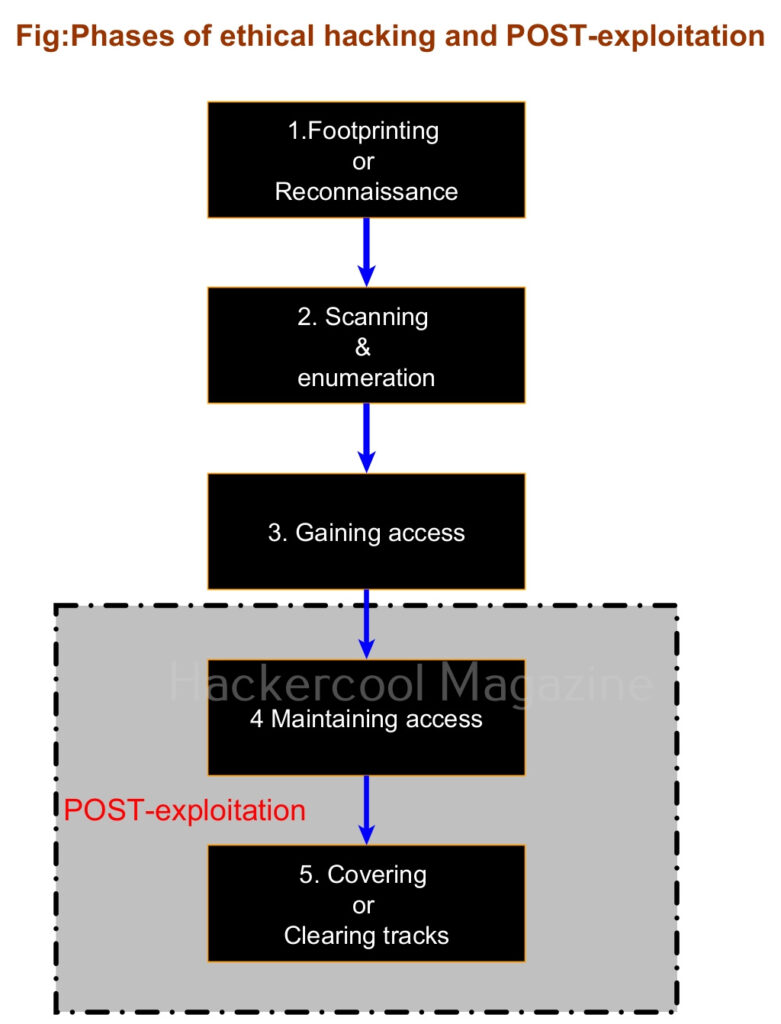
Hello, aspiring ethical hackers. In this blogpost, you will learn about POST-exploitation. POST-exploitation comes after the phase of gaining access in ethical hacking.
What is POST-exploitation?
POST- exploitation refers to all the operations that are performed after gaining initial access on the target system. It is done to further gain control of the target system and network. POST -Exploitation consists of three phases mainly. They are,
Let’s learn about each in detail.
1. Privilege escalation:
Privilege escalation is an act of gaining elevated access to resources that are normally restricted to an application or user. Privilege escalation is an act or process of gaining access to privileges of the other user account using any means or techniques. Normally privileges of user account with higher privileges are targeted by hackers. Learn more about privilege escalation.
2. Maintaining access:
Maintaining access is the fourth phase in the total 5 phases of ethical hacking. In this phase, hackers try to hold on to the initial access or foothold they have gained on the network. For this, they use various techniques like elevating privileges, installing backdoors, running persistence scripts and tunneling.
3. Covering Tracks:
Covering tracks or clearing tracks is the phase of ethical hacking in which a hacker tries to erase all the evidence on the target system that can lead back to the hacker. For covering tracks, hackers perform various actions like clearing logs, time stamping files etc.
Follow Us