. In this blogpost, you will learn about Windows privilege escalation. Windows privilege escalation comes after Windows hacking and is part of Post-exploitation of Windows.
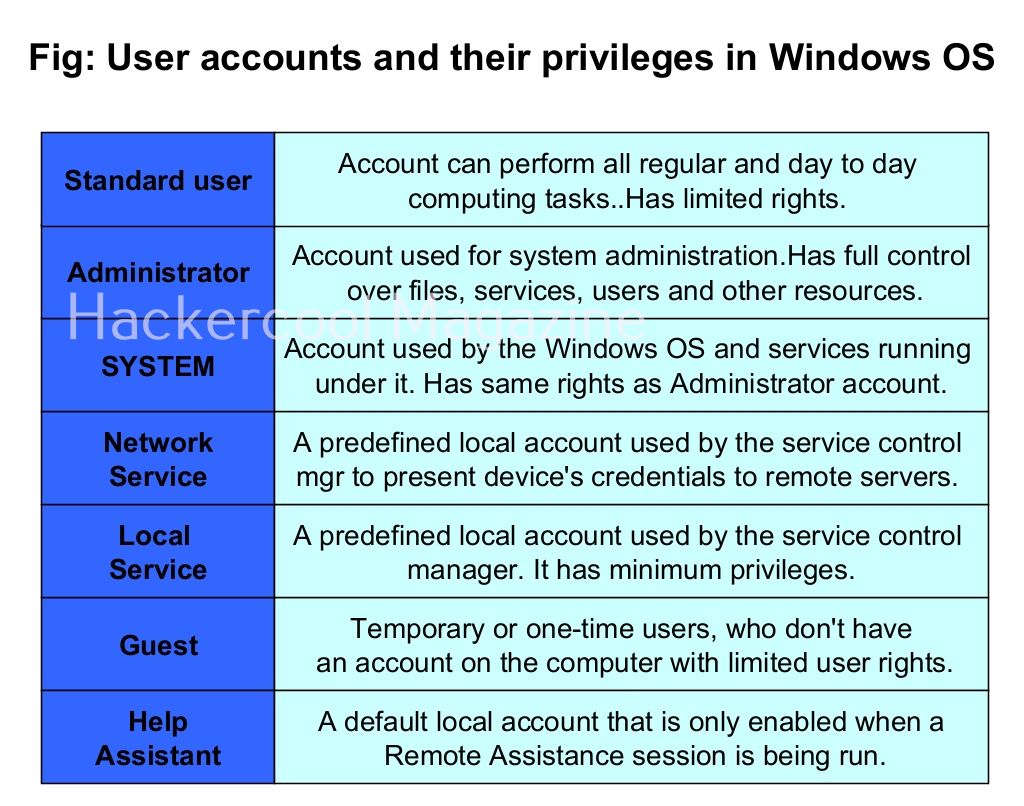
What is Windows privilege escalation?
Windows privilege escalation is the process of elevating privileges on a Windows system after successfully gaining access to a Windows system.
Why is it important?
According to StatCounter Global Stats, over 72.52% of people worldwide use Windows as their Desktop. That is the reason why Windows privilege escalation is one of the most important topics of ethical hacking.
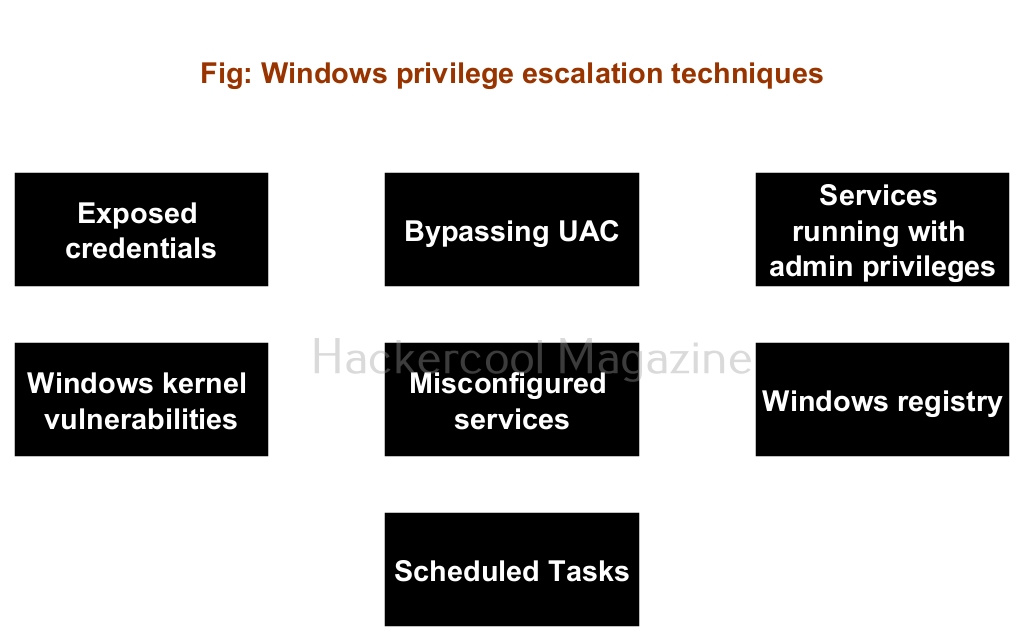
Windows privilege escalation techniques
There are multiple ways by which hackers can elevate privileges on a Windows systems. They are,
- Exposed credentials
- Bypassing UAC
- Exploiting services running with administrator privileges.
- Windows kernel vulnerabilities.
- Misconfigured services.
- Windows Registry.
- Scheduled Tasks.
1. Exposed credentials:
Sometimes, the credentials of user accounts with administrator privileges on a Windows system are exposed. Most people still store Windows credentials on Desktop for easy access (you may not believe this but this is true). So, attackers can login as user with high privileges using these exposed credentials.
2. Bypassing UAC:
User Account Control (UAC) is a Windows security feature that was designed to protect the operating system. Introduced with Windows Vista, it is a mandatory access control enforcement feature. It works by limiting application software to standard user privileges until a user with administrator privileges authorizes an elevation in privileges.
This allows only applications that are trusted by users to be assigned administrator privileges. However, vulnerabilities in this UAC sometimes allows hackers to bypass UAC and get administration privileges on the target system.
3. Exploiting services running with administration privileges:
Some applications installed on Windows by users need administrative privileged on the system to run. If attackers exploit any vulnerabilities in these applications, they can easily elevate their privileges on the Windows system.
4. Windows kernel vulnerabilities:
Windows kernel in Windows (or for that matter any operating system) has the highest privileges assigned to it. If attackers exploit any vulnerabilities in the Windows kernel, they can elevate their privileges on the Windows system.
5. Misconfigured services:
Misconfigurations in services on Windows can also be exploited to escalate privileges on Windows system.
6. Windows Registry:
Windows registry is a hierarchical database that stores all low level; settings of Microsoft Windows. Weak permissions in the Windows registry can also be exploited to elevate privileges.
7. Scheduled Tasks:
Windows Task Scheduler (formerly known as Scheduled Tasks) is used to automate jobs and tasks in Windows just like cron jobs in Linux. Weak file permission setting in Task scheduler can be exploited to elevate privileges on a Windows system.