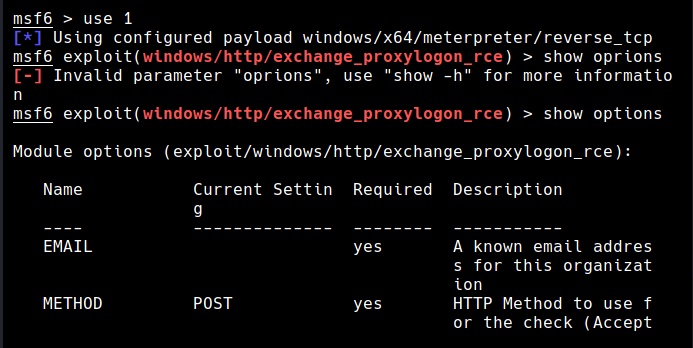
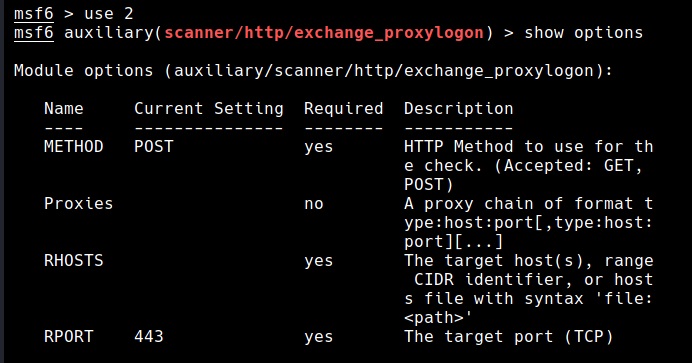
Hello aspiring ethical hackers. Welcome to the second part of understanding Wireless security. In Part 1, readers have learnt about the history of WiFi, terminology used in WiFi and WEP security and its weakness. So, let’s continue from there. Responding to the serious weaknesses in WEP encryption security, the Wi-Fi Alliance introduced Wi-Fi Protected Access (WPA) to secure wireless networks. However, the Wi-Fi Alliance intended WPA as an interim measure to take the place of WEP before they bring in Wi-Fi Protected Access 2 (WPA 2).
Wi – Fi Protected Access (WPA)
Also known as Temporal Key Integrity Protocol (TKIP) standard, WPA implements the TKIP encryption method and was introduced in 2003. TKIP introduced three new methods to overcome weaknesses in Wired Equivalent Privacy (WEP) standard.
1. TKIP implements a key mixing function that combines the secret root key with the initialization vector before passing it to the RC4 cipher initialization. WEP on the other hand merely concatenated the initialization vectors to the root key and passed this value to the RC4 cipher.
2. A sequence counter is implemented to protect against replay attacks. Hence, packets received out of order will be rejected by the Access point.
3.TKIP implements a 64-bit Message Integrity Check (MIC) replacing Cyclic Redundancy Check (CRC) used in WEP. This re-initializes the sequence number each time when a new key (Temporal Key) is used.
Wi – Fi Protected Access (WPA) 2
WPA 2 was introduced in 2004 to replace WPA. It implemented the mandatory elements of IEEE 802.11i. 802.11i makes use of the Advanced Encryption Standard (AES) block cipher instead of RC4 stream cipher used by both WEP and WPA. It also uses Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) encryption protocol. It provides the following security services.
1. Data Confidentiality: It ensures only authorized parties can access the information
2. Authentication: provides proof of genuineness of the user
3. Access control in conjunction with layer management.
Wi – Fi Protected Access 3 (WPA 3)
The Wi-Fi Alliance announced WPA3 as a replacement to WPA2 in 2018. The new standard uses an equivalent 192-bit cryptographic strength in WPA3-Enterprise mode (AES-256 in GCM mode with SHA-384 as HMAC) and still mandates the use of CCMP-128 (AES-128 in CCM mode) as the minimum encryption algorithm in WPA3-Personal mode.
The WPA3 standard also replaces the pre-shared key (PSK) exchange with Simultaneous authentication of Equals (SAE) exchange, a method originally introduced with IEEE 802.11s. This results in a more secure initial key exchange in personal mode and forward secrecy.
WPA – Versions
There are two versions of WPA. They are,
- A. WPA- Personal
- B. WPA – Enterprise
WPA – Personal
Wi-Fi Protected Access (WPA) – Personal is designed for home and small office networks. This version uses Pre- Shared Key (PSK) and hence it is also referred as WPA-PSK (pre-shared key) mode. The network traffic is encrypted using a 128-bit encryption key derived from a 256-bit shared key. WPA-Personal mode is available on all three WPA versions.
WPA – Enterprise
As its name implies, this is designed for enterprise networks and requires a RADIUS authentication server. This requires a more complicated setup but provides additional security like protection against dictionary attacks on short passwords. Various kinds of the Extensible Authentication Protocol (EAP) are used for authentication. WPA-Enterprise mode is available on all three WPA versions.
Weakness Of WPA/WPA2
1. Pre-shared key WPA and WPA2 remain vulnerable to password cracking attacks if users rely on a weak password or passphrase.
2. WPA passphrase hashes are seeded from the SSID name and its length; rainbow tables exist for the top 1,000 network SSIDs and a multitude of common passwords, requiring only a quick lookup to speed up cracking WPA-PSK
Brute forcing of simple passwords can be attempted using the Aircrack Suite starting from the four-way authentication handshake exchanged during association or periodic re-authentication. In this article, readers have seen how WPA password was cracked. One important feature of cracking WPA /WPA2 is that we don’t need a lot of traffic to crack it. We just need one client connected to the Wi-Fi Access point. Then we de authenticate it from the Wi-Fi Access point. The client automatically tries to connect to the Wi-Fi access point again.
It is at this stage, we try to capture the WPA handshake. If you have noticed, while using aircrack, to crack the password, we supplied a dictionary or wordlist. While cracking WEP we didn’t.
So what is a weak password? Any password that is part of a dictionary or wordlist can be called a weak password in WPA. Otherwise, WPA /WPA2 is considered secure. WPA3 replaces cryptographic protocols susceptible to off-line analysis with protocols that require interaction with the infrastructure for each guessed password, supposedly placing temporal limits on the number of guesses. However, design flaws in WPA3 enable attackers to plausibly launch brute-force attacks.
Wi-Fi Protected Setup (WPS)
In year 2007, the Wi-Fi Alliance introduced Wi-Fi Protected Setup (WPS). The main feature of this protocol is to allow home users who have little knowledge about wireless security to set up Wi-Fi Protected Access (For some users, accessing the router dashboard and setting passwords can be too complex). It also makes it easy to add new devices to an existing Wireless network without entering long passphrases. WPS also allows the owner of Wi-Fi privileges to block other users from using their household Wi-Fi. There are two common methods to use WPS.
- PIN Method.
- Push Button Method.
PIN Method
Every Wireless Router with WPS enabled has a PIN on the Wi-Fi Router (which is usually printed on a sticker). This PIN must then be entered into any new device that wants to connect to this Wireless network. No need of memorizing any password.
Push Button Method
In this method, the user has to PUSH a WPS button on both the Access point and the new wireless client device. On most devices, this discovery mode turns itself off as soon as a connection is established or after a delay (typically 2 minutes or less), whichever comes first, thereby minimizing its vulnerability.
Although WPS was introduced to simplify Wi-Fi Connection issues, it suffers from a major vulnerability. Any remote attacker can recover the WPS pin in a few hours by using brute force attack. Once he does this, he can easily recover WPA/WPA2 key also. Nowadays, all recent models of Wireless Routers have WPS enabled by default. It is wise to turn off WPS PIN feature although this is not possible on many routers.
WPS is widely understood to have added insecurity to otherwise secure WPA/WPA2. WPS pin is a 8 digit PIN that is required by clients to connect to the Wireless Router. The Wireless Router instead of checking the entire 8 digit PIN at once, checks the first four digits initially and then checks the last four digits. This makes brute forcing WPS PINs very easy.
This is because there are only 11,000 possible 4 digit pins and once the brute force software gets the first 4 digit pin right, the attacker can move on to cracking the latter 4 digit pin.
Tools Bully and Reaver are first to come to mind when we want to crack WPS pin. However, in our latest tests, both the tools are presenting some problems. You can read our previous articles on Bully and Wifite.
That was a complete guide to understanding wireless security. Hope our readers now have a better understanding of Wireless security. You can read Part 1 of Understanding Wireless security here. Happy hacking.